Device for preventing setting of equipment of software be used or altered by non authorized person
A non-authorized, software technology, applied in the direction of preventing unauthorized use of memory, etc., can solve problems such as content theft, system operation status damage, high damage rate of hardware equipment, etc., to prevent fingerprint forgery, strengthen security, and high practicability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
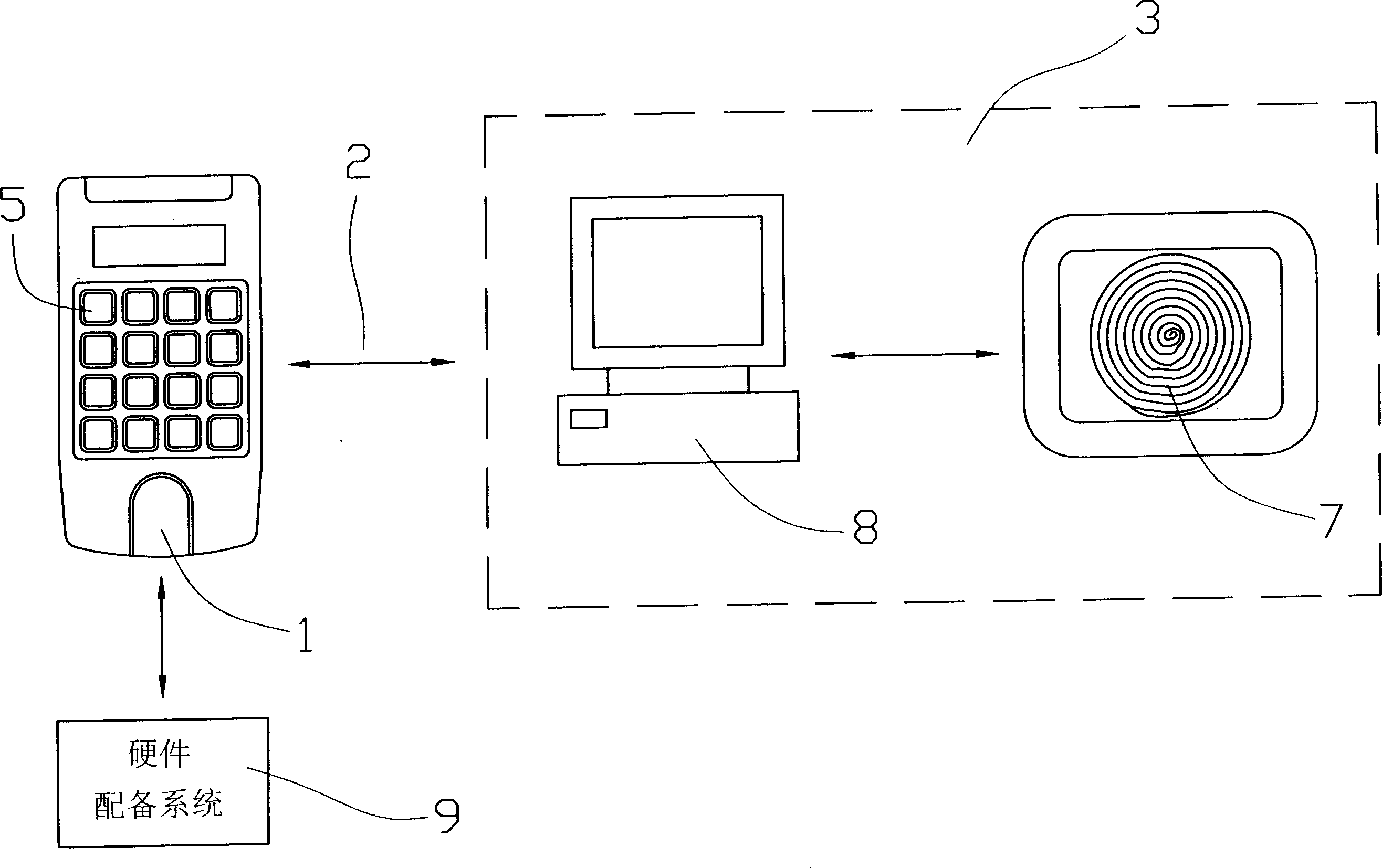
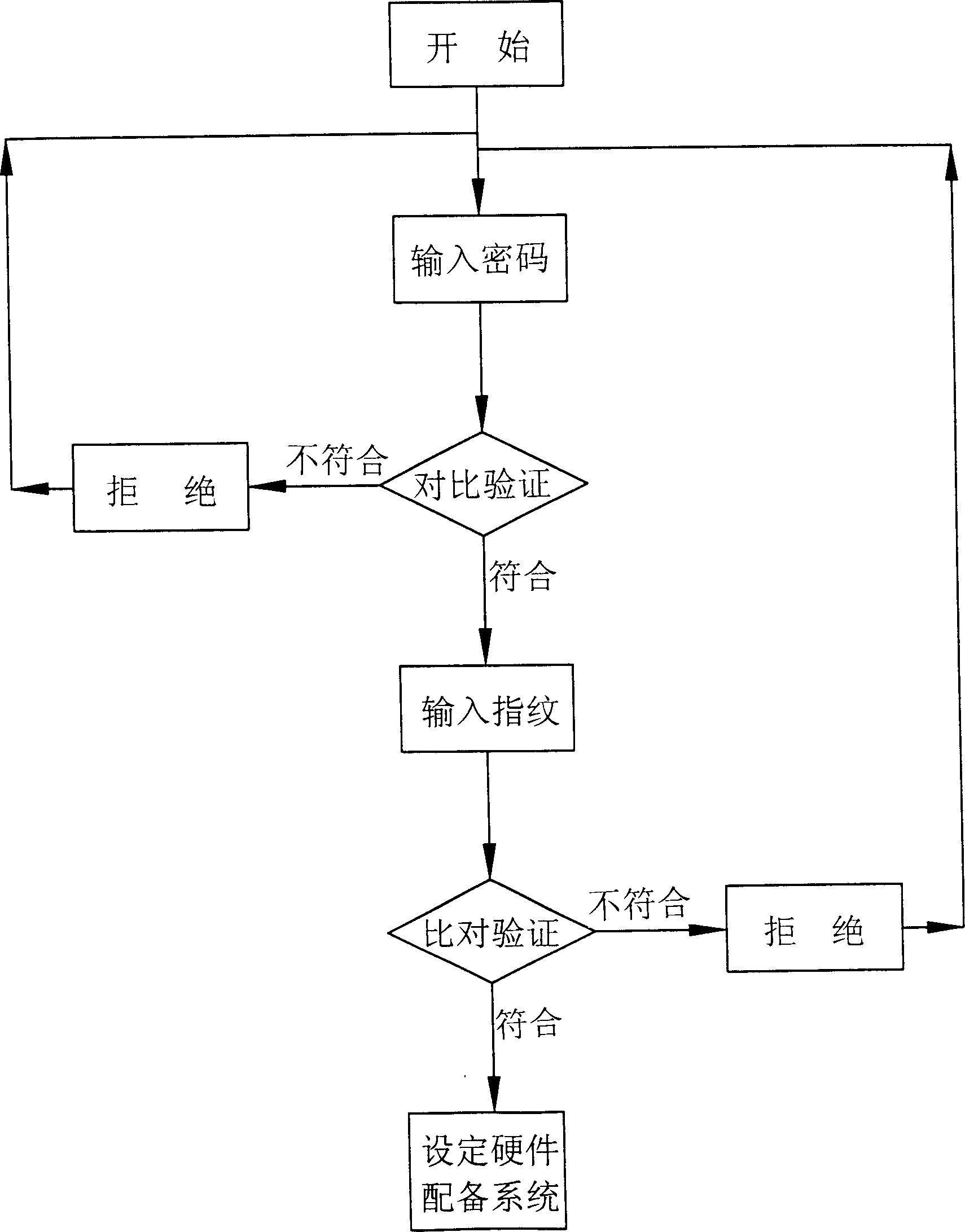
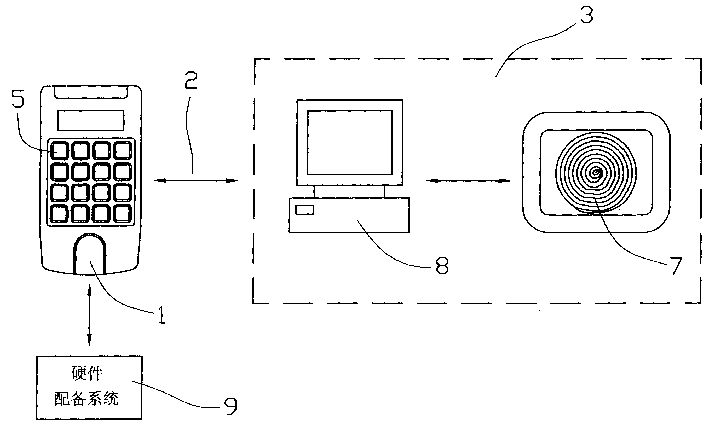
[0018] Such as figure 1 , figure 2 As shown, the present invention provides a device for preventing the settings in equipment and software from being used or changed by unauthorized persons, which can be used by a fingerprint image sensor 1, a password, a fingerprint feature database 8, and a password input unit 5, through fingerprint identification (Identification) or verification (Verification) technology, through the fingerprint feature data stored in the password, fingerprint feature database, and the fingerprint image sensor 1 live fingerprint feature 7 mutual comparison, at the same time Combined authentication method with password, and hierarchical authorization according to the hardware equipment 9, or the confidentiality level of the system, and operating habits to prevent unauthorized personnel from entering the security operation mode of the hardware device or the system, thereby preventing the device from being used, Or the settings in the software have been changed b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com