System and method for managing security access for users to network systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
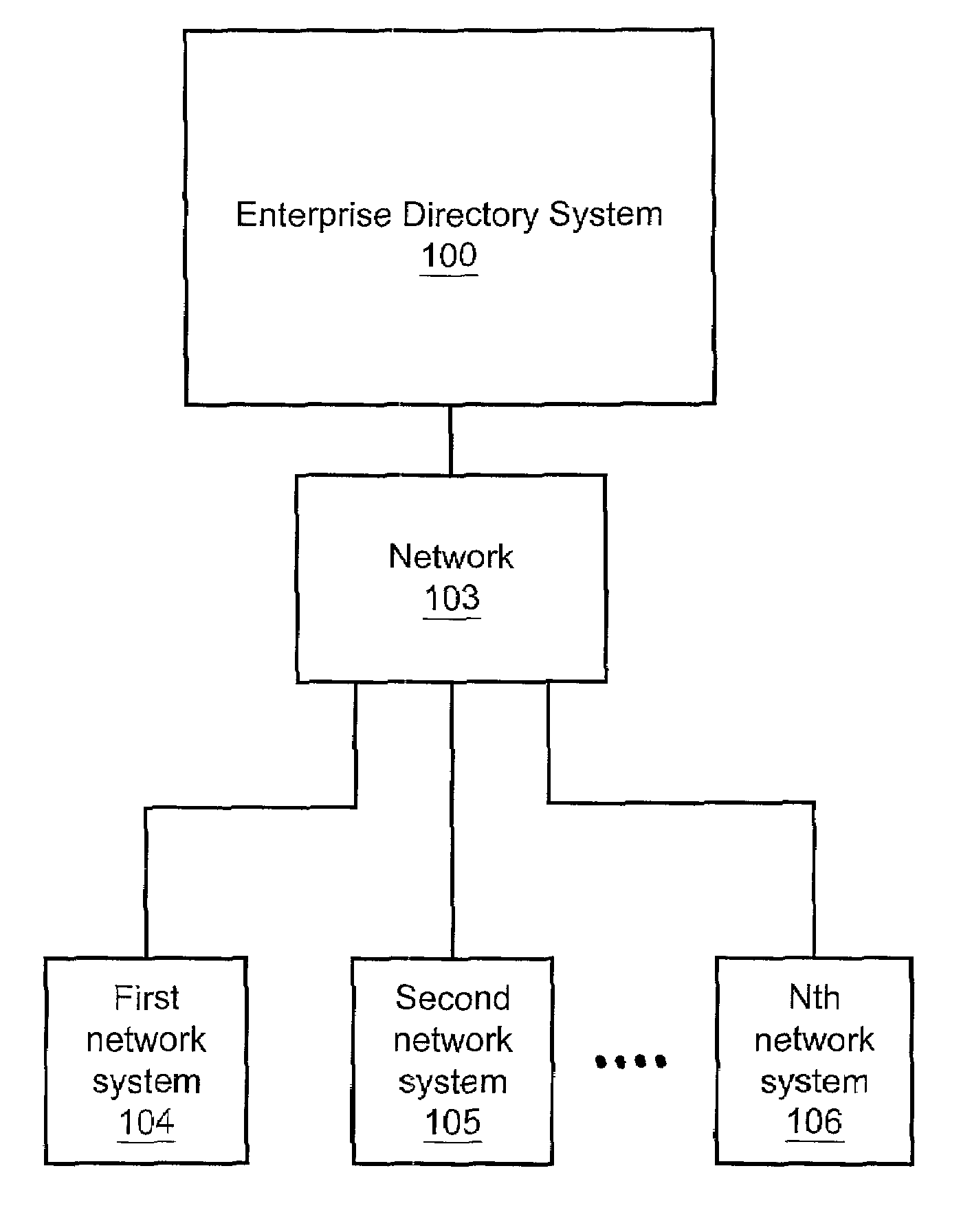
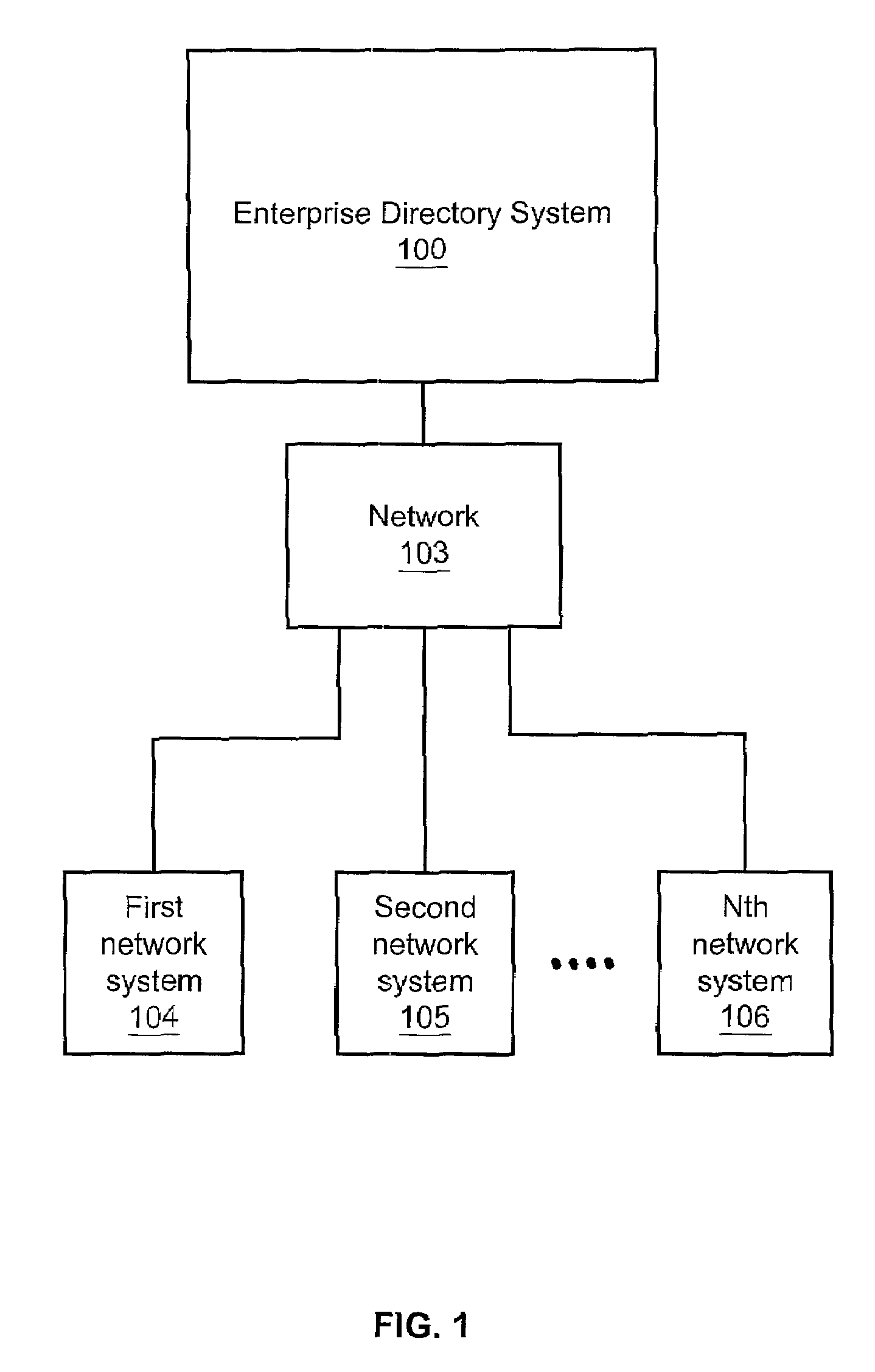
Enterprise Directory System FIG. 1:
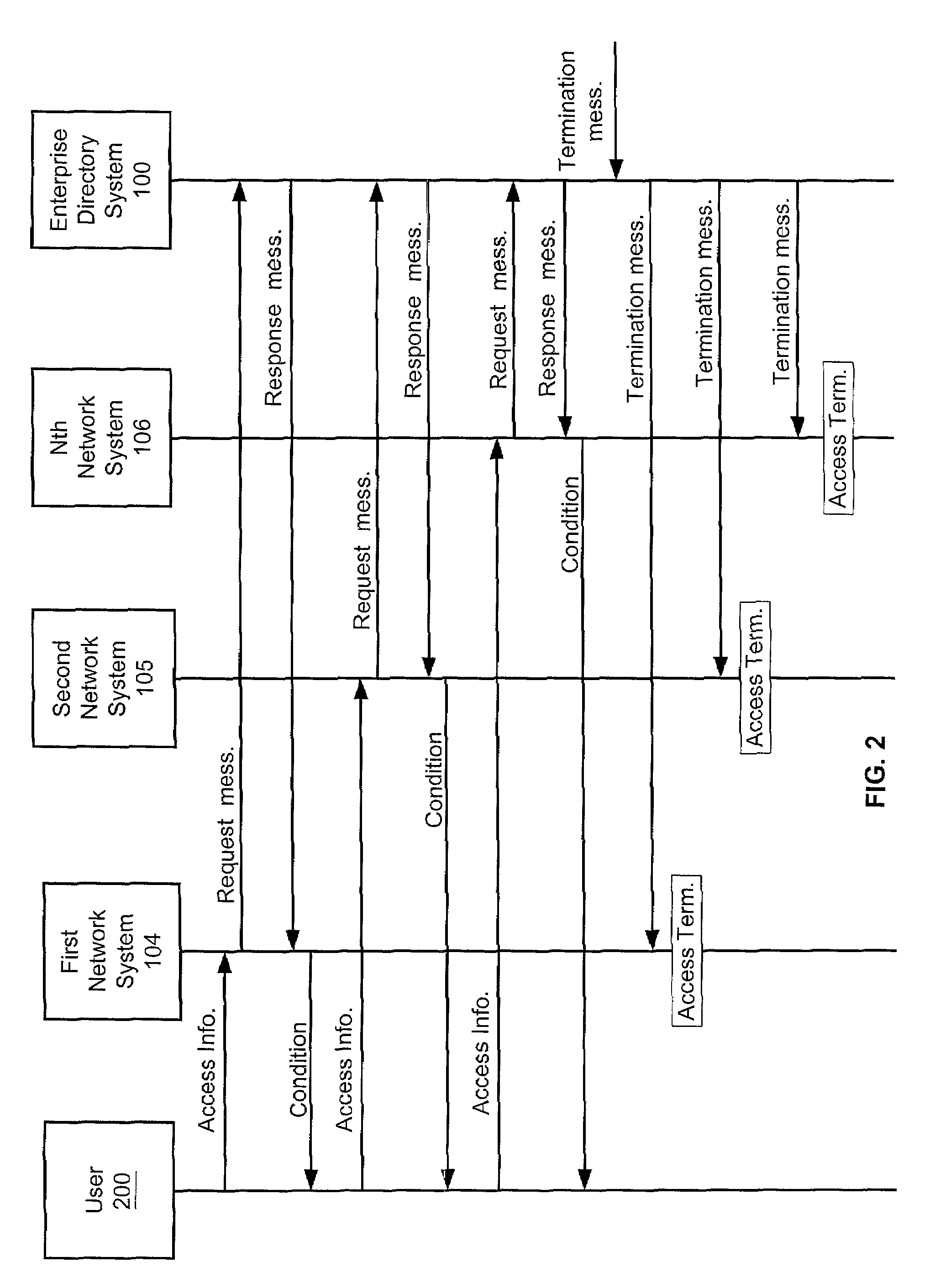
[0019]FIG. 1 depicts an enterprise directory system 100, a network 103, a first network system 104, second network system 105, and Nth network system 106. The network 103 is connected to the enterprise directory system 100 and the network system 104, the network system 105, and the network system 106. Those skilled in the art will appreciate that numerous other network systems could be connected to the network 103 although only network systems 104-106 are depicted on FIG. 1 for clarity.
[0020]The network 103 could be one or more networks that connect the network systems 104-106. For example, the network 103 could comprise a Local Area Network (“LAN”) or a Wide Area Network “(WAN”) or a LAN connected to a WAN. The network 103 could also be interconnected with other WANs by a data network, such as an IP, Frame Relay or ATM network. In another example of the present invention, the network 103 could be connected to other wireline or wireless networks. F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com