Data interaction method and device, equipment and storage medium
A data interaction and data technology, which is applied in the field of communication security, can solve problems such as insecure data interaction, and achieve the effects of solving insecurity, improving security, and ensuring authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
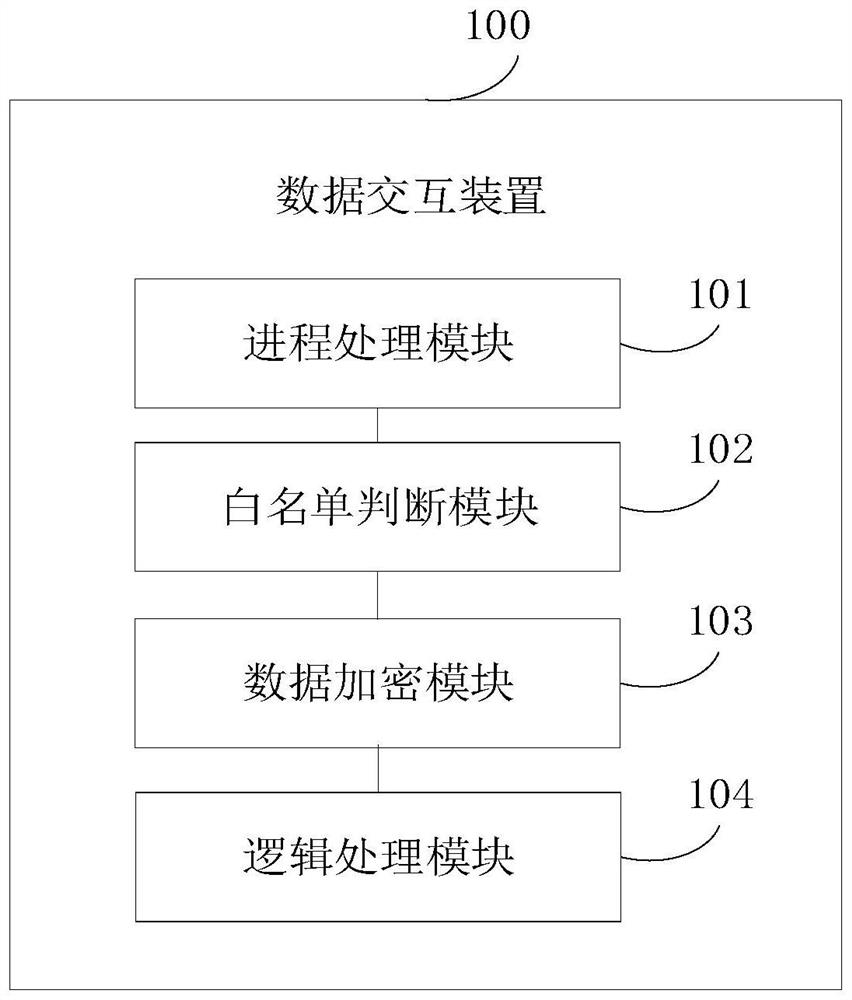
[0079] In detail, the specific implementation manner of each module of the data interaction apparatus 100 is as follows:
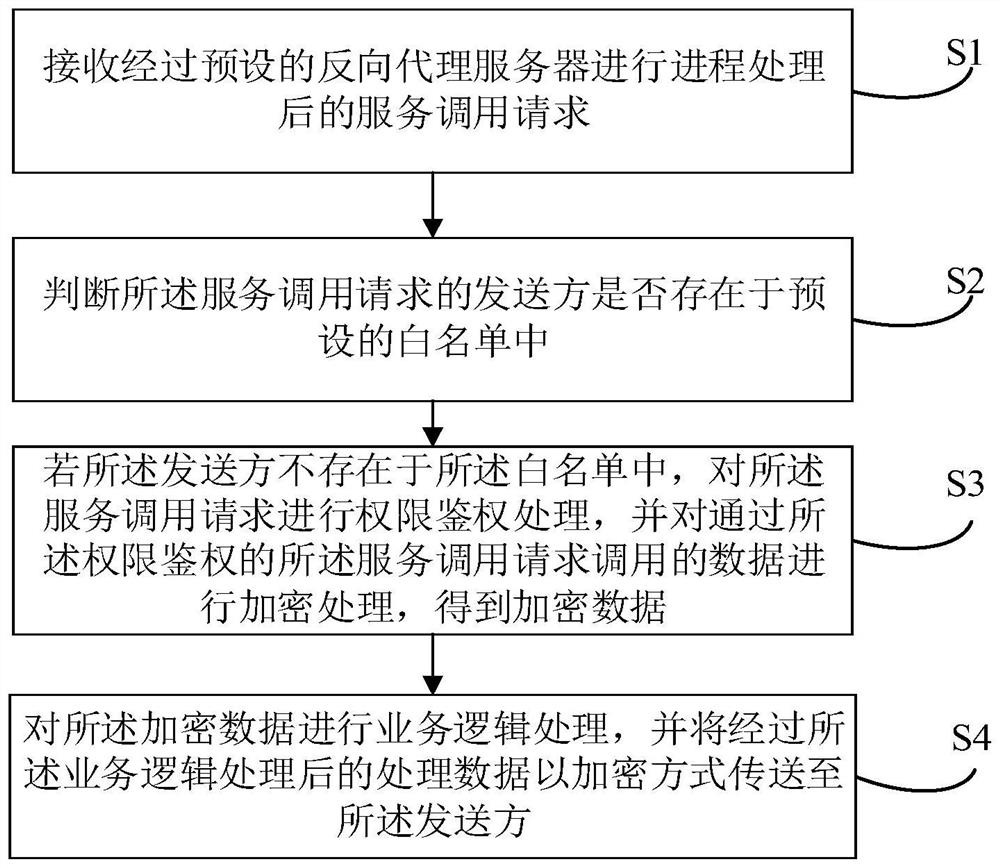
[0080] Step 1: Receive a service invocation request processed by a preset reverse proxy server.
[0081] In this embodiment of the present invention, the preset reverse proxy server may be Nginx, where Nginx is a high-performance HTTP and reverse proxy web server. Nginx can eliminate a single point of failure through load balancing, and has the advantages of achieving high availability and providing website scalability.
[0082] Specifically, before receiving the service invocation request processed by the preset reverse proxy server, the method further includes:
[0083] Acquire the main process in the reverse proxy server and multiple worker processes corresponding to the main process;
[0084] Utilize the main process to receive the request of the client, and perform parsing processing on the request to obtain the parsed and processed request;
[008...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com