Bidirection control method for preventing fraudulent use of client end software
A client software, two-way control technology, applied in electrical components, security devices, radio/induction link selection and arrangement, etc., can solve the problems of illegal activation of client software, no guarantee that the software will not be stolen, loss of profits, etc. To achieve the effect of reducing the possibility of being stolen, reducing the possibility of being stolen, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
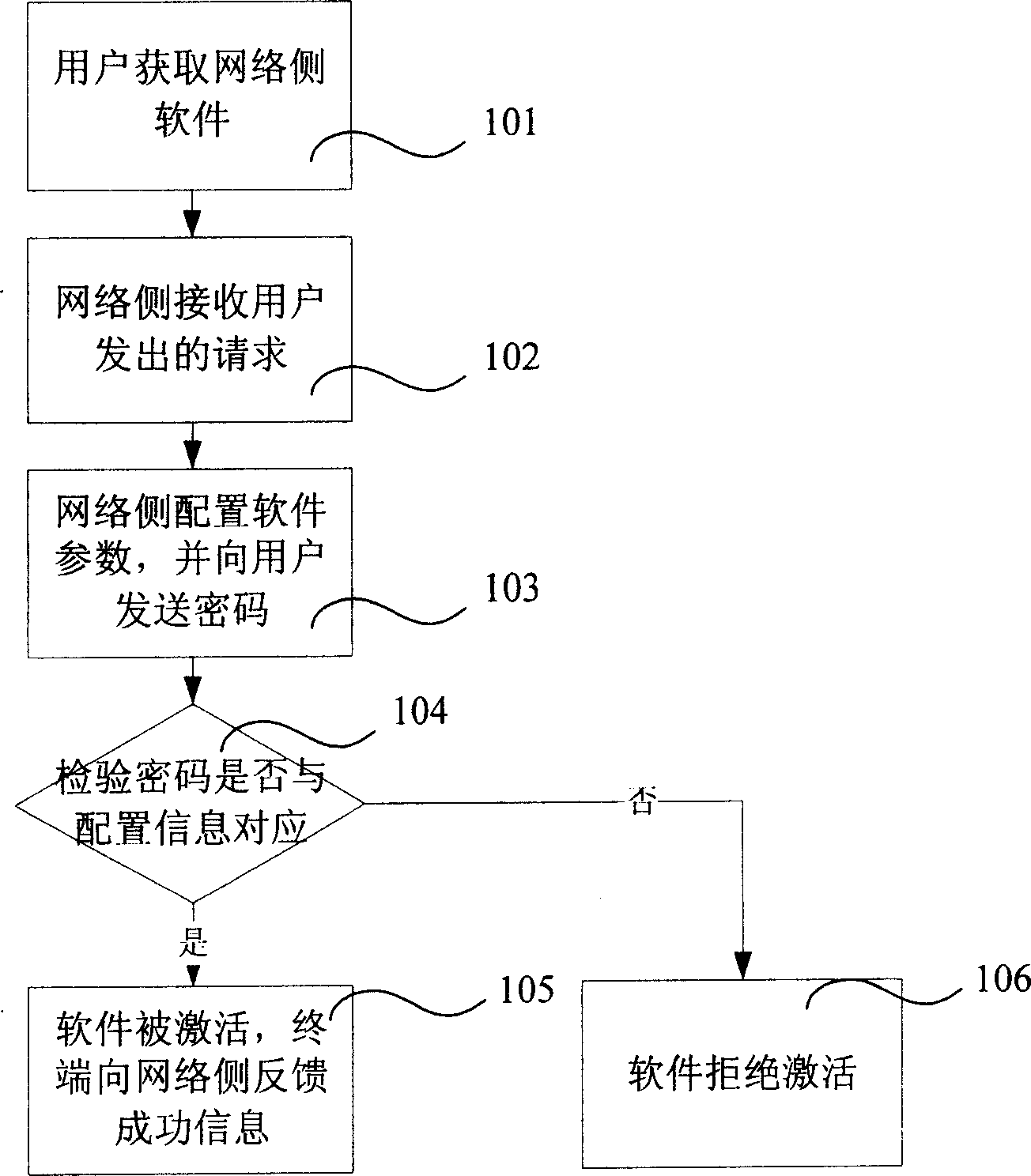
[0014] Such as figure 1 Shown is a flowchart of an embodiment of the present invention, including:
[0015] Step 101, the user obtains the client software provided by the network content provider on the mobile communication network side through WAP, and loads the client software into the user's mobile terminal.
[0016] In step 102, the user sends a request to activate the application service of the client software to the mobile communication network side through the telephone manual console.
[0017] Step 103, the mobile communication network side sends configuration information for the user number to the mobile terminal to configure the parameters of the client software, the mobile communication network side generates an activation password corresponding to the configuration information one-to-one, and sends an activation password to the mobile terminal via a text message. password. In this embodiment, the communication mobile network side targets the mobile phone number o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com