Method and system for accessing critical region
A critical area and priority mark technology, applied in the field of data communication, can solve problems such as unsatisfied
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
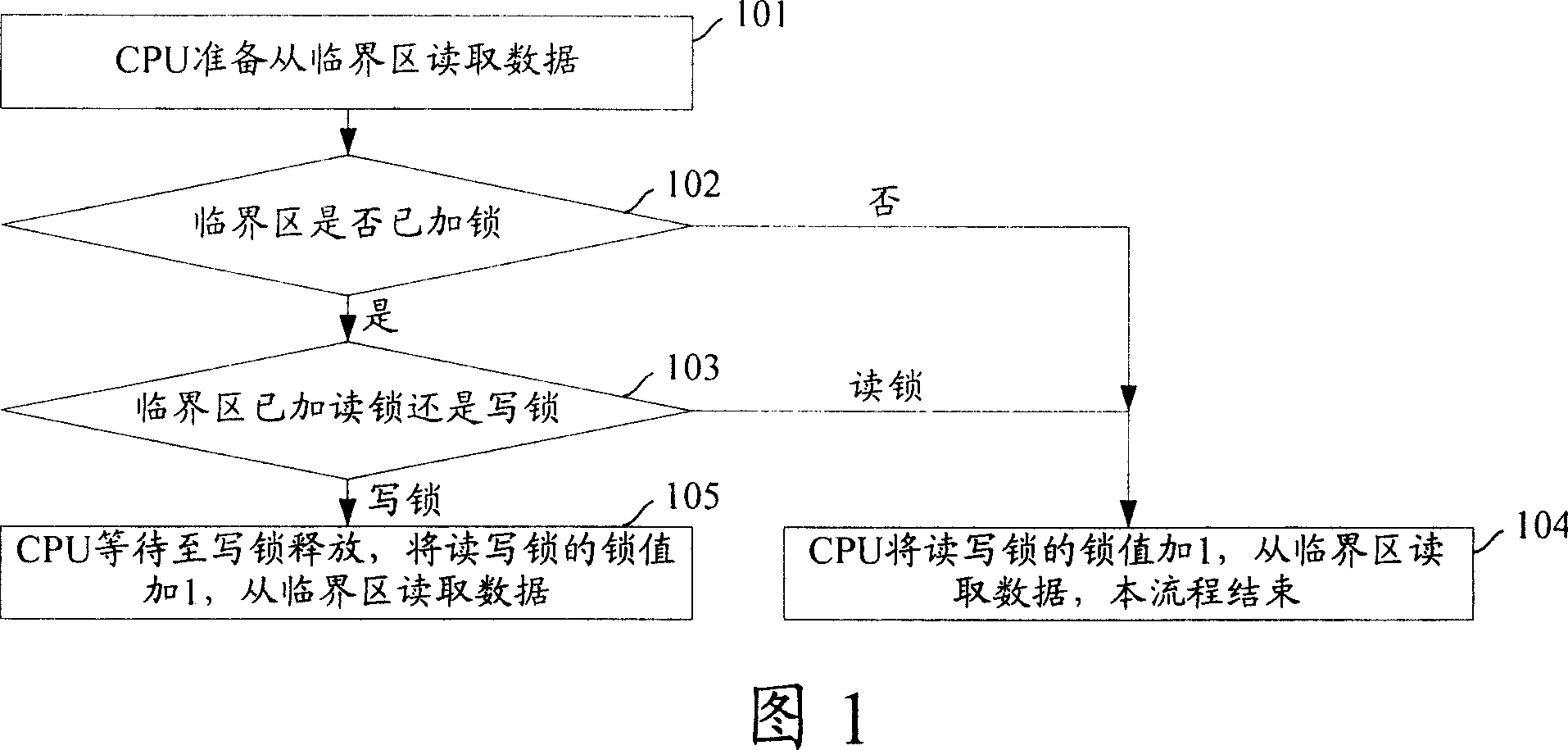
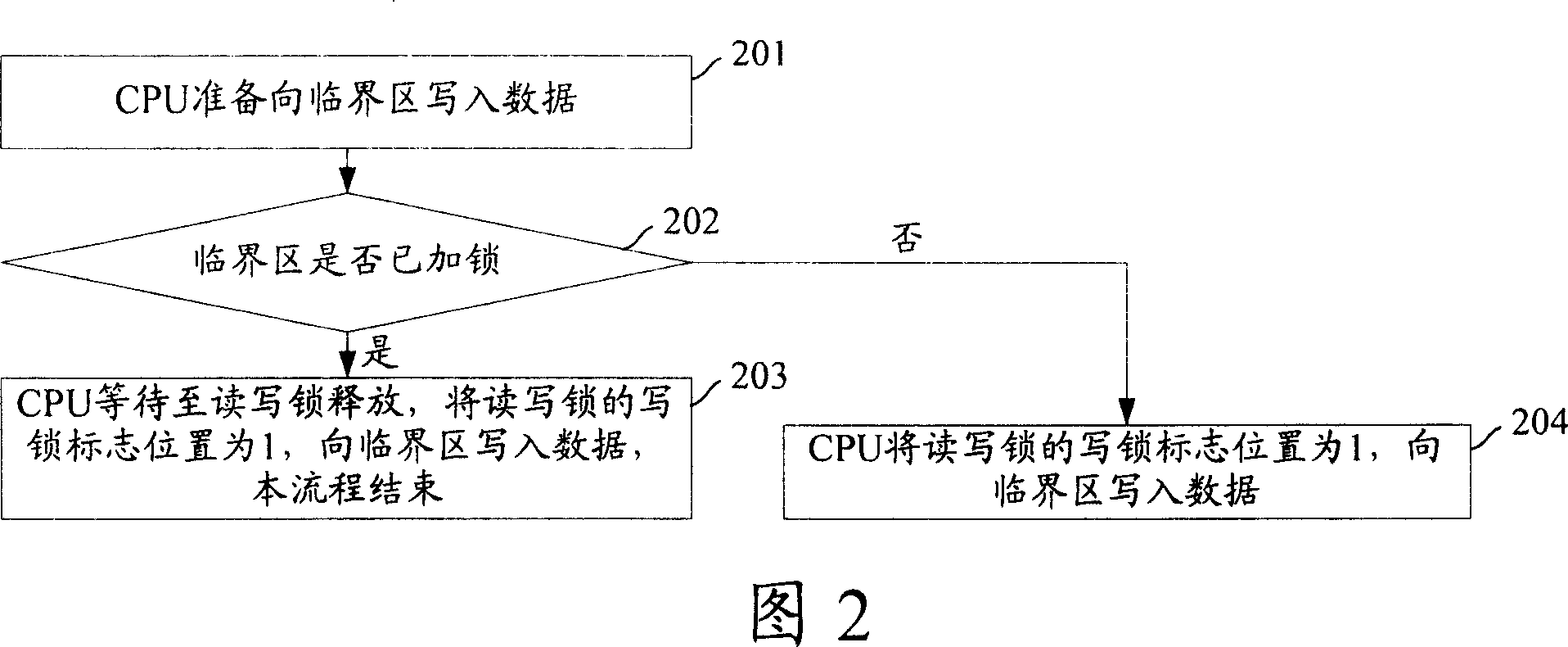
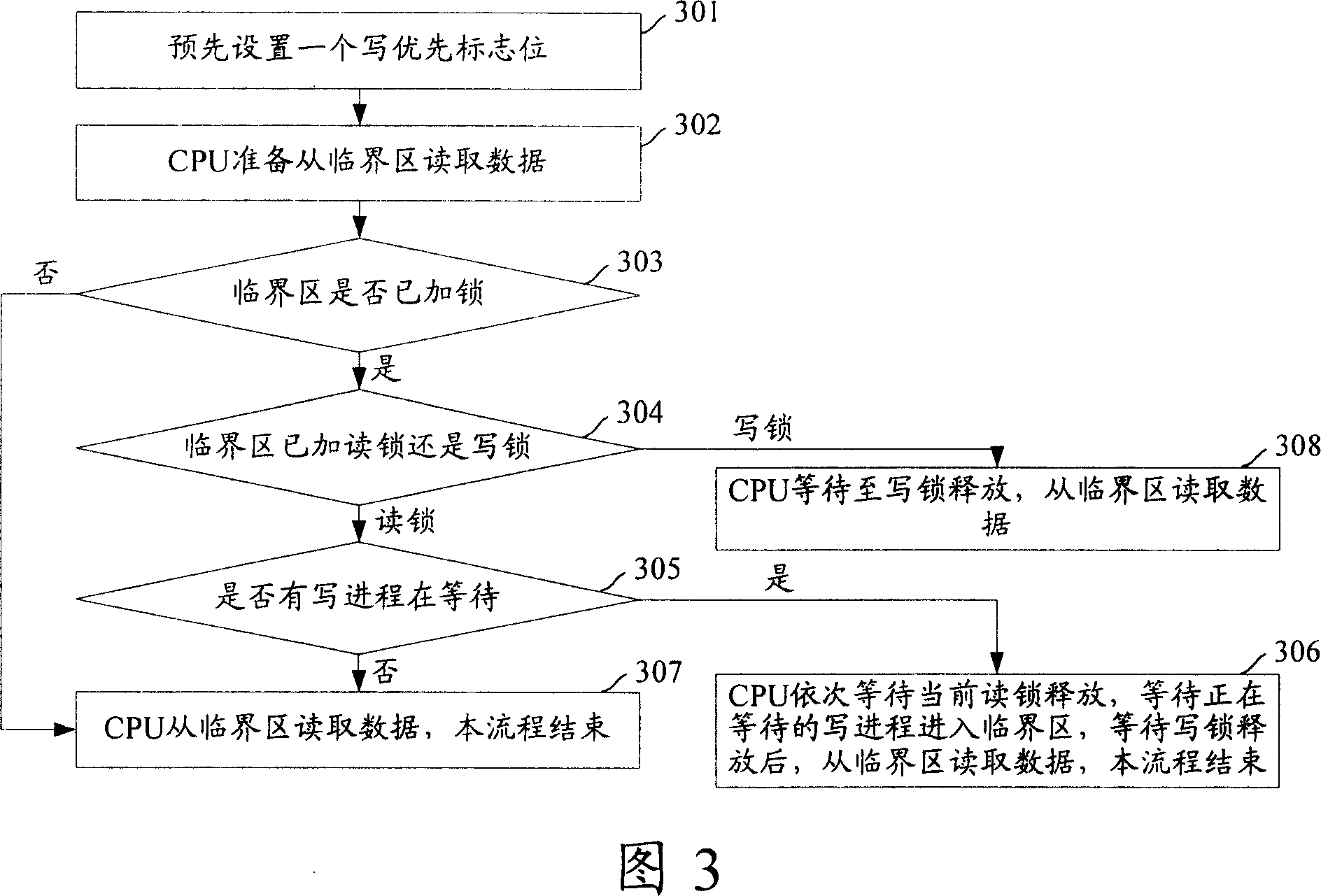
[0057] Fig. 3 is a flow chart of reading data from a critical section in a multi-core system provided by an embodiment of the present invention, as shown in Fig. 3 , the specific steps are as follows:
[0058] Step 301: Presetting a write priority flag bit for indicating whether there is currently a write process waiting to enter the critical section.
[0059] For example: for MIPS supporting Linux, the 14th bit of the read-write lock can be set as the write priority flag. When the write priority flag is 1, that is: when the value of the read-write lock is [0x4000, 0x7FFF], it means The writing process is waiting. If there is a reading process waiting at the same time, the writing process should enter the critical section first.
[0060] Or, besides the read-write lock, a write-priority flag bit can be set independently, and the valu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com