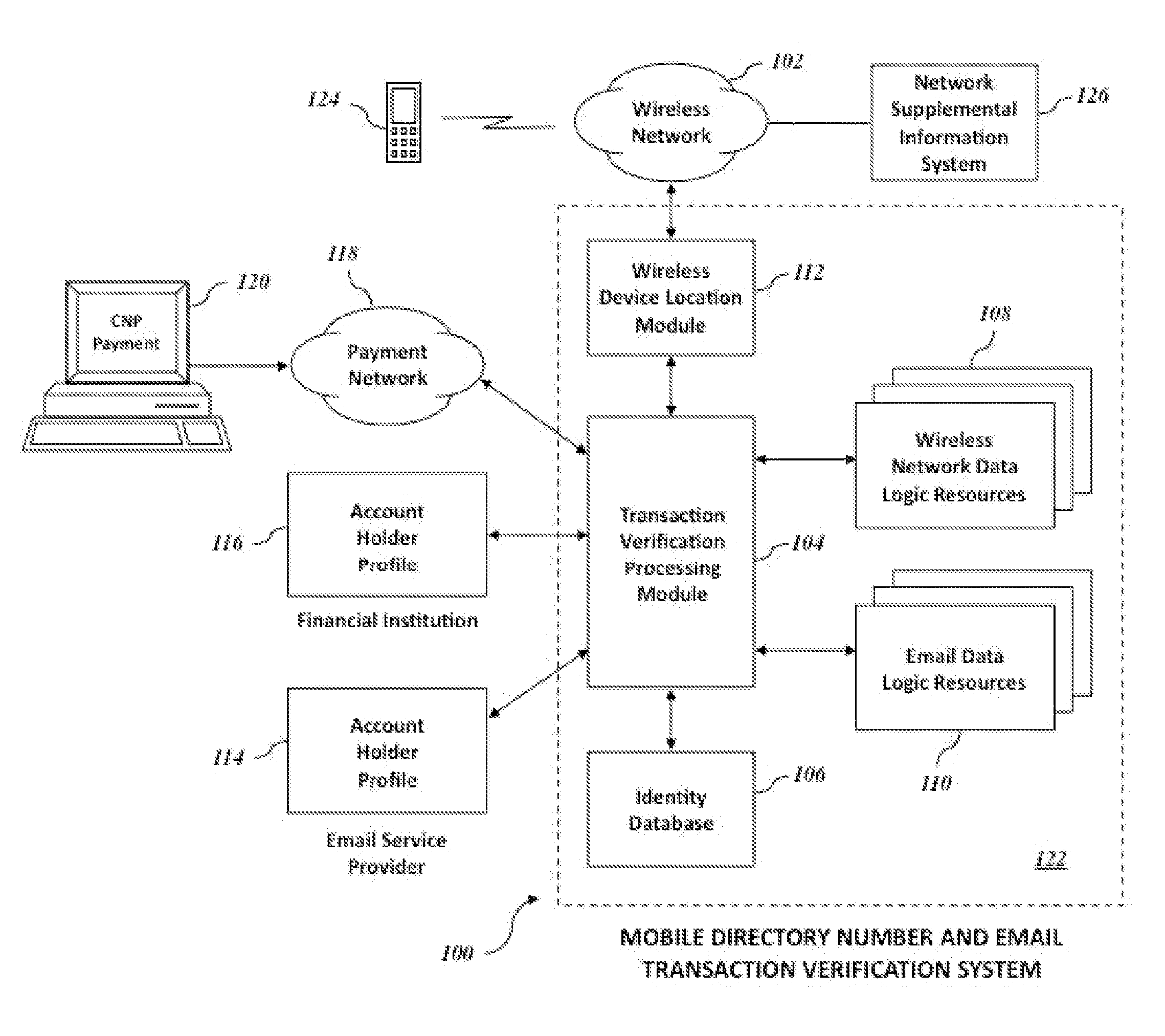
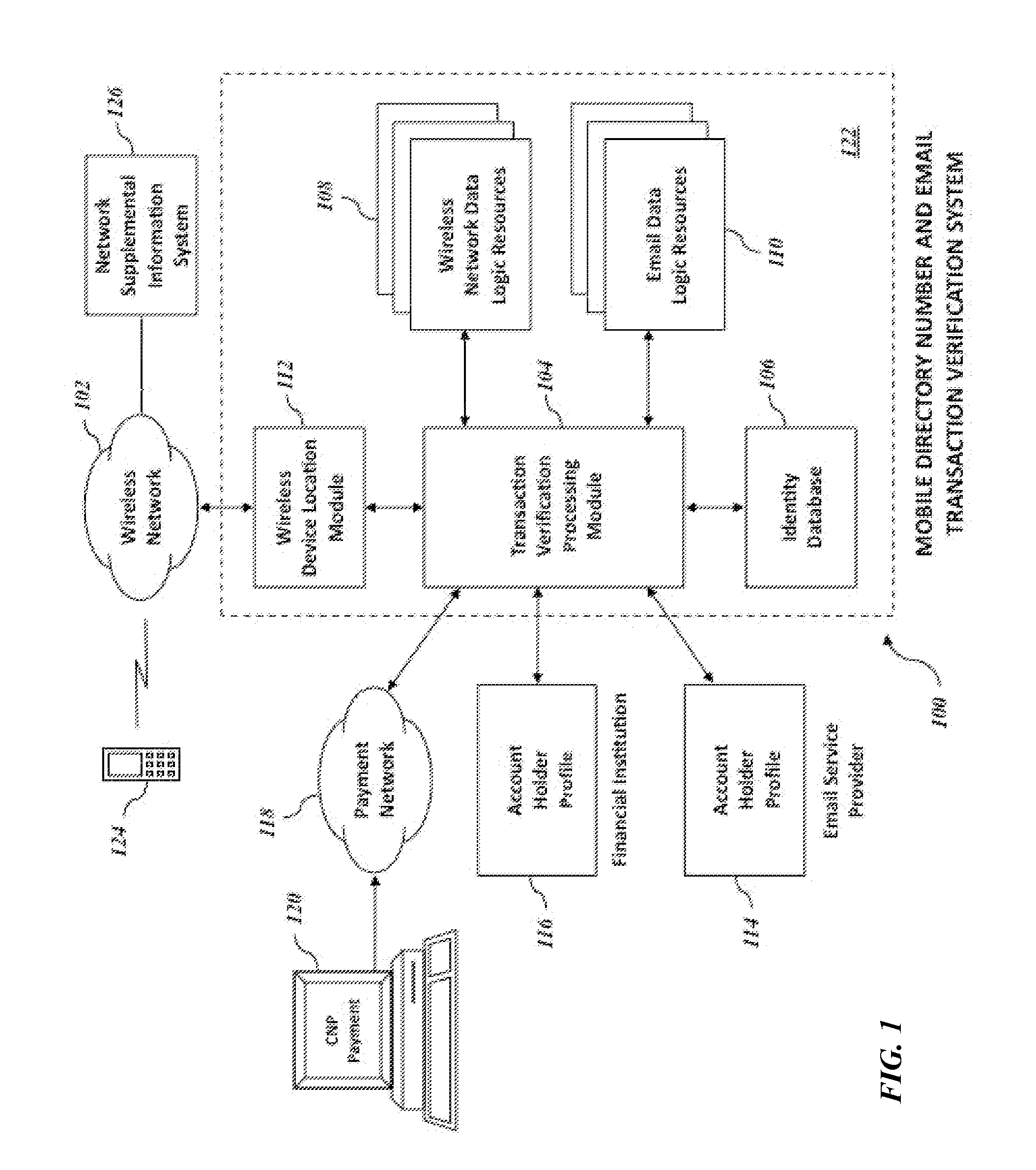
[0010]An object of an embodiment of the present invention is to provide a
system, and its methods of use, to detect fraudulent transactions based on information derived from a
payment network pertaining to
payment transactions, information derived from a
wireless network pertaining to particular wireless device IDs (e.g. mobile directory numbers) and information derived from a financial institution pertaining to cardholders associated with financial accounts. The invention relates generally to protecting the identity of a cardholder and detecting
identity theft by using the wireless device ID of the cardholder's wireless device (e.g.
mobile phone) and validating that wireless device ID using data obtained from a
payment network and a financial institution pertaining to the cardholder. This data may be used to validate the wireless device ID obtained from the payment network where such validation may be used for a variety of applications, such as assisting in the detection and prevention of
identity theft, fraudulent behavior or activity that may be engaged in by a purported cardholder.
[0011]Another object of an embodiment of the present invention is to provide a
system, and its methods of use, to detect fraudulent transactions based on information derived from a payment network pertaining to payment transactions, information derived from a
wireless network pertaining to particular wireless device IDs (e.g. MDNs) and information derived from a financial institution pertaining to cardholders associated with financial accounts. Data pertaining to the wireless device ID obtained from a
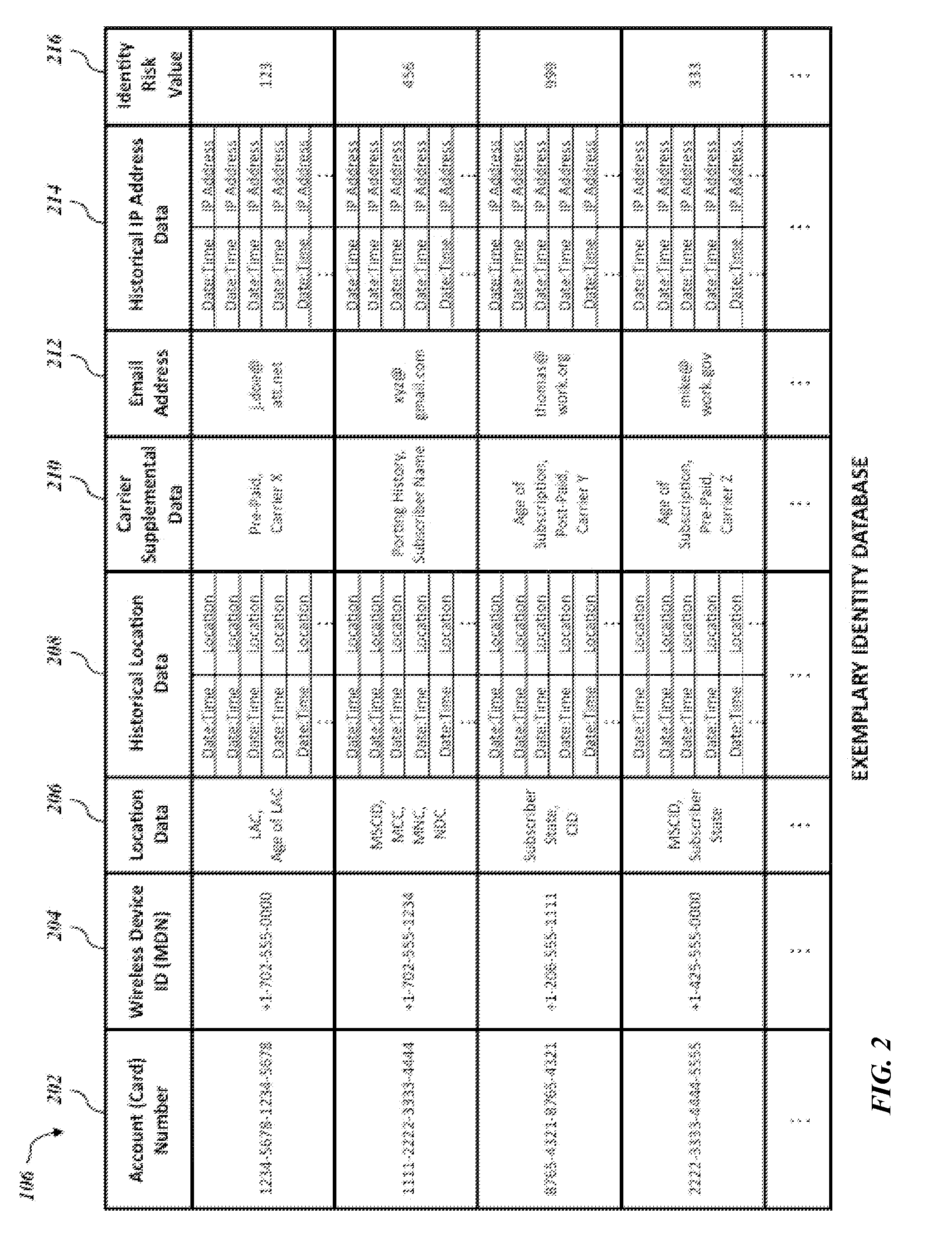
wireless network 102 and data pertaining to the cardholder obtained from a financial institution can be used as the basis for a
statistical analysis, resulting in an identity risk value. Data that may be obtained and derived include the wireless device ID (e.g. the MDN) itself, other telephone numbers (directory numbers) associated with the account,
location data of the wireless device identified by the wireless device ID, supplementary subscription data associated with the wireless device, the format and characteristics of the wireless device ID and the format and characteristics of other directory numbers. All
location data obtained or otherwise derived from telephone directory numbers provides utility for fraud detection as irregular or anomalous locations associated with an individual may be indicative of financial fraud. Furthermore, supplementary subscription data associated with the wireless device, such as the network serving the wireless device, age of the subscription, name on the subscription,
porting history of the
directory number, and subscribed supplementary features (e.g.
call forwarding), may be indicative of financial fraud. This data may be used for a variety of applications, such as assisting in the detection and prevention of
identity theft, fraudulent behavior or activity that may be engaged in by a purported cardholder.
[0012]Yet another object of an embodiment of the present invention is to provide a
system, and its methods of use, to detect fraudulent transactions based on information derived from a payment network pertaining to payment transactions, information derived from a financial institution pertaining to cardholders associated with financial accounts and information derived from an email
service provider pertaining to particular email addresses and
Internet Protocol (IP) data pertaining to cardholders associated with email accounts. This data may be used to validate the
email address data obtained from the payment network where such validation may be used for a variety of applications, such as assisting in the detection and prevention of identity theft, fraudulent behavior or activity that may be engaged in by a purported cardholder.
[0013]Yet another object of an embodiment of the present invention is to provide a system, and its methods of use, to detect fraudulent transactions based on information derived from a payment network pertaining to payment transactions, information derived from a financial institution pertaining to cardholders associated with financial accounts and information derived from an email
service provider pertaining to particular email addresses and
Internet Protocol (IP) data pertaining to cardholders associated with email accounts. Data pertaining to the email addresses obtained from a financial institution and data pertaining to the cardholder obtained from an email service provider can be used as the basis for a
statistical analysis, resulting in an identity risk value. Data that may be obtained and derived include the email address,
IP address data associated with the email address and the format and characteristics of the email address itself. All
location data obtained or otherwise derived from
IP address data provides utility for fraud detection as irregular or anomalous locations associated with an individual may be indicative of financial fraud as
IP address data may be indicative of location data where an email account has been accessed by an individual. This data may be used for a variety of applications, such as assisting in the detection and prevention of identity theft, fraudulent behavior or activity that may be engaged in by a purported cardholder.
 Login to View More
Login to View More  Login to View More
Login to View More