Safety grade arranging method
A technology of security level and algorithm, applied in the field of communication and information security, which can solve the problem of indeterminate algorithm, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
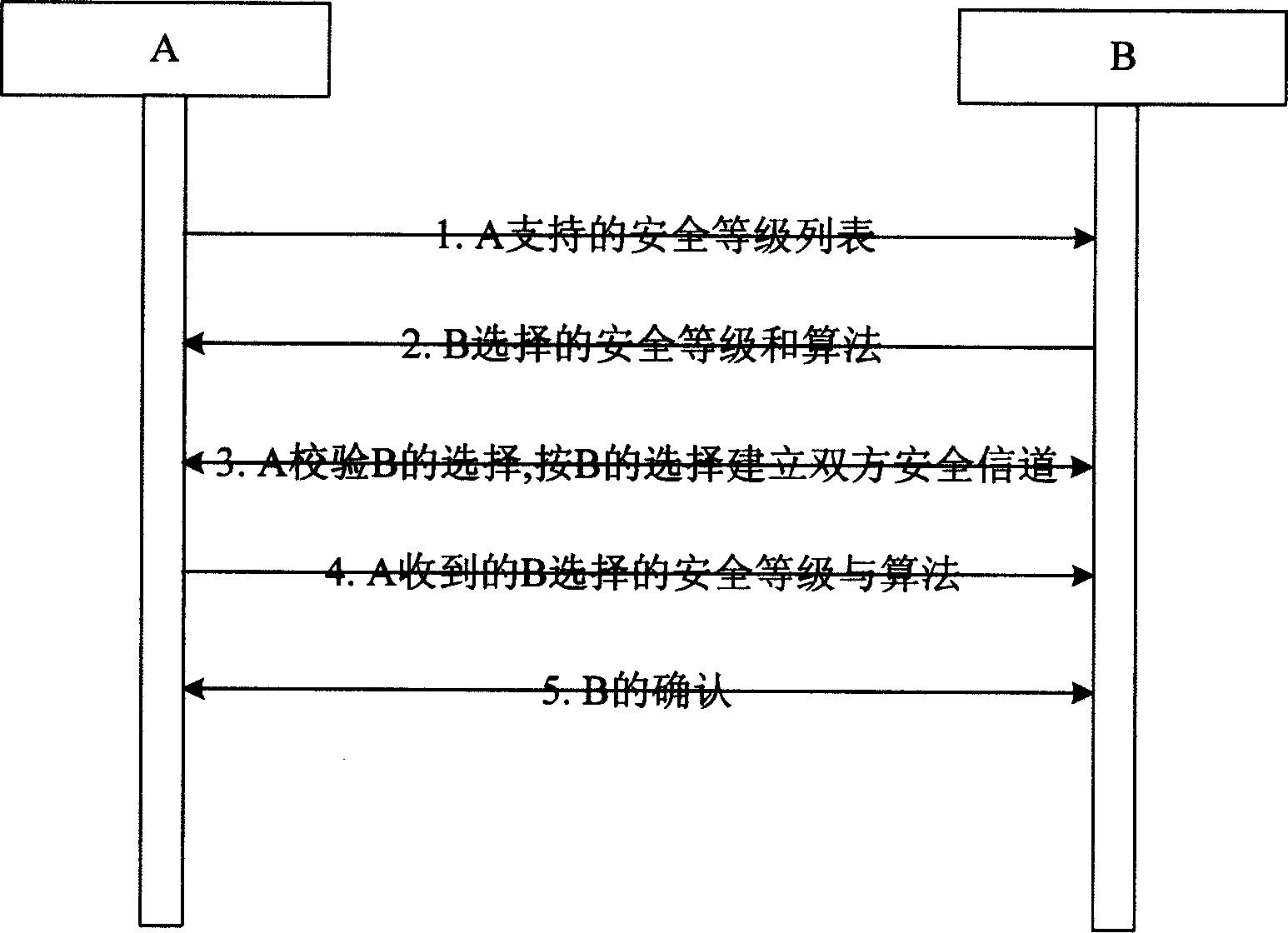
[0015] Such as figure 1 As shown in the method flow of the present invention, it is assumed that entities A and B carry out security level negotiation, A is the calling party, and B is the called party, and the negotiation process specifically includes the following five steps:
[0016] In the first step, A sends the list of security levels it supports to B;
[0017] In the second step, B compares the list sent by A, and B selects the highest security level and its algorithm parameters among the security levels supported by both parties and sends it to A;
[0018] In the third step, A checks whether the received choice of B is in its own list, and if it is correct, A establishes a secure communication channel between the two parties; otherwise, the negotiation fails;
[0019] In the fourth step, A uses the opened secure channel to send back the received choice of B to B;
[0020] In the fifth step, B verifies the choice of B sent by A. If it is confirmed that it is the origi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com