Intrusion detection method for host under Windows environment
A technology of intrusion detection and host, applied in the direction of instruments, electrical digital data processing, digital data processing components, etc., can solve the problem of inability to effectively judge abnormal intrusion of the system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be described in further detail below in conjunction with the accompanying drawings.
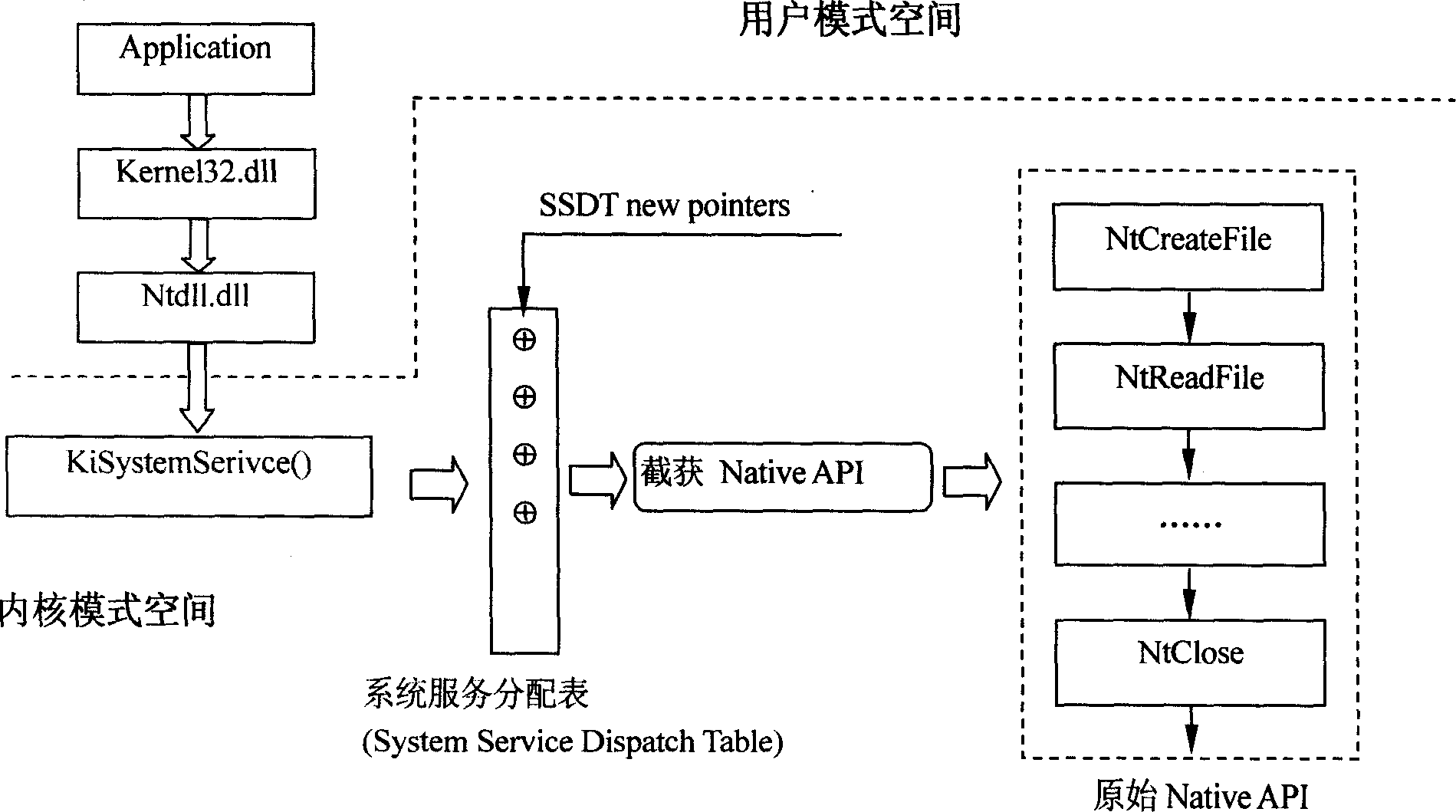
[0060] see figure 1 , when the application program in user mode, namely Application, is run, it will call the encapsulation function Win32 API in the dynamic link library Kernel32.dll, and the encapsulation function Win32 API in the dynamic link library Kernel32.dll will call the dynamic link library Ntdll The function encapsulated in the .dll actually calls the corresponding system service, and then calls the function KiSystemSerivce () to execute the interrupt INT 2E instruction to turn the processor CPU to the kernel mode and execute the handle specified in the interrupt description table. This handle will copy the parameter from the user-mode stack to the kernel-mode stack, and point the contents of the register EDX to the base address of the stack frame passed in the parameter. When the encapsulation function Win32 API called in the application program ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com