Method of selecting safety communication algorithm
A technology for secure communication and algorithm, applied in secure communication devices, security devices, wireless communication, etc., can solve the problem of not providing the priority of encryption algorithm, and achieve the effect of small impact, simple implementation and less modification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
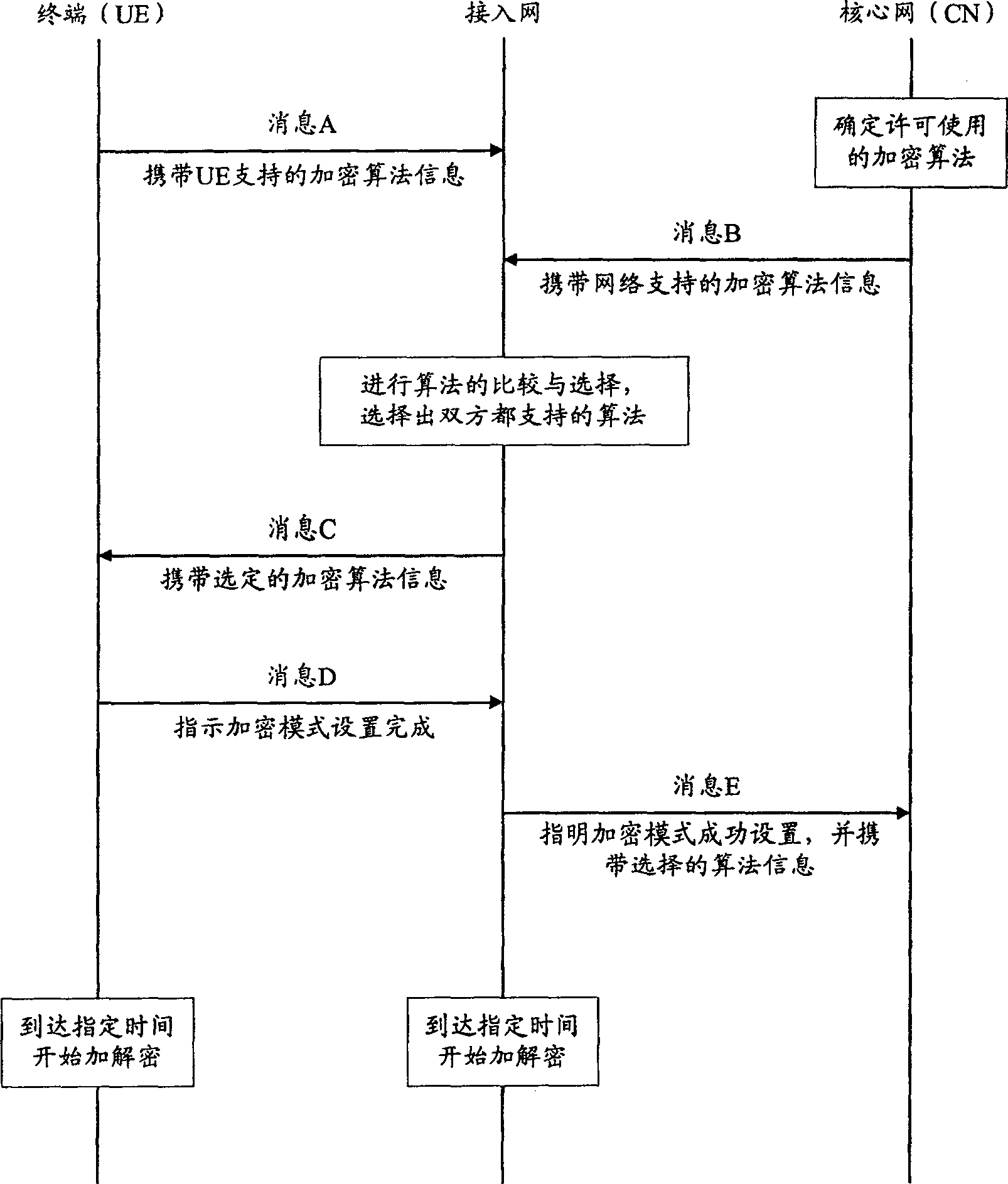
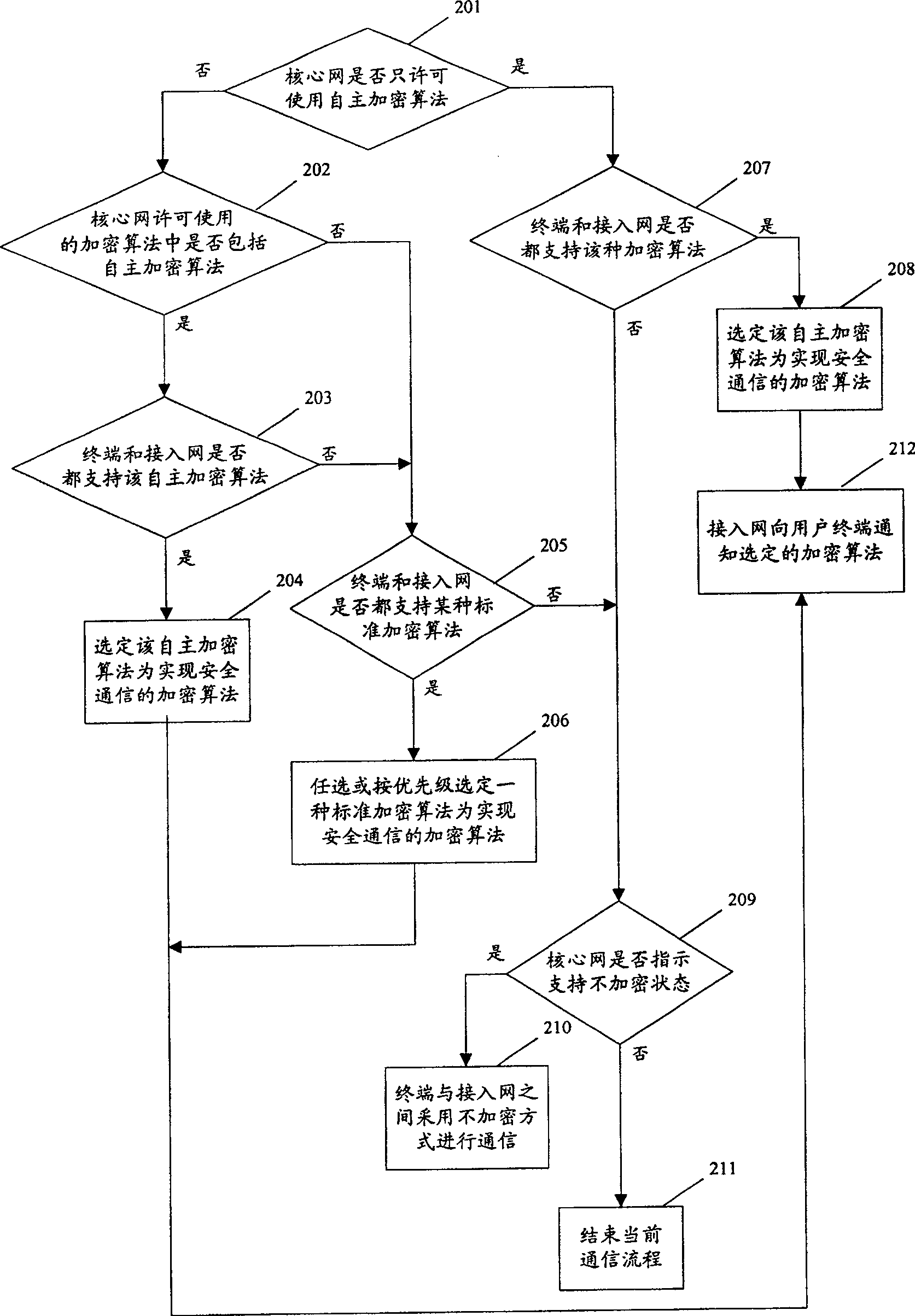
[0041] The secure communication algorithm mentioned in the present invention may be an encryption algorithm or an integrity algorithm. The following will take the encryption algorithm as an example and further describe the present invention in detail in conjunction with the accompanying drawings and embodiments.
[0042]The premise that the present invention realizes is: if multiple licensed standard encryption algorithms are defined in the standard, in order to support international roaming in all countries in the world, the system is required to support all standard encryption algorithms, which is exactly what all existing 3G mobile communication systems conditions that must be met.
[0043] Moreover, for countries or operators with special encryption algorithm requirements, in addition to supporting all the above-mentioned standard encryption algorithms, the mobile communication system must also support at least one set of self-developed non-standard encryption algorithms. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com