Content-Aware Firewalling, Policy Regulation, and Policy Management for Industrial Automation, Machine To Machine Communications, and Embedded Devices
a firewalling and content-aware technology, applied in the field of industrial automation, can solve problems such as unsafe or inefficient industrial machine operation, device malfunctions, and significant vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
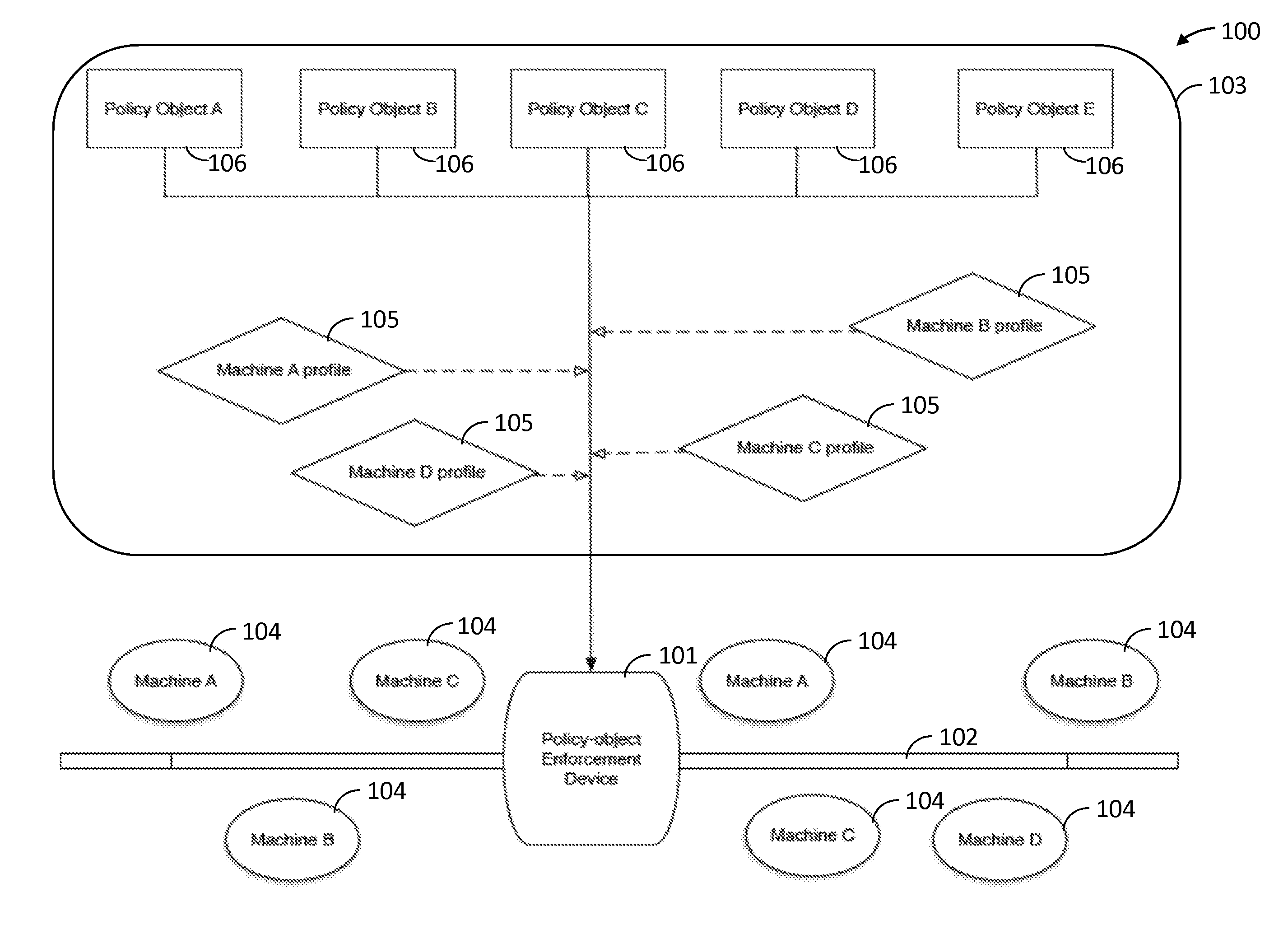
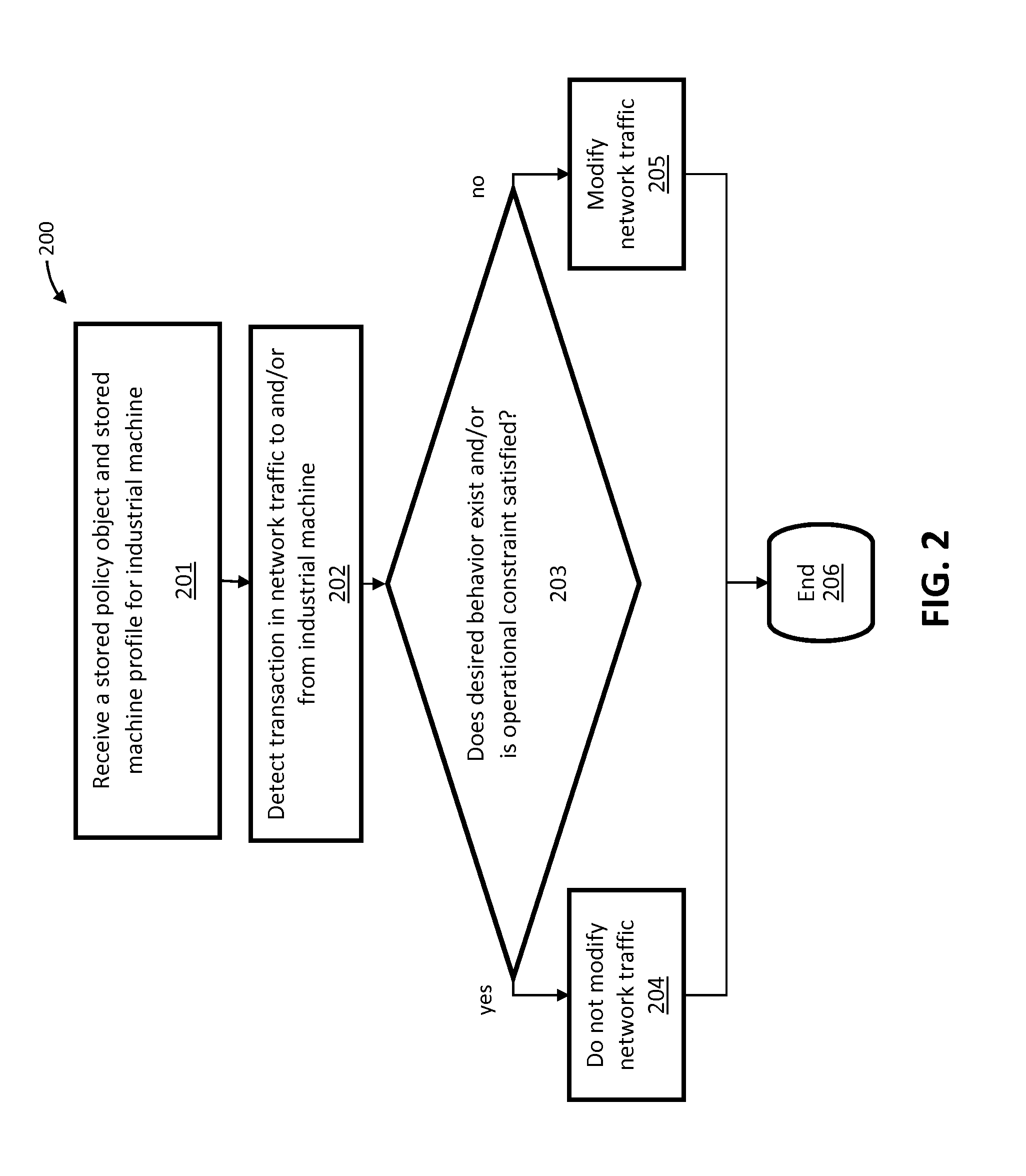
Image
Examples
example a
Stateful and Conditional Controls
[0042]
language / 2014” policyname=“segregate-client-data” uuid=“cbdf9064-3ab711e4a2be0800276380c2”> value=“(?i)supersecret-client-A”> control=“session.variable” parameter=“$confidential” value=“true” / > control=“session.variable” parameter=“$confidential” value=“true”> op=“=“ value=“clientb.mycompany.com” / >op=“=“ value=“clientc.mycompany.com” / >
[0043]This example illustrates conditionality and stateful behavior in the control language, which are important characteristics of certain embodiments of the invention. It should be observed that the control “protocol” is used in two conditional statements in the language. These conditional statements examine the value of the “protocol” control which is returned by the runtime environment. The additional control-language statements contained inside the conditionals are executed whenever the conditional statement evaluates “true.” In this example, the statements inside the conditional labeled “detect smb / c...
example b
Enforcing Allowed Transactions
[0050]
language / 2014” policyname=“robot-control” uuid=“cbdf9064-3ab711e4a2be0800276380c2”>uuid=“d84f166e560e11e3949d0800273a32bd” value=“robot-rpc” verb=“allow” op=“=“ / >uuid=“056f4b583ab811e4a2be0800276380c2” value=“192.168.0.0 / 24” verb=“allow”op=“=“ / >op=“>=“ verb=“allow” uuid=“7f521efa-3ab8-11e4-a2be-0800276380c2” / >op=“
[0051]In this example, the control language is being executed by a network device that reads streams from a network, following the general pattern of a blocking firewall. This policy object has four rules marked with the verb “allow,” referencing three different controls. As the device inspects and parses the data flowing through the network, it determines (for each network flow) whether the data in the flow conform to the “robot-rpc” protocol. (Different embodiments of the invention may support any communications protocol(s) that are appropriate and meaningful for their applications.) Because the verb in the rule is “allow,” any networ...
example c
Machine Control Policy
[0055]
language / 2014” policyname=“centrifuge-control” uuid=“cbdf9064-3ab711e4a2be0800276380c2”>model” op=“one-of” value=“6000 series|7000 series|8000 series”> op=“ verb=“report” op=“>” value=“480” / >
[0056]This is an example of a policy object that illustrates operational constraints on machines. The conditional labeled “Manufacturer M centrifuges” is true whenever the control “centrifuge-model” evaluates to one of the values “6000 series,”“7000 series,” or “8000 series.” Clearly, in this embodiment of the invention, a way of obtaining a meaningful value for this control should be obtained. It should be observed, however, that the structure of the control language remains uniform and consistent despite the considerable difference in abstraction levels between this example (which refers to machine characteristics) and that of the preceding examples (which refer to values obtainable by parsing network flows).
[0057]Continuing the example, it can be seen that, for Se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com