Hardware-logic based flow collector for distributed denial of service (DDOS) attack mitigation
a flow collector and hardware logic technology, applied in the field of intrusion prevention, can solve the problems of slowing down, slowing down, and slowing down the network infrastructure of the internet service provider (isp) to bear the brunt of such attacks, and achieve the effect of slowing down the service provided by the isp and slowing down
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
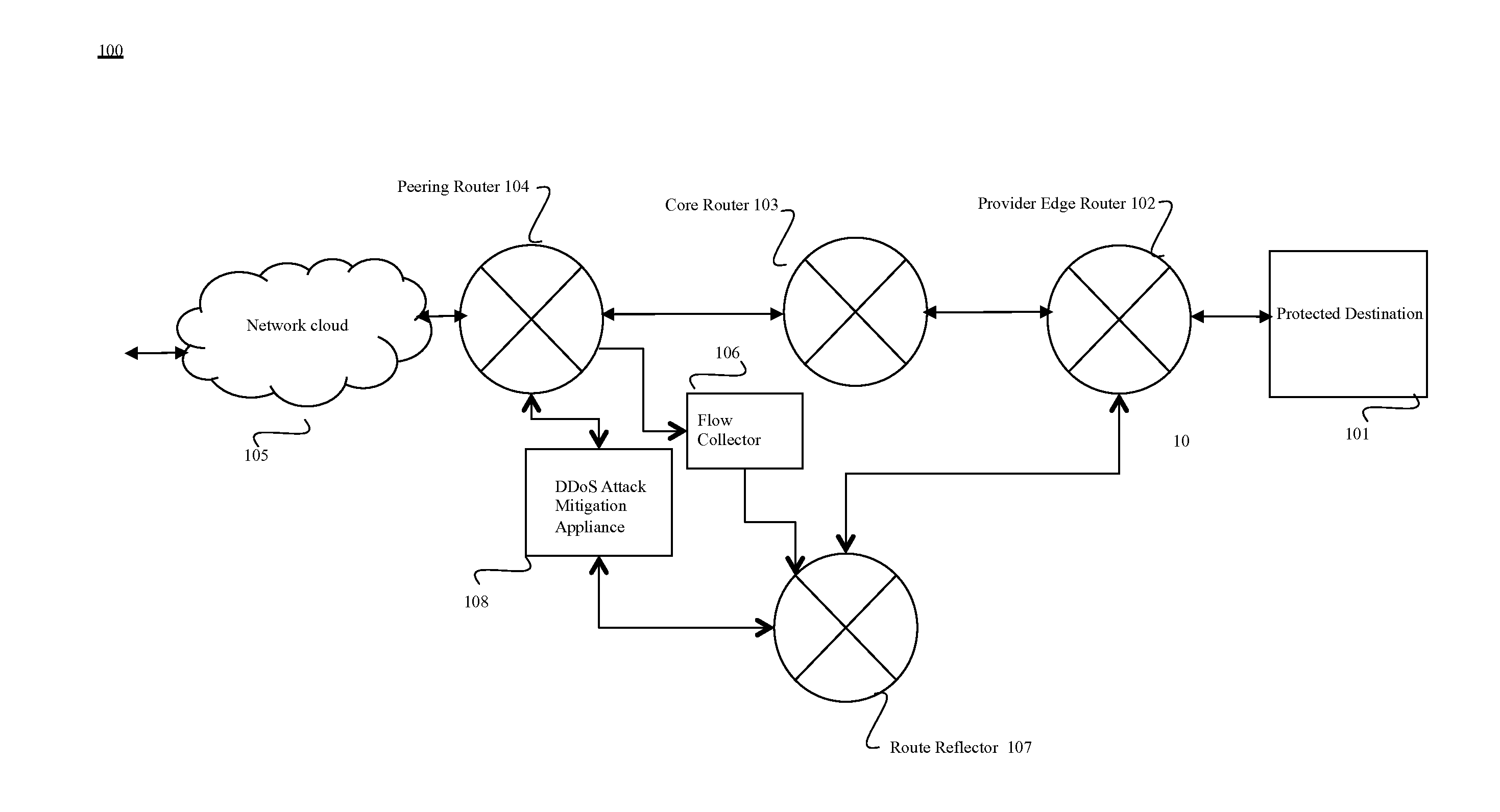
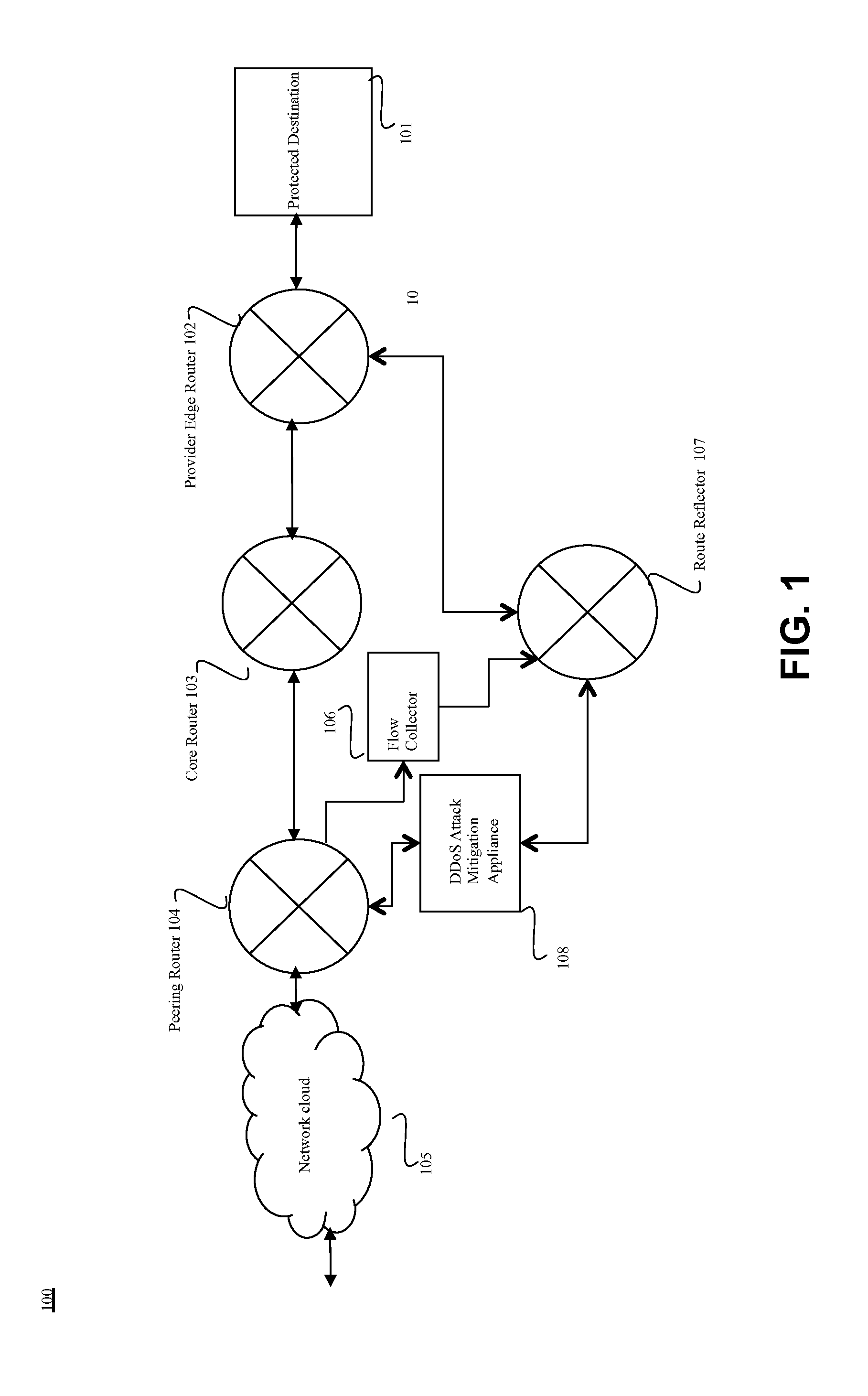
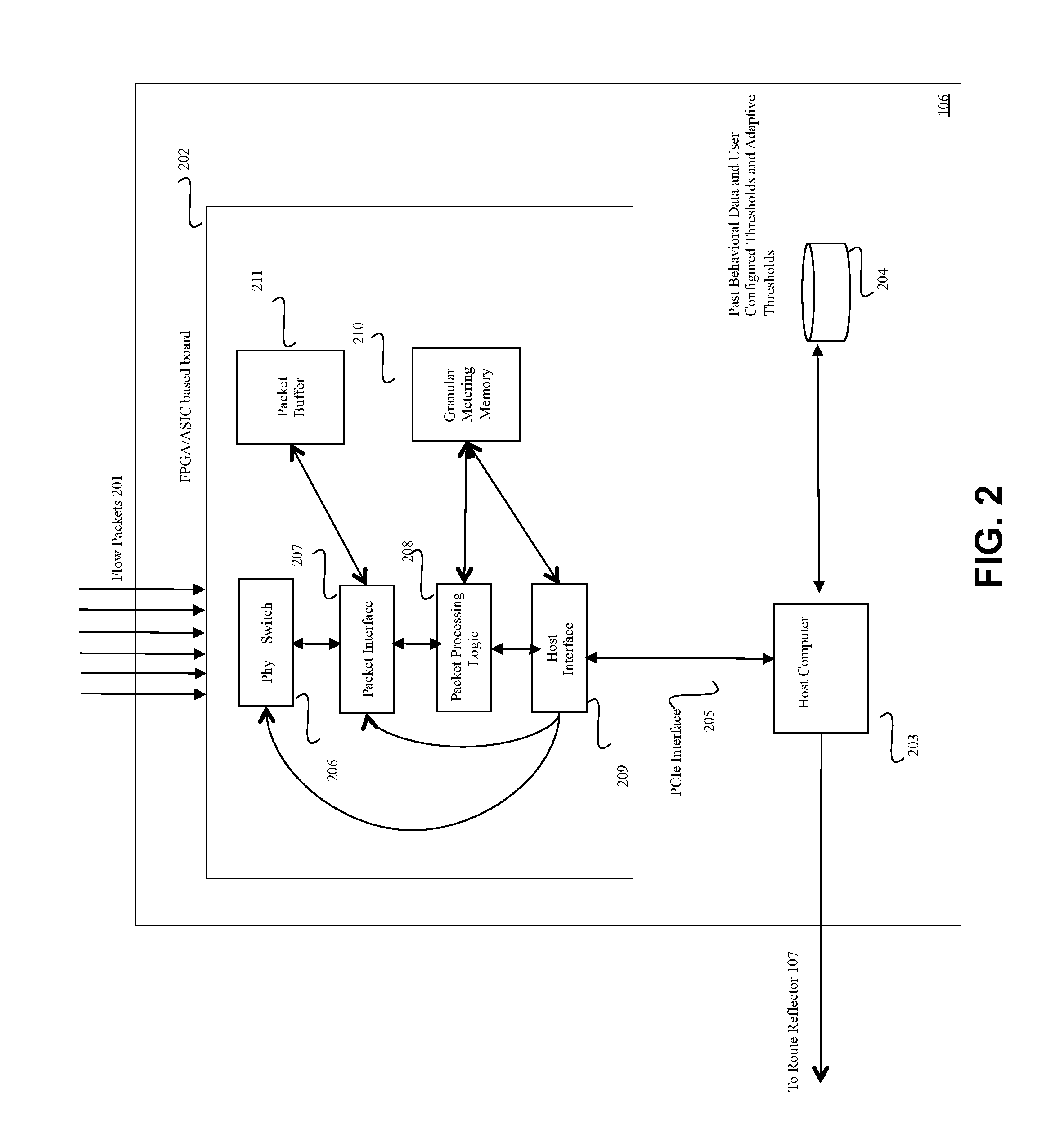
[0014]Methods and systems are described for an integrated solution to rate-based DoS attacks targeting service provider networks. According to one embodiment, a flow collector is capable of receiving a variety of flow statistics in industry standards from routers and switches. These flow statistics may be in the form of packets in protocols, including, but not limited to, NetFlow, JFlow, SFlow, CFlow and the like. The hardware-based apparatus collects this data and converts them to granular rate statistics in a round robin database for varying periods such as past hour, past day, past week, past month, past year etc. Based on the past granular traffic statistics, the apparatus can determine corresponding rate-thresholds through continuous and adaptive learning. Once these granular rate thresholds are breached for any traffic parameter, the apparatus can determine the networks being attacked or protocols or transmission control protocol (TCP) or user diagram protocol (UDP) ports unde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com