System and Method For Providing Technology-Driven End-to-End Managed Security Service Products Through a Security Marketplace
a security marketplace and marketplace technology, applied in the field of cybersecurity marketplace, can solve the problems of customer employees who sign up for non-standard services and use web tools, inadvertent disclosure of sensitive business information and intellectual property, etc., and achieve the effect of improving customer security posture, effective and seamless improvement of customer experien
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
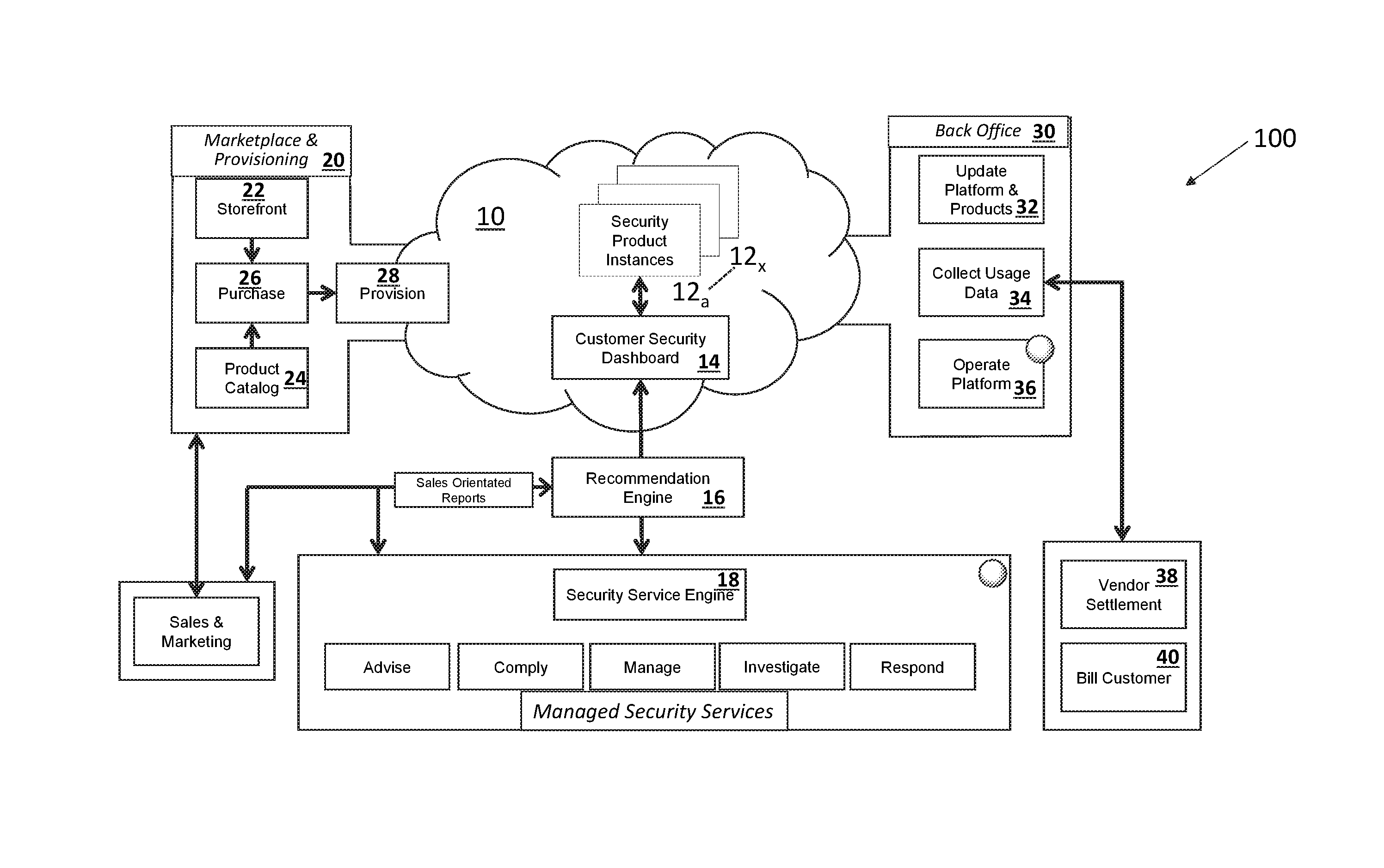
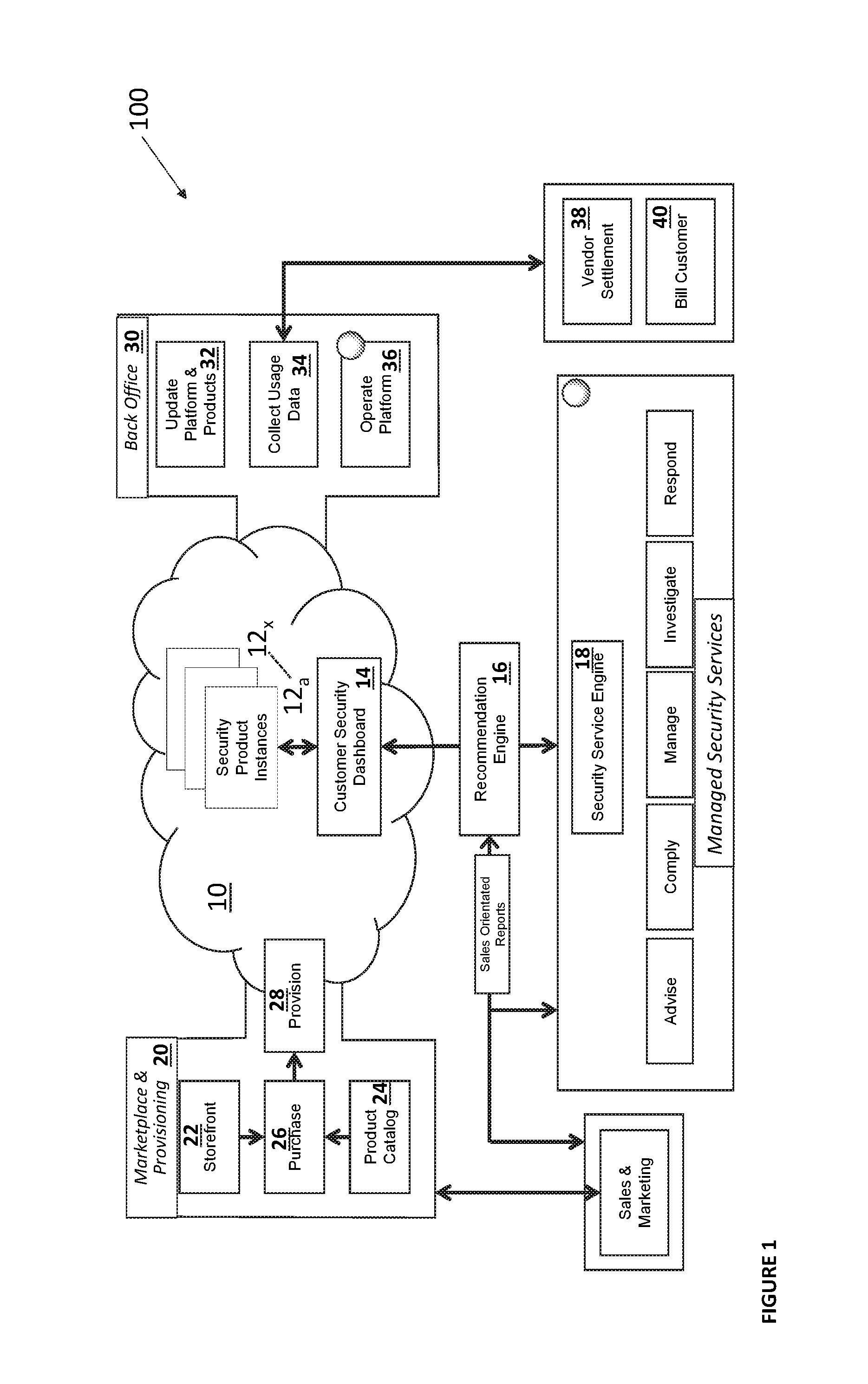
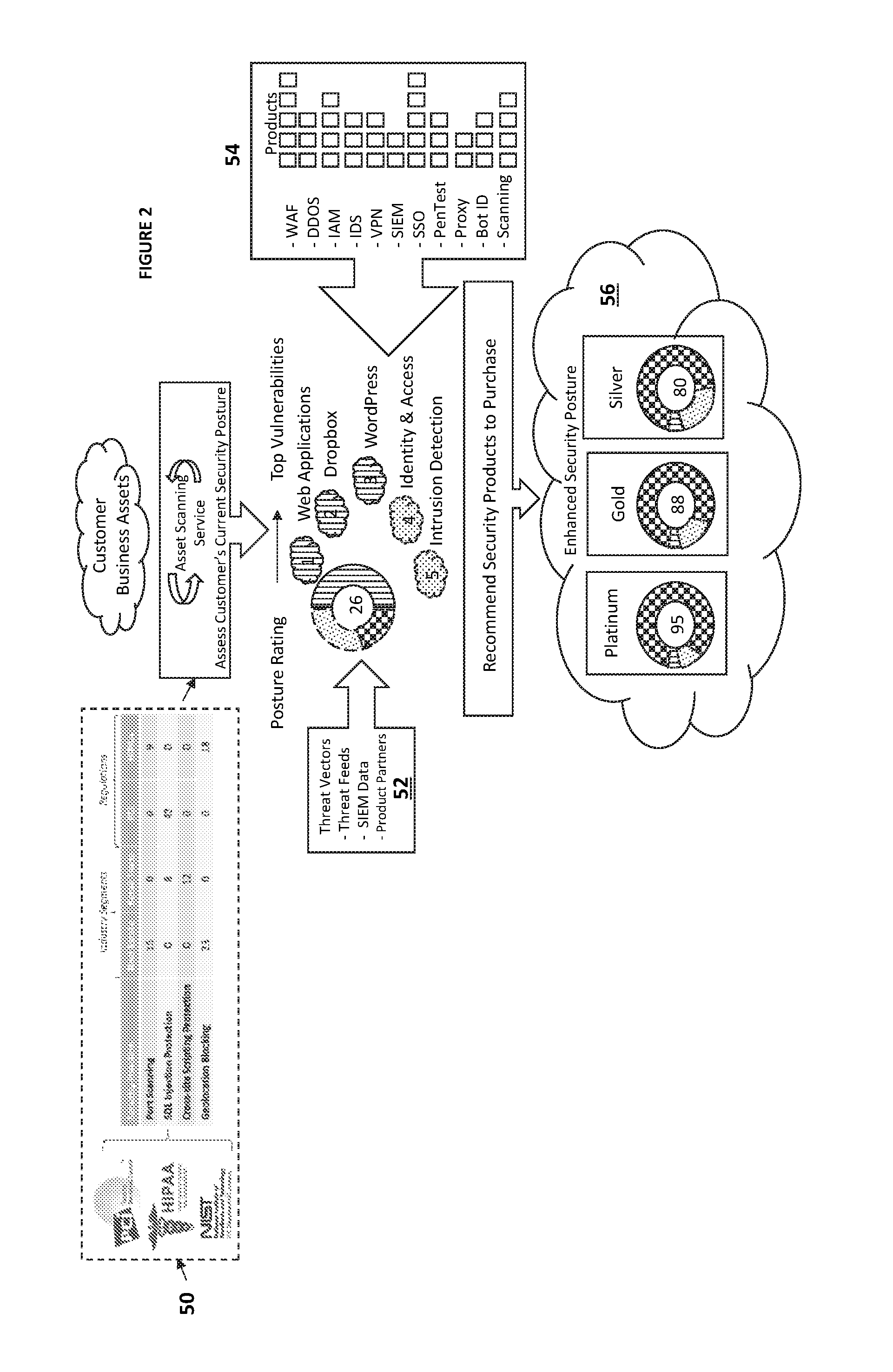
[0011]In a first embodiment, a system for the automated provisioning and tracking of cloud-implemented security products for protecting an entity's digital assets includes: a first application programming interface for receiving security product data from one or more security product vendors and storing the security product data in a relational database; a second application programming interface for receiving entity data and storing the entity data in the relational database, wherein the entity data is associated with one or more digital assets of the entity and further wherein the digital assets are accessible through the entity's virtual private cloud; a processing engine for comparing the received entity data with the received security product data and providing at least one recommendation to the entity for a security product from the one or more security product vendors to protect one or more digital assets of the entity; a provisioning component for receiving instructions from...
second embodiment
[0012]In a second embodiment, a method for facilitating the automated provisioning and tracking of cloud-implemented security products for protecting an entity's digital assets includes: receiving via a first application programming interface security product data from one or more security product vendors and storing the security product data in a relational database; receiving via a second application programming interface entity data and storing the entity data in the relational database, wherein the entity data is associated with one or more digital assets of the entity and further wherein the digital assets are accessible through the entity's virtual private cloud; comparing by a processing engine the received entity data with the received security product data; providing to the entity via the first application programming interface at least one recommendation for a security product from the one or more security product vendors to protect one or more digital assets of the entity...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com