Safety interacting method for user terminal access softswitch system
A technology of user terminal and interaction method, which is applied in the field of secure interactive two-way authentication and key distribution, which can solve problems such as low password security and replay attacks, and achieve the effects of avoiding algorithm instability, avoiding attacks, and meeting communication security requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
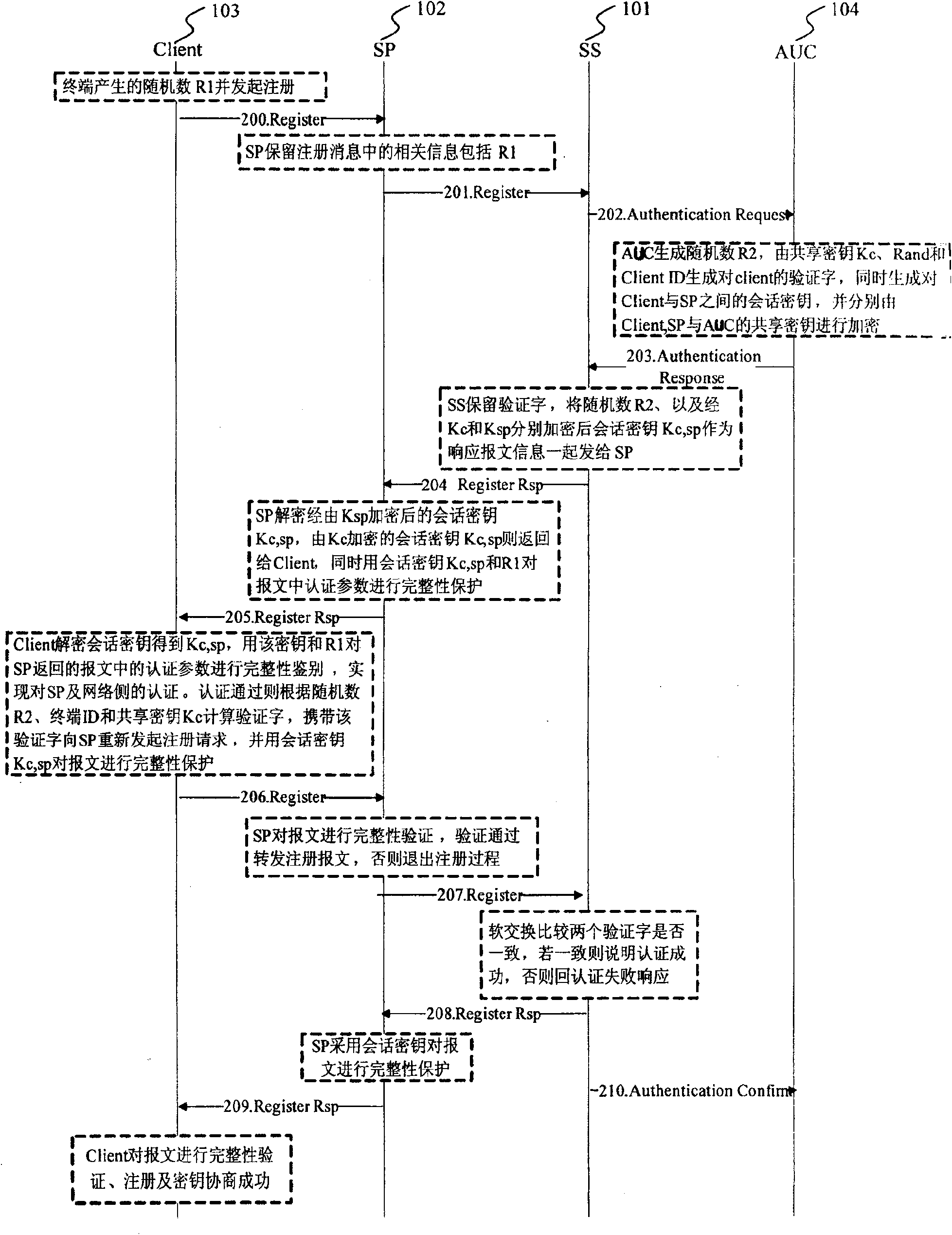
[0027] The implementation of the technical solution will be further described in detail below in conjunction with the accompanying drawings.
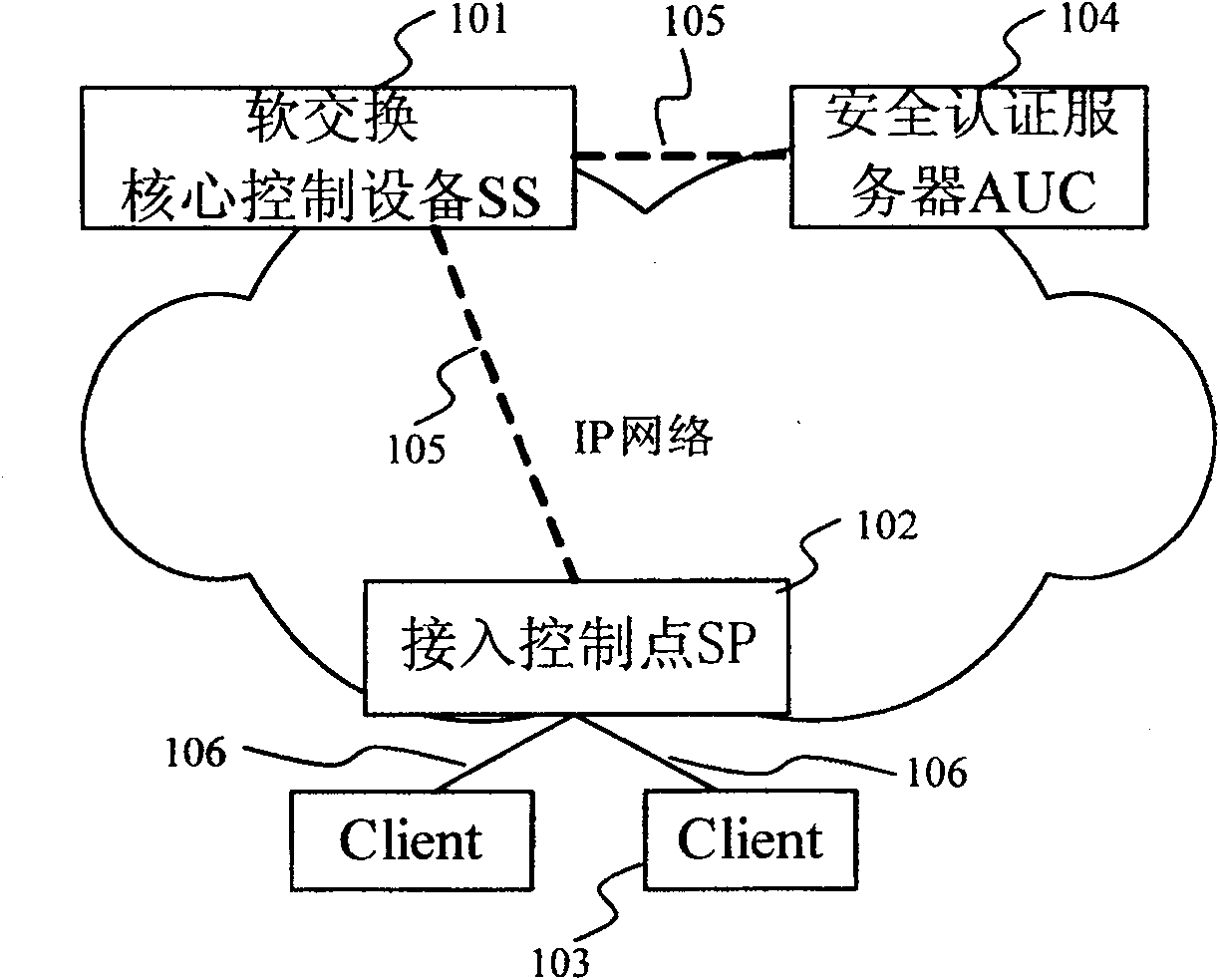
[0028] see figure 1 As shown in the figure, it describes the schematic diagram of the softswitch network access domain. Among them, SS (Soft Switch) refers to the soft switch core control device 101, SP (Signing Point) refers to the access control point 102, Client refers to the user terminal 103, and AUC (Authentication Center) refers to the security authentication server / authentication center 104; figure 1 The dotted line 105 in the figure means that the security authentication parameters of each functional entity are stored on the security authentication server AUC 104, while the solid line 106 indicates the communication connection relationship between each functional entity.
[0029] exist figure 1 Among them, in the IP network architecture based on softswitch technology, there is at least one softswitch core control device 101;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com