Method for processing extra-long message in two-layer virtual special-purpose network
A dedicated network and layer-2 virtualization technology, applied in the field of network transmission, can solve problems such as error fragmentation processing, unspecified application of layer-2 network transmission technology, frame discarding, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
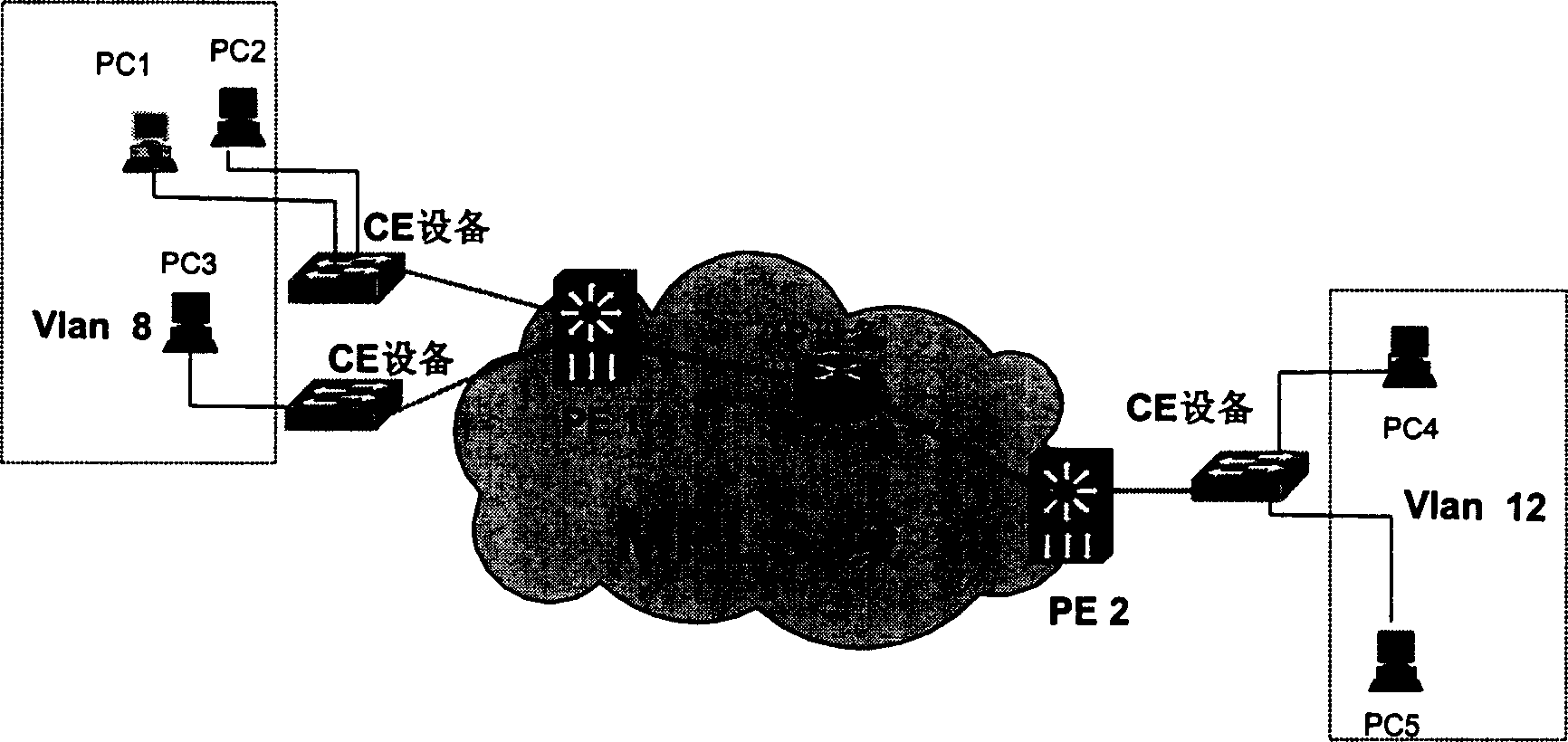
[0015] The following will refer to Figure 4 and Figure 5 Embodiments of the present invention will be described in detail.
[0016] In order to reduce the time-consuming fragmentation operation of the router and improve network efficiency, the current mainstream operating systems basically set the DF bit of the message when communicating on the network, and are ready to adjust their MTU value according to the situation at any time. The intention of the present invention is to utilize this feature, add an ICMP (Internet Control Message Protocol) on the PE equipment and actively adjust the MTU value of the host computer by using the protocol to respond to the ICMP message, so as to solve the problem of the L2VPN MTU value . Specific embodiments of the present invention will be described in detail below.
[0017] First, an ICMP protocol needs to be bundled on the PE device. The ICMP protocol is an existing three-layer protocol, not all in the L2VPN protocol. One of its most...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com