A method for content protection of the handset TV service
A technology of mobile TV service and mobile TV, which is applied in the field of communication to achieve the effect of less system changes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] The present invention will be described in further detail below in conjunction with the accompanying drawings.
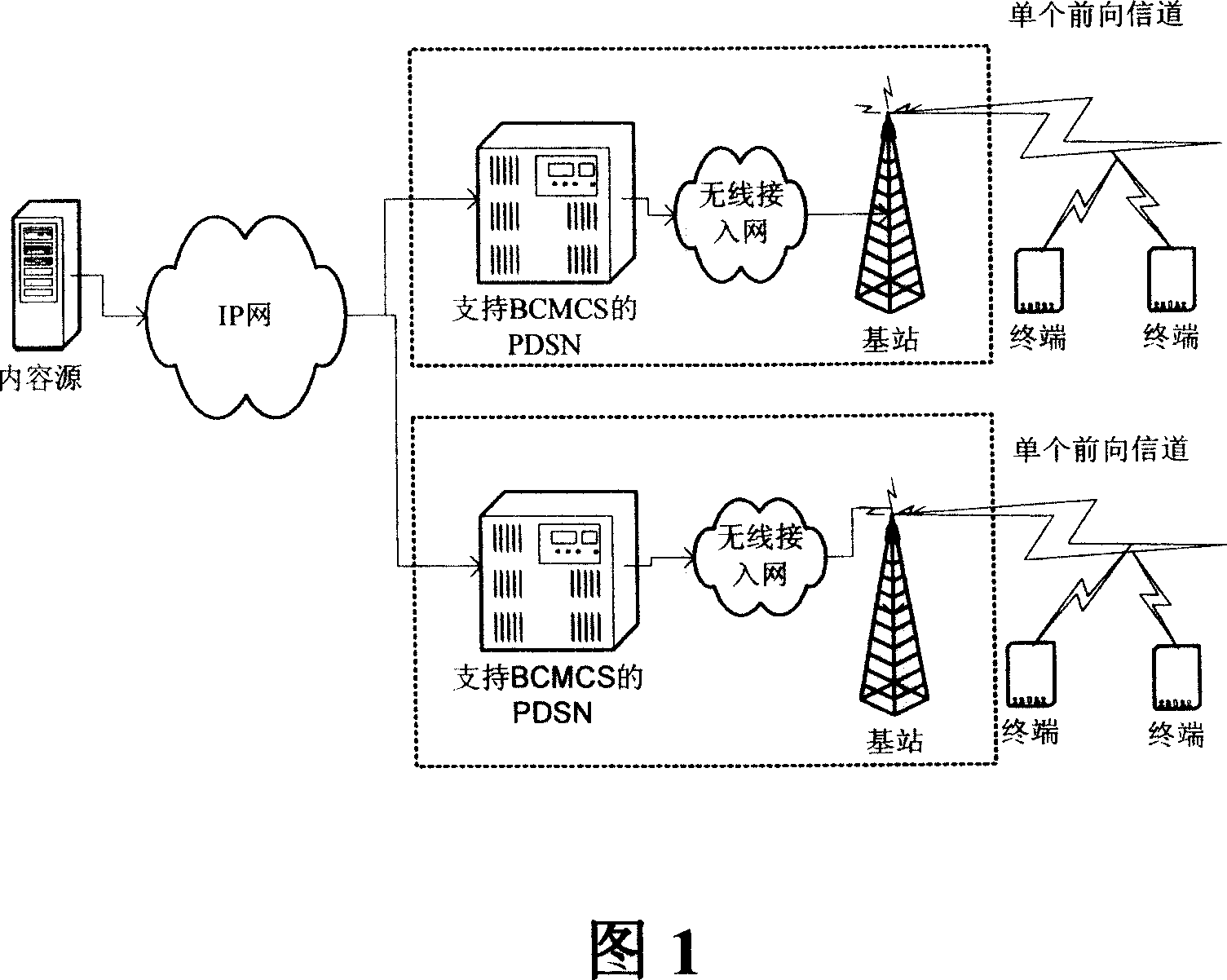
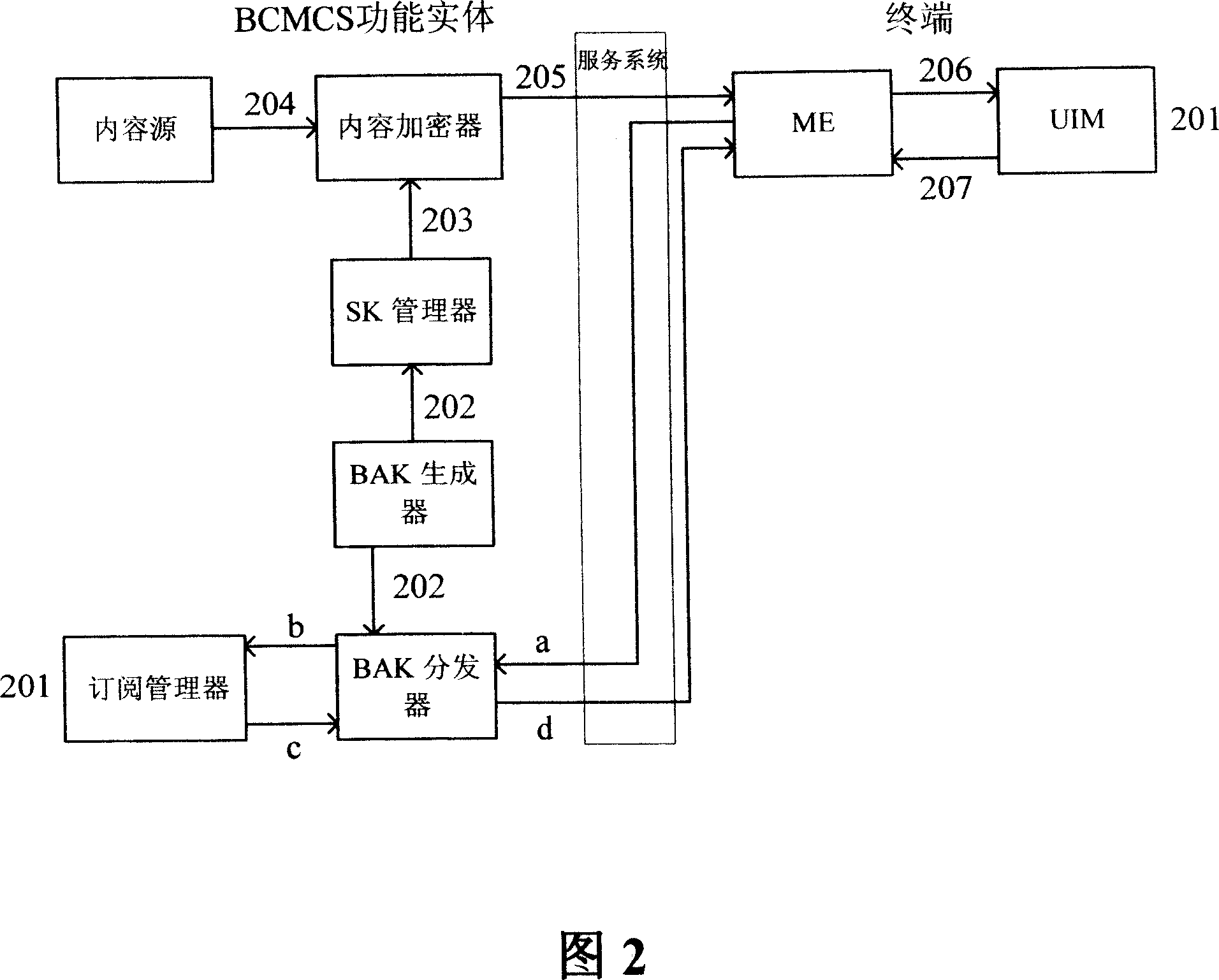
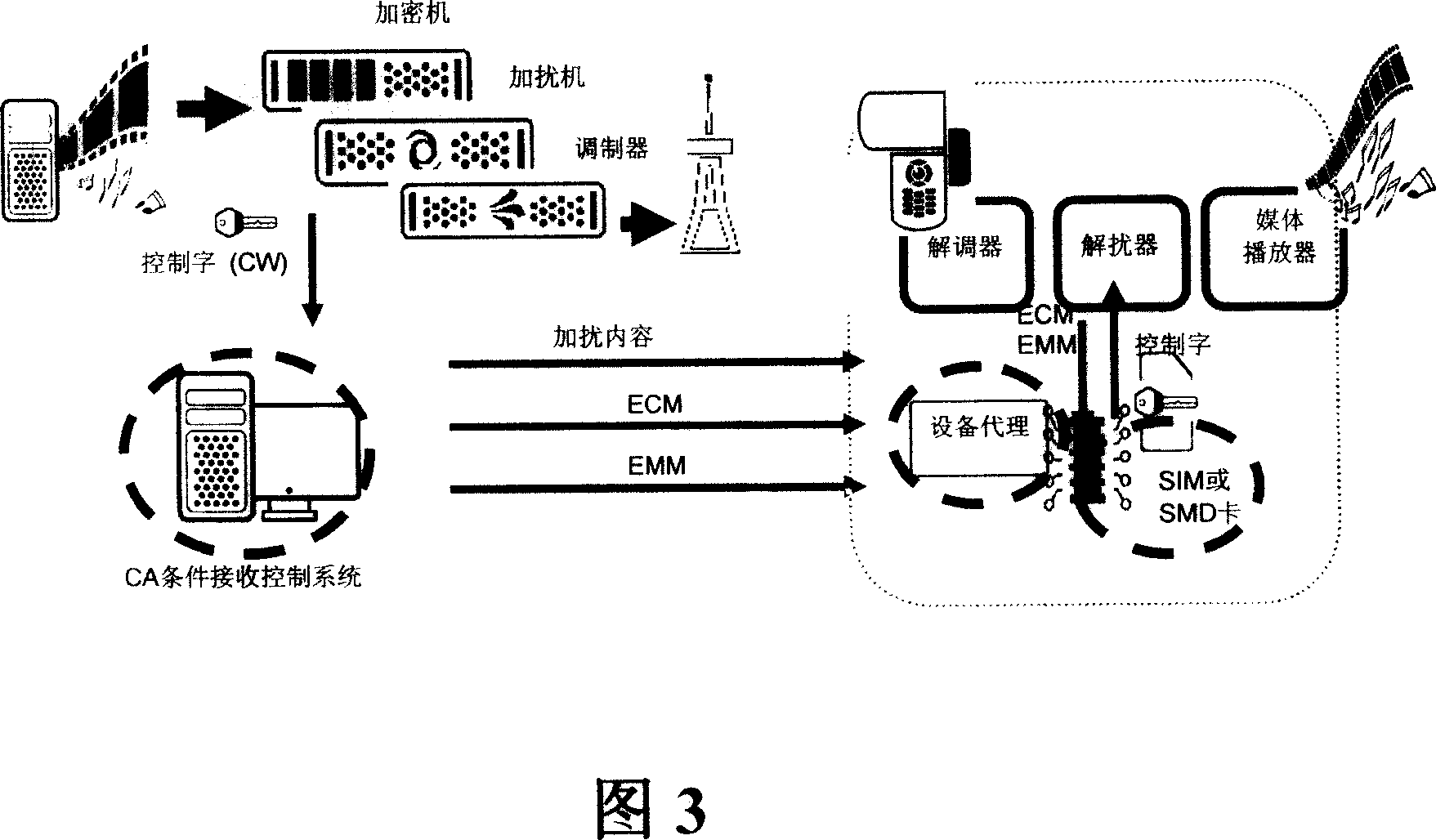
[0079] The method flow of the present invention is shown in Figure 5, the mobile TV / mobile multimedia broadcasting content provider uses the CA system to generate a control word (CW), and the CW is used as a content key to encrypt the content, and then sends the CW to the mobile operator. According to the BCMCS security framework, the operator generates SK from BAK and SK_RAND to encrypt CW, and the encrypted CW is returned to the mobile TV / mobile multimedia broadcasting content provider together with BAK index BAK_ID and SK_RAND. The mobile TV / mobile multimedia broadcasting content provider broadcasts the encrypted content, BAK_ID and SK_RAND to the terminal together. On the terminal side, according to the key distribution process of BCMCS, UIM generates SK from BAK and SK_RAND, and sends SK back to ME, ME uses SK to decrypt CW, and then CW decrypts the cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com