Method for realizing end-to-end phonetic encryption
A voice encryption and voice technology, applied in the field of encrypted transmission, can solve the problems of affecting the transmission efficiency of the system, the reduction of single-frame coding efficiency, and the increase of redundant data, so as to improve transmission efficiency, reduce coding overhead, and reduce redundant data. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
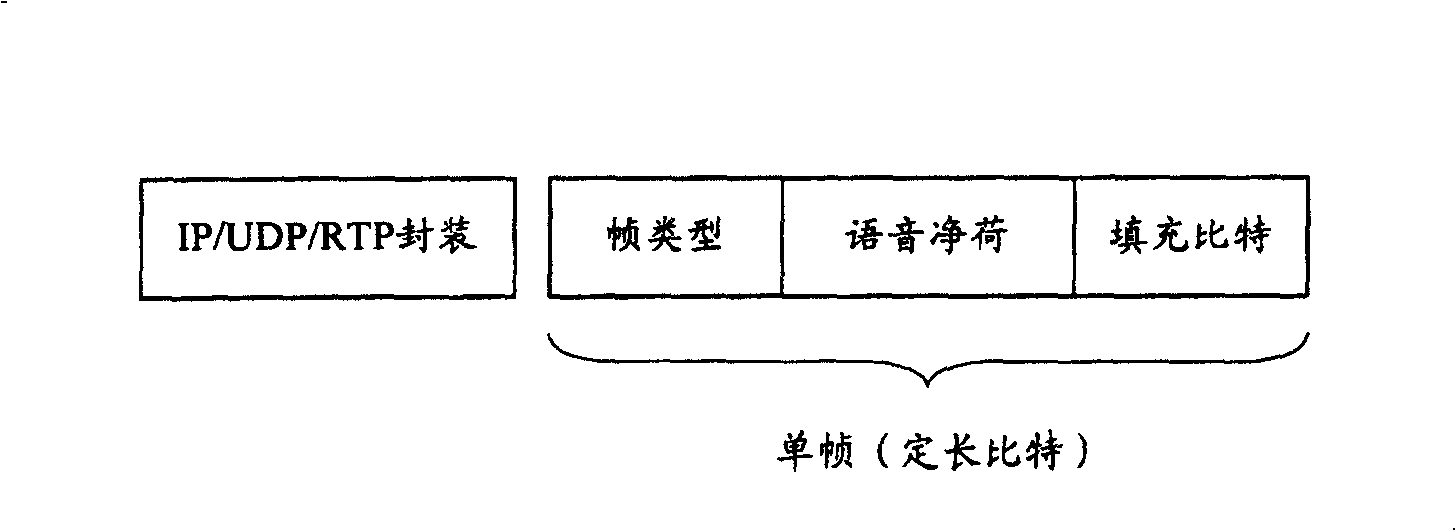
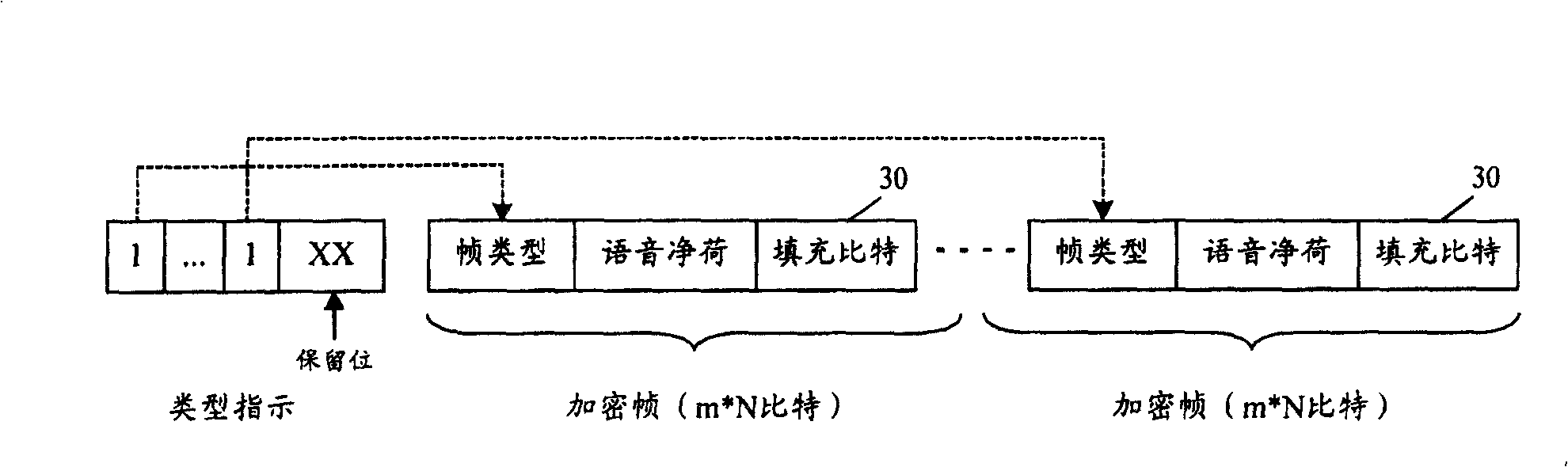
[0026] The core idea of the present invention is: before encoding, multiple single frames are combined, and then the encrypted frames are sent to the encoder for speech encoding and encryption. When realizing the combination of multiple single frames, multiple single frames of fixed length can be combined together, and filling bits can be supplemented in each single frame; multiple single frames of different lengths can also be combined together, Filling bits are added after the frame.
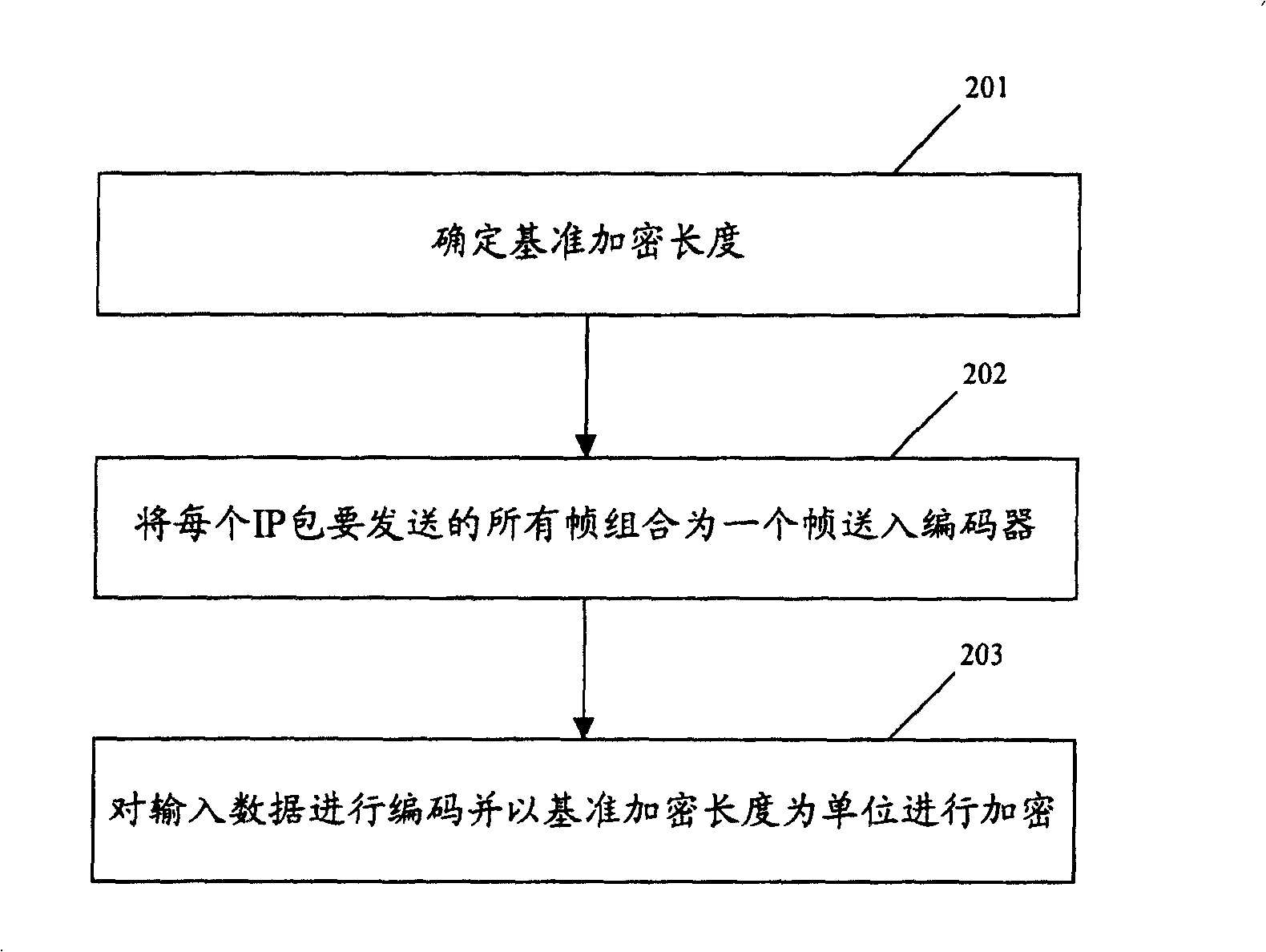
[0027] The method for realizing end-to-end voice encryption in the present invention is as follows: figure 2 shown, including the following steps:
[0028] Step 201: When performing voice transmission between two mobile terminals, before encoding and encrypting the voice data, the sending end first determines the reference encryption length according to the encrypted data length required by the current communication system;
[0029] Step 202: Then, combine all the single frames to be sent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com