Security model for actor-based languages and apparatus, methods, and computer programming products using same
a security model and programming language technology, applied in the field of programming languages, can solve problems such as time-consuming, error-prone and time-consuming approaches, and the security of most programming languages is not enough, and mistakes are common
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
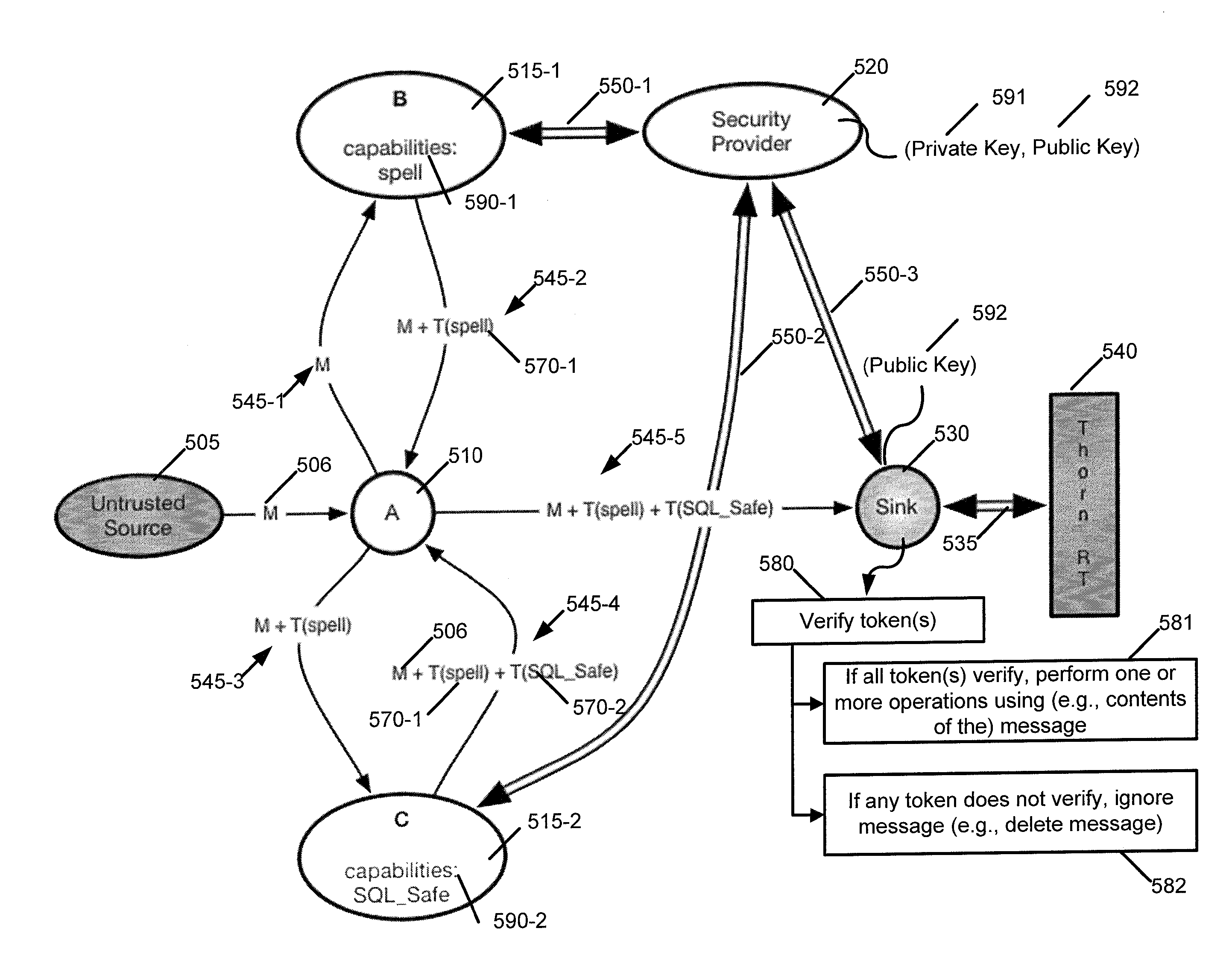
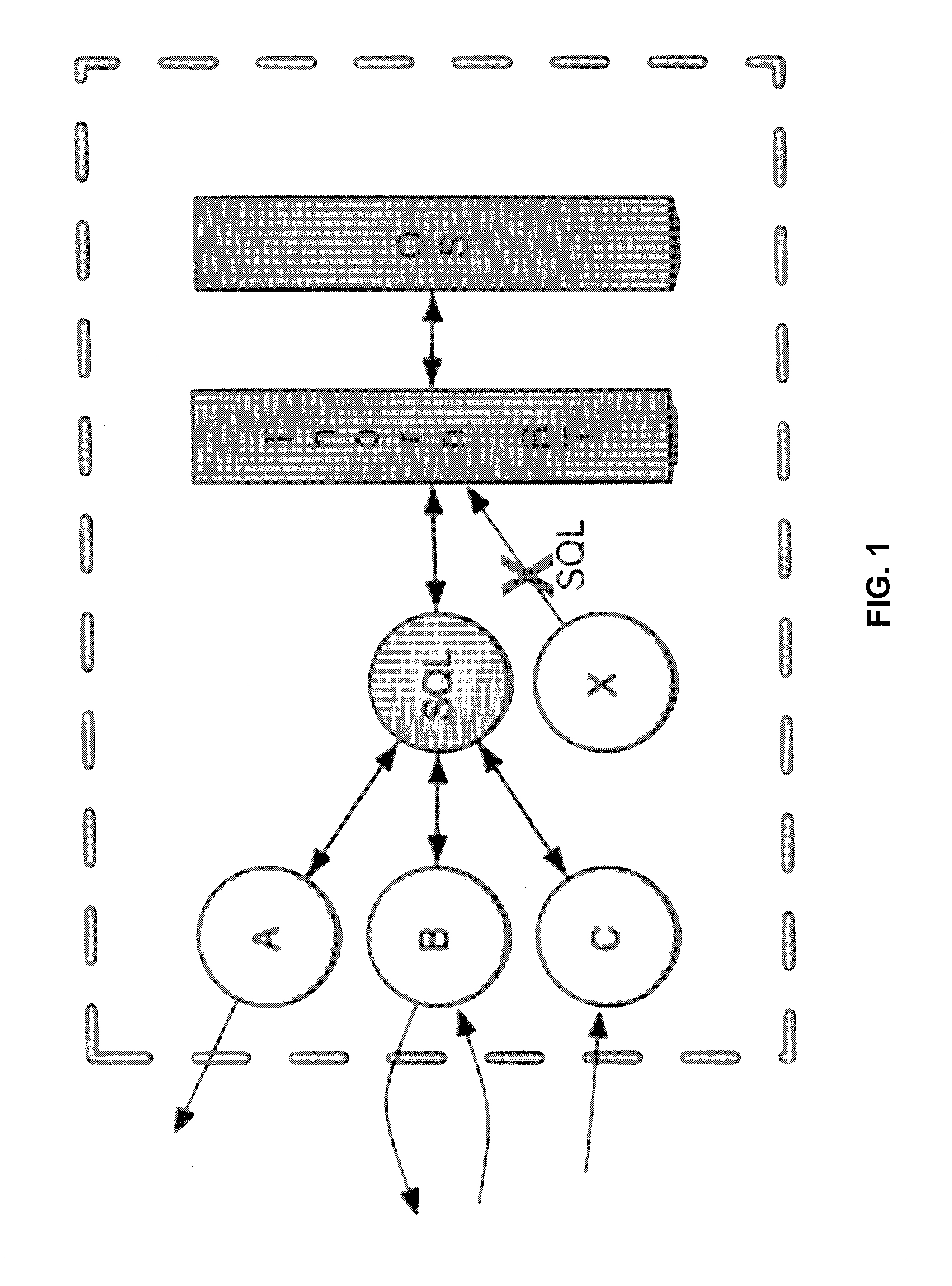
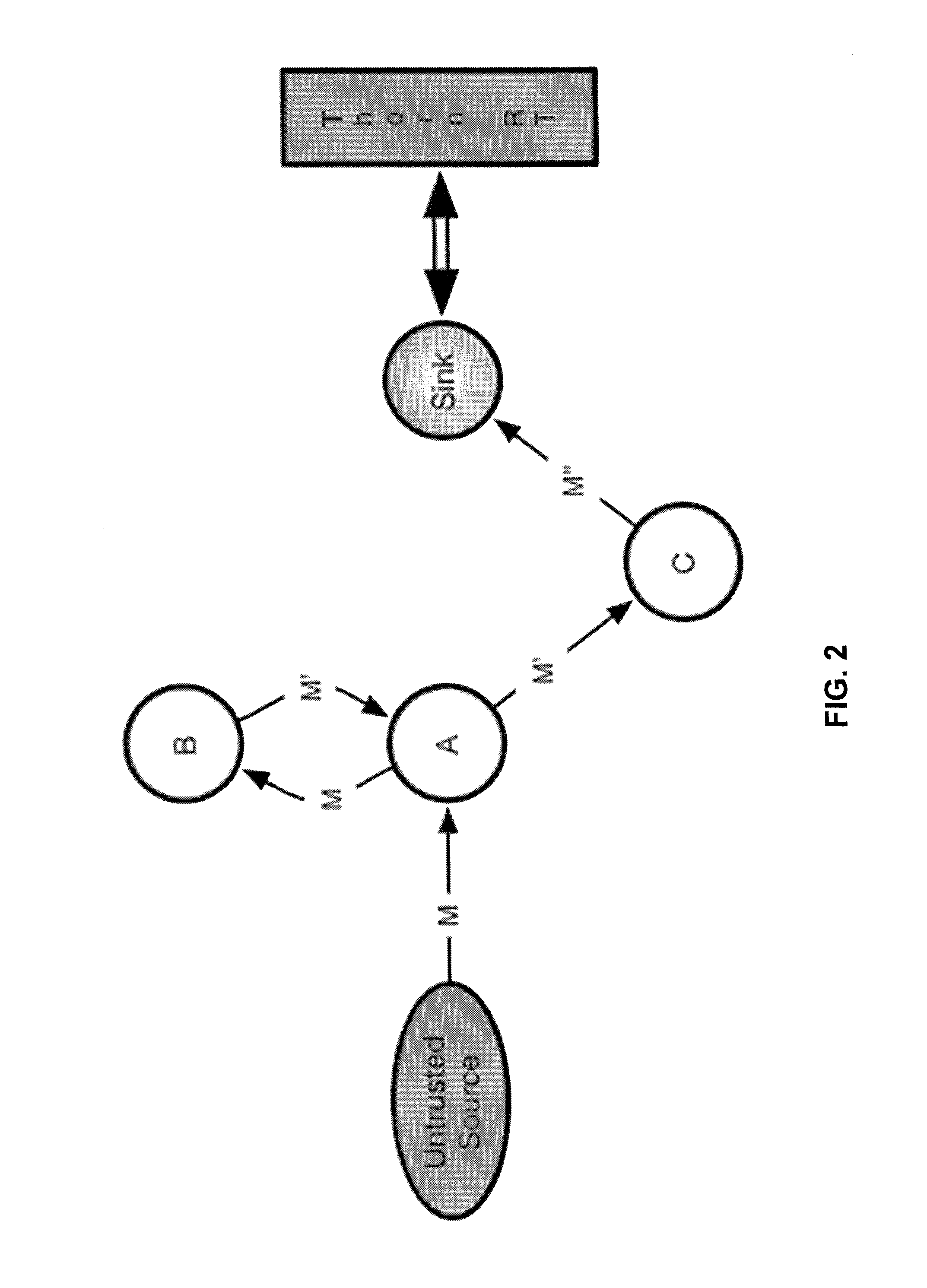
[0028]As stated previously, the purpose of language-based security is to make applications more secure by embedding security mechanisms inside the programming languages in which those applications are written. Research in the area of language-based security has become very active in the past fifteen years, starting with the advent of Java (a programming language and computing platform first released by Sun Microsystems in 1995) in the mid 1990s. With Java, it became possible for the first time to add dynamic content to Web pages in the form of Java applets. This was an attractive enhancement for the Web, since Web pages up to that point had only been static. However, it also created the possibility for attackers to exploit potential vulnerabilities in the underlying Java runtime environment of remote systems for endusers, and compromise its integrity and confidentiality. To address these concerns, the first version of Java was released with a binary access-control model, allowing lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com