Smart home security communication system and communication method
A secure communication and smart home technology, applied to secure communication devices and key distribution, can solve problems such as low key rate, reduced related system security, user data and privacy leakage, etc., to improve security and reduce the risk of being stolen Risks, Preventing Predicted Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
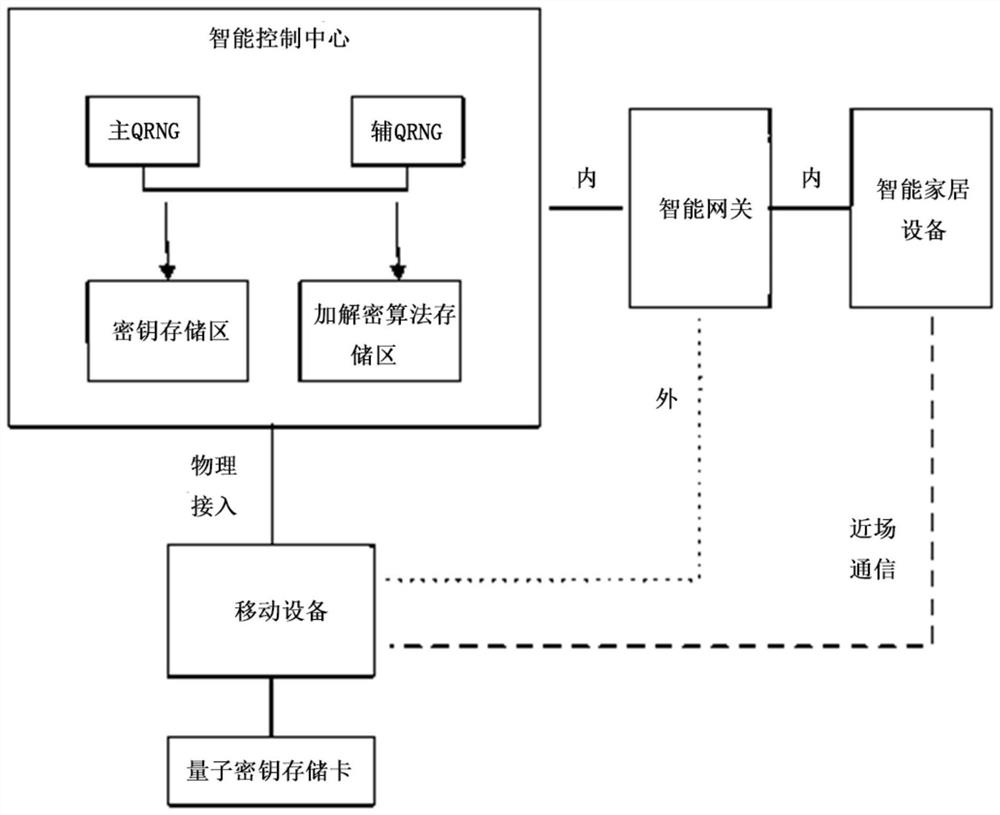
[0057] refer to figure 1 ,like figure 1 Shown is a schematic structural diagram of a smart home security communication system provided by this embodiment. The system specifically includes the following structures:
[0058] The entire installation consists of an intelligent control center (ICC), a smart gateway, smart home devices, mobile devices, and quantum key memory cards.
[0059] The intelligent control center is mainly composed of main QRNG (high-speed quantum random number generator), backup QRNG, key storage area, and encryption and decryption algorithm storage area. When the main QRNG works normally, a true random number is generated and packaged into a quantum key product and stored in the key storage area. When the working state of the main QRNG is abnormal, it switches to the standby QRNG to generate true random numbers. The encryption algorithm storage area is preset with encryption algorithms such as AES, RC4, and XOR encryption algorithms of one-time pad. Th...
Embodiment 2
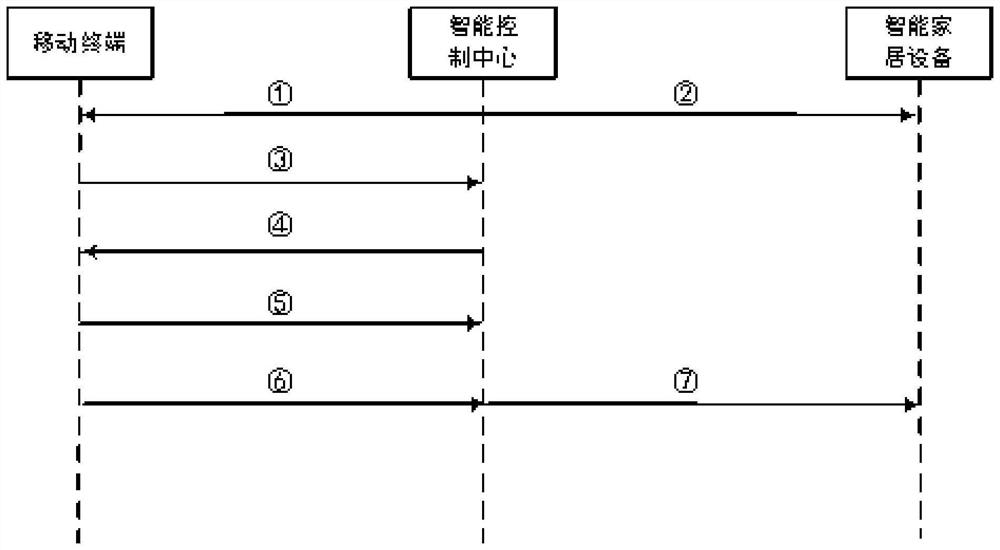
[0071] The specific working principle and process of the aforementioned smart home security communication system are divided into two scenarios, one is the scenario in which the mobile terminal communicates with the intelligent control center and then controls the smart home, and the other is the scenario in which the mobile terminal communicates directly with the smart home device through near field communication. Thereby controlling the scene of the smart home. This embodiment provides a scenario flow in which the mobile terminal communicates with the intelligent control center to control the smart home.
[0072] Before the instruction initiating terminal communicates with the smart home device through the control center, a registration step is also included, and the key storage medium and the smart home device are connected to the control center for registration;
[0073] The registration of the key storage medium includes: connecting the key storage medium offline to the c...
Embodiment 3
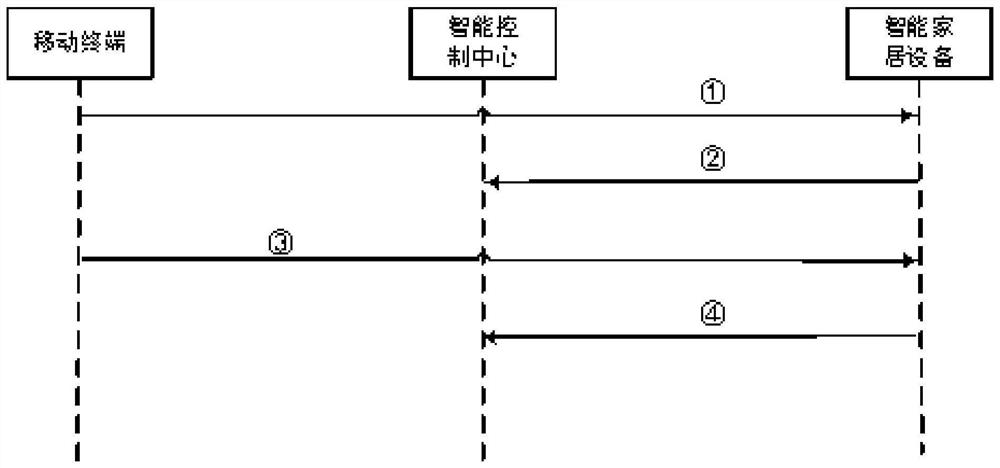
[0089] This embodiment provides a scenario flow in which the mobile terminal directly communicates with the smart home device through near field communication to control the smart home.
[0090] Before the instruction initiating terminal directly communicates with the smart home device through near field communication, a registration step is also included, and the key storage medium and the smart home device are connected to the control center for registration;
[0091] The registration of the key storage medium includes: connecting the key storage medium offline to the control center, injecting a certain number of authentication keys and transmission keys into the key storage medium according to requirements, and transferring the key storage medium to the control center. The physical hardware information of the user is registered in the control center, and the user's biometric information is entered in the control center.
[0092] refer to image 3 ,like image 3 Shown is a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com