Method and device for realizing computer safety and enciphering based on identity confirmation
A technology of computer security and identity authentication, which is applied in the field of computers and information, can solve the problems of undisclosed motherboard BIOS system security and identity authentication, increase hardware costs, etc., and achieve the effect of not being easy to crack, improving security, and uniqueness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
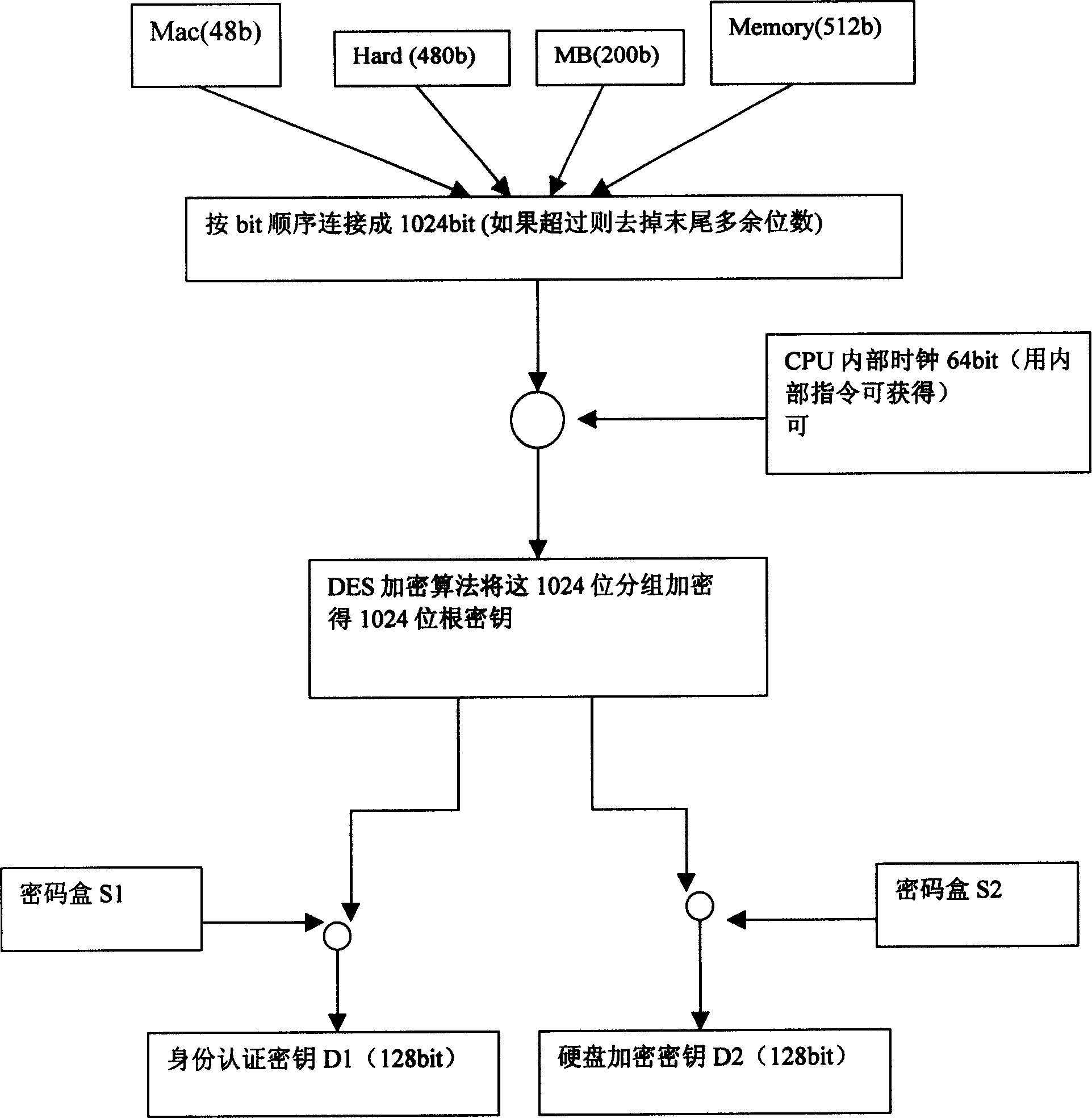
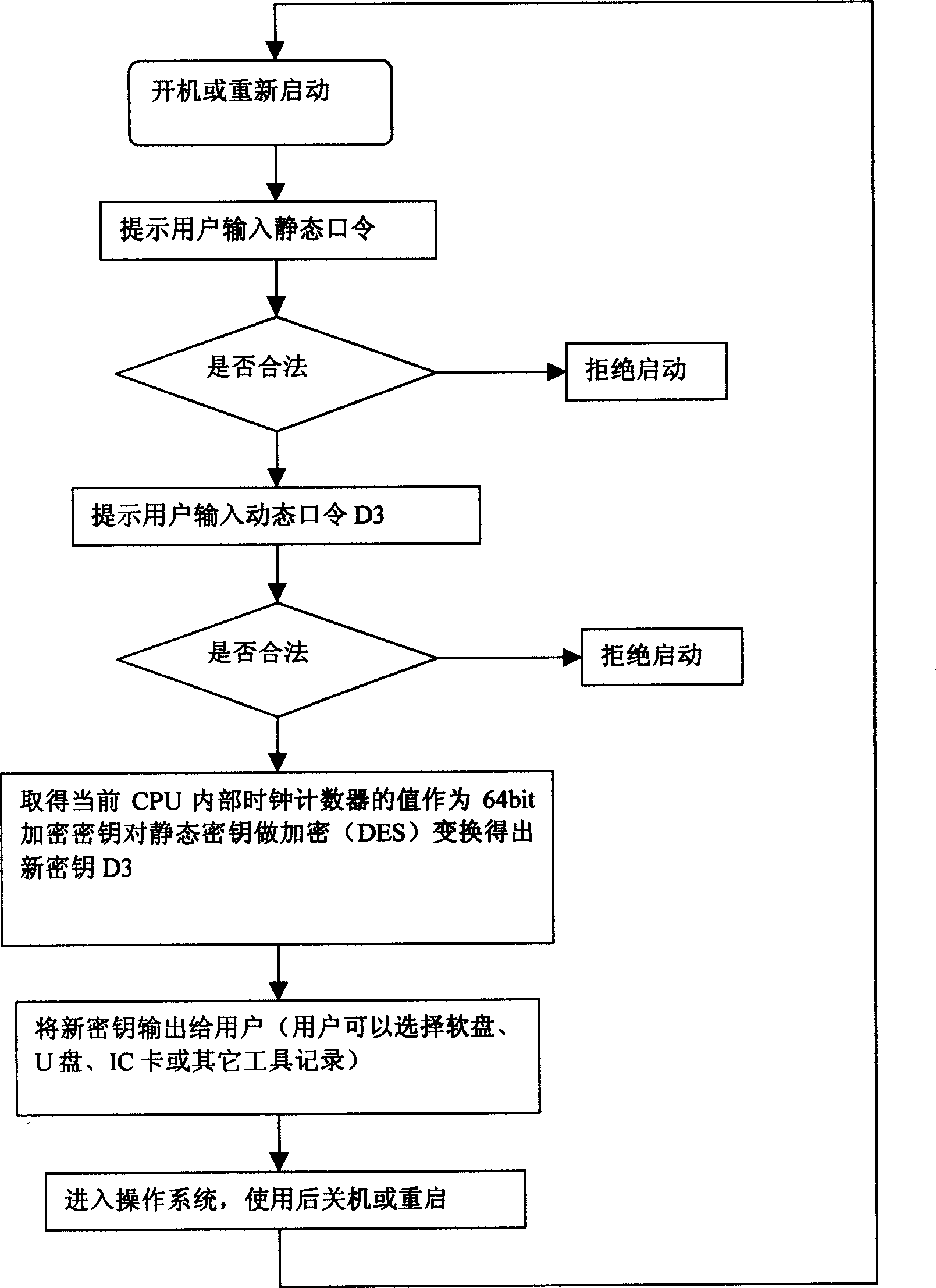
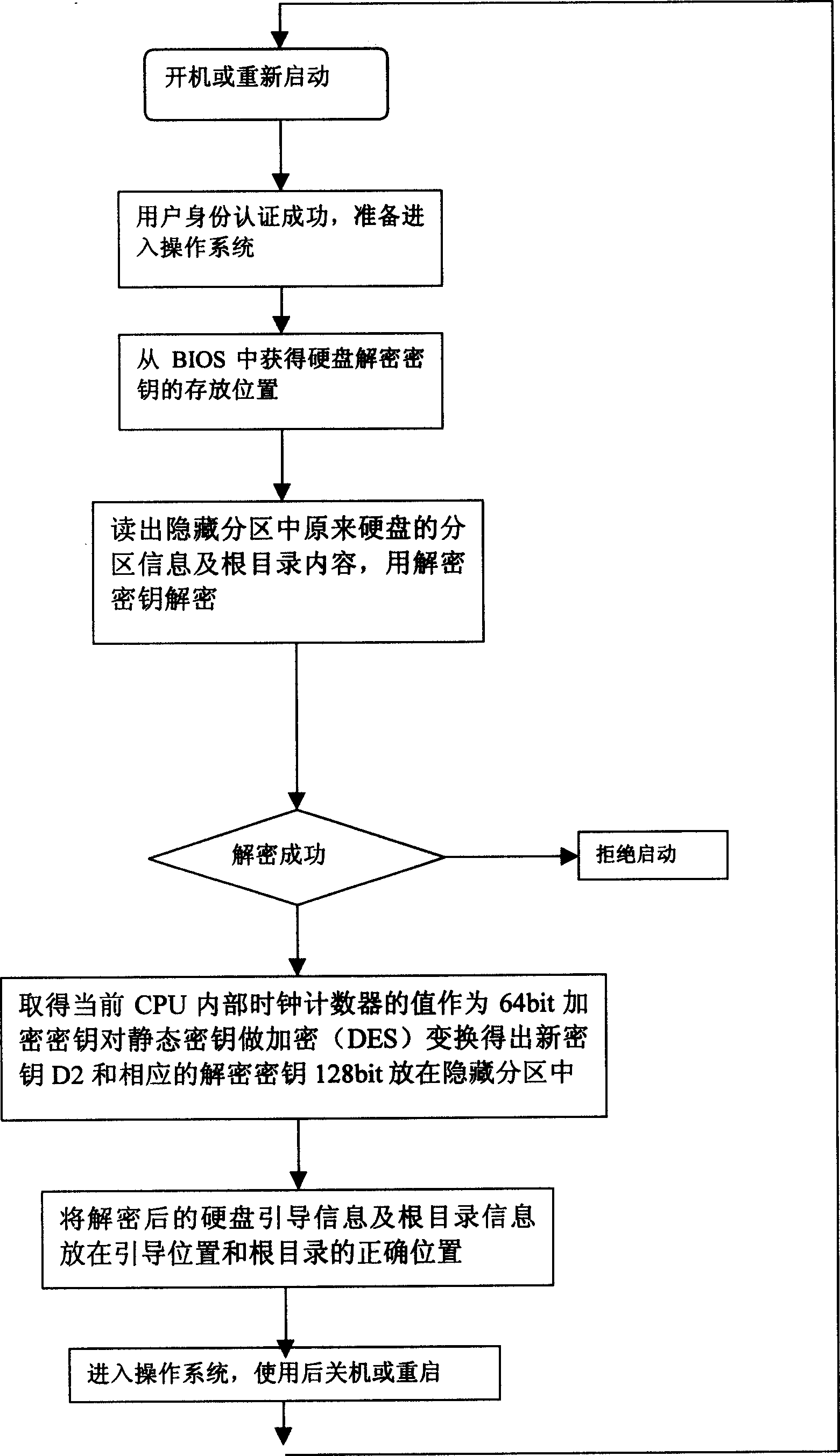
[0033] The device of the embodiment of the present invention comprises five functional modules of key storage, hardware security detection, identity authentication, encryption engine and hard disk encryption, wherein the encryption engine adopts DES (Data Encryption Standard, data encryption standard) and IDEA (IDEA: International Data Encryption Algorithm (International Data Encryption Algorithm) two algorithms, all are prior art, this paper does not describe in detail. The key storage is completed by the user and the system BIOS. If the key is fingerprint identification, there is no need to use other media to save the user key; The algorithm judges whether it is a legitimate user; the function of the encryption engine is to realize the encryption and decryption of the hard disk data
[0034] Implementation method and steps of the embodiments of the present invention:
[0035] (1) The user has his own key, and uses this key every time he starts, and the security module in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com