UMTS authenticating vector generating method based on service network label
A service network and authentication vector technology, which is applied in the field of UMTS authentication vector generation based on the service network logo, can solve problems such as unguaranteed, relocation attacks, user information leakage, etc., and achieve the effect of improving security strength and preventing relocation attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The security assumption of the present invention is: the home network and the service network are legal and safe, and the UTRAN is not safe, which conforms to the actual situation of mobile communication.
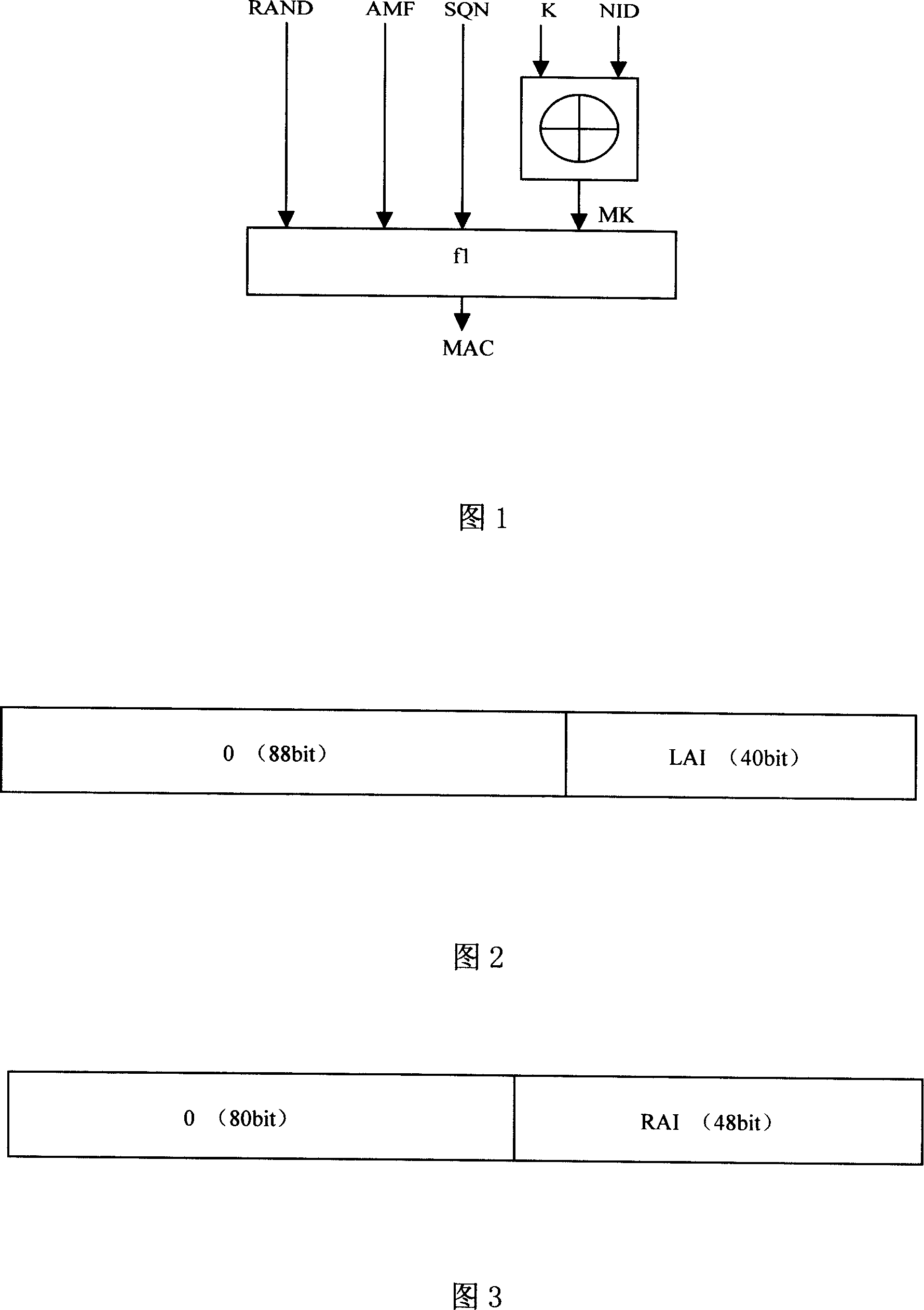
[0017] As shown in Fig. 1, the present invention based on the UMTS authentication vector generation method of the service network mark, by modifying the MAC in AUTH, one of the five tuples of the UMTS authentication vector, makes the MAC include the information of the service network.
[0018] Described MAC still adopts f1 algorithm described in 3GPP standard TS33.102 to calculate, and it comprises four input parameters: AMF, SQN, RAND and MK, respectively correspond to the AMF of original MAC generation algorithm (3GPP TS33.102), SQN , RAND and K.
[0019] The intermediate quantity MK is calculated according to the following formula:
[0020] MK=KNID (1)
[0021] Among them, K is the key shared by HN and UE, NID is the service network identifier, and the length i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com