Mobile phone message security method
A security method and mobile phone information technology, applied in the field of mobile communication terminals, can solve problems such as loss of key information, inconvenience for users, and inability of users to handle information confidentially.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in further detail below through specific embodiments and in conjunction with the accompanying drawings.
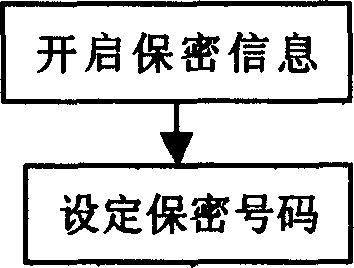
[0019] See figure 1 , first open the confidential information function, you can set or modify the password and set the secret number when it is turned on; the secret number can be added or deleted at any time. These secret code(s) form a secret code group.
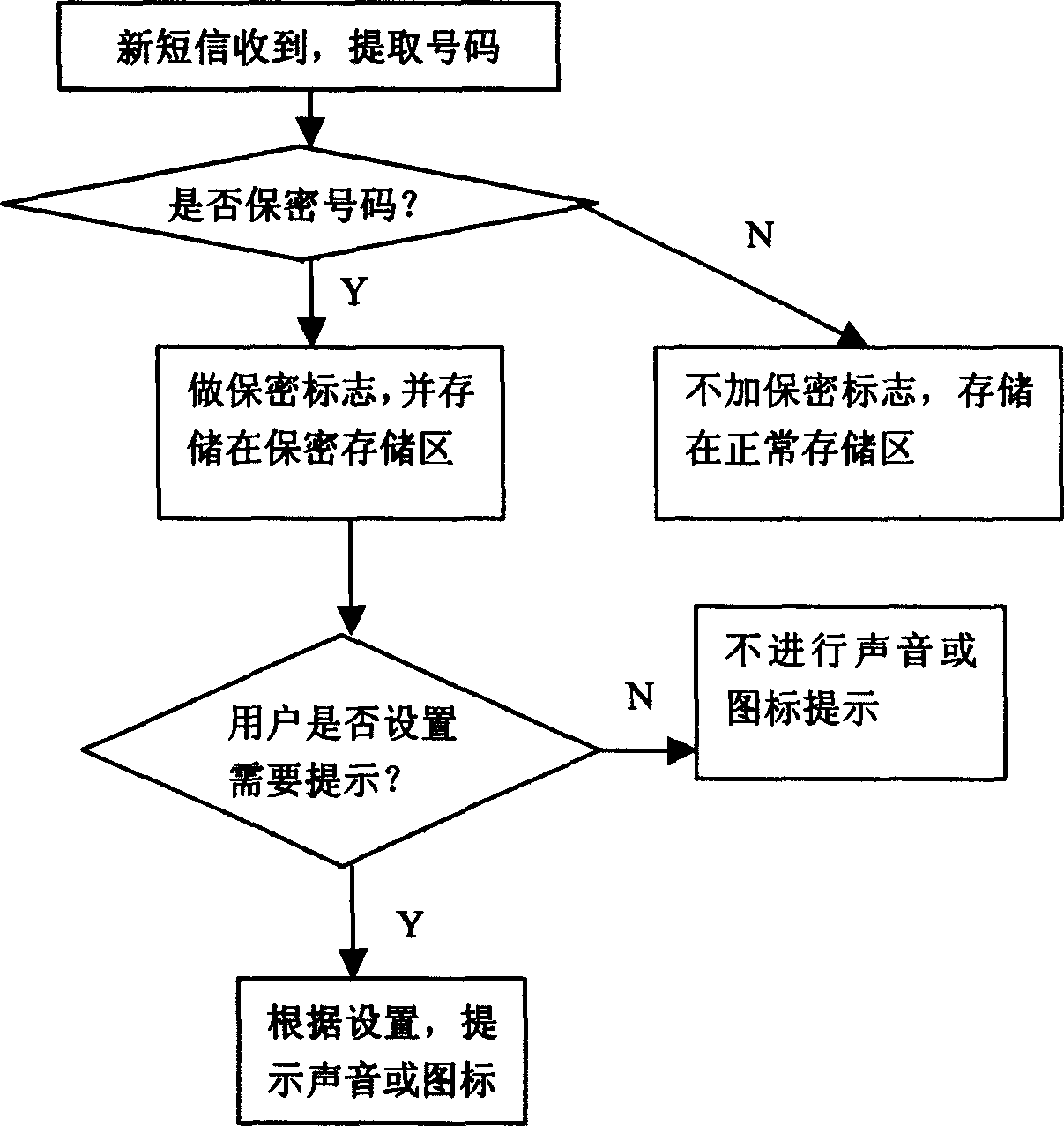
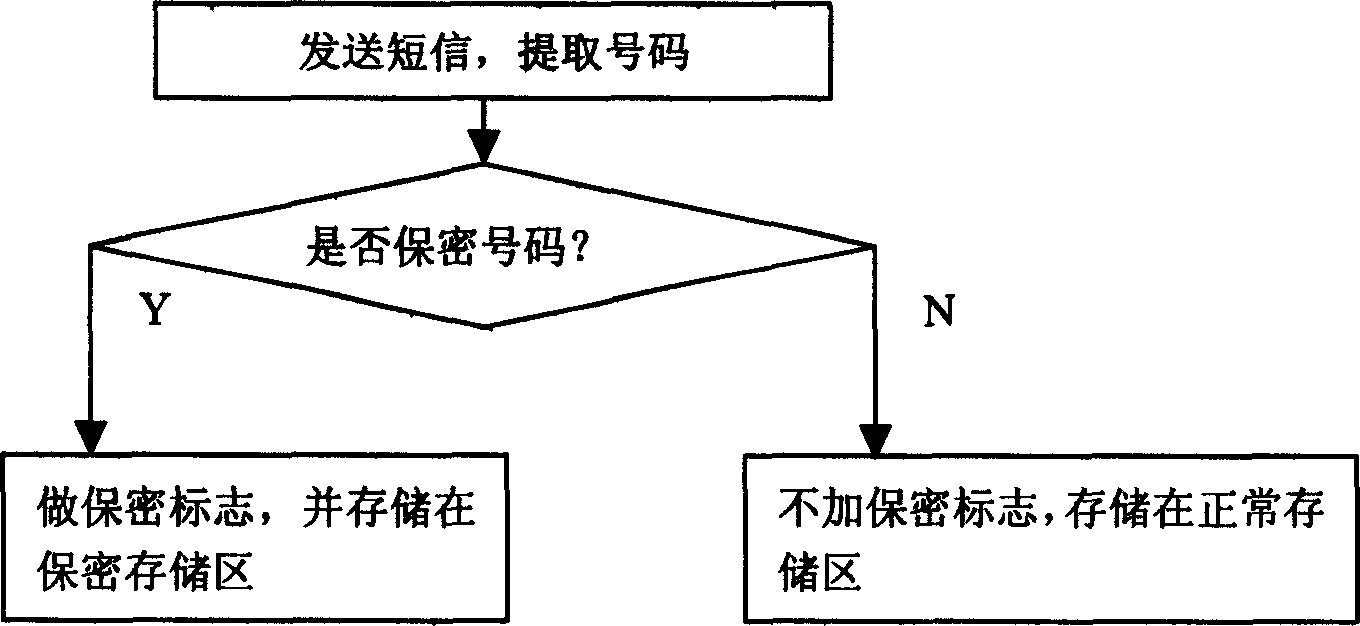
[0020] Such as figure 2 , 3 As shown, when sending and receiving short messages, compare the number of the sender and receiver, if it is a confidential number, then do special processing for this piece of information (make a confidentiality mark, and store it in a confidential storage area); if it is not a confidential number, then do General processing (no confidentiality flag, stored in the normal storage area). When receiving a text message, it is also necessary to decide whether to perform relevant prompts according to user settings. If so, then perform sound or / a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com