Method of realizing intelligence cryptographic key set of fingerprint for multiple users to use
An intelligent key device, multi-user technology, applied in computer security devices, instruments, digital data authentication and other directions, can solve the problems of low utilization rate of fingerprint intelligent key device and less authority levels, etc., to improve flexibility and reduce user costs. Cost, Ease of Use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
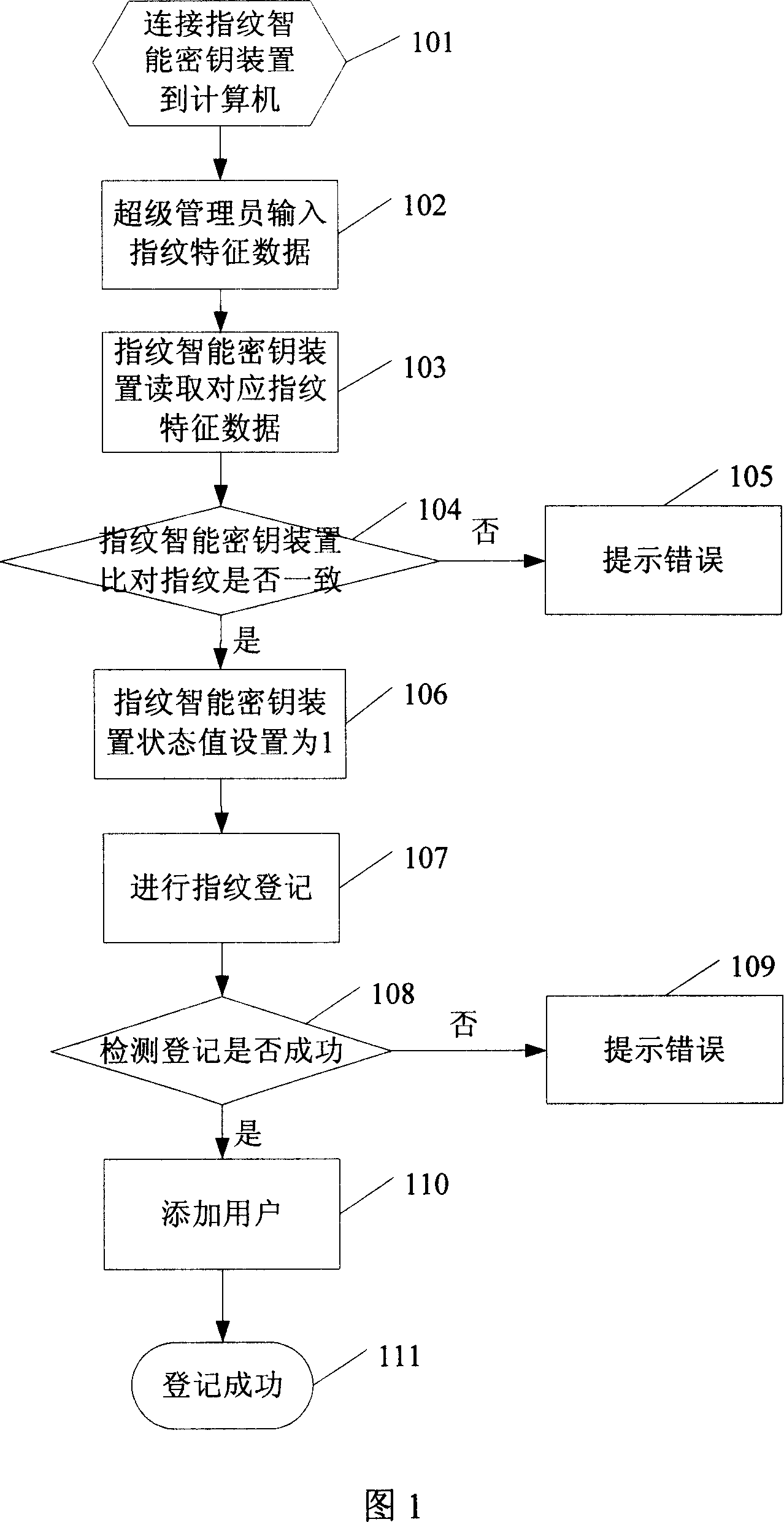
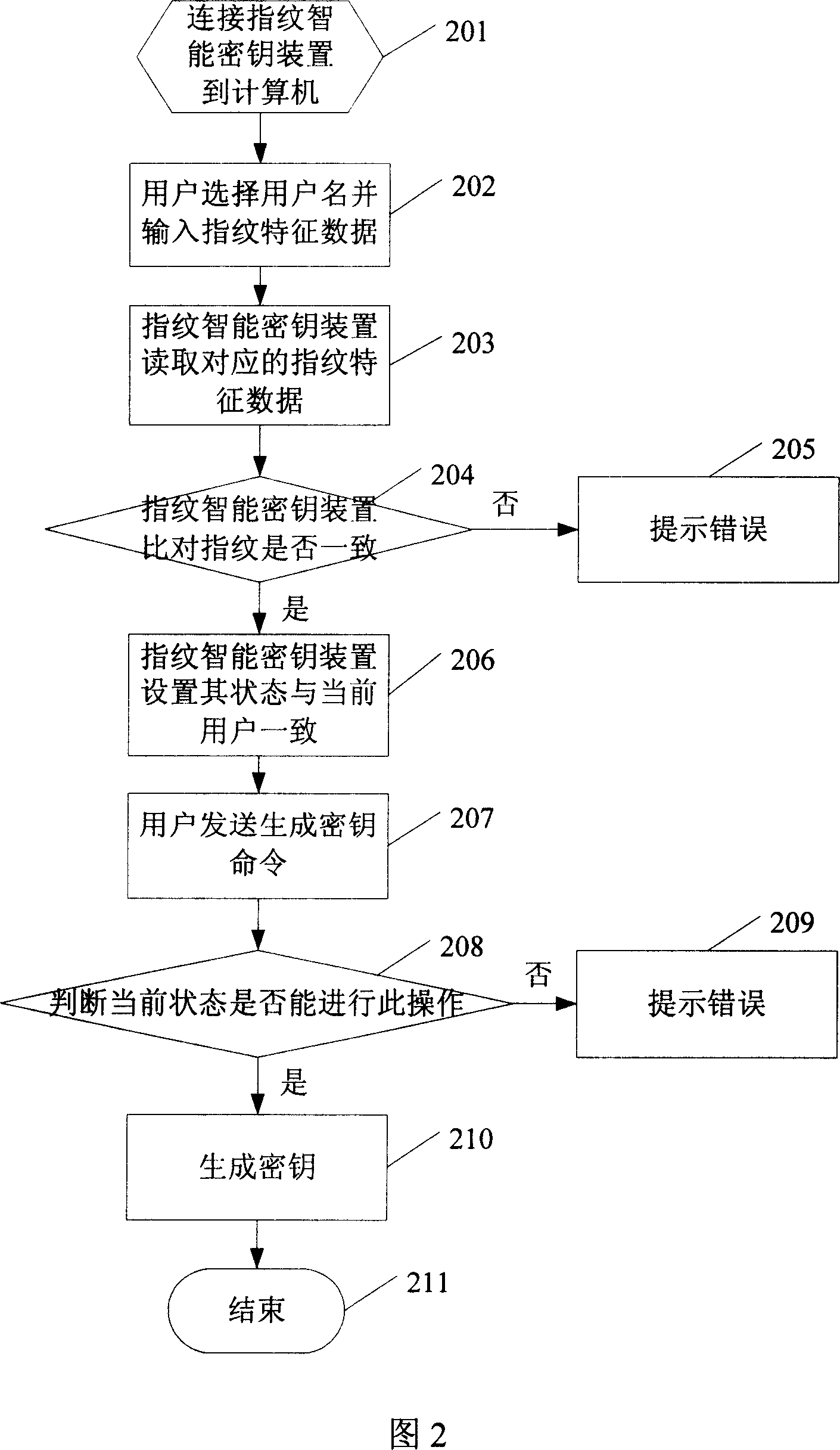
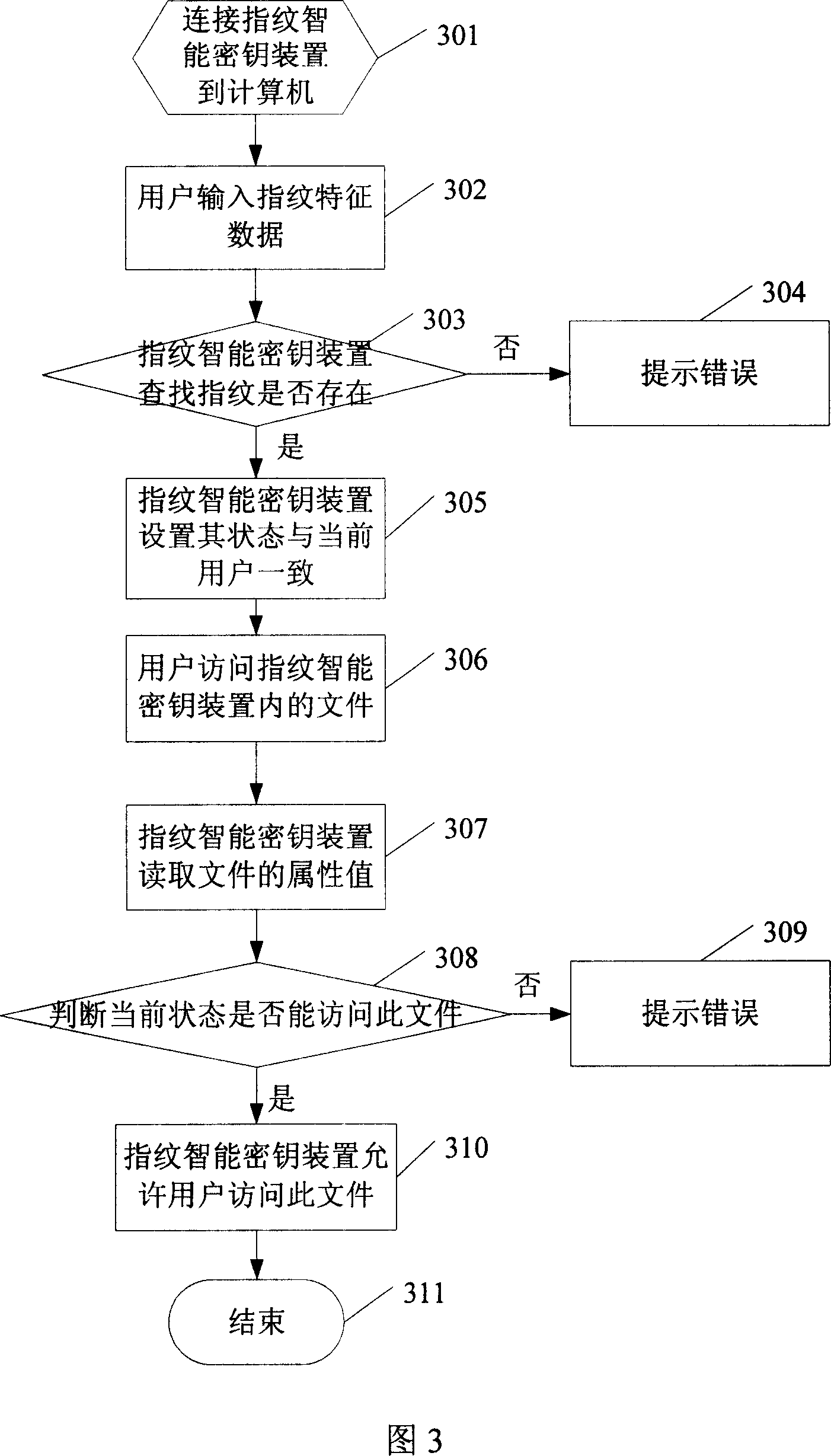
[0019] The system and method of the present invention will be described in more detail below with reference to the accompanying drawings and specific embodiments.
[0020] A part of the area is divided in the memory of the fingerprint smart key device for storing the user list. The user list includes items such as user ID, user name, user authority value, and user fingerprint feature data. Wherein, the user ID represents the serial number of the user, and generally the user IDs are numbered in descending order according to the registration order of the users, and each of them is different. During fingerprint registration, the system automatically assigns a user ID to each user in sequence. The user name is the name of each user. Generally, the user names of each user in the same fingerprint smart key device are different. When registering fingerprints, the user can set a character string as his user name as required. The user authority value refers to the authority level whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com