Mitigating security risks via code movement
a security risk and code movement technology, applied in the field of application code analysis, can solve the problems of web applications, web services, and web applications continuously exposed to security threats, and are too complex to reason about statically, and are vulnerable to a sophisticated remote code execution attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
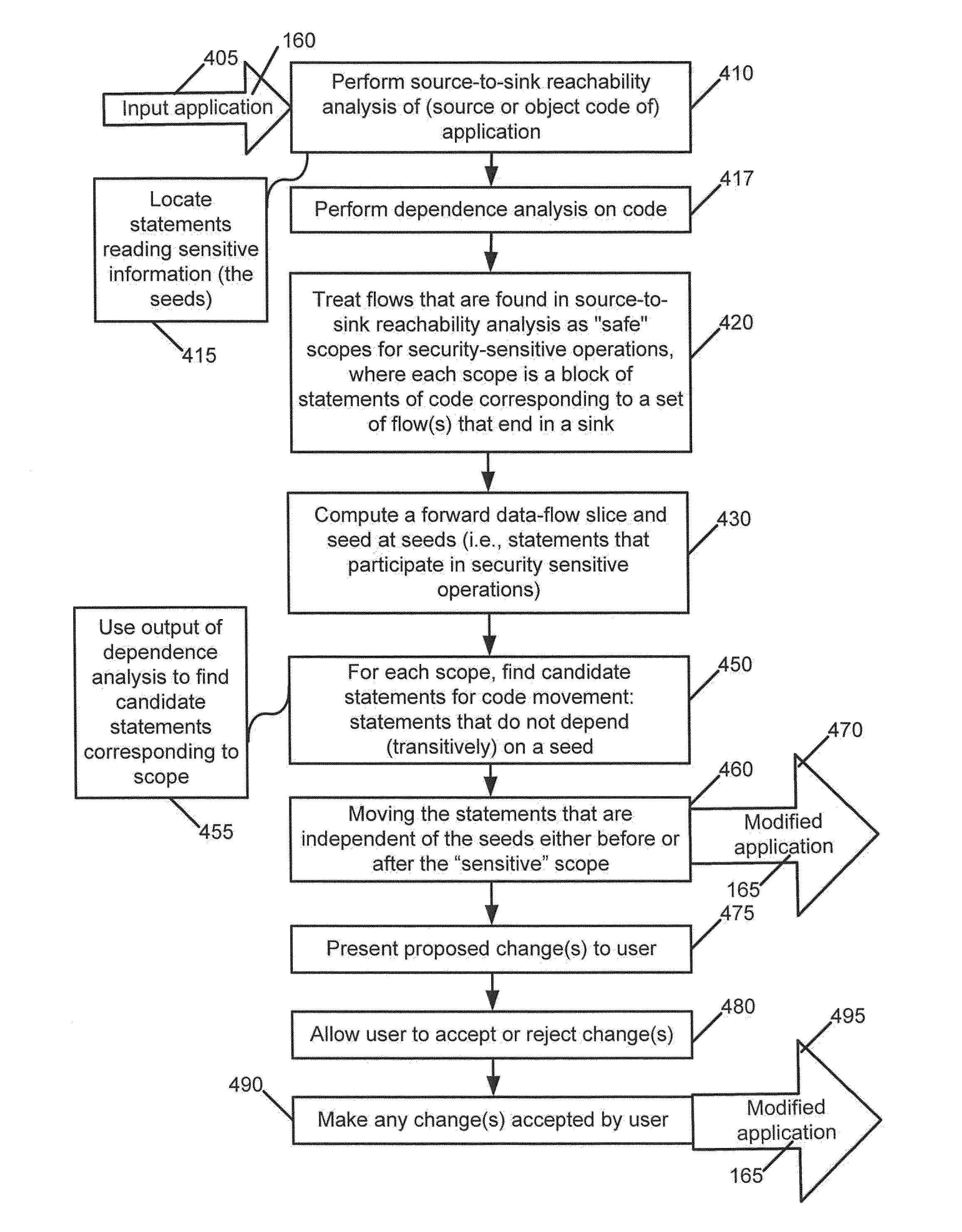
[0025]As stated above, there is a growing need to protect web applications against threats that lie outside the scope of existing static security-scanning solutions. Exemplary embodiments herein take steps toward enhancing security analysis tools, such that the enhanced tools mitigate security threats that lie beyond insecure data-flow vulnerabilities. An exemplary technique is (i) to identify security-sensitive areas within an application, and (ii) to reduce the computations performed within these areas, so as to minimize the exposure of the application to security threats. The exemplary embodiments move code from the security-sensitive areas within the computations to areas outside the security-sensitive areas. Examples of JAVA (a programming language and computing platform first released by Sun Microsystems in 1995) code and movement are provided below after an overview of an exemplary computing system suitable for use with the exemplary embodiments.
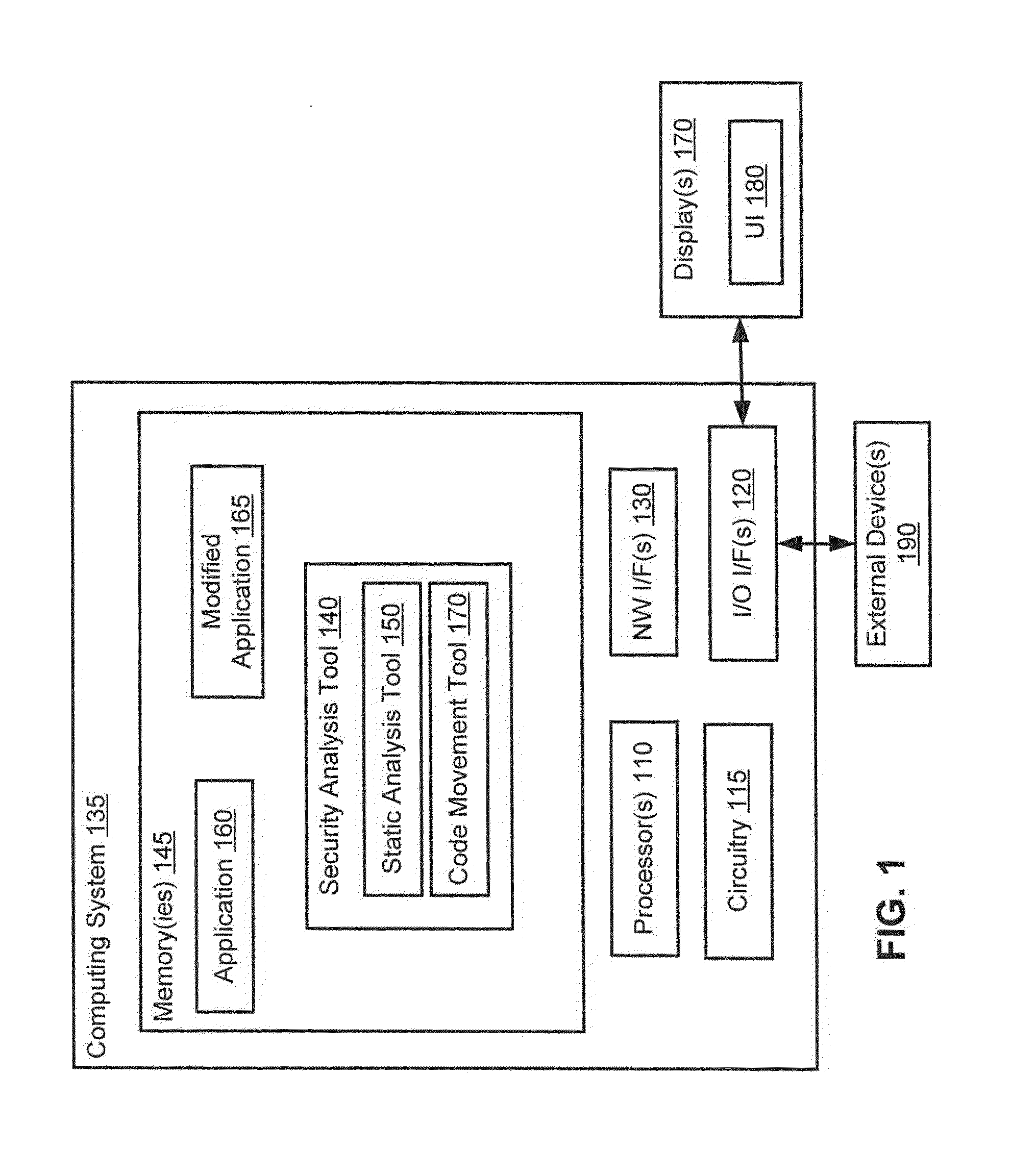
[0026]Referring to FIG. 1, thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com