Method for protecting against keylogging of user information via an alternative input device
a keylogger and user information technology, applied in the field of computer network security, can solve the problems of largely unused by the majority of computer users, the keylogger program once installed and activated on the computer system is extremely difficult to detect, and the anti-spyware detection program may not identify new and more recent variations of the keylogger program,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
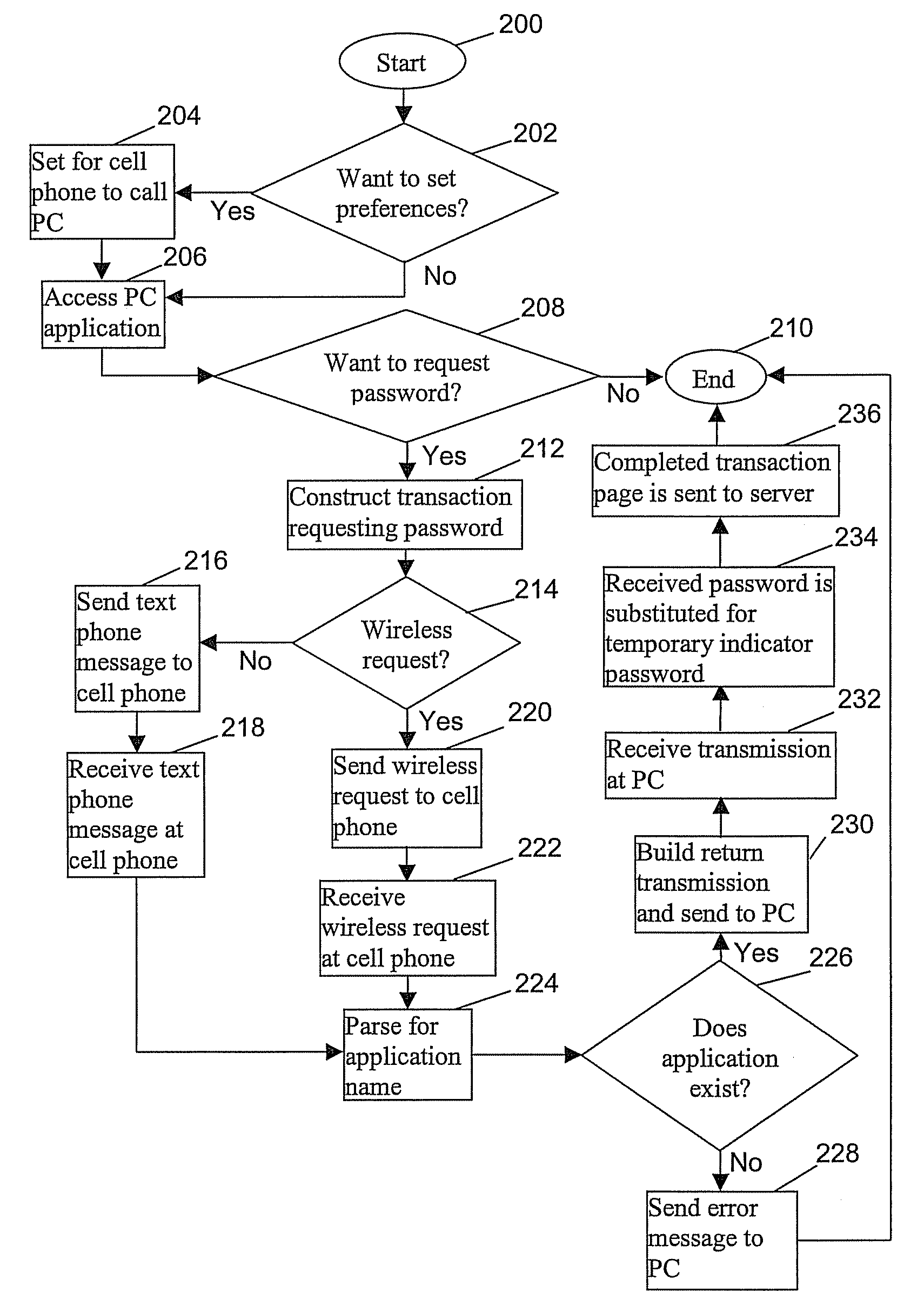
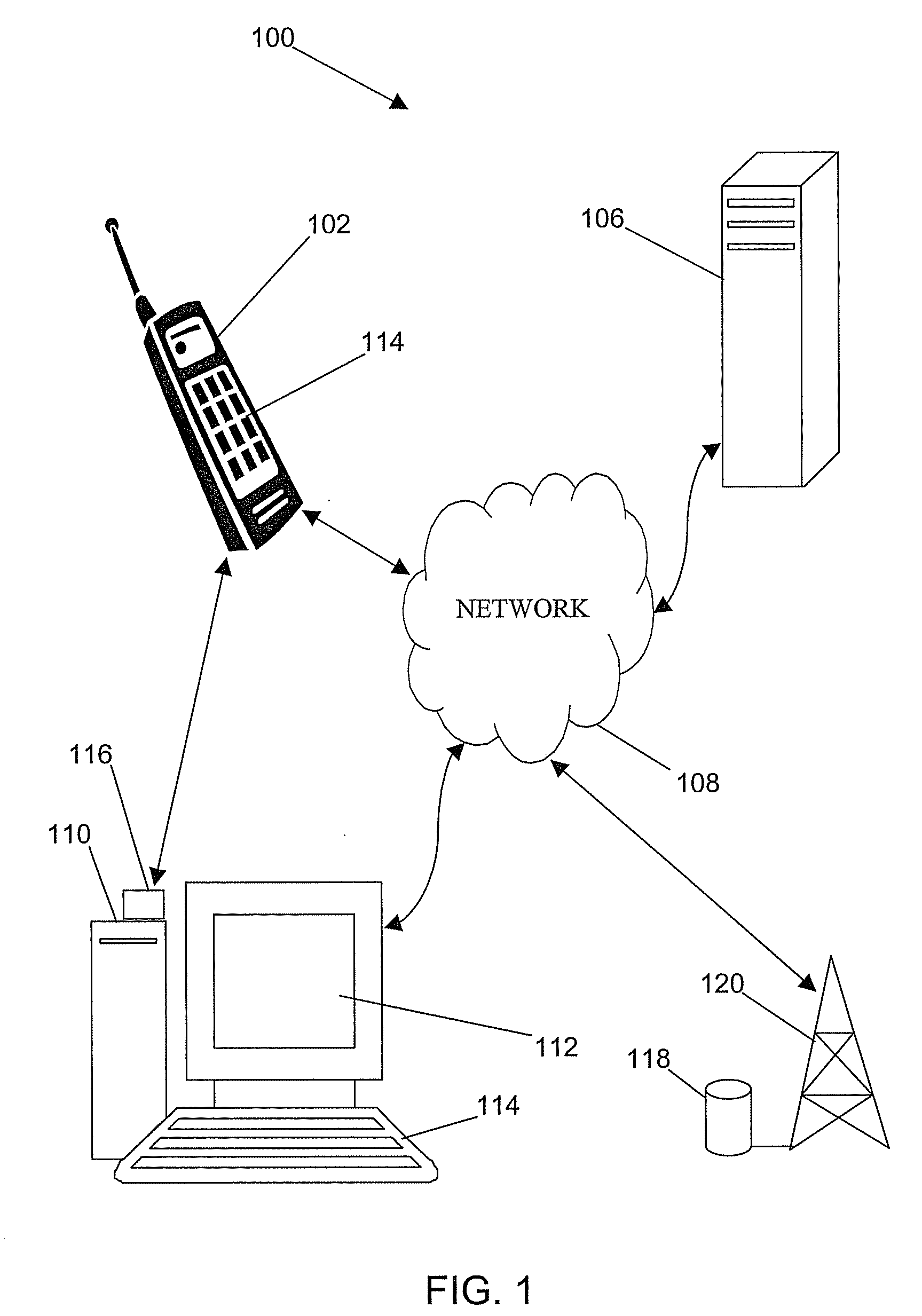
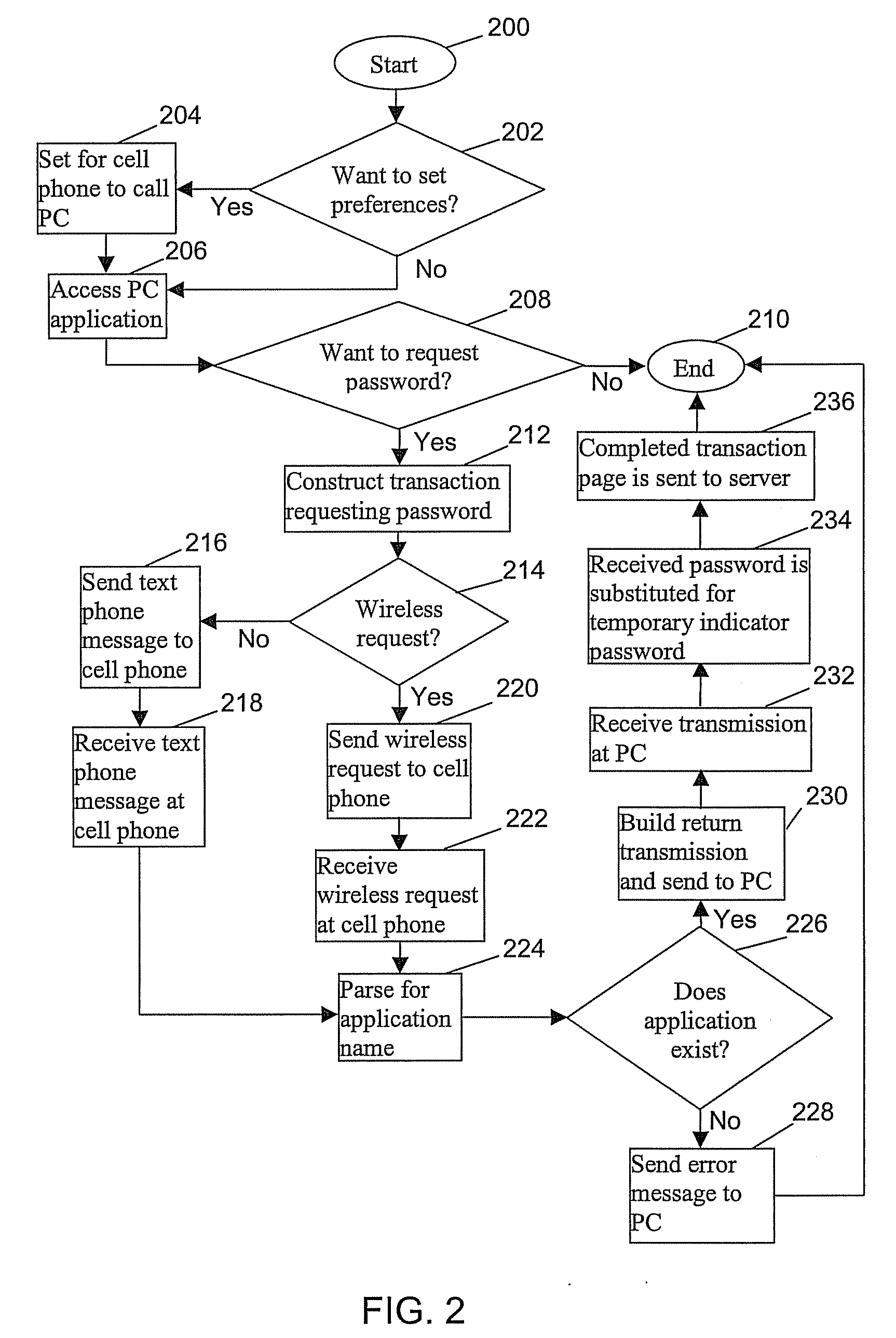
[0013]Embodiments of the invention provide a method for keylogging prevention by generating an alternate input transaction on another device such as a cellular phone, personnel digital assistant, or any external peripheral device with alphanumeric entry and wireless or wired communication capability that is not susceptible to keylogging. Embodiments of the invention bypass the keyboard of the device, such as a personnel computer (PC) that is the target of the keylogger programs that are able to steal confidential information. The alternative input devices provide transactional information, which includes a password or other confidential data to be input into fields that are to be shielded from key logger observation. The transaction is sent to the PC via, wired link, telephone call, cell phone call, infrared, bluetooth or similar technology.
[0014]Embodiments of the invention utilize a plug-in to a browser application on a PC that generates a transaction that is transmitted to an ent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com