Device and method for preventing unauthorized use of information processing device
An information processing equipment and unauthorized technology, applied in the direction of unauthorized/fraudulent telephone prevention, branch equipment, selection device, etc., can solve the problems of inability to guarantee the security of boycotting information processing equipment, unaffordable passwords, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
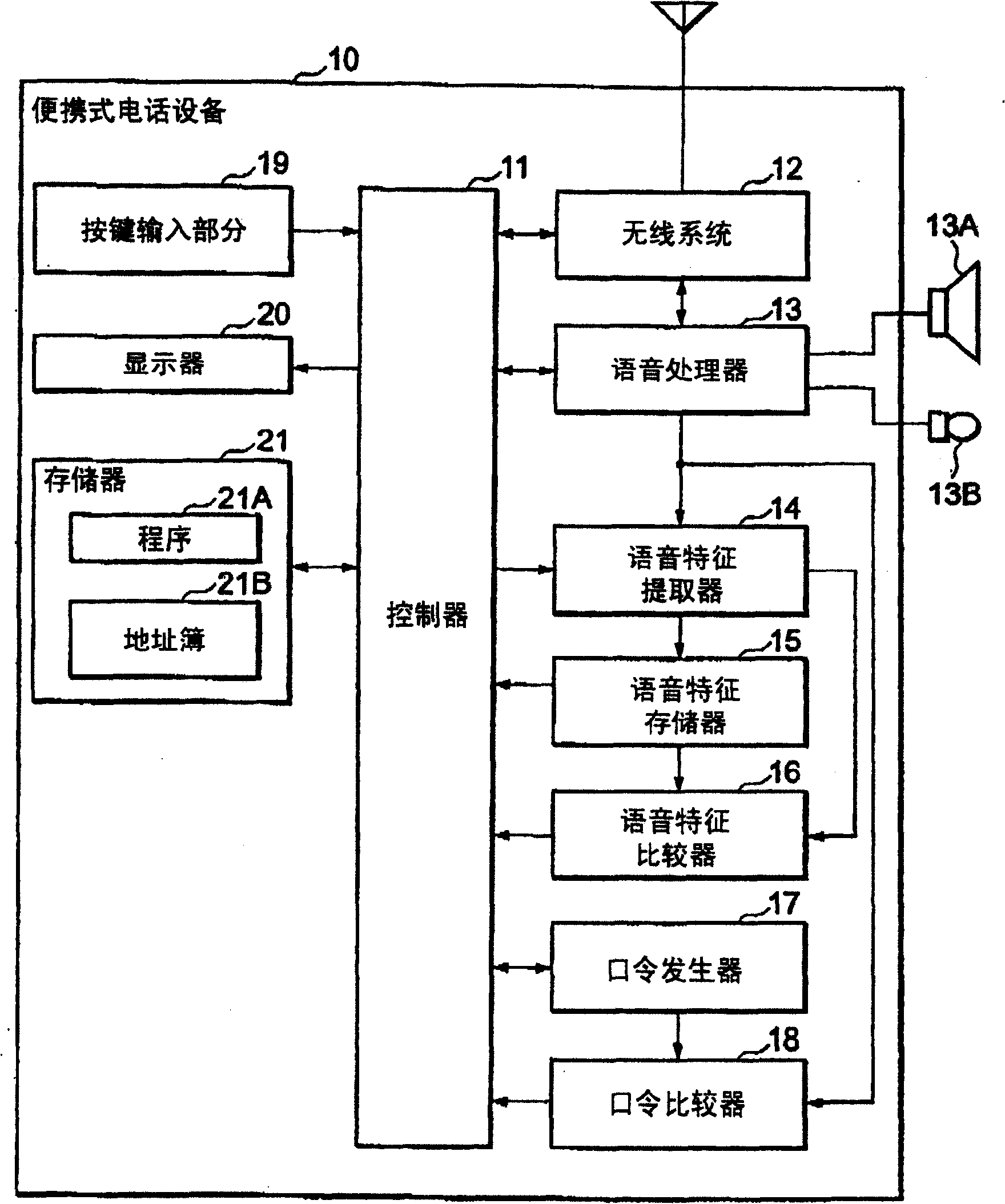
[0021] refer to figure 1 , the portable telephone device 10 according to the first embodiment of the present invention is equipped with a controller 11 for controlling the entire operation of the portable telephone device 10 including control for preventing unauthorized use. The controller 11 may be a program-controlled processor such as a DSP (Digital Signal Processor), on which a control program as described later runs.
[0022] The portable telephone device 10 also has a wireless system 12 and a voice processor 13 for voice and data communication over a radio channel under the control of the controller 11 .
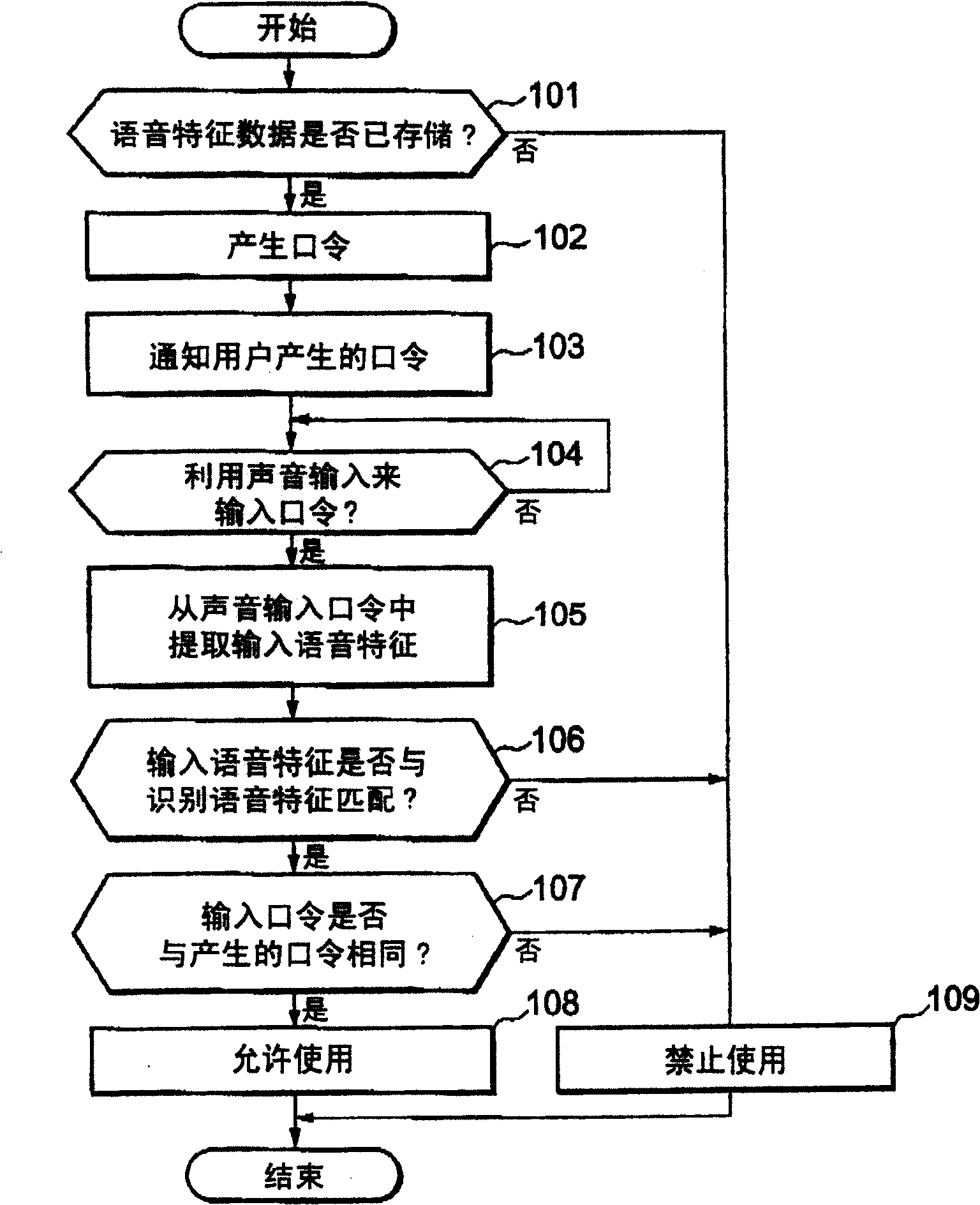
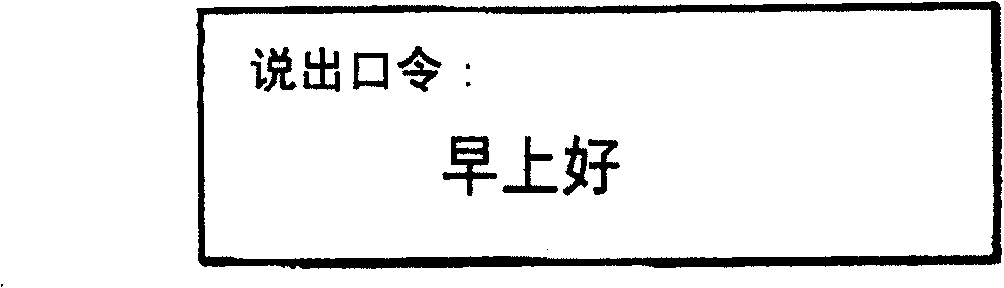
[0023] The speech processor 13 has a speaker (telephone handset) 13A and a microphone (telephone handset) 13B connected thereto. In the case of telephone communication, the data received by the microphone 13B is speech coded for transmission over the radio system 12 . In the case of user authentication, the input sound received by the microphone 13B is converted into...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com