User authentication system, method, program, and recording medium containing the program
A technology of user authentication and authentication system, which is applied in the field of user authentication to achieve the effect of convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
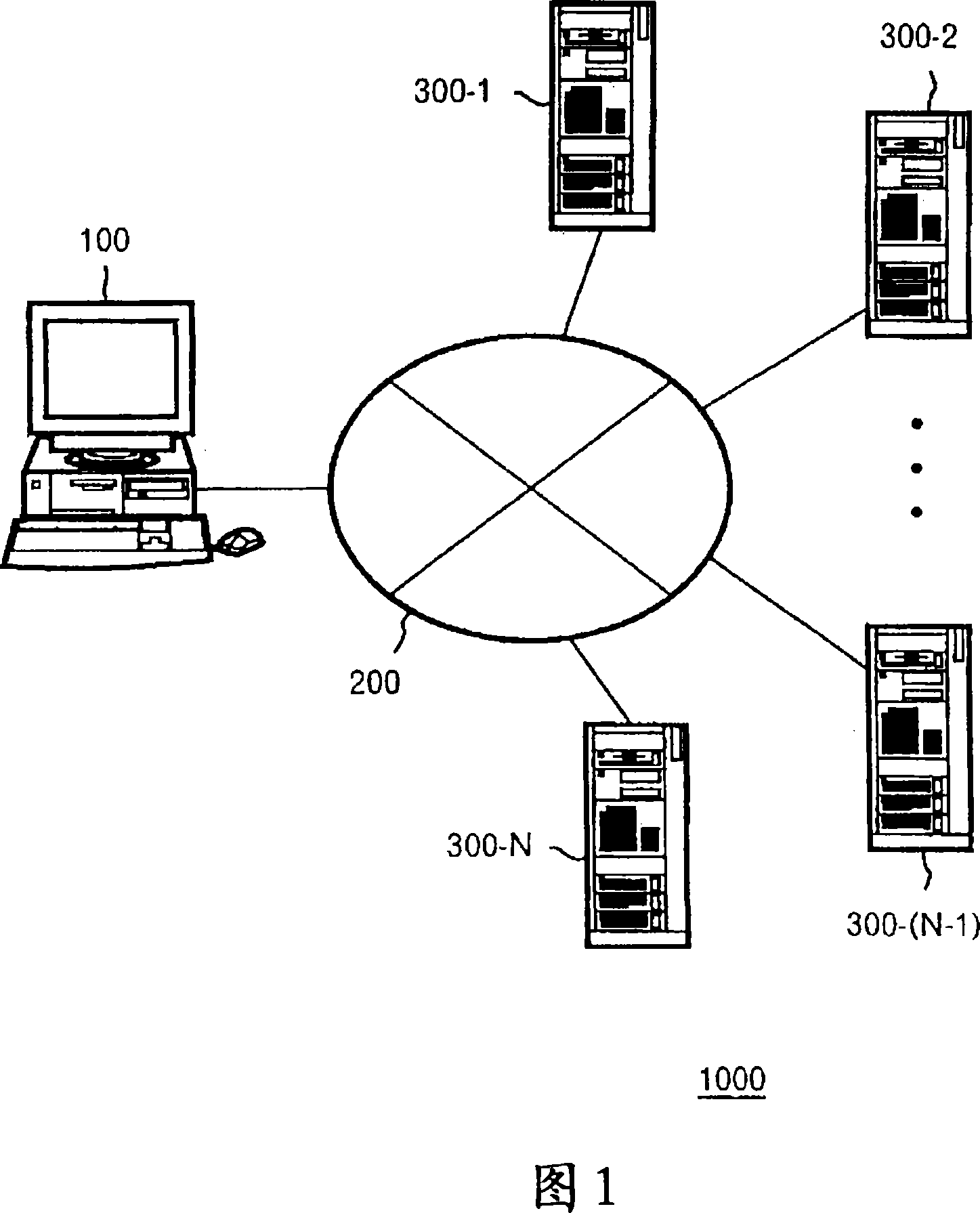
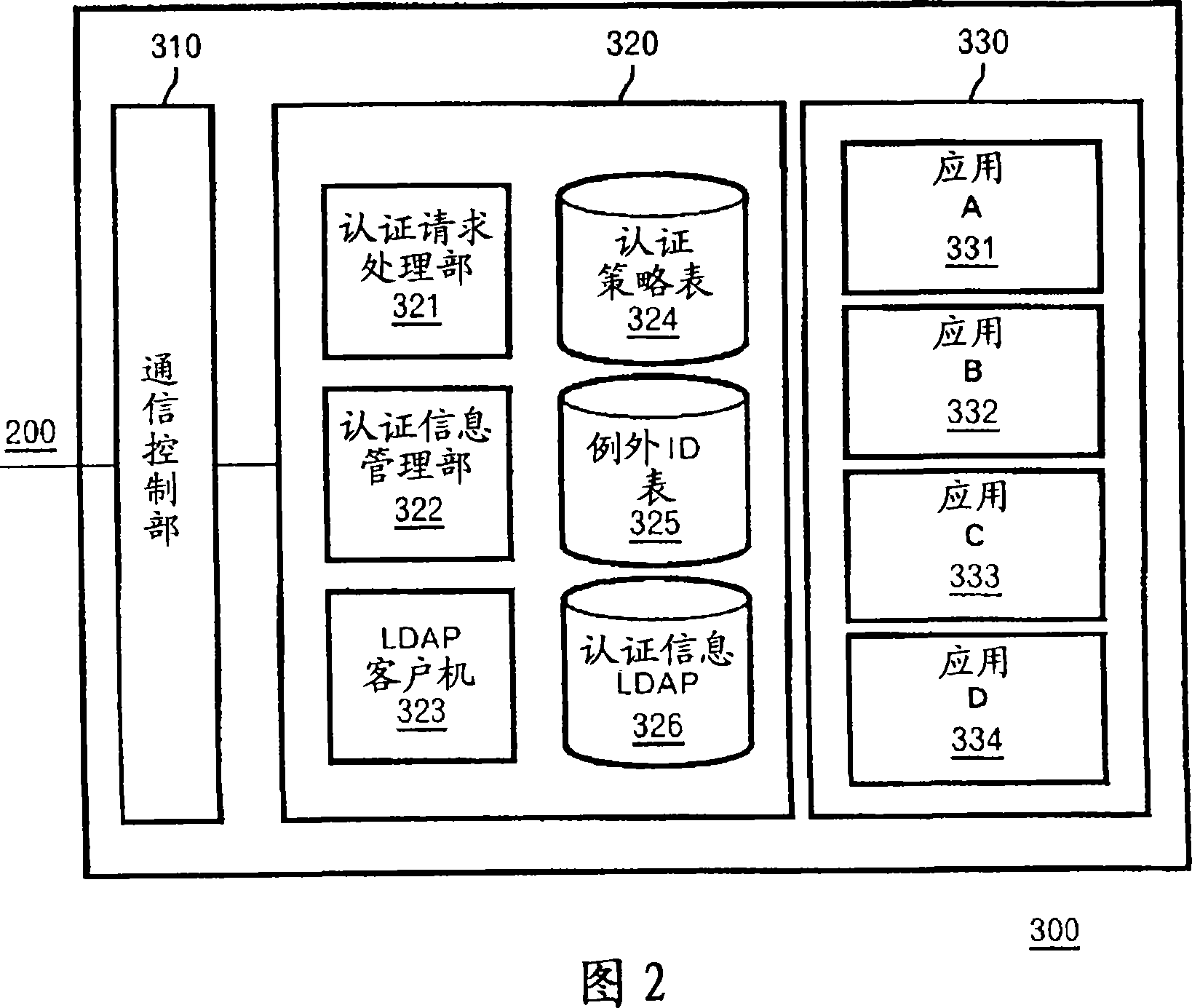
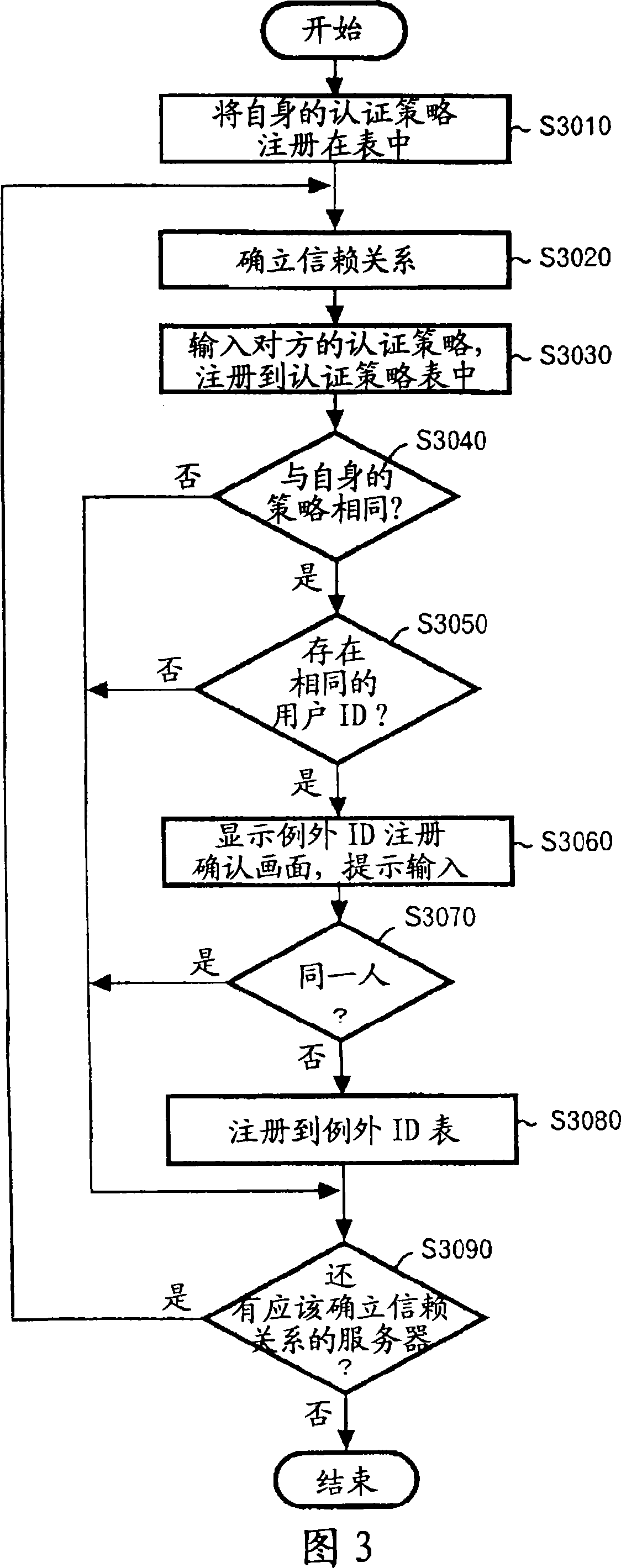
[0028] Hereinafter, the best mode for realizing the present invention will be described in detail with reference to the drawings. In addition, the present invention can be implemented in many different ways, and should not be limited and interpreted by the descriptions of the embodiments. In addition, all combinations of features described in the embodiments cannot be limited to the solutions of the present invention. necessary. In addition, in the whole description of embodiment, the same code|symbol is attached|subjected to the same element.
[0029] In the following embodiments, although methods and systems are mainly described, those skilled in the art can understand that the present invention can also be implemented as a program that can be used in a computer. Therefore, the present invention may take an embodiment as hardware, an embodiment as software, or an embodiment as a combination of software and hardware. The program may be recorded on any computer-readable medi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com