Address renewing method based on network key exchange protocol
A technology of address update and network key, applied in the field of virtual private network and network, to prevent bombing and ensure physical reachability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
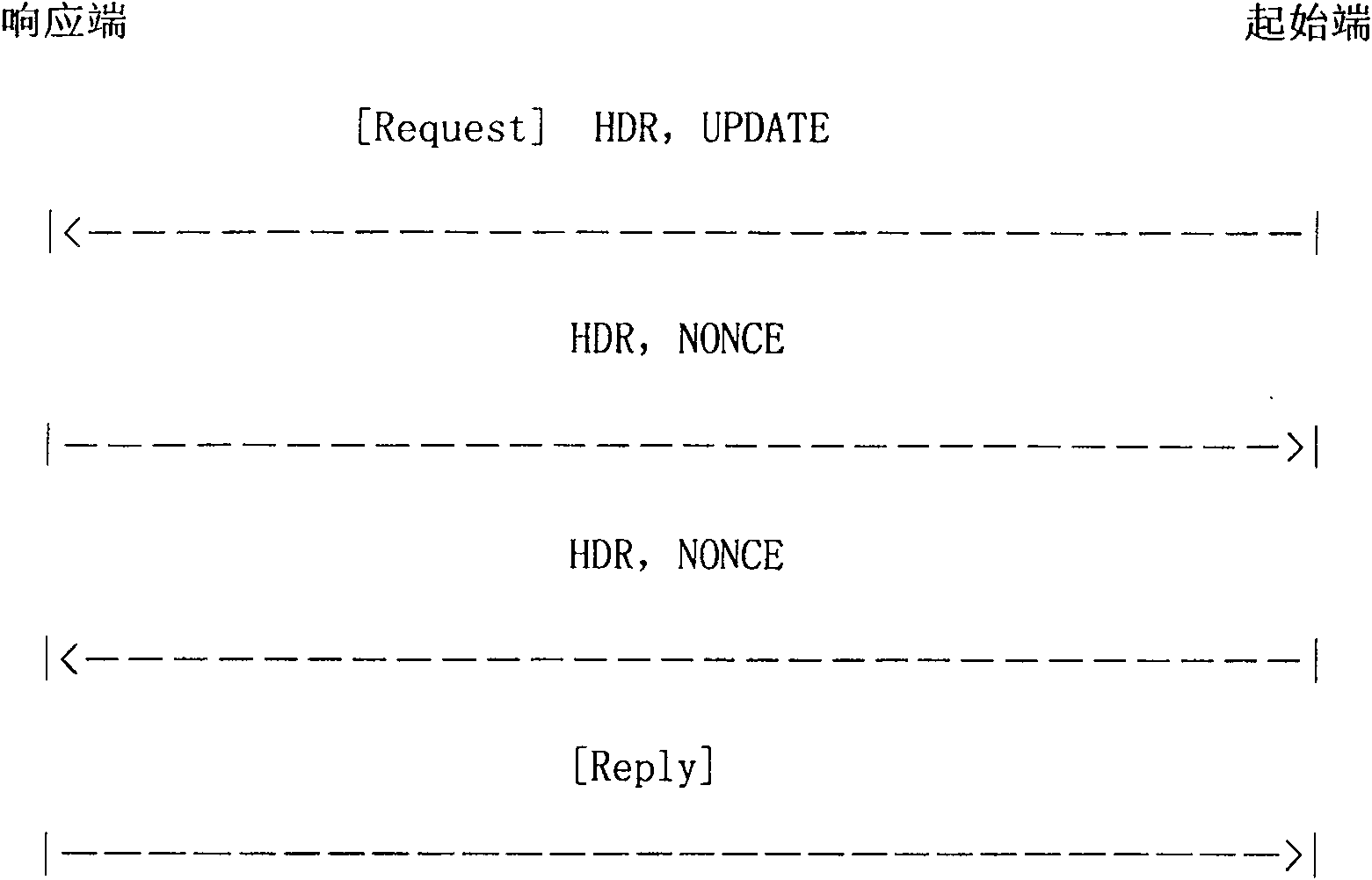
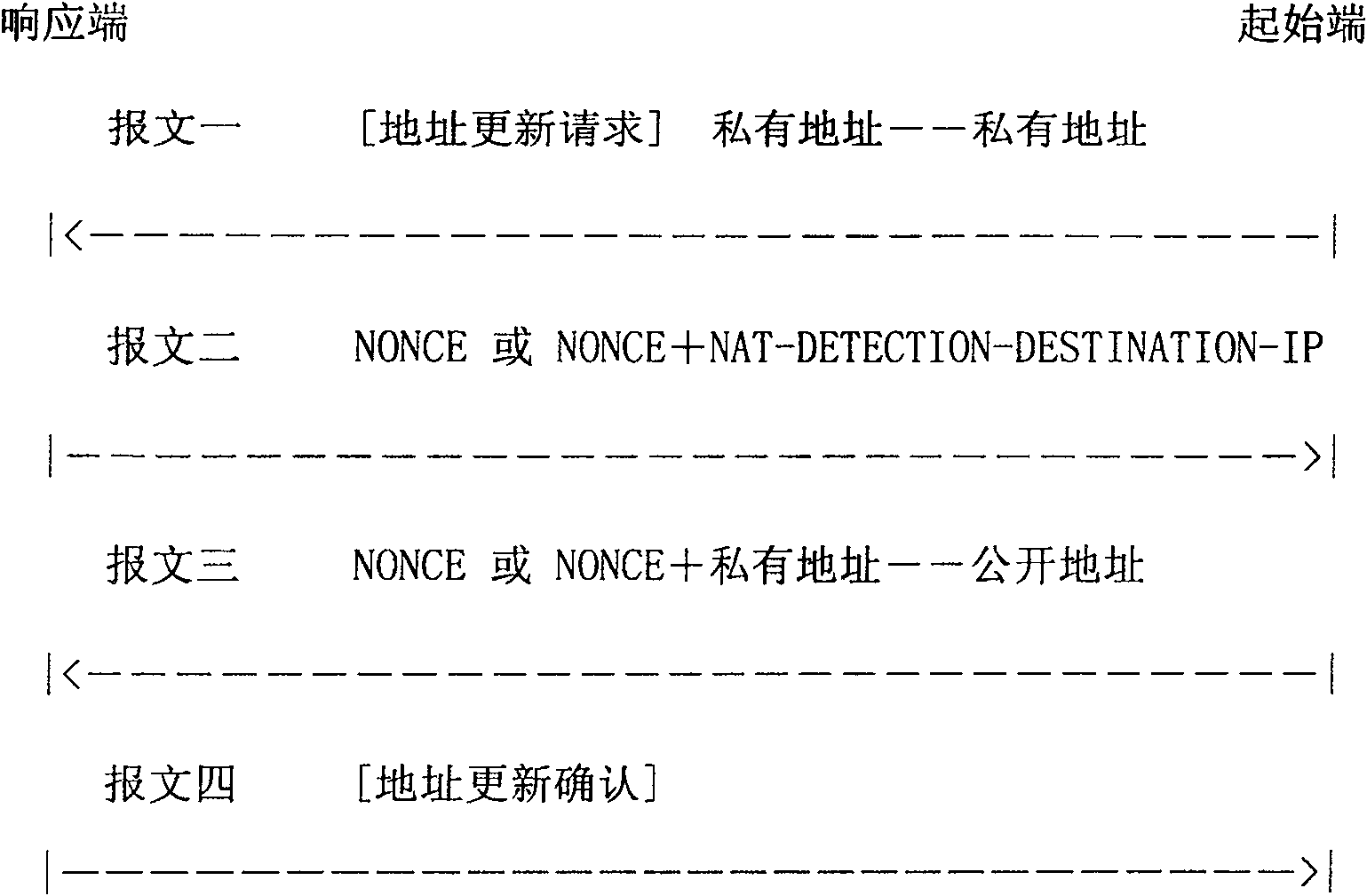
[0044] The present invention provides an address updating method based on the network key exchange protocol. The hosts at the starting end and the responding end need to maintain a binding address list of private addresses and public addresses. The private address is the IP address of the originating host itself. This IP address may be a private address in a certain subnet, which is used to identify the security association; the public address is the address that is changed after the data packet passes through NAT. The public address is the real address on the Internet. NAT traversal can be completed by adding the IP address of the transport layer port number to the IP address. The bind address list is divided into two parts:
[0045] One part is the start-end host binding address list, and the list entries are the start-end host's private IP address and its public address. When the originating host obtains a new private IP address (if there is no NAT, it obtains a new public...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com