Privacy protection data subscription method in block chain Internet of Vehicles
A technology of privacy protection and data subscription, which is applied in vehicle components, digital transmission systems, vehicle wireless communication services, etc., can solve problems such as single point of failure and incorrect query results, and achieve high reliability, data privacy protection, and strong reliability sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
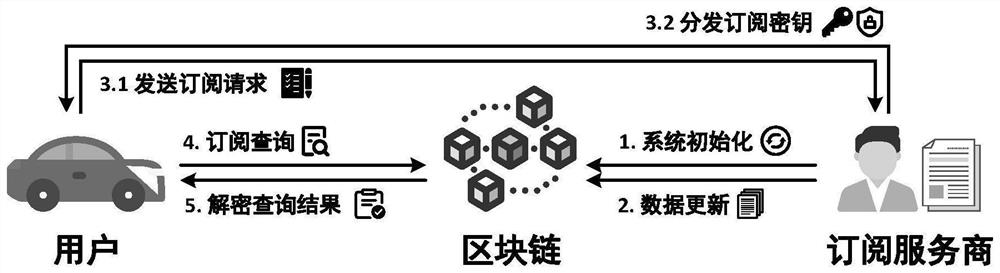
[0079] like figure 1 As shown, a privacy protection data subscription method in the blockchain Internet of Vehicles includes the following steps:
[0080] Step 1: System initialization.
[0081] The subscription service provider first needs to initialize the data subscription query system and generate a series of keys. Specifically, it includes the following steps:
[0082] Step 1.1: The subscription service provider generates a master key k and a public-private key pair (pk, sk) for generating a digital signature.
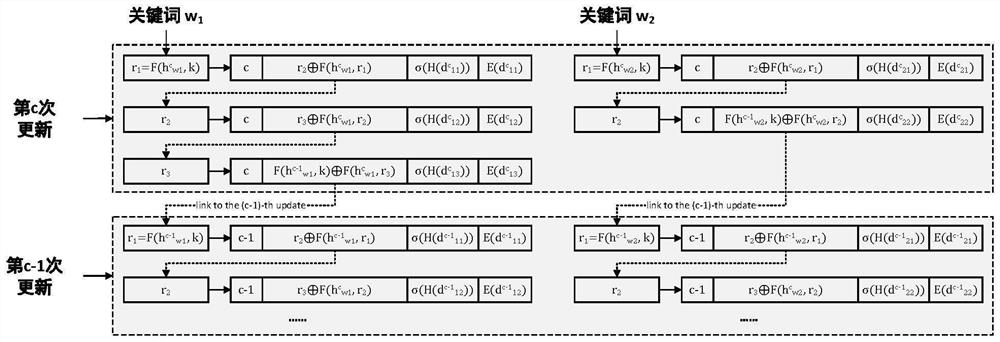
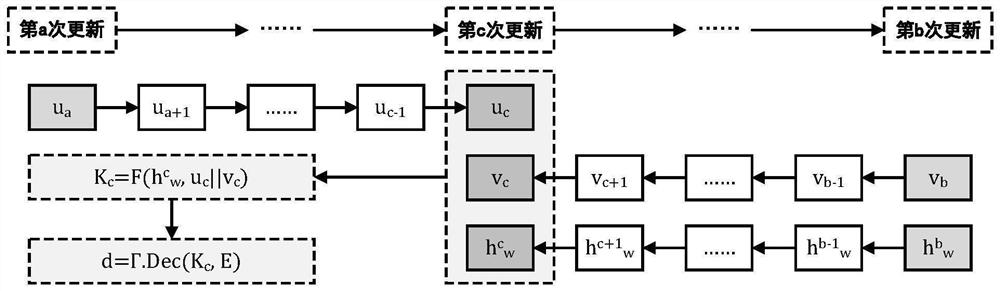
[0083] Step 1.2: The subscription service provider generates two hash chains U={u 1 , ..., u L } and V={v 1 ,...,v L }, each hash chain is composed of L hashes with a length of 256 bits, where L represents the maximum number of updates that the system can support, which is set by the subscription service provider. Specifically, the hash u in U i The calculation rule is: when i=1, u i is a random string with a length of 256 bits, when 1i =H(u i-1 ), where...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com