System and method for preventing software and hardware with communication condition/function against embezzlement
A technology of communication conditions, software and hardware, applied in transmission systems, wireless communications, digital transmission systems, etc., can solve the problems of unable to track and control mobile phone numbers, difficult to operate, data outflow, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
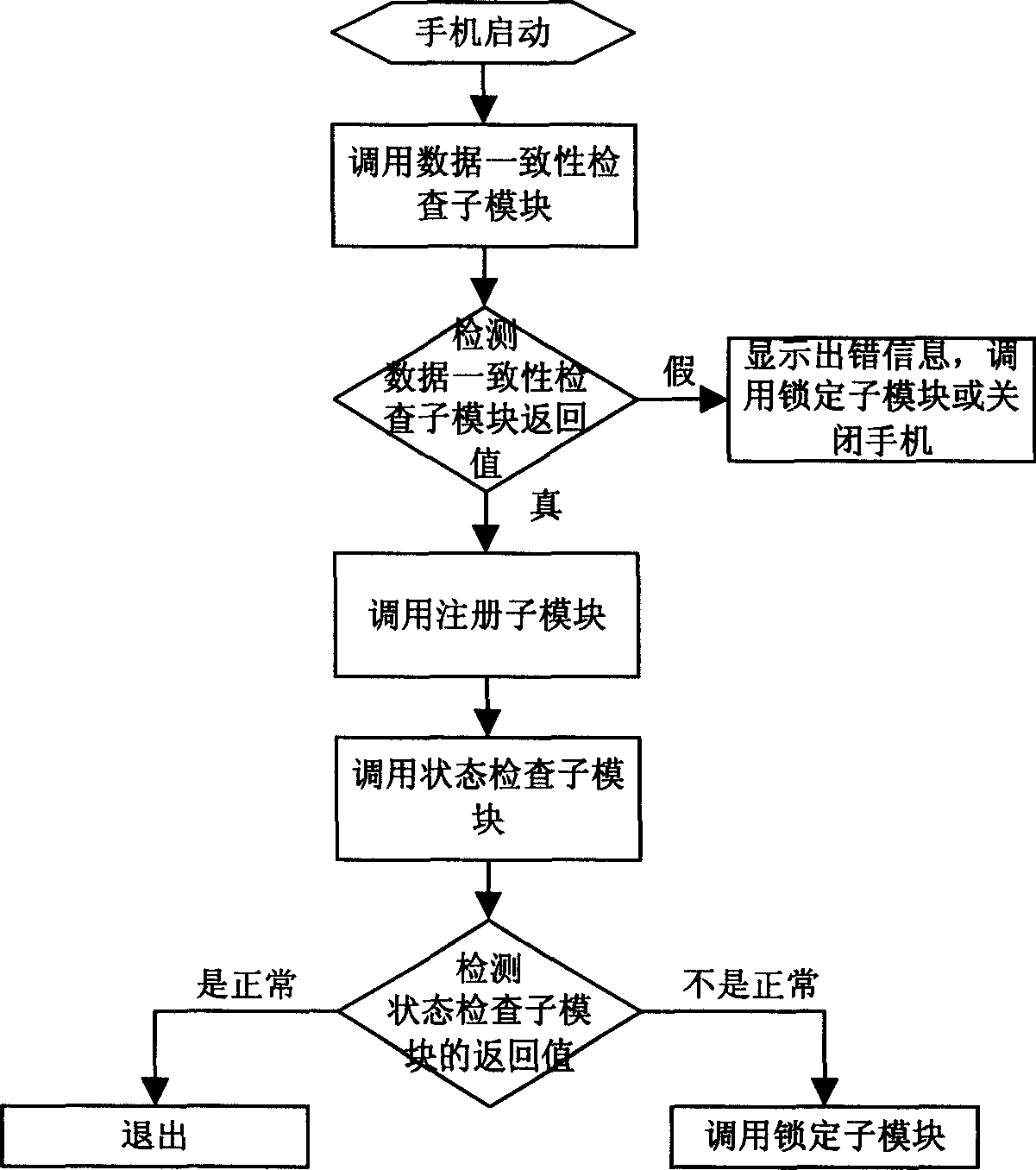
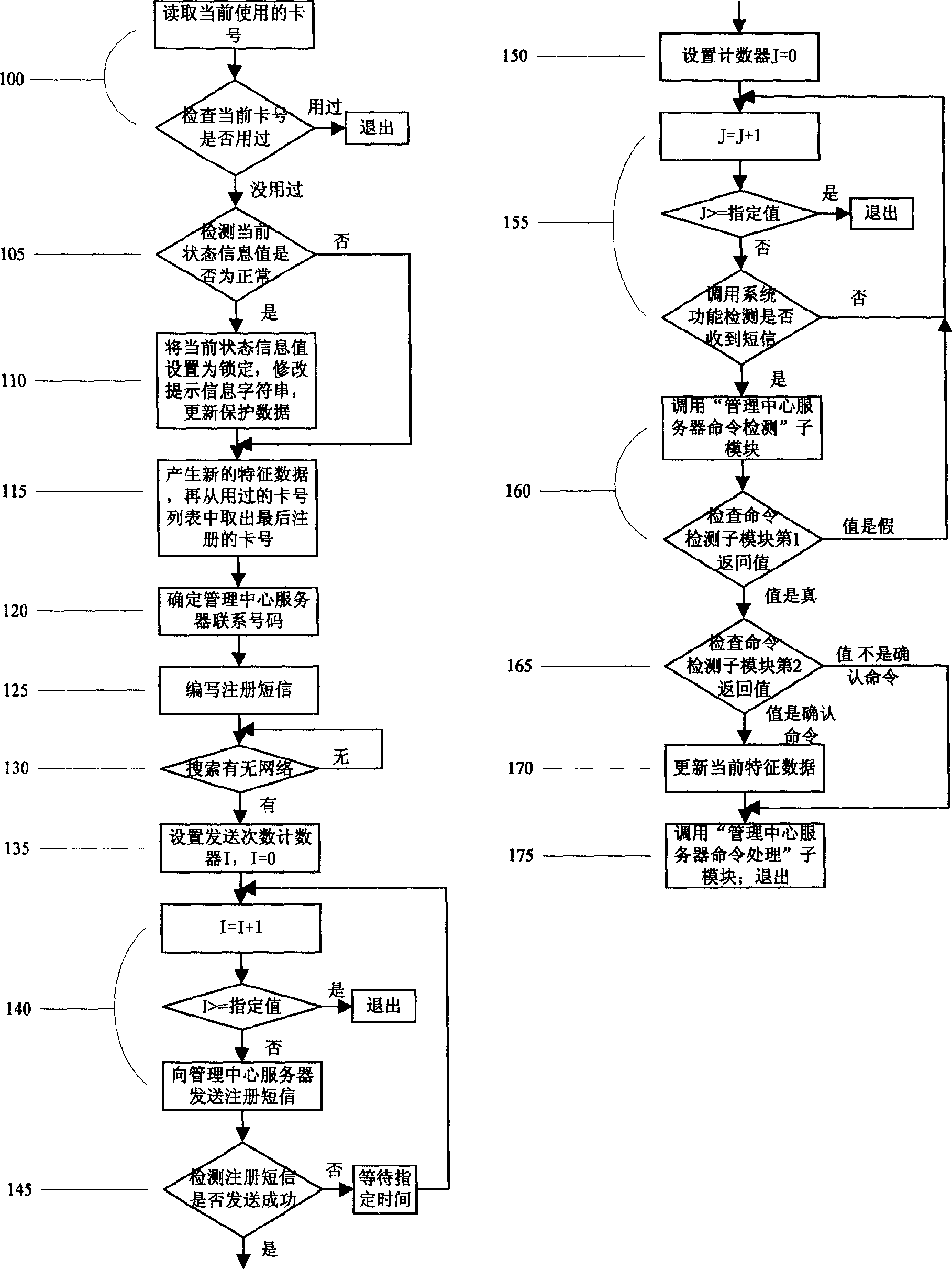
[0130] This embodiment provides an implementation of a mobile phone anti-theft, anti-counterfeiting, and anti-smuggling system and method.
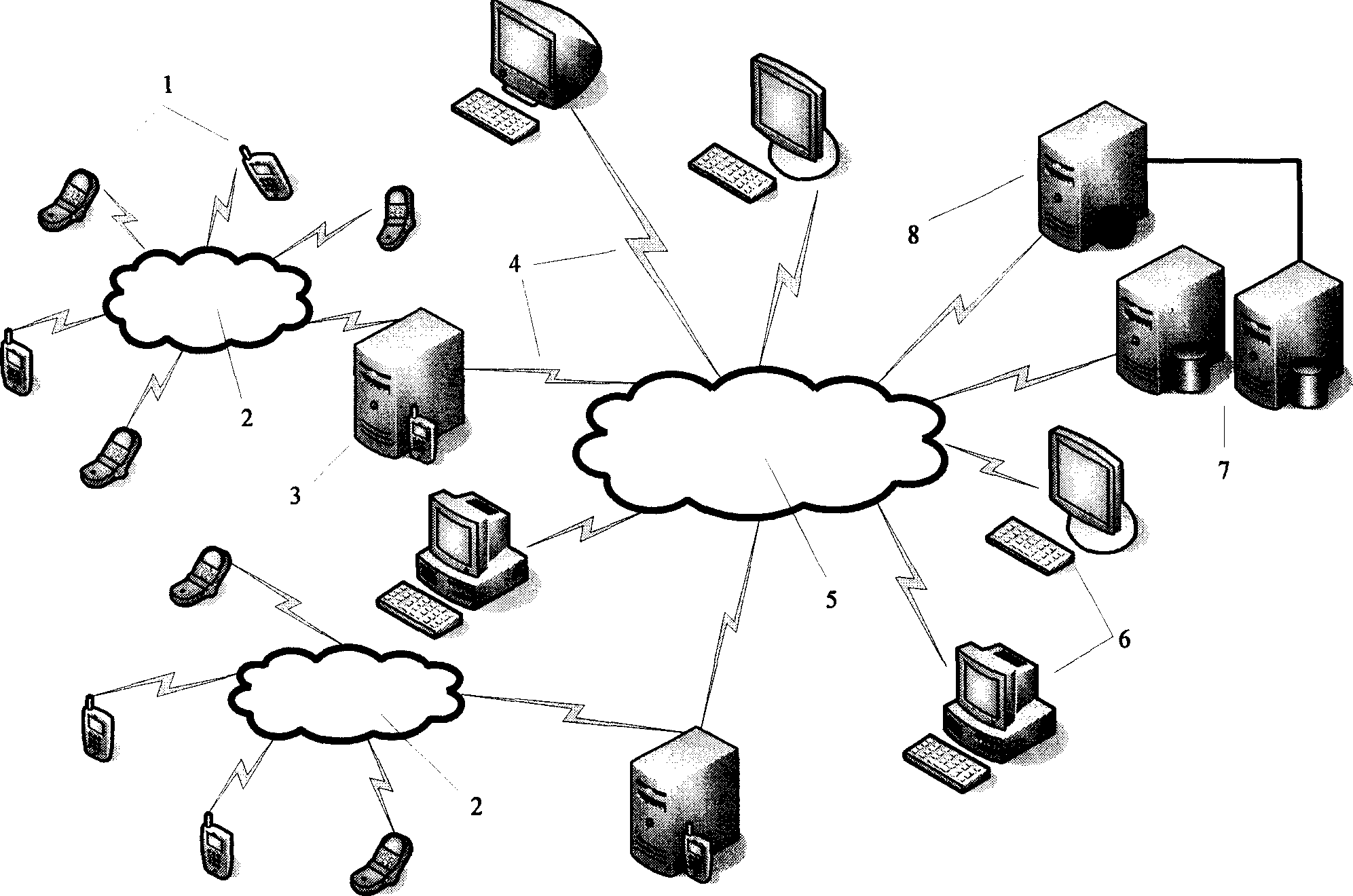
[0131] The system consists of mobile phone 1, GSM network 2, mobile phone SMS service center 3, communication link 4, INTERNET network 5, PC 6, management center server 7 and WEB server 8, and its topology is as follows figure 1 shown.
[0132] The mobile phone 1 is connected with the management center server 7 through the short message channel formed by the GSM network 2, the mobile short message service center 3, the mobile short message gateway and the INTERNET network 5, so as to realize the information interaction between the mobile phone and the management center server. WEB server 8 is connected with management center server 7 through local area network. Users and after-sales service personnel can operate the PC 6 to access the management center server through the INTERNET network 5 and the WEB server, and can report the loss of t...
Embodiment 2
[0257] This embodiment provides a system and method for preventing the SIM card number of a mobile phone from being stolen.
[0258] This embodiment is realized by adding corresponding functions to the existing SIM card of the mobile phone and the server of the mobile operator. The communication mode between the existing SIM card of the mobile phone and the server of the mobile operator is not changed.
[0259] In the database of the mobile operator server, organize the card number basic information data table with the anti-theft function into a new sub-database, or add the field "whether it is an anti-theft card number" in the original data table. Then add the "last successfully dialed phone number" field in the card number basic information data table.
[0260] Use STK technology to develop the SIM card of the mobile phone, and save a character string at a specified location on it, whose value is the last successfully dialed phone number, or a specified substring in the las...
Embodiment 3
[0266] This embodiment provides an anti-piracy method for software that requires a server to provide a certain service.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com