Patents
Literature
39 results about "48-bit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer architecture, 48-bit integers can represent 281,474,976,710,656 (2⁴⁸ or 2.814749767×10¹⁴) discrete values. This allows an unsigned binary integer range of 0 through 281,474,976,710,655 (2⁴⁸ − 1) or a signed two's complement range of -140,737,488,355,328 (-2⁴⁷) through 140,737,488,355,327 (2⁴⁷ − 1). A 48-bit memory address can directly address every byte of 256 tebibytes of storage. 48-bit can refer to any other data unit that consumes 48 bits (6 octets) in width. Examples include 48-bit CPU and ALU architectures are those that are based on registers, address buses, or data buses of that size.
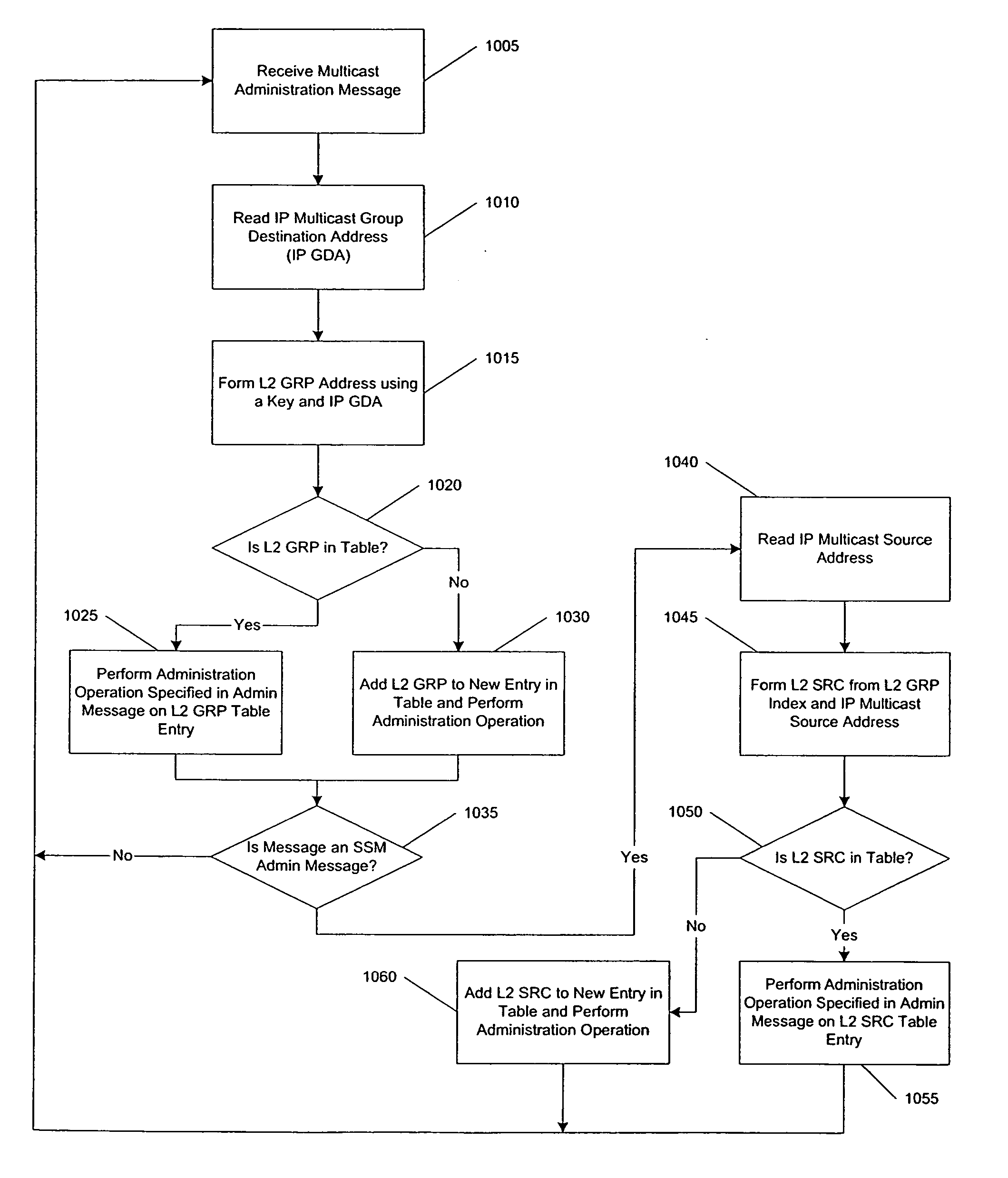
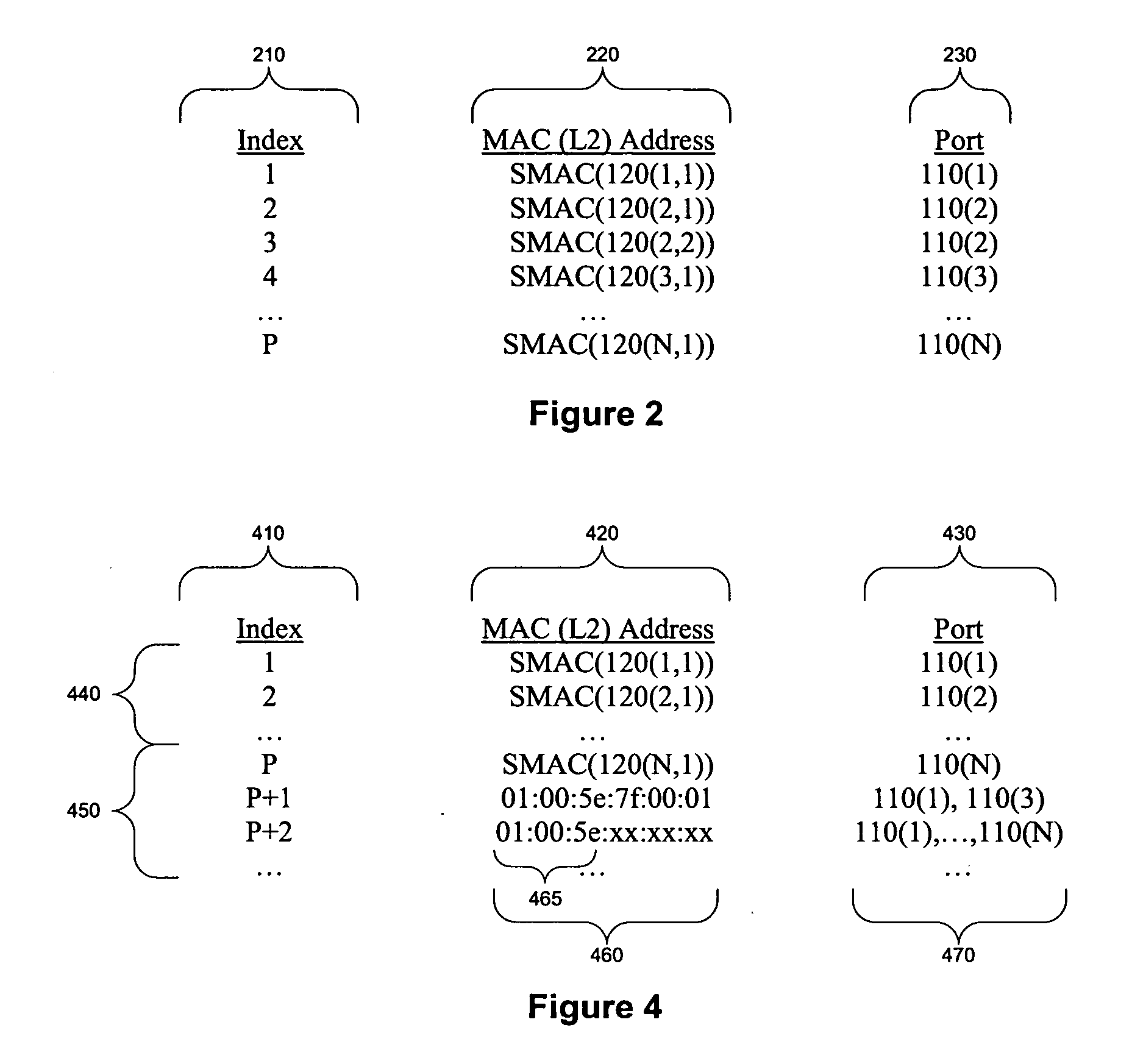
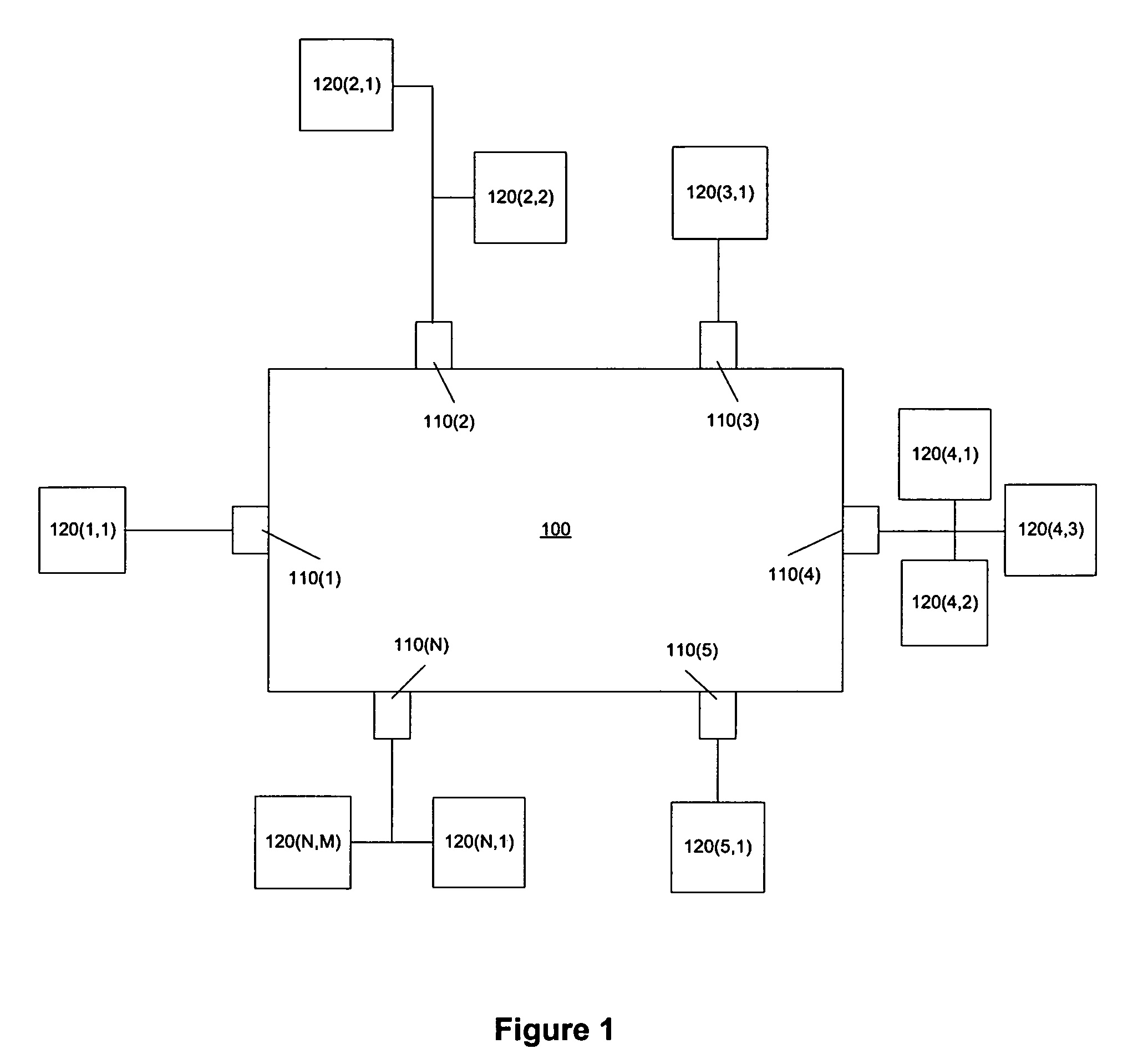
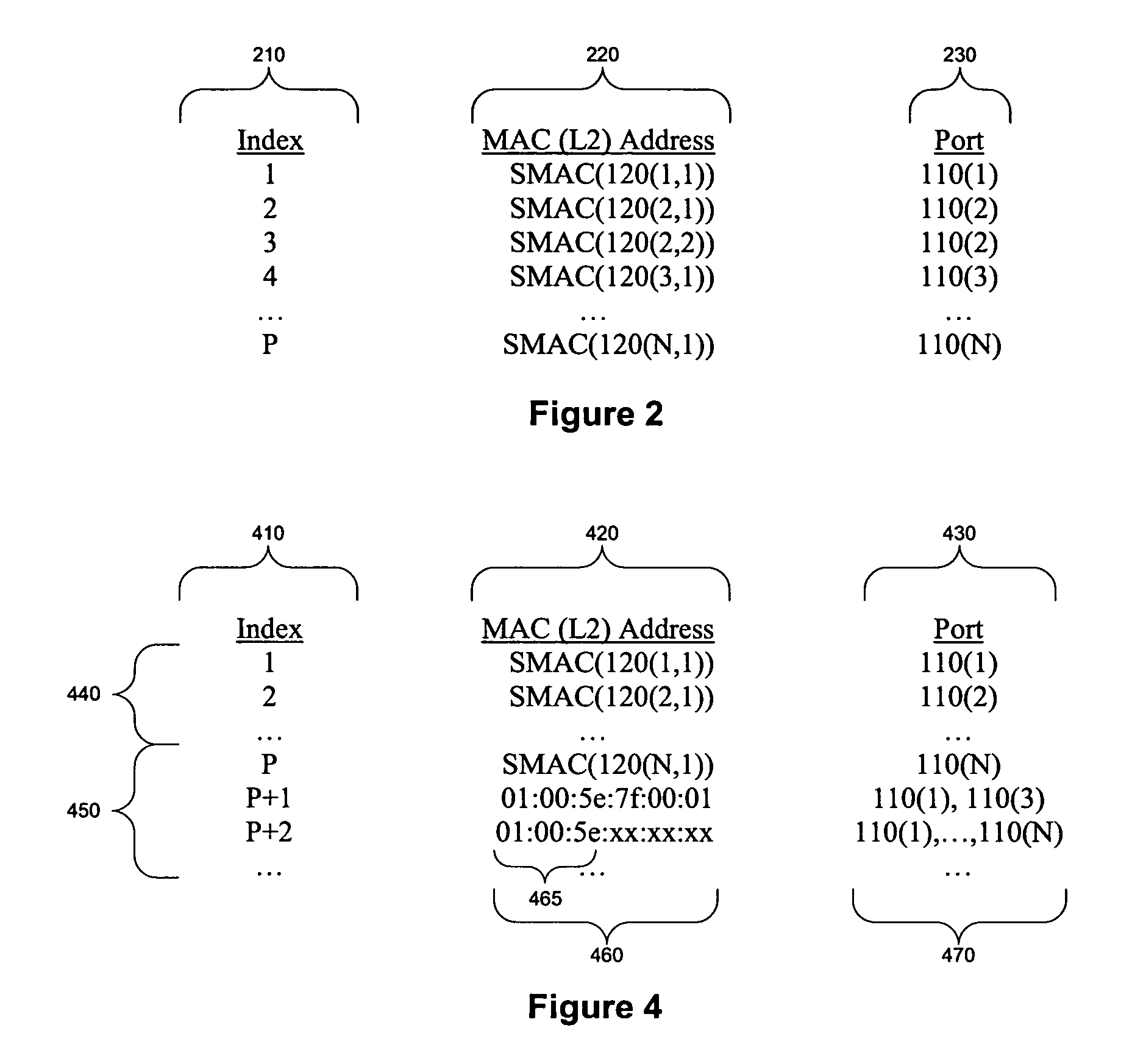
Performing extended lookups on mac-based tables
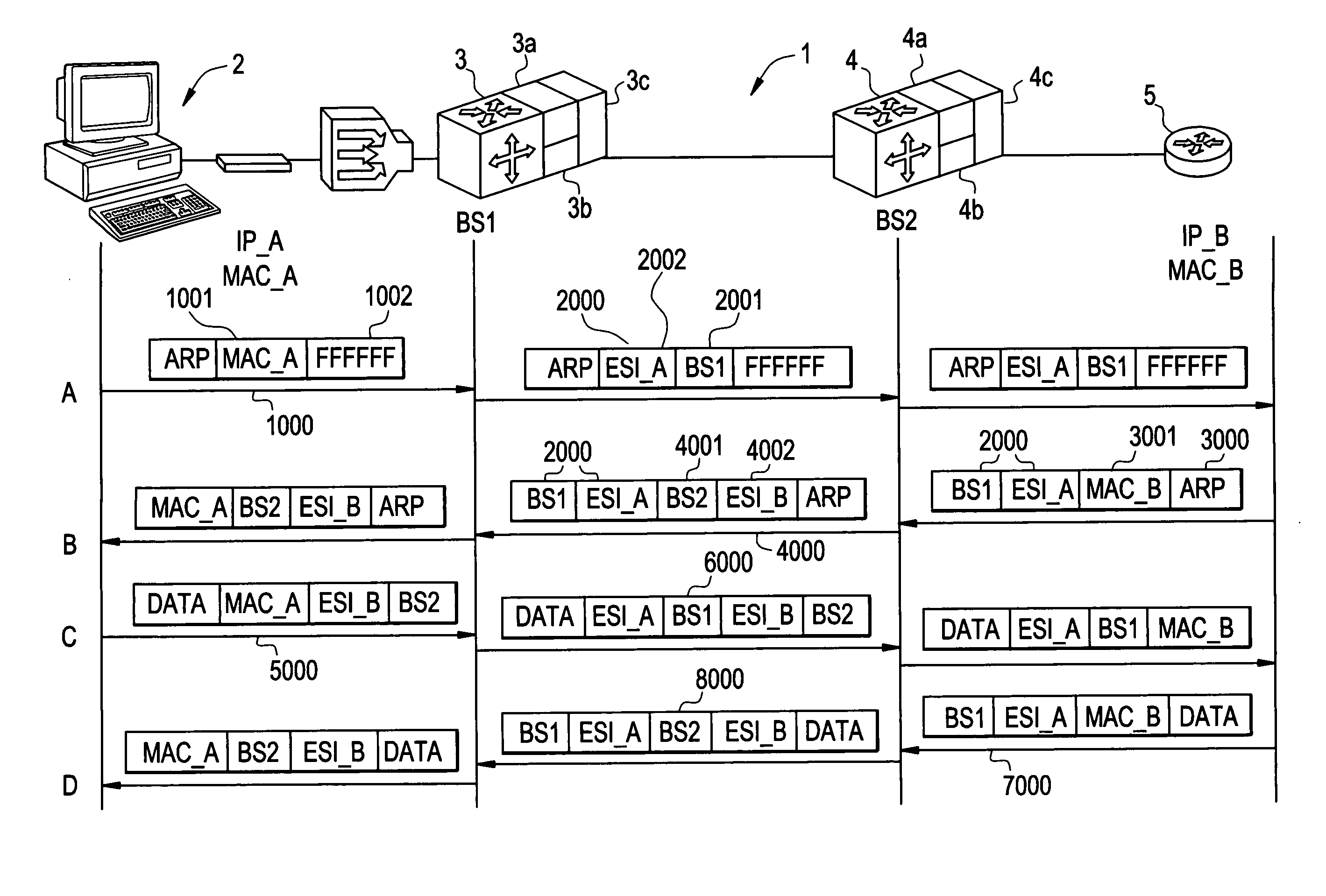
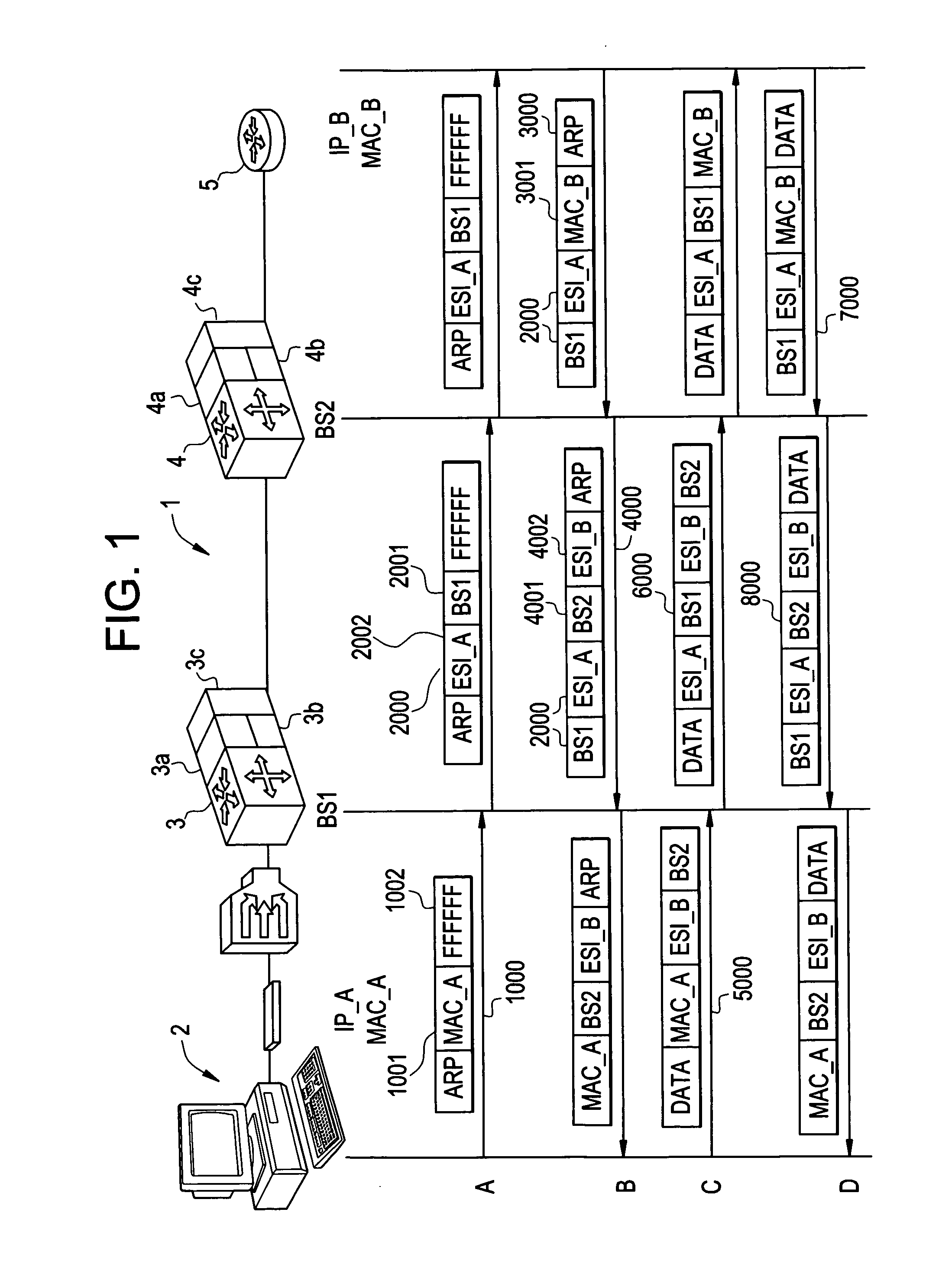
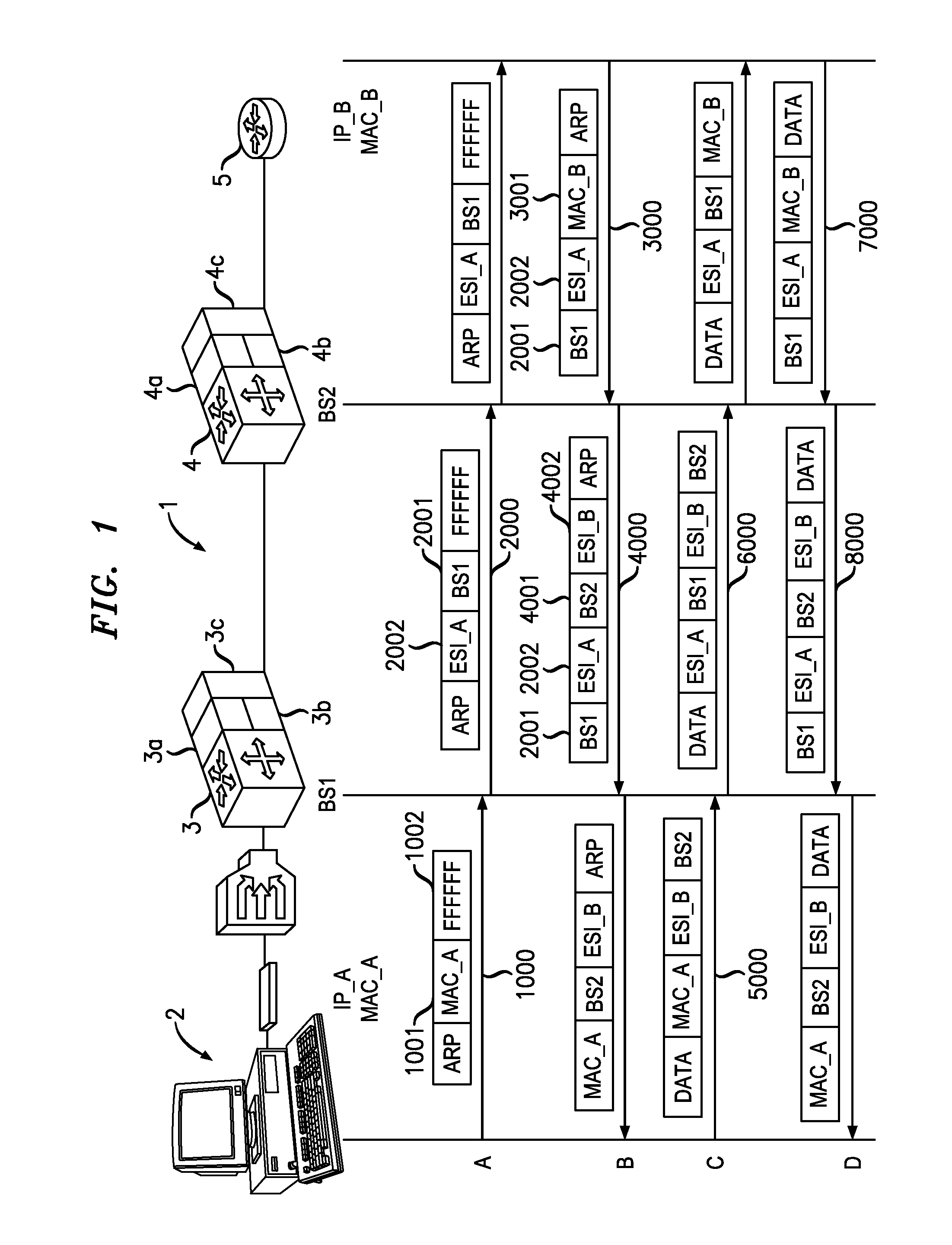
ActiveUS20060221960A1Special service provision for substationTime-division multiplexInternet trafficIp address
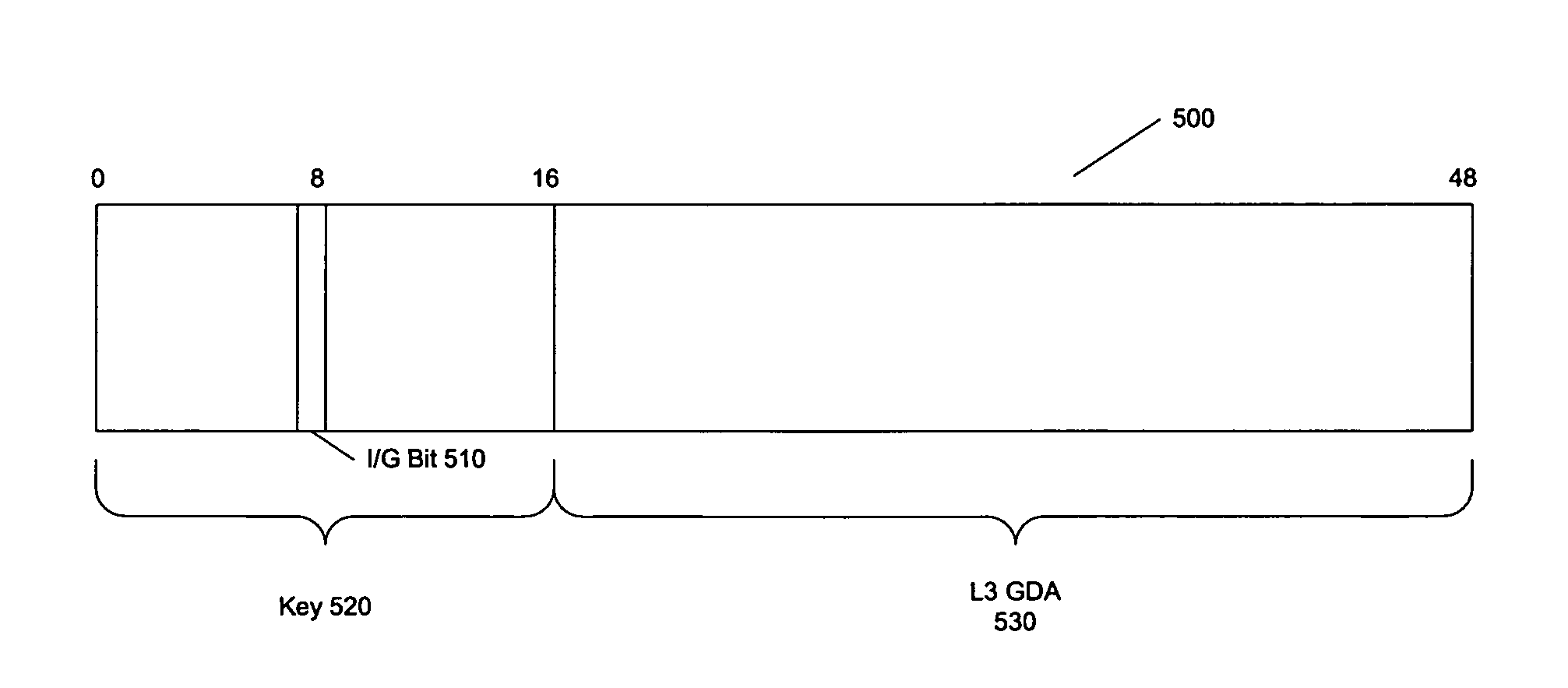
A method, system, and computer program product are presented to optimize OSI Level 2 switch forwarding of frames comprising IP addresses, 802.1 QinQ VLAN identifiers, multi-protocol label switching labels, and any other usable information meaningful to derive an L2 forwarding result on frames. In one embodiment, a 16-bit key is included as a prefix to a 48-bit OSI Level 2 address entry, thereby allowing the inclusion of a 32-bit OSI Level 3 address in the lookup table (e.g., a complete IP version 4 address). Implementations of such a solution are presented to resolve address aliasing issues experienced with multicast group destination addresses, including single source multicast. Solutions to optimizing forwarding of frames in an IEEE 802.1 QinQ environment are also presented. A result of these implementations can be reduction of the amount of unnecessary network traffic generated by a network switch incorporating such an OSI Level 2 address lookup table.
Owner:CISCO TECH INC
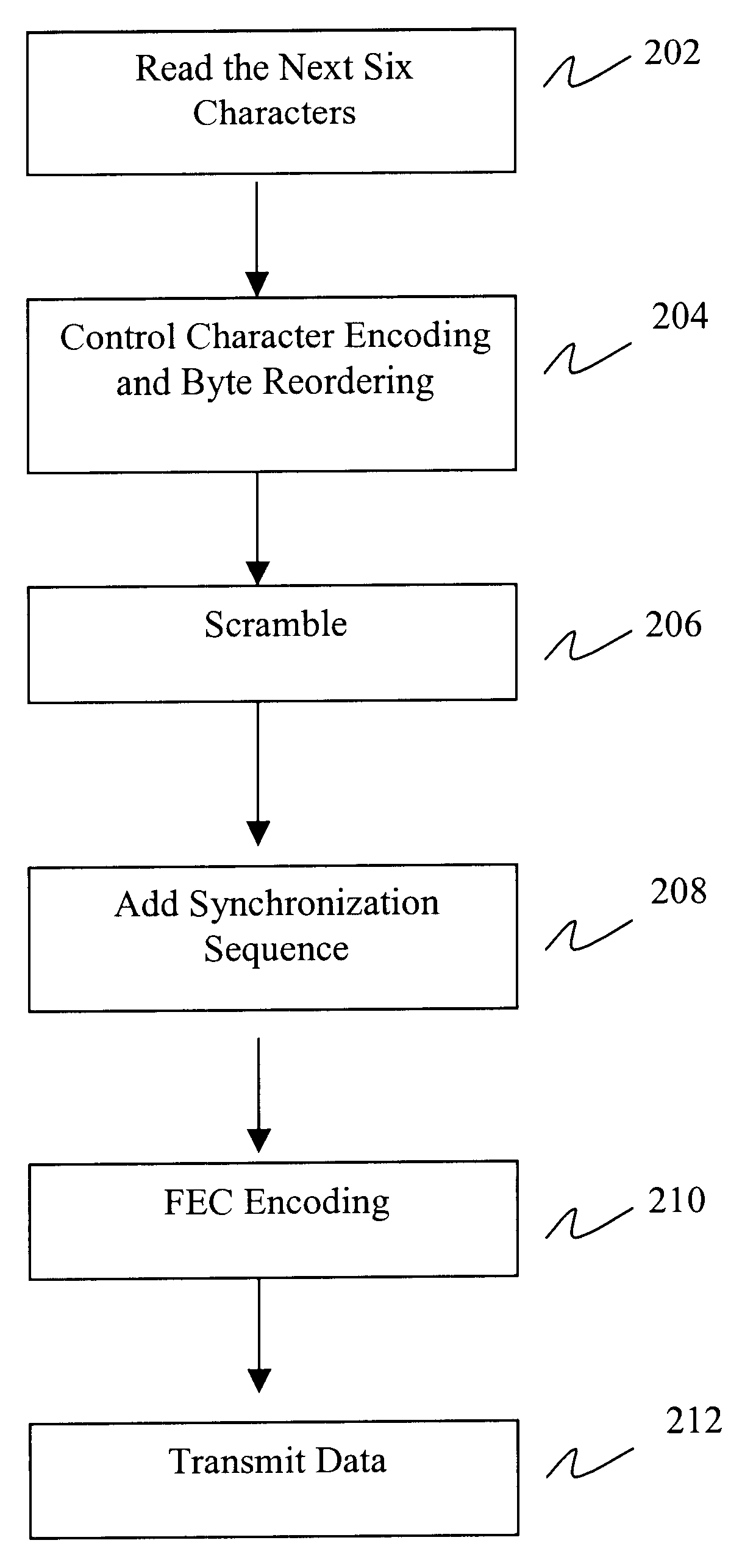
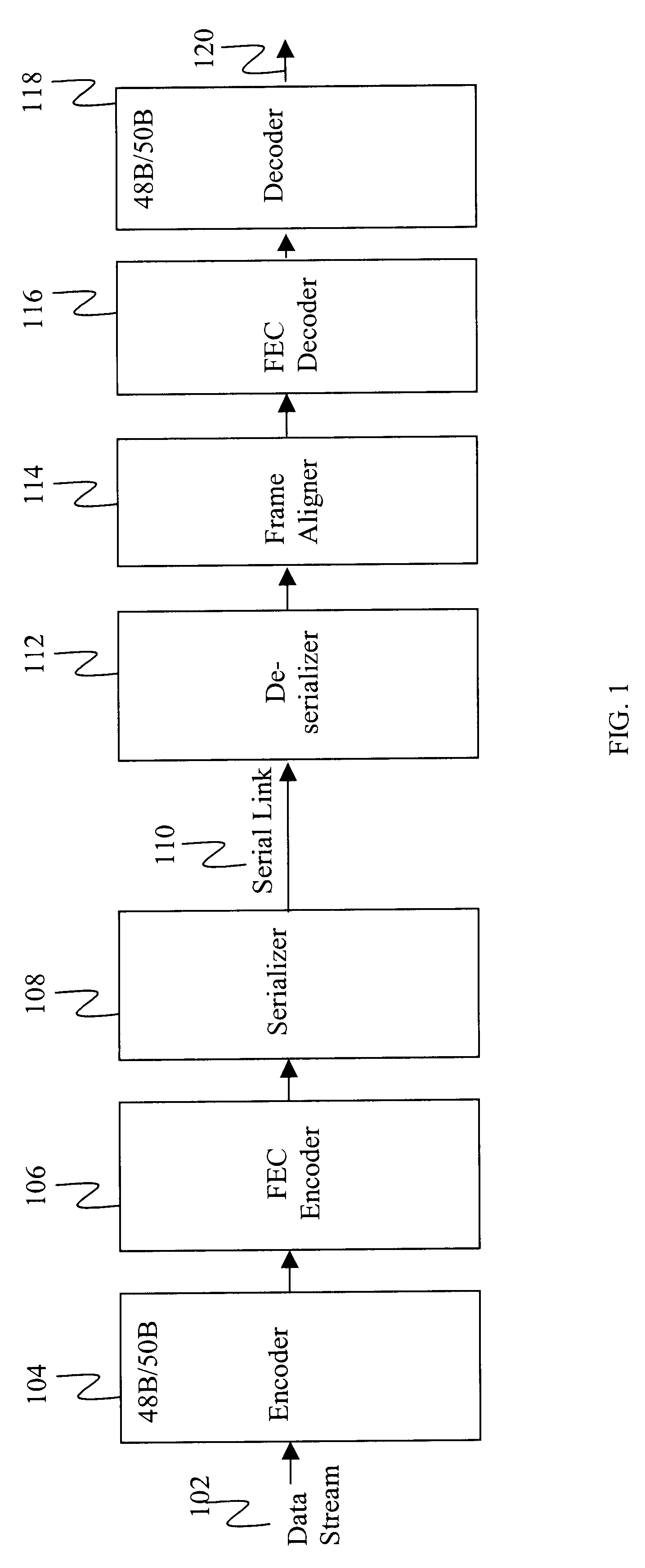
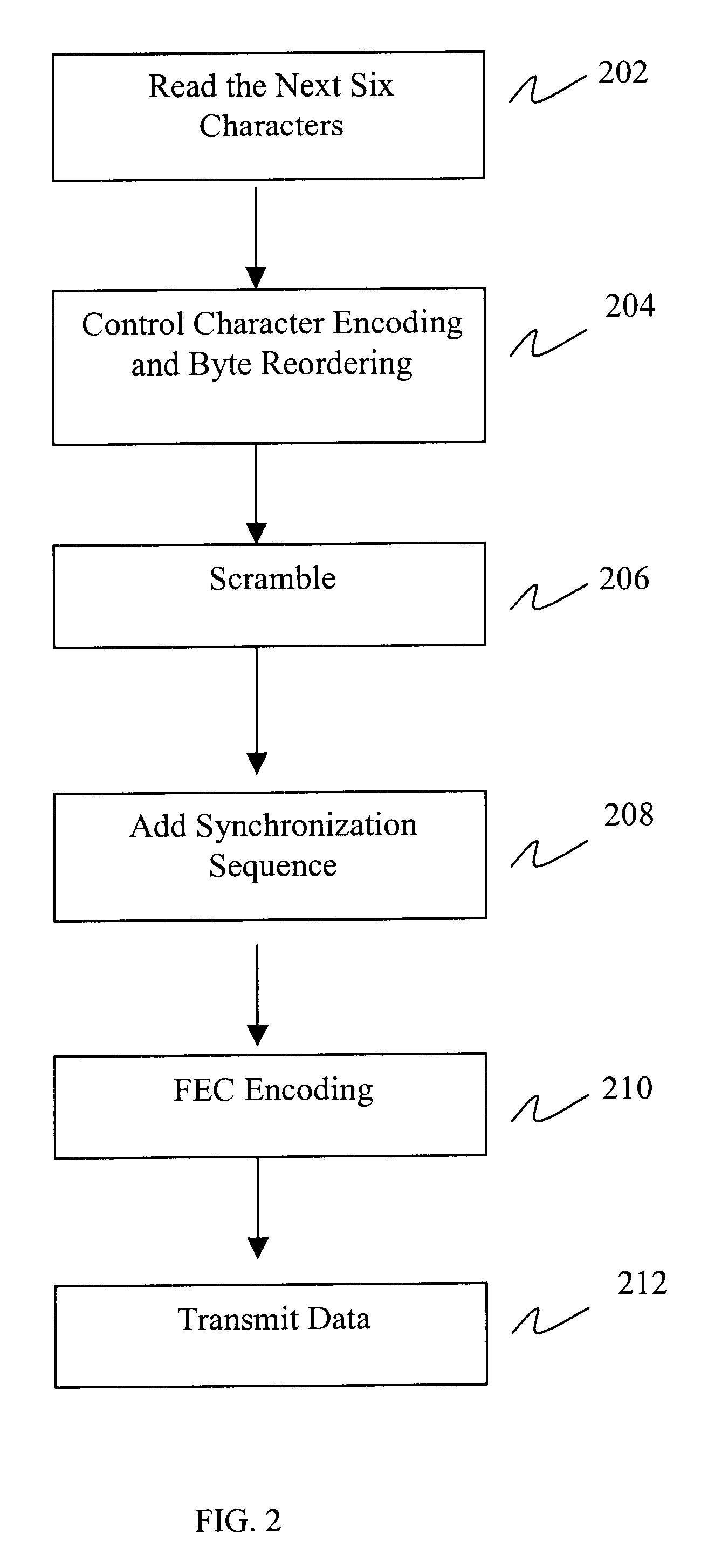
Method and system for encoding data for transmission over a serial link
An exemplary embodiment of the invention is a method for encoding data into a 48B / 50B format for transmission over a serial link. A data stream that includes characters is received and segmented into a six-character block. The block of six characters is translated into a 50-bit byte frame in 48B / 50B format. A 48-bit word is created from the block of six characters by encoding the characters contained in the block. The 48-bit word is scrambled and a 2-bit synchronization sequence is appended to the scrambled 48-bit word. The result is the 50-bit byte frame in 48B / 50B format. An alternate embodiment of the present invention includes a method for decoding data from the 48B / 50B format.
Owner:CIENA
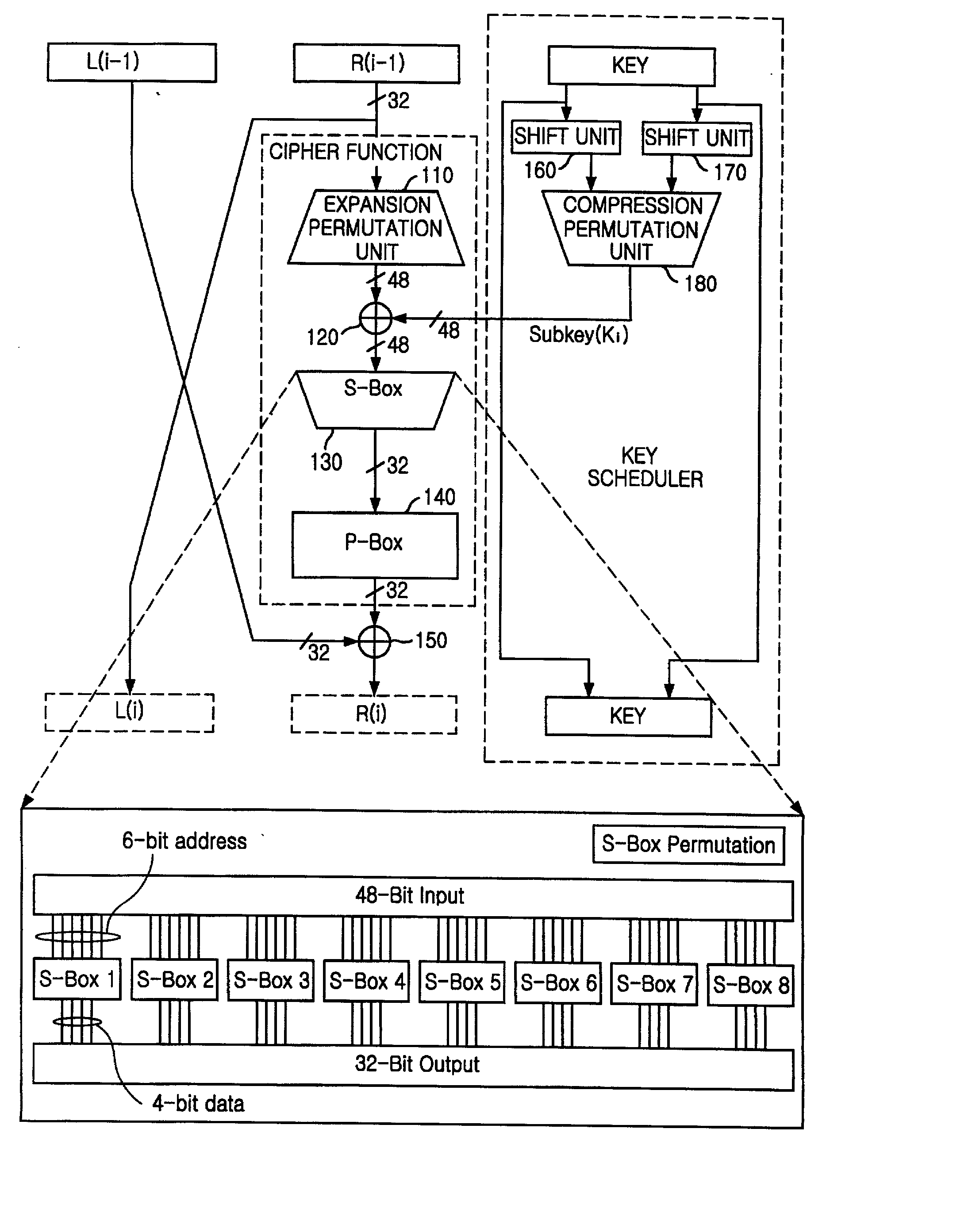
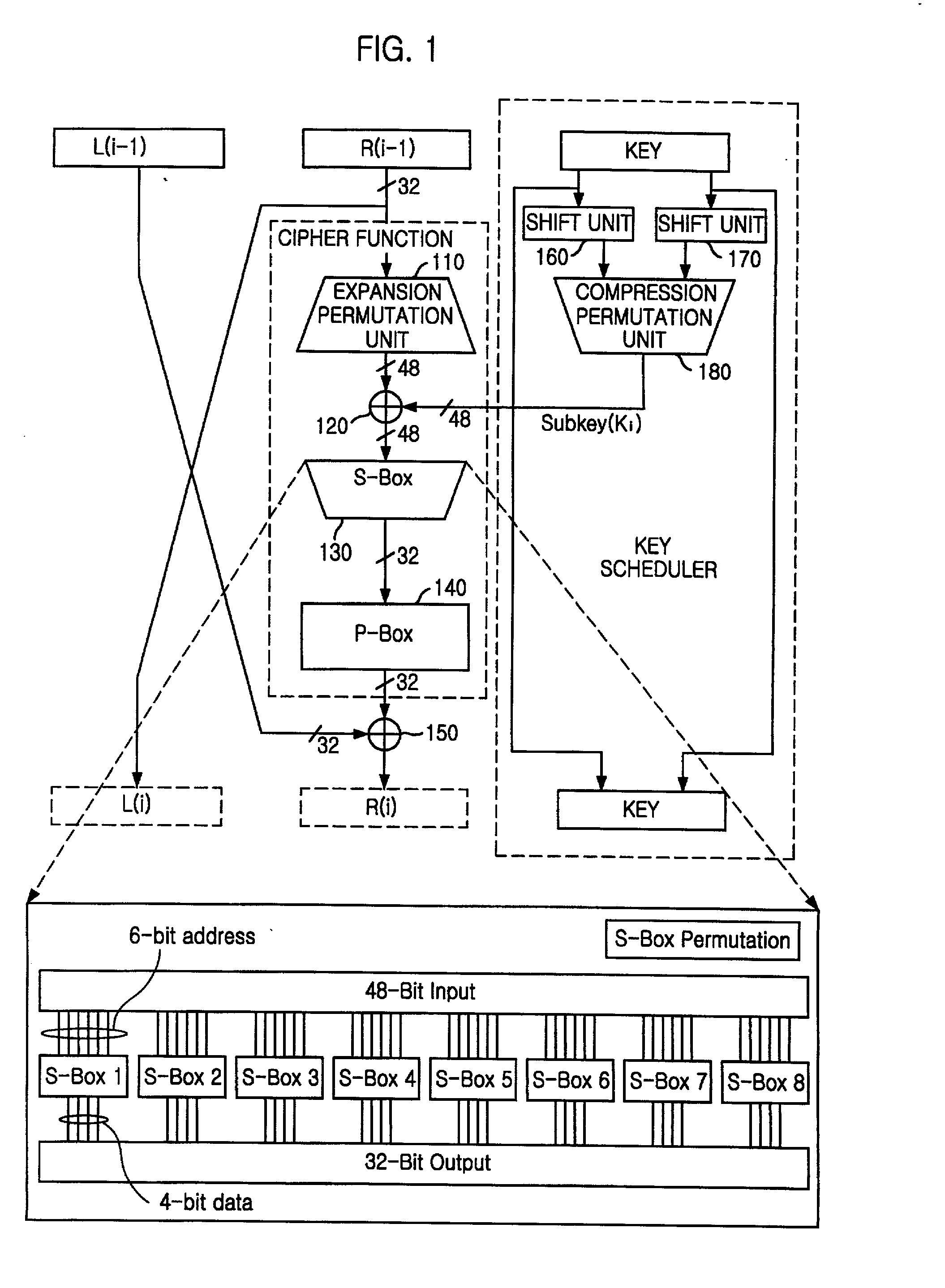
Encryption apparatus using data encryption standard algorithm
InactiveUS20020003876A1Improve process capabilityEncryption apparatus with shift registers/memoriesSecret communicationS-boxMultiplexer
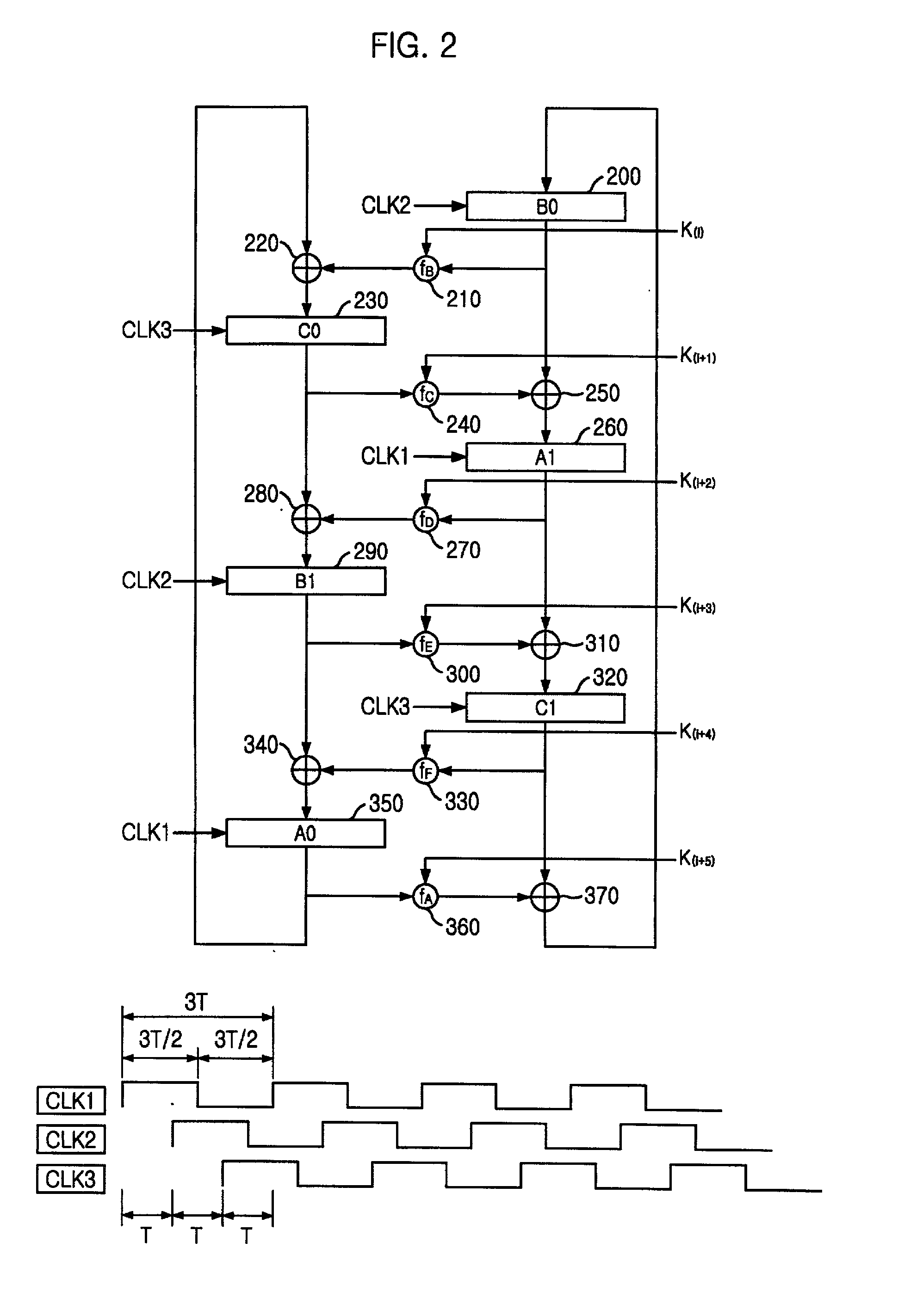
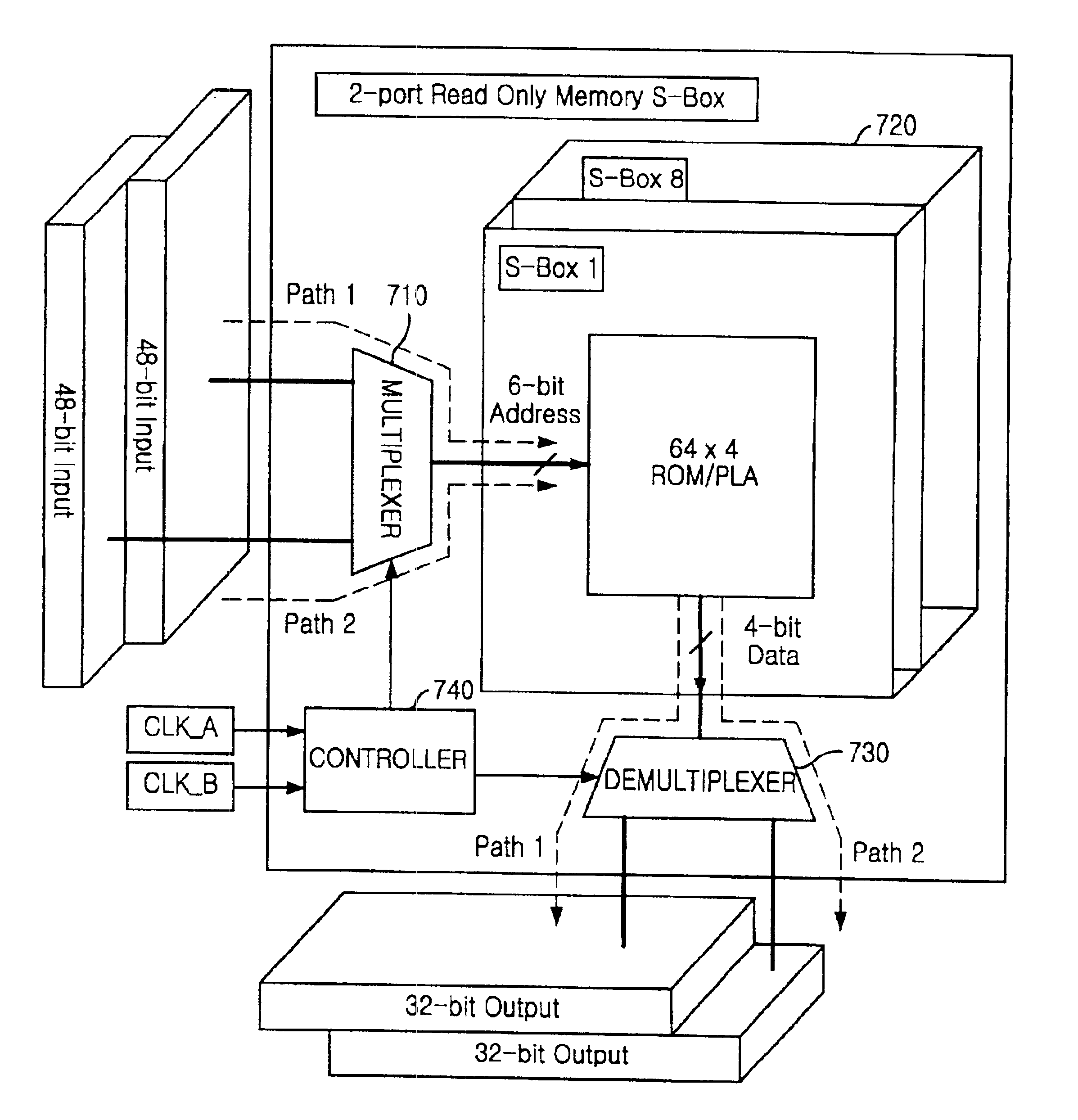
An encryption device eliminates data contention and minimizes area by accessing twice data for a given time by using a memory device of two times faster access time. The encryption device for performing encryption of plain text blocks using data encryption standard algorithm, wherein the encryption device includes an initial permutation unit, a data encryption unit having n-stage (n is an even number) pipeline structure using a first clock, a second clock and a third clock, and an inverse initial permutation unit, the encryption device includes: a multiplexer for selecting one of n / 3 48-bit inputs; 8 S-Boxes, each for receiving 6-bit address among the selected 48-bit and outputting 4-bit data; a demultiplexer for distributing 32-bit data from the S-Boxes to n / 3 outputs; and a controller for control the multiplexer and the demultiplexer with a fourth clock and a fifth clock, wherein the fourth and the fifth clock are faster than the first, the second and the third clocks by n / 3 times.
Owner:ABOV SEMICON
Digital image encrypting and decrypting method
InactiveCN102609893AMaintain styleAchieving mean invarianceImage data processing detailsCiphertext48-bit
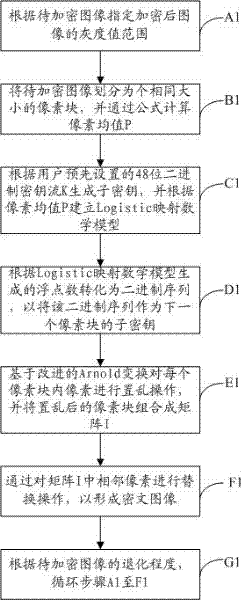
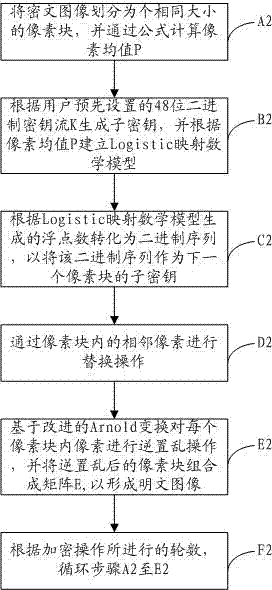
The invention discloses a digital image encrypting and decrypting method comprising the following steps of: appointing the gray value range of an encrypted image according to an image to be encrypted; dividing the image to be encrypted into pixel blocks with the same size, and computing a pixel mean value by virtue of a formula; generating a sub-secret key according a 48-bit binary system key stream preset by a user, and building Logistic mapping according to the pixel mean value; converting into a binary sequence according to the number of floating points generated by the Logistic mapping, and taking the binary sequence as the sub-secret key of the next pixel block; scrambling the pixel in each pixel block based on the improved Arnold conversion, and combining the scrambled pixel blocks into a matrix; and replacing the adjoining pixels in the matrix, so that a ciphertext image can be formed. According to the requirement of a user, the image can be encrypted by means of different numbers of sheaves, various filtering attacks can be resisted, and the invariability of the pixel mean value of the image can be realized, so that the whole style and feature of the original image can be maintained.
Owner:AEROSPACE SCI & IND SHENZHEN GROUP
Lift trackless hoist capable of receiving absorption and hanging in wireless manner
The invention relates to a lift trackless hoist capable of receiving absorption and hanging in a wireless manner. A traveling vehicle with a lift and hoist frame is used to complete the functions of storing and withdrawing goods and cars which respectively has at least two rows, 2-7 layers and more than 48 bits, and a lift movement operates without a track, a control wire and an insulated control roller. In the front of the hoist, an upper switch and a lower switch are bi-injected by infrared ray to search a target, high-low points at each row and each layer are controlled by a spiral encoder, each jointed action is completed by a wireless signal transmitter and a receiver, and actuation transport is finished by power supply of a dry battery after a magnetic field is generated by a magnet. As for the product in the invention, the manufacture cost can be lowered over 1 / 3 compared with the that of other similar products, and the car or goods storage amount can be improved by over 13 times (including the channel area) in the same area. The hoist can be used for parking, storing goods, jointed manufacture and common use; and the stall platens and containers can be increased or reduced according to the requirements of cars and goods quantity, and also can be used independently. By using the hoist, land resource and human source can be saved greatly. The storing and withdrawing of the cars and goods automatically operate by a specially-assigned person via magnetic cards, passwords or fingerprints.
Owner:傅黎明
Performing extended lookups on MAC-based tables including level 3 multicast group destination addresses
ActiveUS7586895B2Easy to adaptSpecial service provision for substationTime-division multiplexIp addressMulti protocol
A method, system, and computer program product are presented to optimize OSI Level 2 switch forwarding of frames comprising IP addresses, 802.1 QinQ VLAN identifiers, multi-protocol label switching labels, and any other usable information meaningful to derive an L2 forwarding result on frames. In one embodiment, a 16-bit key is included as a prefix to a 48-bit OSI Level 2 address entry, thereby allowing the inclusion of a 32-bit OSI Level 3 address in the lookup table (e.g., a complete IP version 4 address). Implementations of such a solution are presented to resolve address aliasing issues experienced with multicast group destination addresses, including single source multicast. Solutions to optimizing forwarding of frames in an IEEE 802.1 QinQ environment are also presented. A result of these implementations can be reduction of the amount of unnecessary network traffic generated by a network switch incorporating such an OSI Level 2 address lookup table.
Owner:CISCO TECH INC
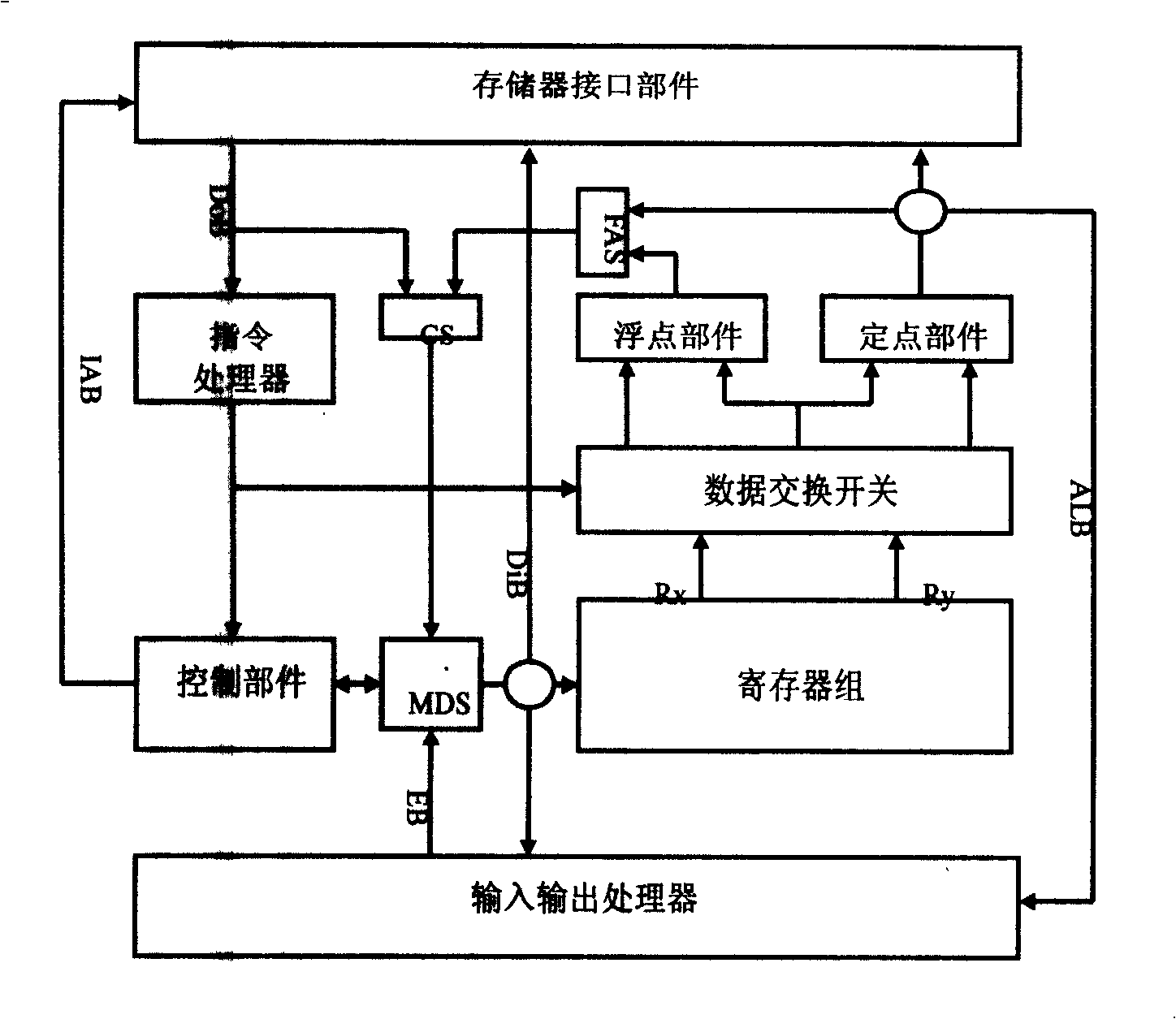
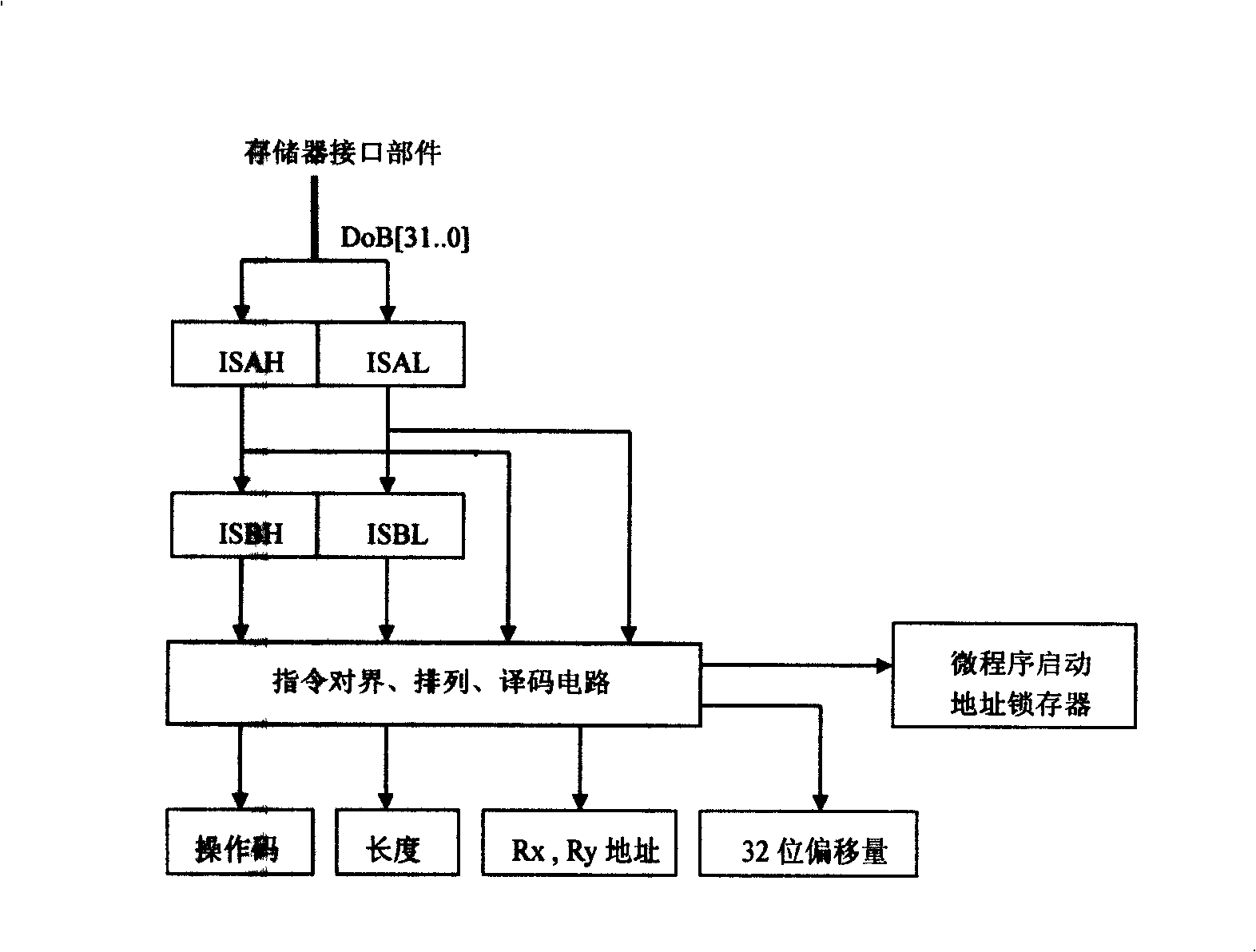
32 bits micro-processor
InactiveCN101256546AConcurrent instruction executionArchitecture with single central processing unitMemory interfaceInstruction cycle
The invention relates to a 32 bits microprocessor and its instruction set. The microprocessor system comprises an instruction processor, a control component, a fixing point operation a floating-point operation, a register group, a storage interface component and an I / O processor. The entire instruction cycle adapts two state pipelining and is simple in structure. The system is provided with 16 32 bits general registers which hold 4GB storage address space and input output address space. The storage, the I / O processor and the central processor are connected with 64 bits data path. The speed of the processor can be up to 32 bits instruction flow and 32 bits data flow in each clock cycle. The microprocessor system supports 16 bits, 32 bits and 48 bits three instruction formats which are nine kinds and 50 instructions, wherein, the floating-point add, subtract, multiply and divide, fixing-point divide, fixing-point modulus, the conversion between floating-point and fixing-point are all realized by instructions. The instruction is simplified in number but is strong in function, and also has advantages of RISC and CISC.
Owner:黄新亚 +1
Methods and devices for generating and forwarding translated MAC addresses
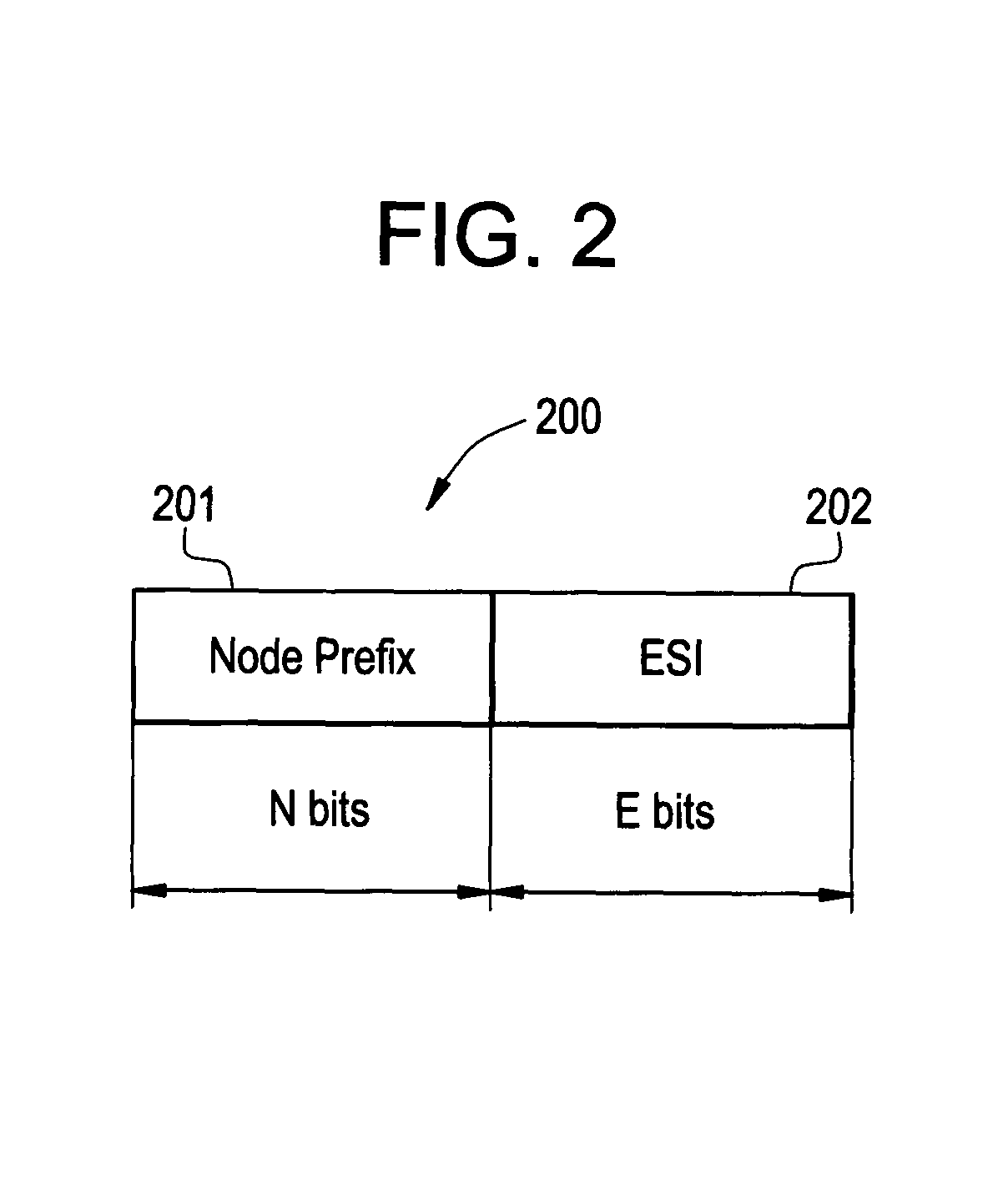
ActiveUS20080205425A1Increase the number ofLow costStore-and-forward switching systemsNetwork packet48-bit
The number of MAC addresses and corresponding tables that need to be stored to forward messages in a network is substantially reduced. Conventional MAC addresses are converted to translated (sometimes called “virtual”) MAC addresses using a new hierarchical format which redefines the conventional 48-bit, MAC label. Though the MAC label is redefined the packet size remains the same. For example, the number of MAC address tables stored by a HUB node may be reduced from 60,000 to 8 while the number stored at a POP node may be reduced from 120,000 to 8 in a “flat” Ethernet design.
Owner:RPX CORP +1
Special-purpose double production line RISC instruction system and its operation method
The invention discloses a special double-pipeline RISC instruction system. The system is provided with two pipelines which are parallel mutually, and sequentially includes an instruction fetching unit, an instruction decoding unit, an instruction execution unit, a memory accessing unit and a data writing back unit. The system uses a double pipeline RISC instruction which comprises two incorporate single pipeline instructions. The invention further provides an operation method of the special double-pipeline RISC instruction system. The method includes the following steps: two parallel pipelines are arranged, namely, the instruction fetching unit, the instruction decoding unit, the instruction execution unit, the memory accessing unit and the data writing back unit are sequentially arranged; the double pipeline RISC instruction provided with two incorporate single pipeline instructions is arranged. Using the invention, the resource waste is avoided, wherein the resource waste is caused because a plurality of resources are not used during implementing algorithms when using a general digital signal processor. In addition, the invention has the advantages that the calculation more than 24 bits (48 bits inside) is realized, at the same time, the cost is low, and the power consumption is low.
Owner:SHANGHAI BEILING
Floating-point multiplicator and method of compatible double-prepcision and double-single precision computing
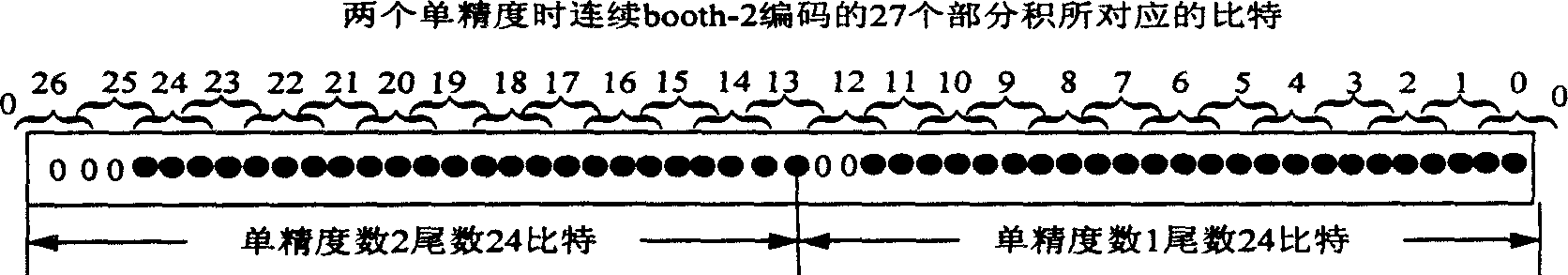
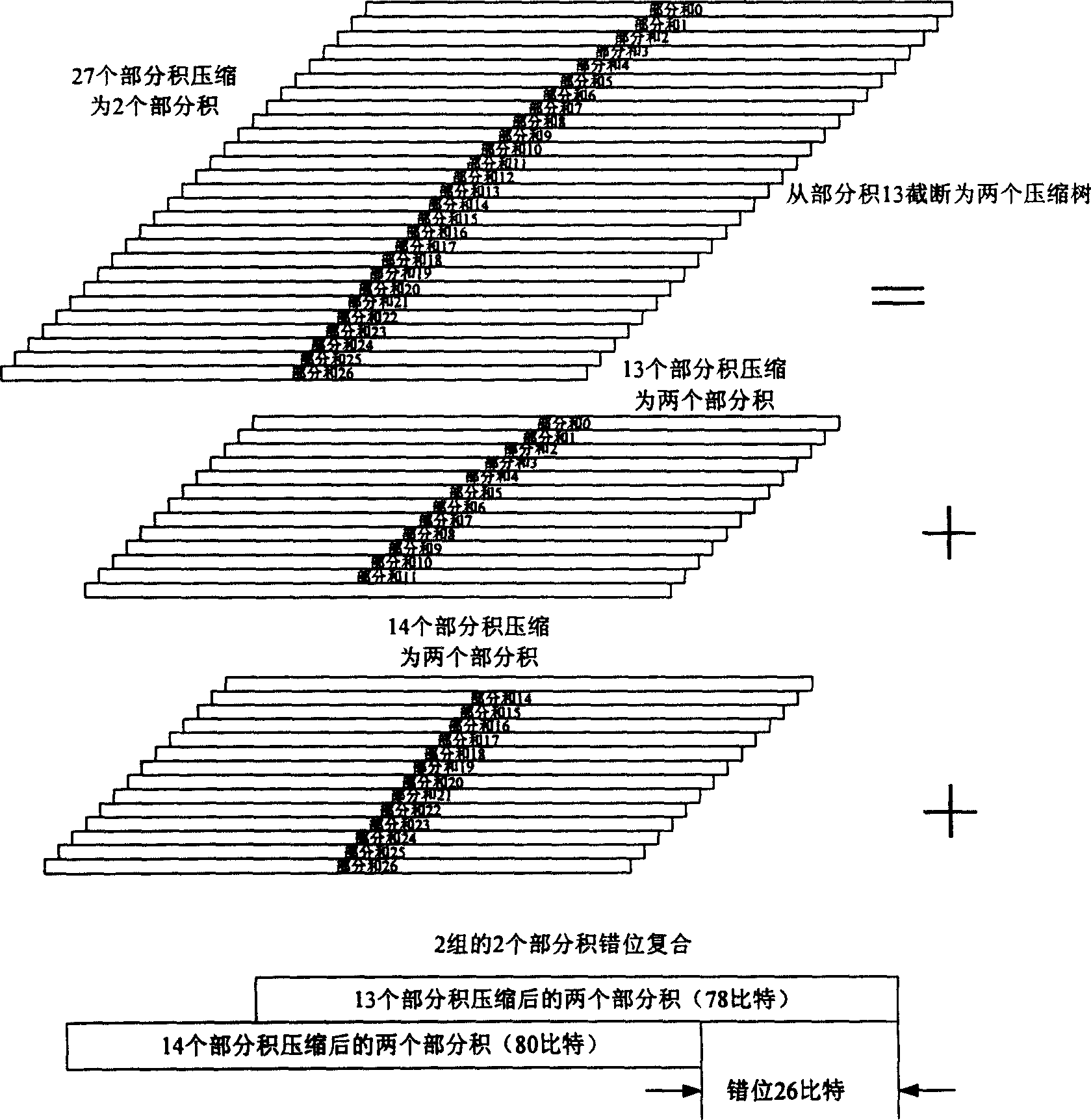
ActiveCN1831753ATake advantage ofNo wasteComputation using non-contact making devices48-bitFloating point multiplier
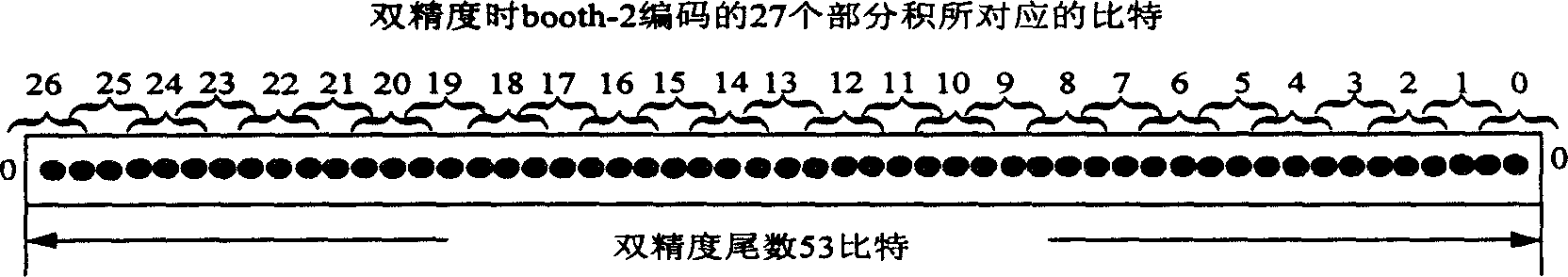
A floating-point multiplier consists of single accuracy continuous coding - packing unit, the first selector, base 2 Pots coder, 13 : 2 compression tree, 14 : 2 compression tree, 48 bit adder, 4 : 2 compression composite tree, the second selector, 106 bit adder, 48 bit single accuracy round - off and normalization unit, 106 bit double accuracy round - off and normalization unit, double accuracy and double accuracy index processing unit . The said floating-point multiplier can multiplex double accuracy data channel for carrying out calculation to obtain two single accuracy multiplication results of floating-point at each beat.
Owner:LOONGSON TECH CORP
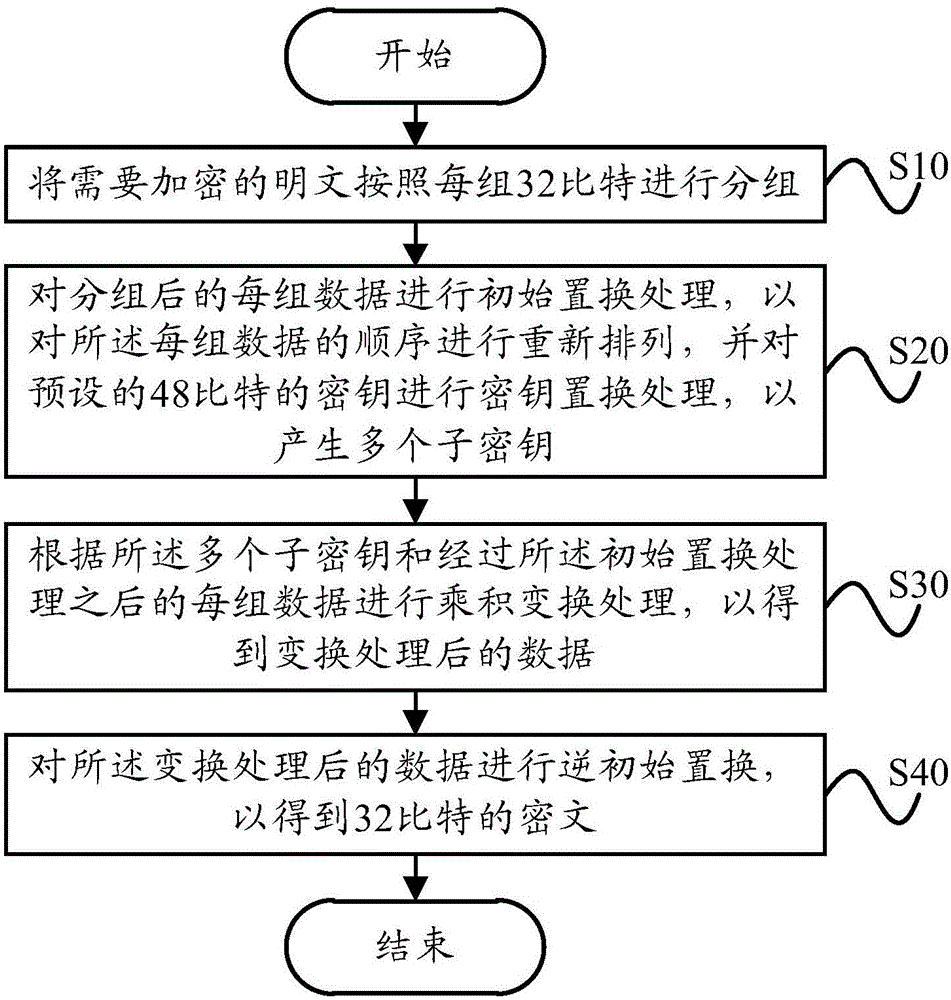
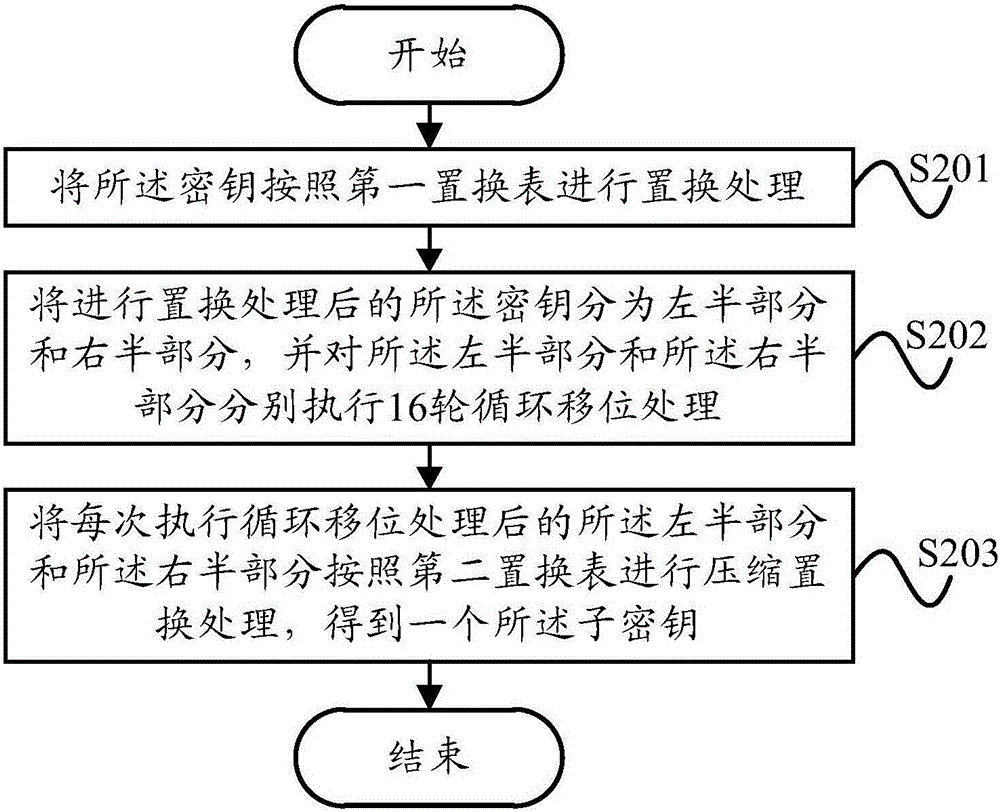
Information encryption method and information encryption device used for mobile terminal and mobile terminal
InactiveCN105790930AGuaranteed encryption securitySmall amount of calculationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextCiphertext
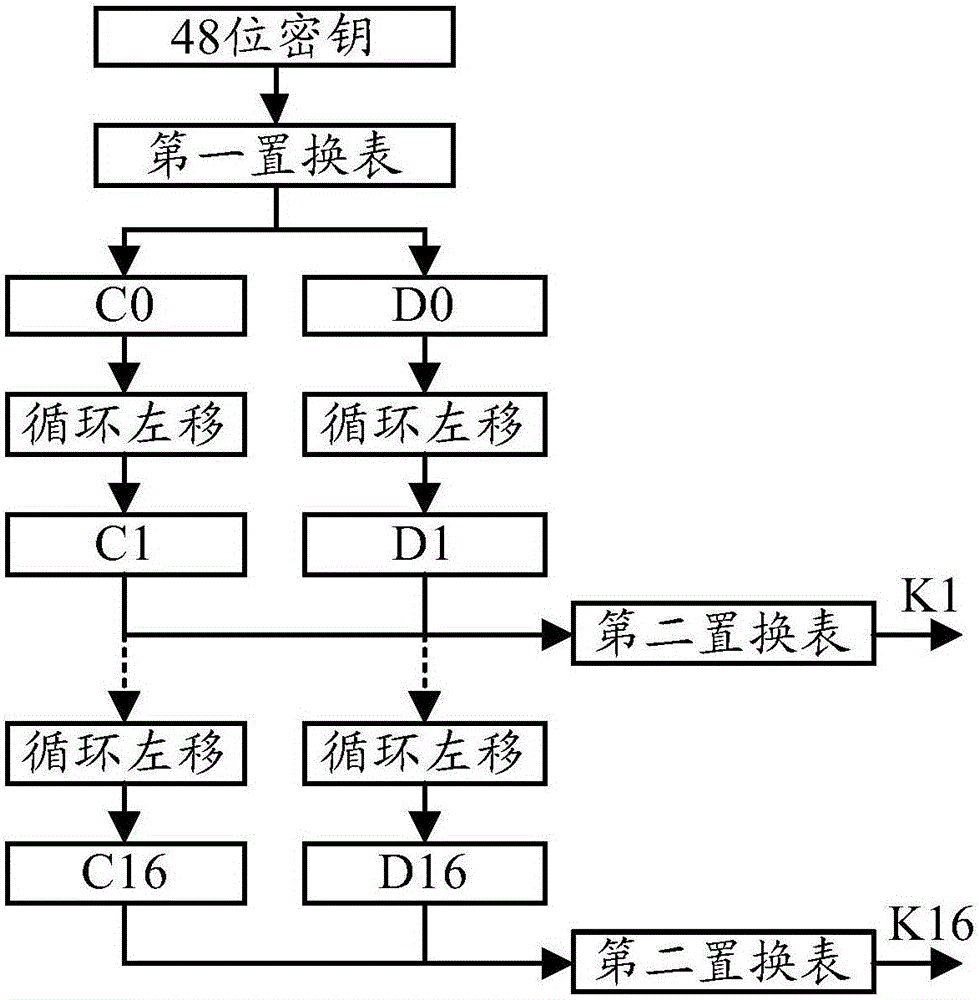
The invention provides an information encryption method and an information encryption device used for a mobile terminal and the mobile terminal. The information encryption method comprises the steps that plaintexts requiring encryption are grouped in a way that each group includes 32 bits of plaintexts; initial permutation processing is performed on each group of data after grouping so that the order of all groups of data is arranged again, and secret key permutation processing is performed on preset 48 bits of secret keys so that multiple sub-keys are generated; product transformation processing is performed according to the multiple sub-keys and each group of data after initial permutation processing so that the data after transformation processing are obtained; and inverse initial permutation is performed on the data after transformation processing so that a ciphertext of 32 bits is obtained. According to the technical scheme, the burden of computation of data encryption can be obviously reduced under the premise of guaranteeing security of data encryption so that efficiency of data encryption can be enhanced, and power consumption of the mobile terminal in data encryption can be reduced.
Owner:NANJING COOLPAD SOFTWARE TECH
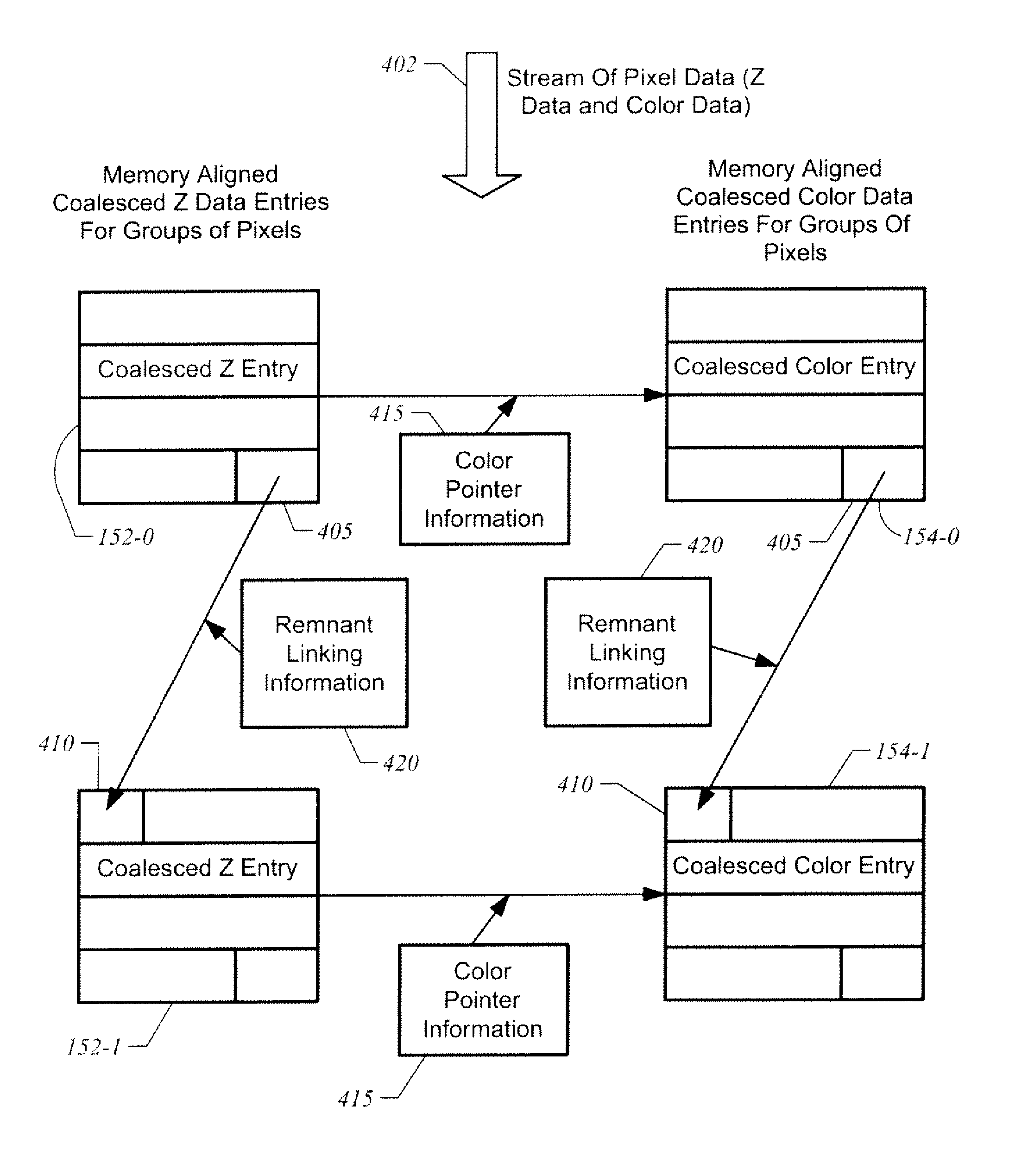
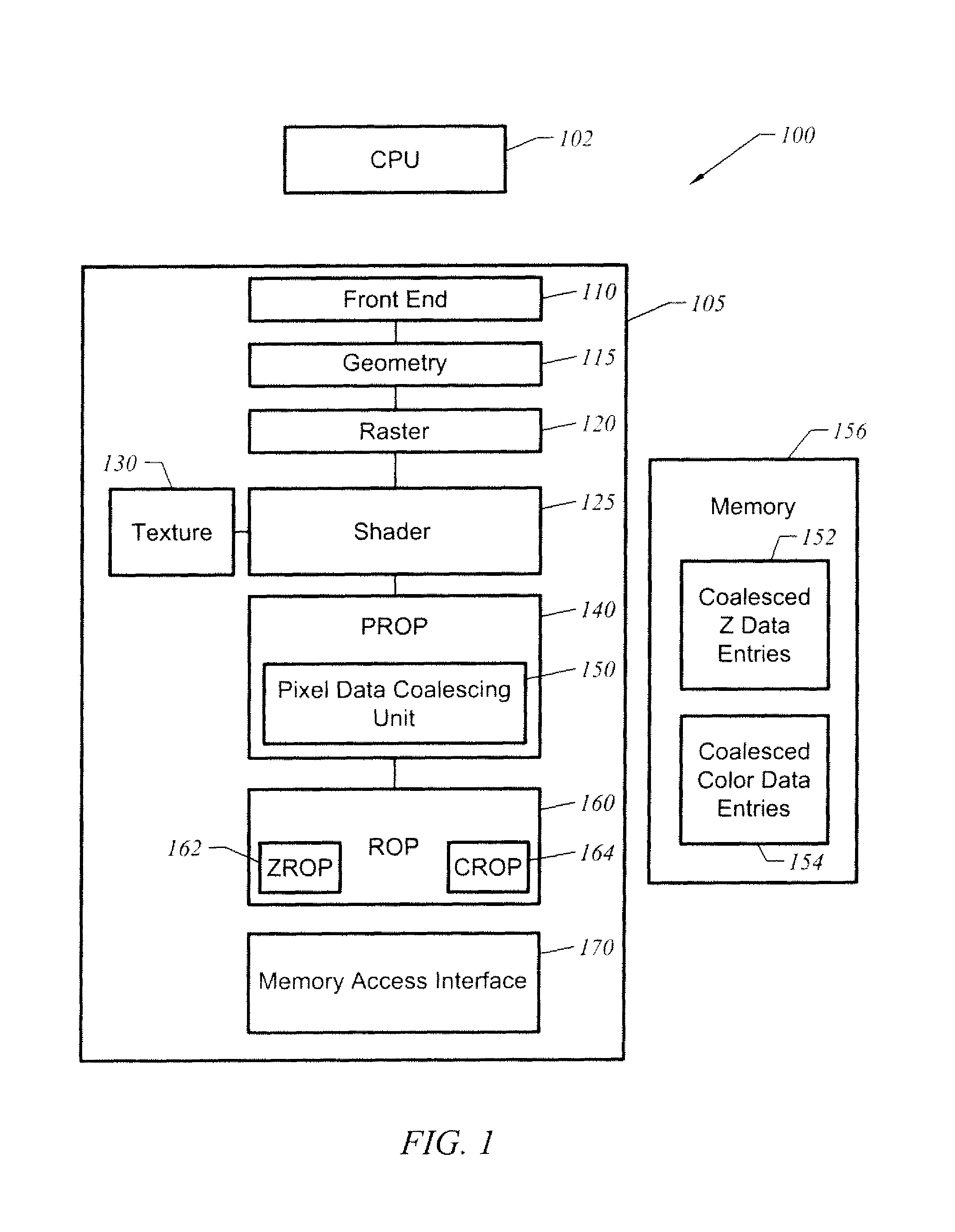
Apparatus, method, and system for coalesced Z data and color data for raster operations
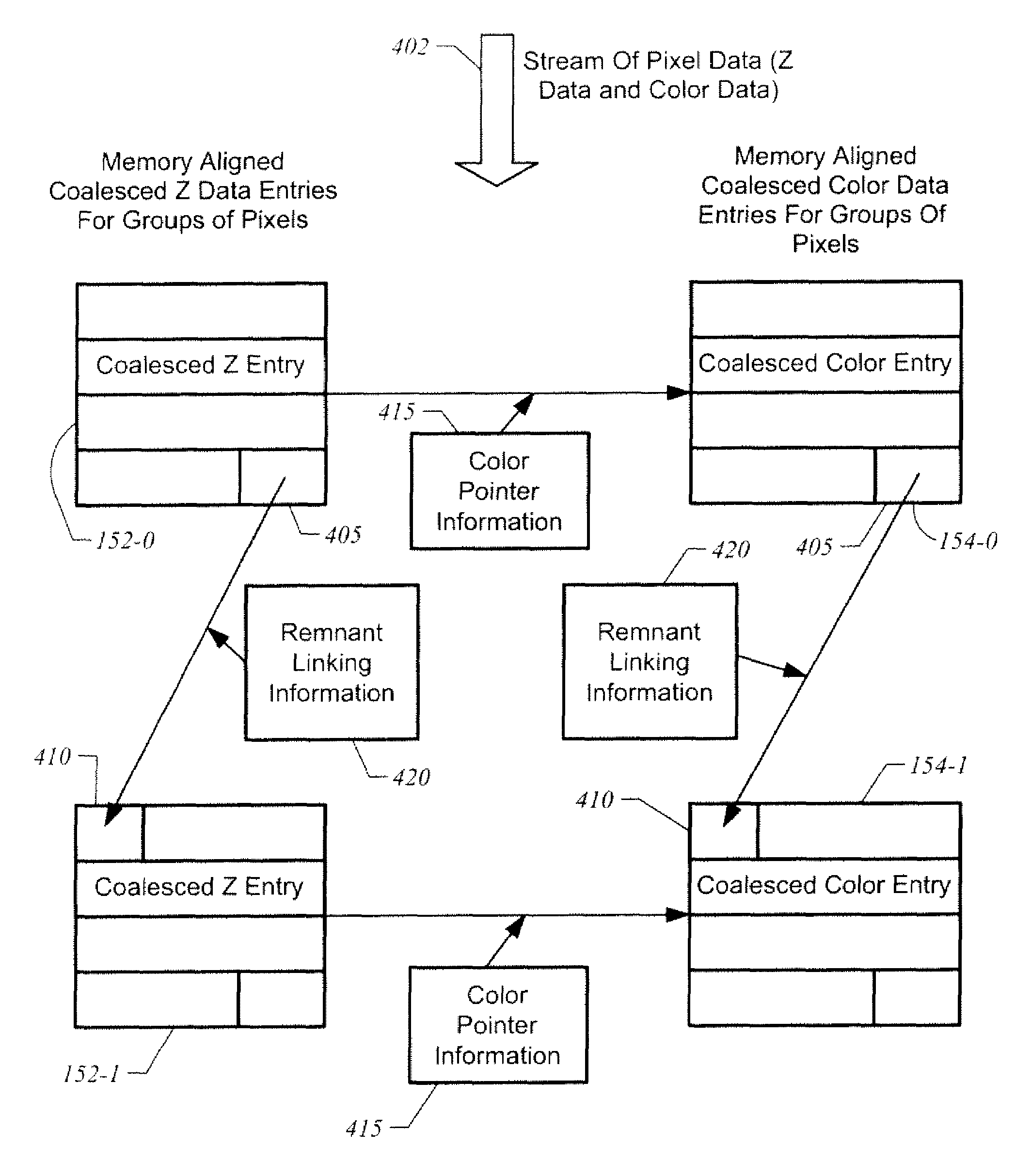
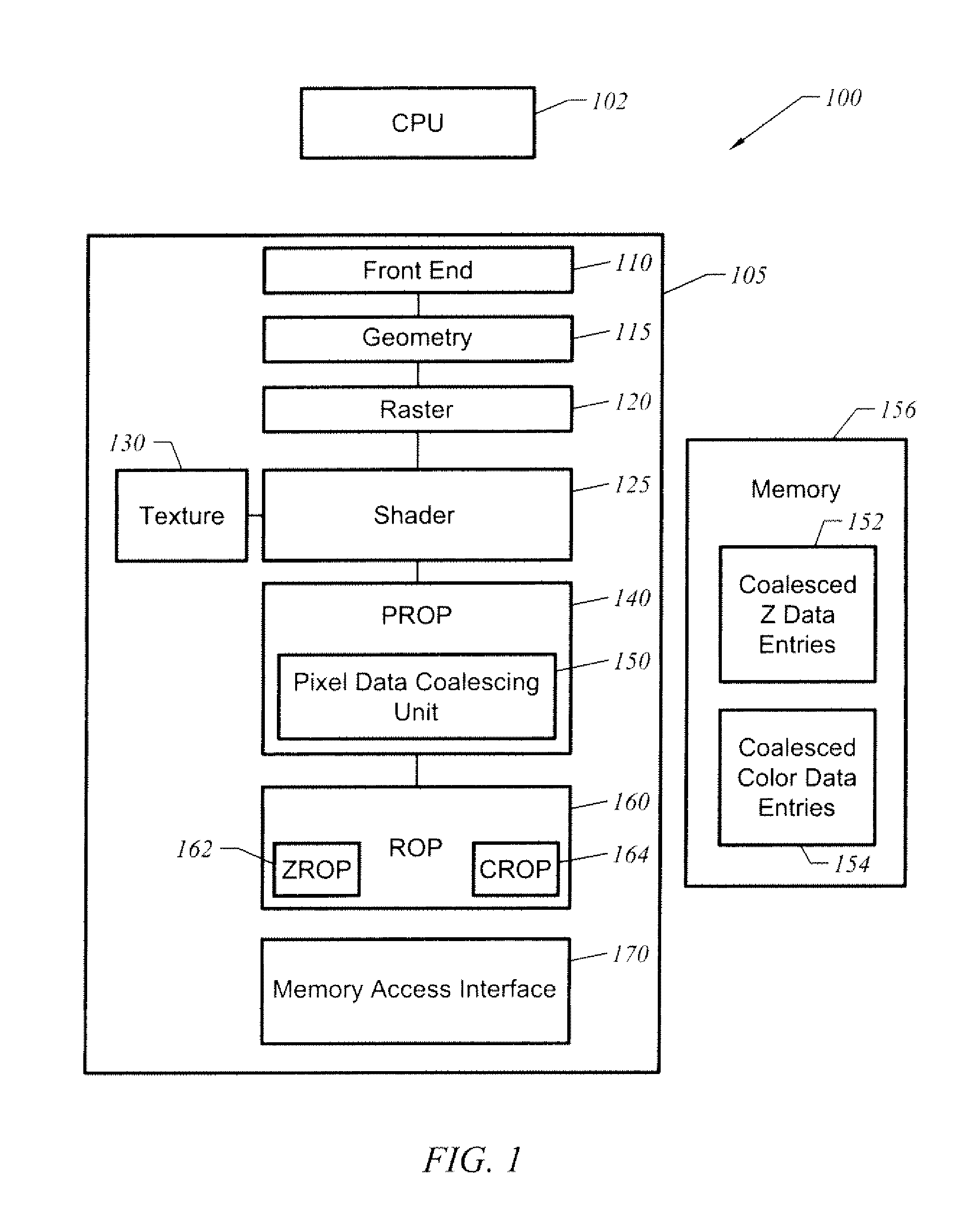
ActiveUS7474313B1Improve transfer access efficiencyImprove packaging efficiencyMemory adressing/allocation/relocationCathode-ray tube indicatorsData capacityGraphics
A graphics system coalesces Z data and color data for a raster operations stage. The Z data and color data are stored in a memory aligned tile format. In one embodiment, rendering modes in which the tile does not have a data capacity corresponding to Z data or color data for a whole number of pixels have data for at least one pixel split across entries to improve packing efficiency. Rendering modes having a number of bits for Z data or color data that does not equal a power of two such as 24 bits, 48 bits, and 96 bits, may be implemented with a high packing efficiency in tile formats having a data capacity corresponding to a power of 2 bits.
Owner:NVIDIA CORP
Reconfigurable fixed/floating point general adder
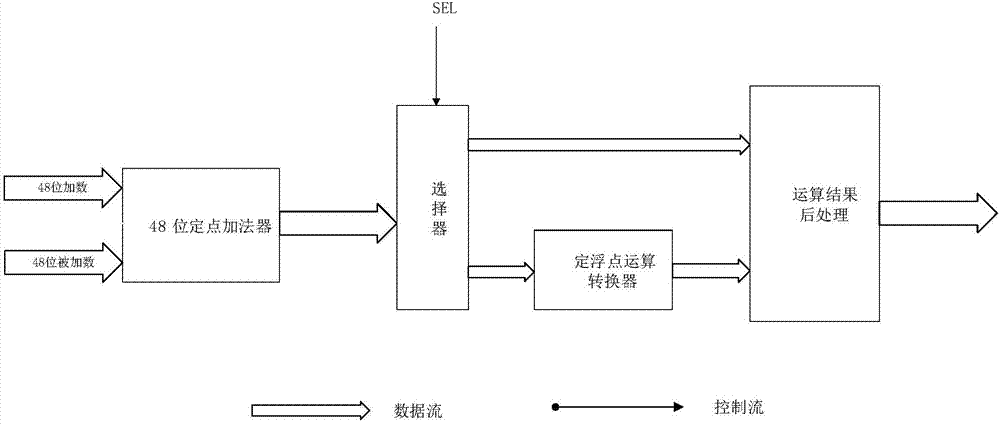
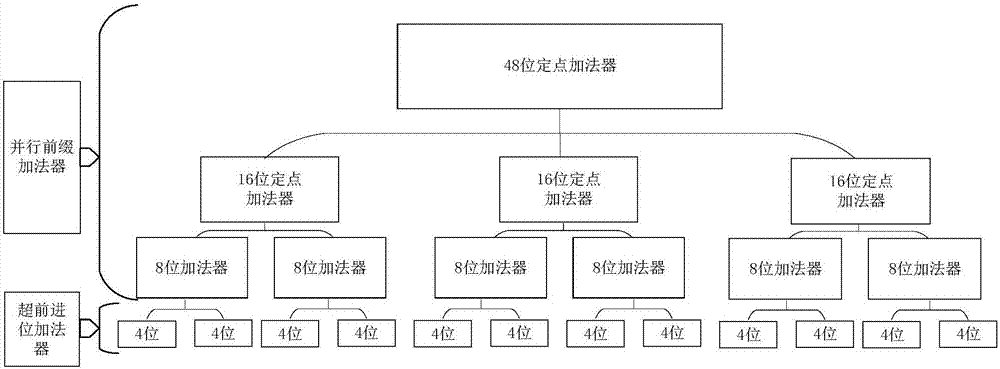
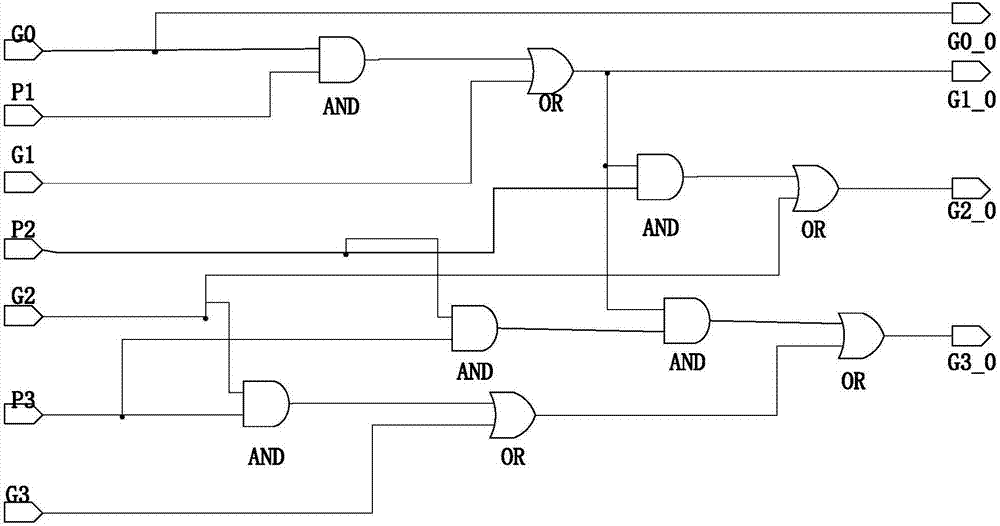
InactiveCN106970775AImprove versatilityImprove data throughputDigital data processing details48-bitFloating point
The invention provides a reconfigurable fixed / floating point general adder. The general adder comprises a 48-bit fixed point adder, a selector and a fixed / floating point operation converter, wherein the 48-bit fixed point adder performs fixed point additive operation and can be reconfigured into a single-precision floating point adder; the selector selects a corresponding fixed point or floating point additive operation passage according to top configuration information and performs output control; and the fixed / floating point operation converter converts the 48-bit fixed point adder into a 32-bit single-precision floating point adder. The general adder has the advantages that a full running structure is adopted, the fixed point adder is correspondingly optimized based on a parallel prefix adder, and on the basis of guaranteeing the operation performance of the fixed point adder, operation delay of the fixed point adder is shortened, and a gate circuit area is reduced. Through the overall structure of the fixed / floating point general adder, the universality of the adder is effectively improved under the condition that precision and data throughput are guaranteed.
Owner:NANJING UNIV
Customized bluetooth enabled identification device
A customized Bluetooth enabled identification device for Bluetooth based identification, communication and tracking system is described. The device uses a customized Bluetooth hardware as identification of location is done through its 48 bit unique hardware address by providing password based security over identification.
Owner:LAKSHMANAN BALAJI
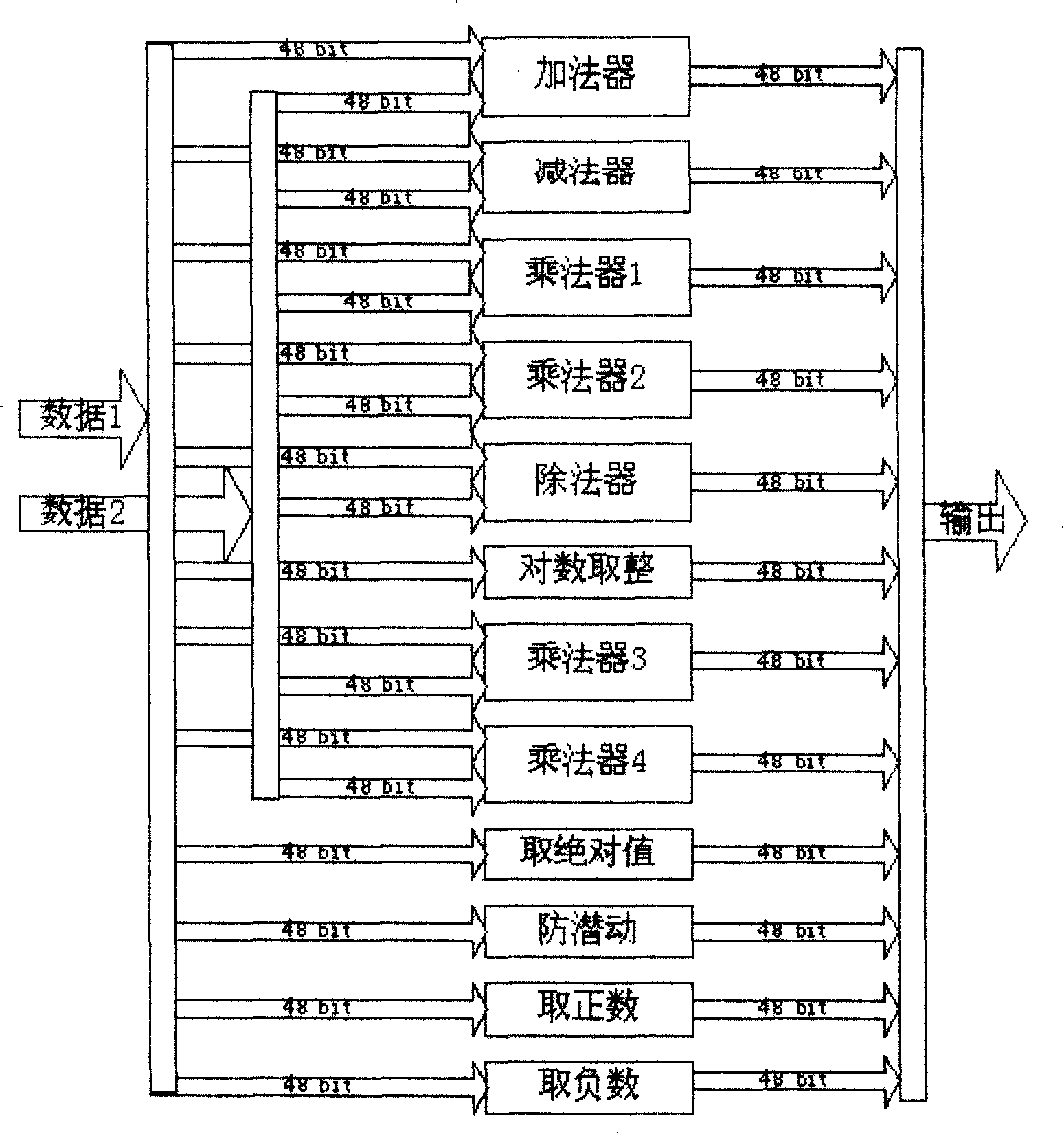
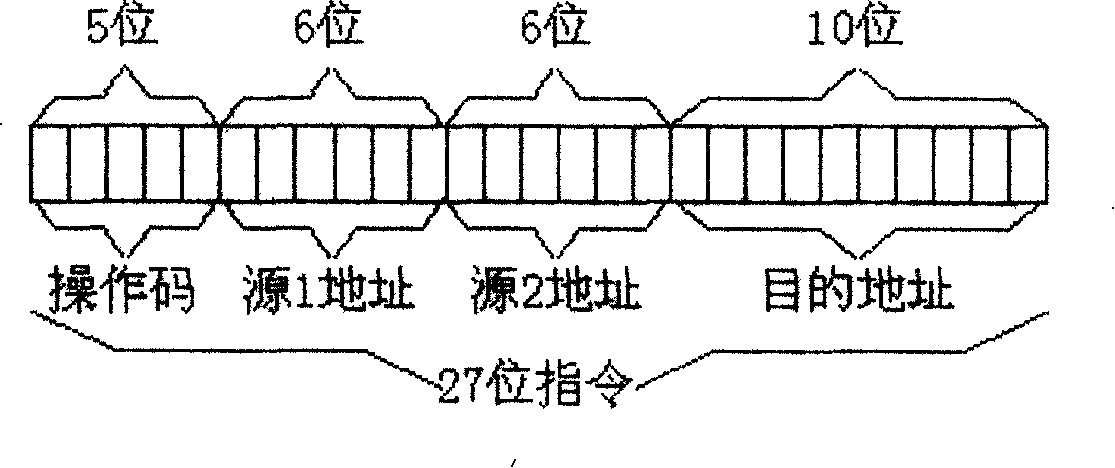
Special arithmetic unit ALU
ActiveCN101206561APerform arithmetic quicklyQuick execution of operabilityDigital data processing detailsElectrical measurementsArithmetic logic unit48-bit
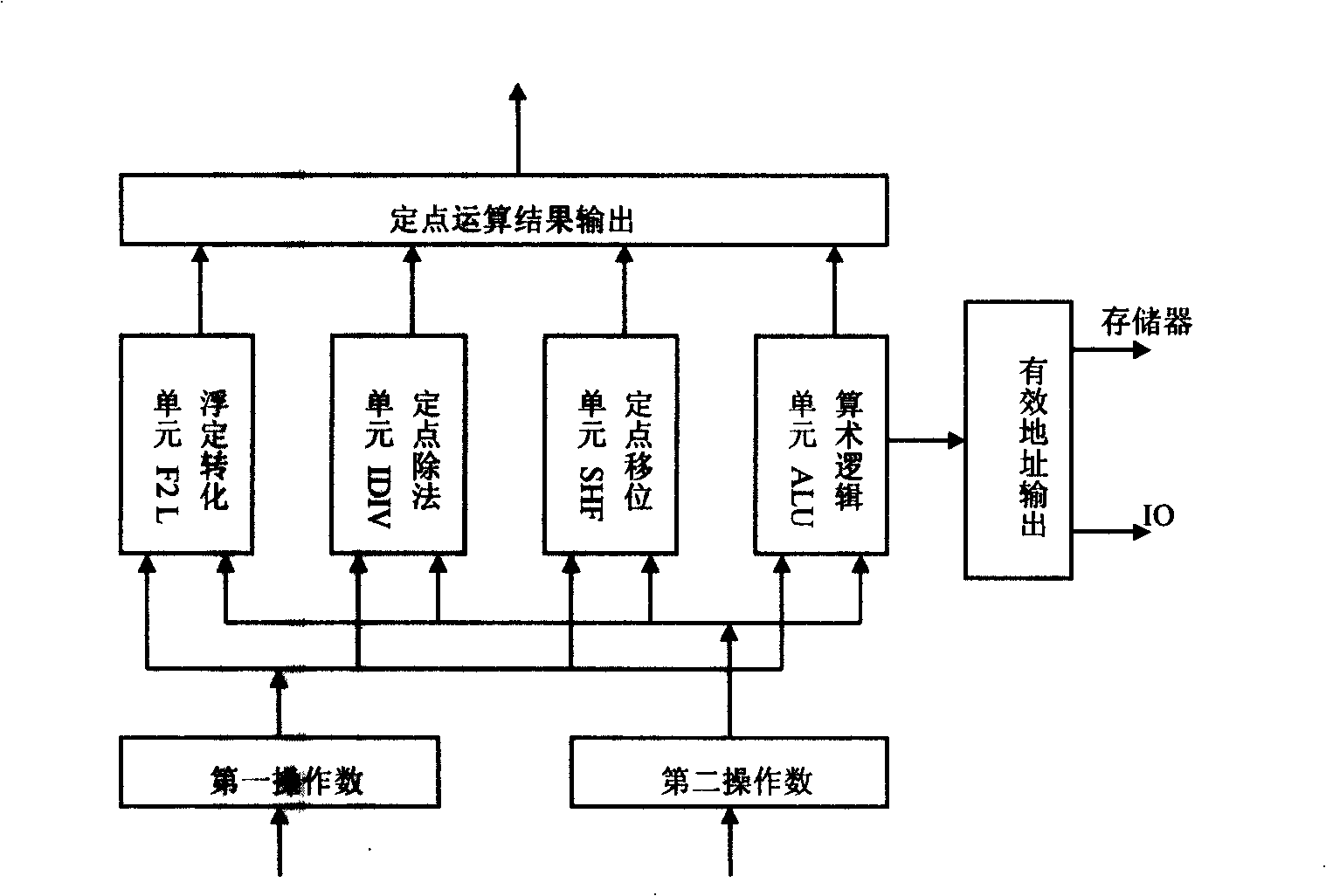
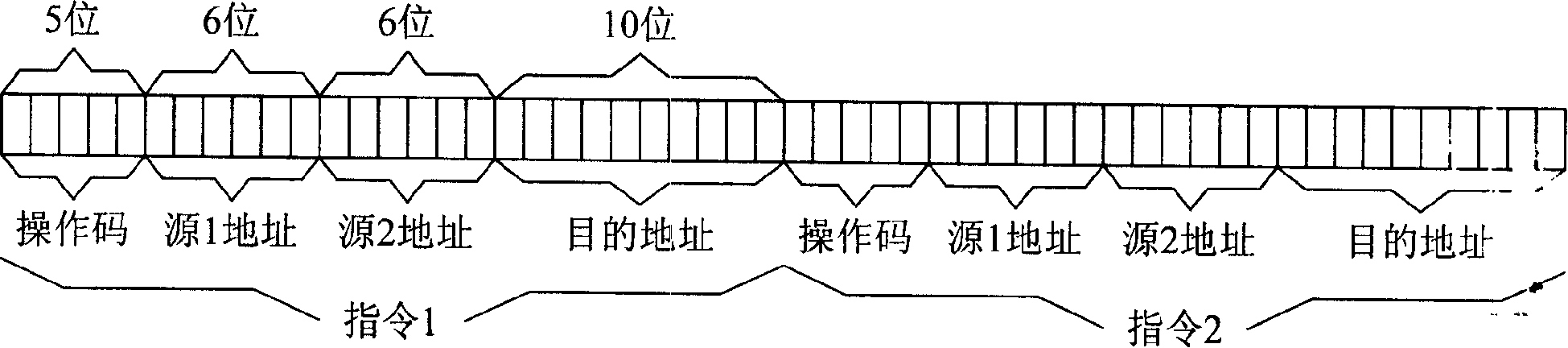
The invention discloses a special arithmetic logic unit (ALU), comprising 12 48-bit arithmetic or logic modules of a summer, a subtracter, a multiplier (1), a multiplier (2), a divider, logarithm int, a multiplier (3), a multiplier (4), using absolute value, an anti-creeper, taking positive number, taking negative number. The special arithmetic logic unit (ALU) is operated by instructions the length of which is 27 bits including 5 bits for opecode, 6 bits for source 1 address, 6 bits for source 2 address and 10 bits for destination address. Each instruction corresponds to an arithmetic or logic operation. ALU can realize the functions required for electric energy meter design by means of external program, particularly for multi-functional high-performance electric energy meter design, with a simple structure and a high speed.
Owner:SHANGHAI BEILING
Encryption apparatus using data encryption standard algorithm
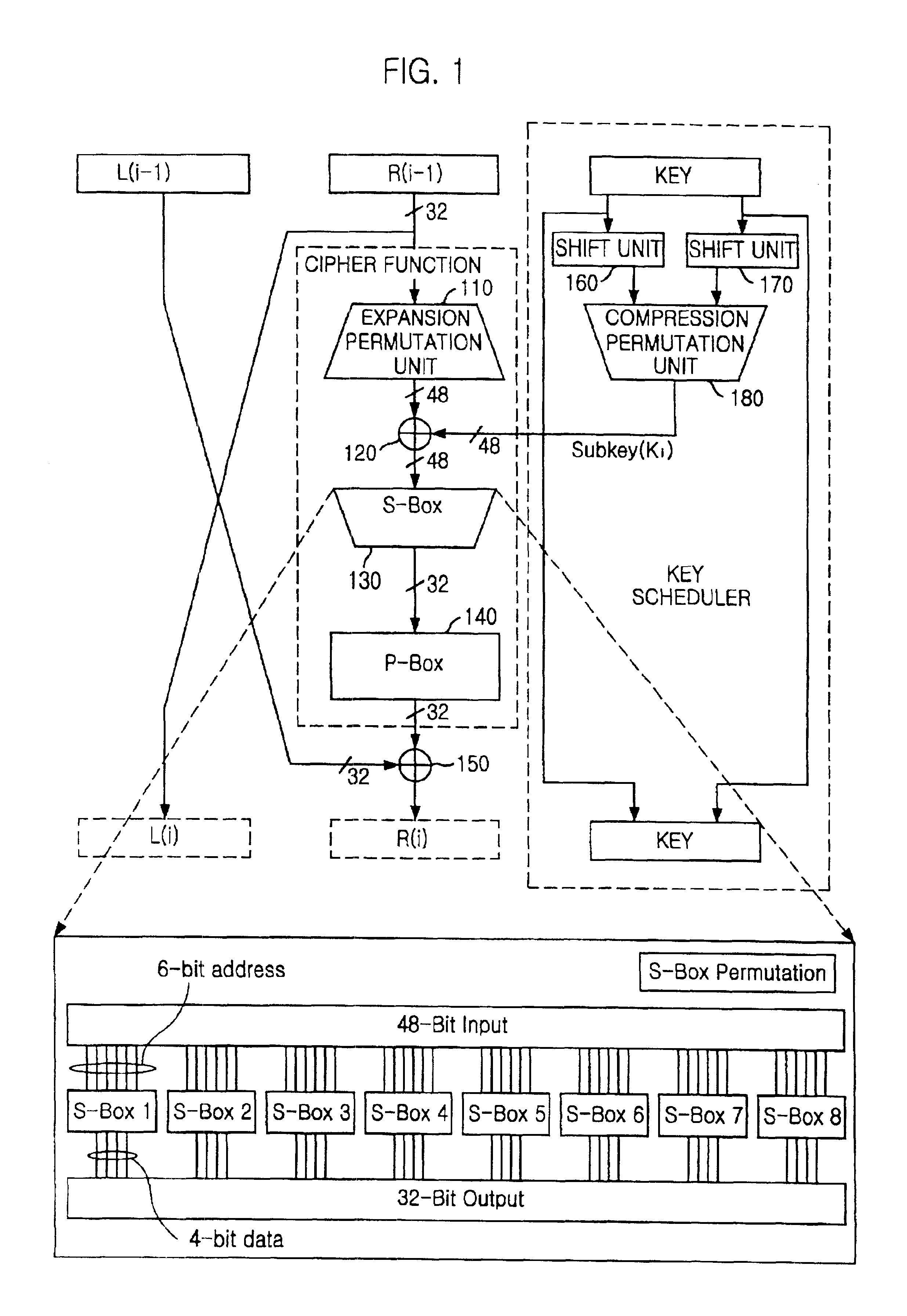
InactiveUS6914984B2Area minimizationEliminating data contentionEncryption apparatus with shift registers/memoriesTelegraphic message interchanged in timeS-boxMultiplexer
Owner:ABOV SEMICON
Method and apparatus for handling data transfers
InactiveUS20050188145A1Input/output to record carriersFilamentary/web record carriers48-bitData transmission
Owner:INTEL CORP
Method for OFDM communication system to transmit and receive frame prefix
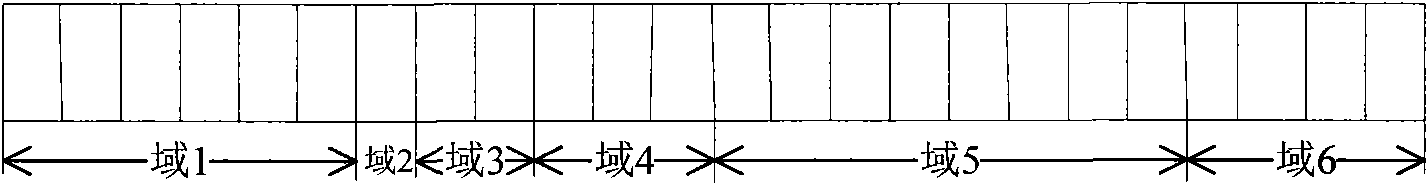
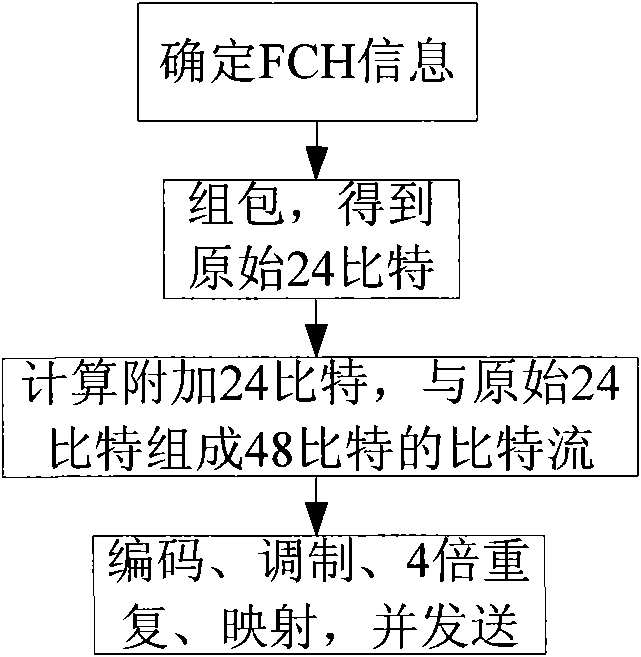
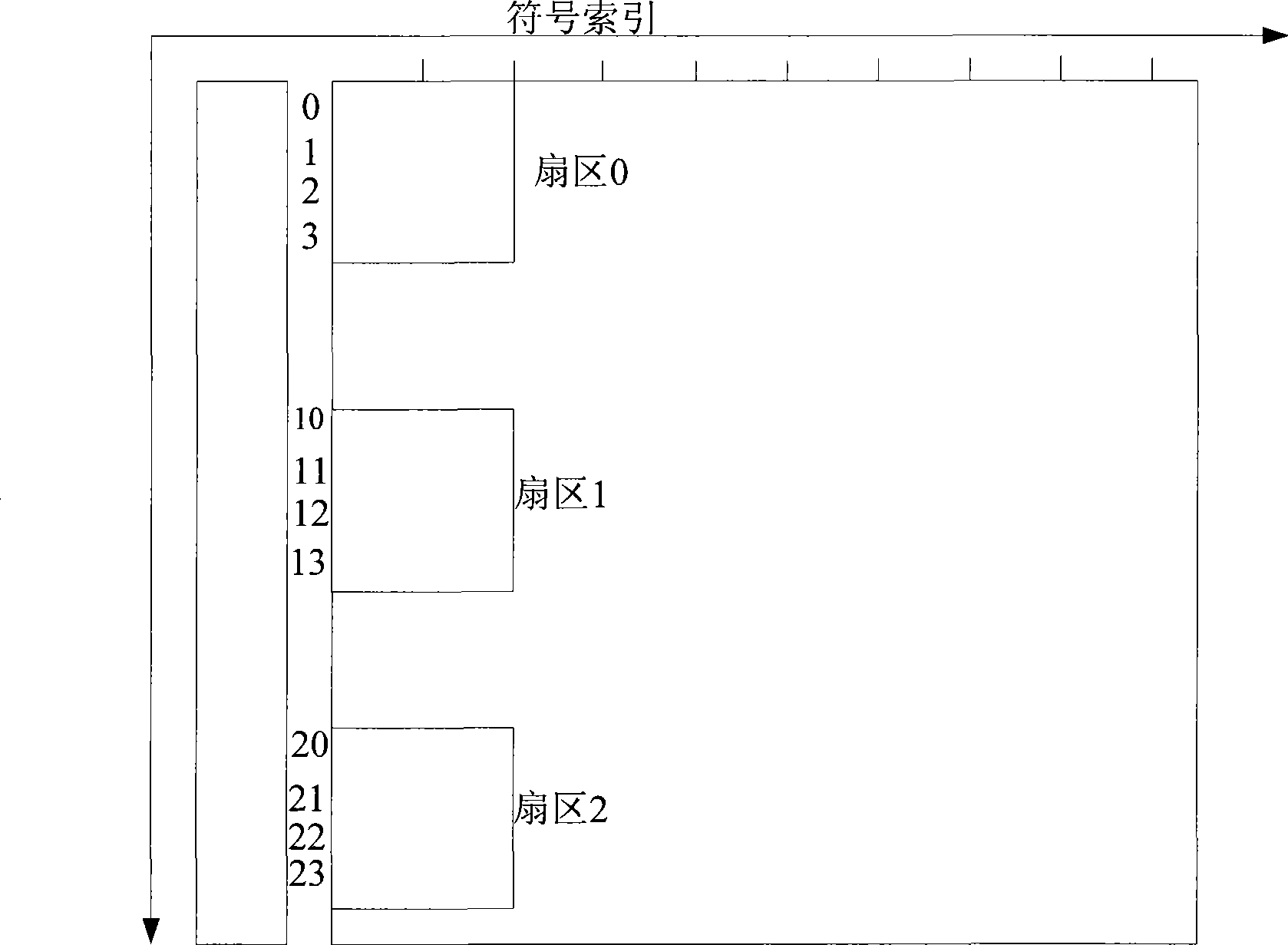
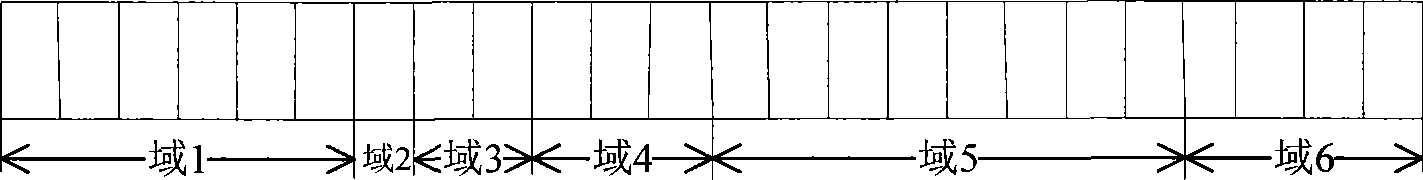
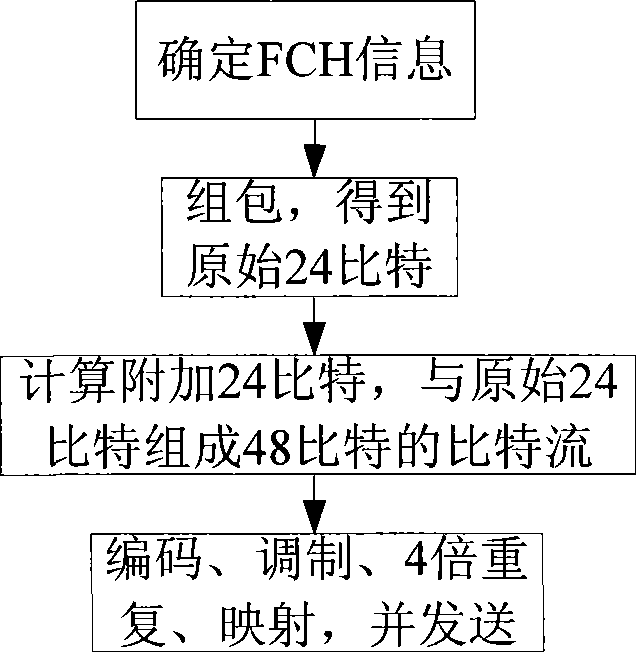
ActiveCN101686218ASave software and hardware resourcesSave resourcesError preventionMulti-frequency code systems24-bit48-bit
The invention relates to a method for OFDM system to transmit and receive frame prefix. The transmitting method includes that: a base station firstly assembles frame prefix information into package, so as to obtain original 24 bits; then additional 24 bits are calculated and forms 48 bits required by frame prefix coding with the original 24 bits; coding, modulating and four times repetition are carried out on the bit stream of the 48 bits, and the 48 bits are mapped into four sub channels to be transmitted; the receiving method includes that: a receiving terminal firstly extracts corresponding data in four channels, and demodulating, decoding and de-interlacing are carried out on the data to obtain bit stream of the 48 bits; then verification 24 bits are calculated; the verification 24 bits are compared with the rear 24 bits of the 48 bits, if coincident, decoding is correct, frame configuration information is reported to high layer; or else, decoding is error, and an error message isreturned to the base station. The invention can save system soft hardware resource while the receiving terminal analyzes error.
Owner:ZTE CORP
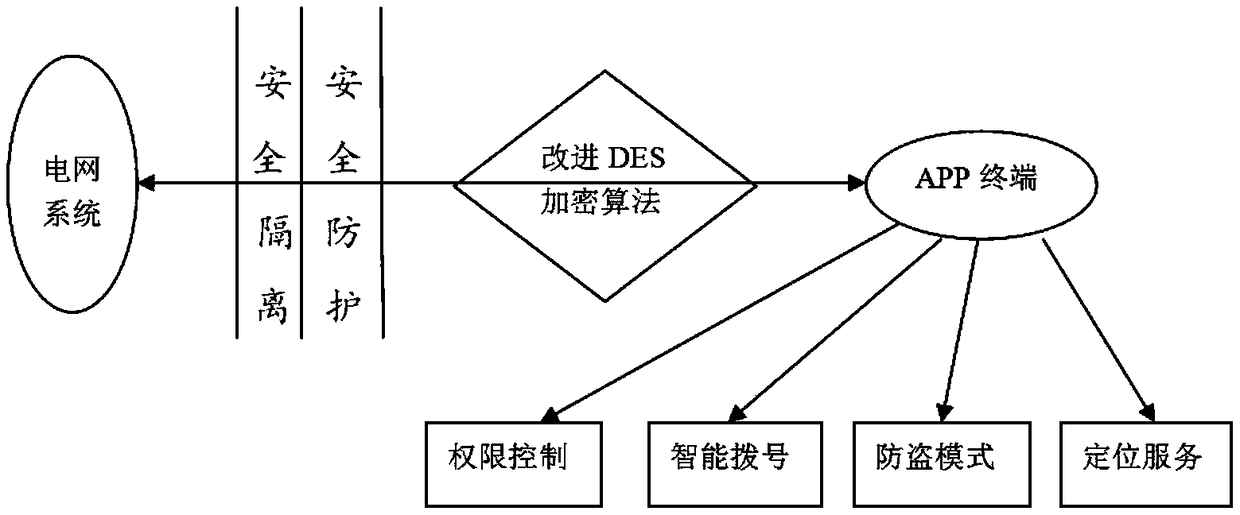
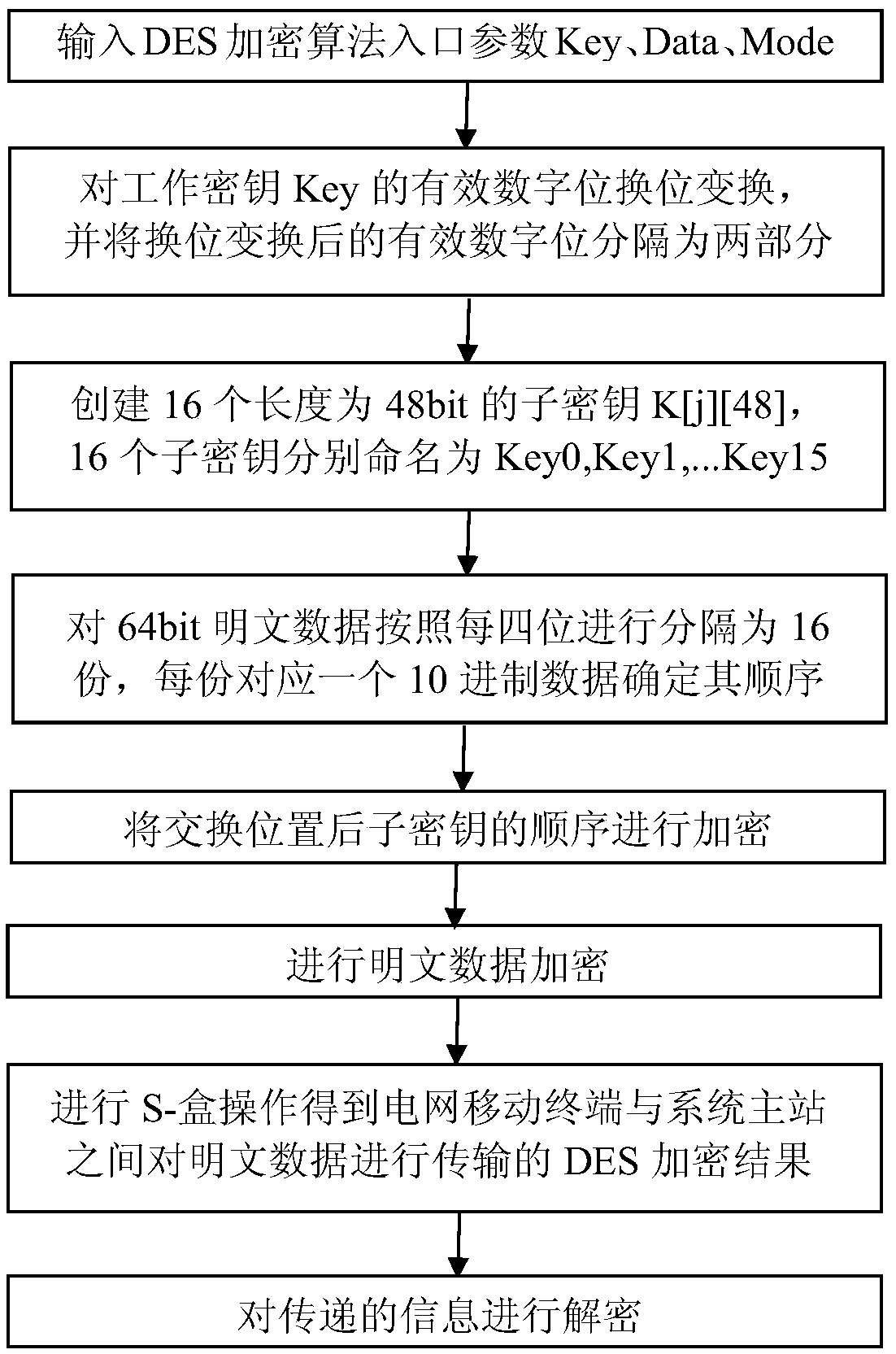
Data transmission method for grid mobile terminal based on improved DES encryption algorithm
InactiveCN108737070AReduce complexityOperational efficiency is not compromisedEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresPlaintextS-box
The invention relates to a data transmission method for a grid mobile terminal based on an improved DES encryption algorithm, comprising: inputting an entry parameter of a DES encryption algorithm, translating and dividing the significant digits of the key Key into two parts, creating 16 sub-keys K[j][48] having a length of 48 bits, dividing the 64-bit plaintext data into 16 copies every four bits, encrypting the order of the sub-keys after the location exchange, encrypting the plaintext data, performing S-box operation to obtain the DES encryption result of the transmission, and decrypting the information transmitted. At the same time, a right control module, an anti-theft mode and positioning service module, and a smart dialing module are added on the mobile terminal side. The inventionmakes the attacker cannot obtain the transformation situation through a large amount of plaintext, reduces the complexity and cumbersomeness of the algorithm, and makes the operation efficiency of thealgorithm basically not affected, makes the complex degree of the exhaustive attack also become more cumbersome since the sub keys change corresponding to the order of the transformation, and greatlyimproves the security of data protection.
Owner:STATE GRID SHANDONG ELECTRIC POWER COMPANY RIZHAOPOWER SUPPLY
Method and apparatus for handling data transfers
InactiveUS6892274B2Input/output to record carriersFilamentary/web record carriers48-bitData transmission
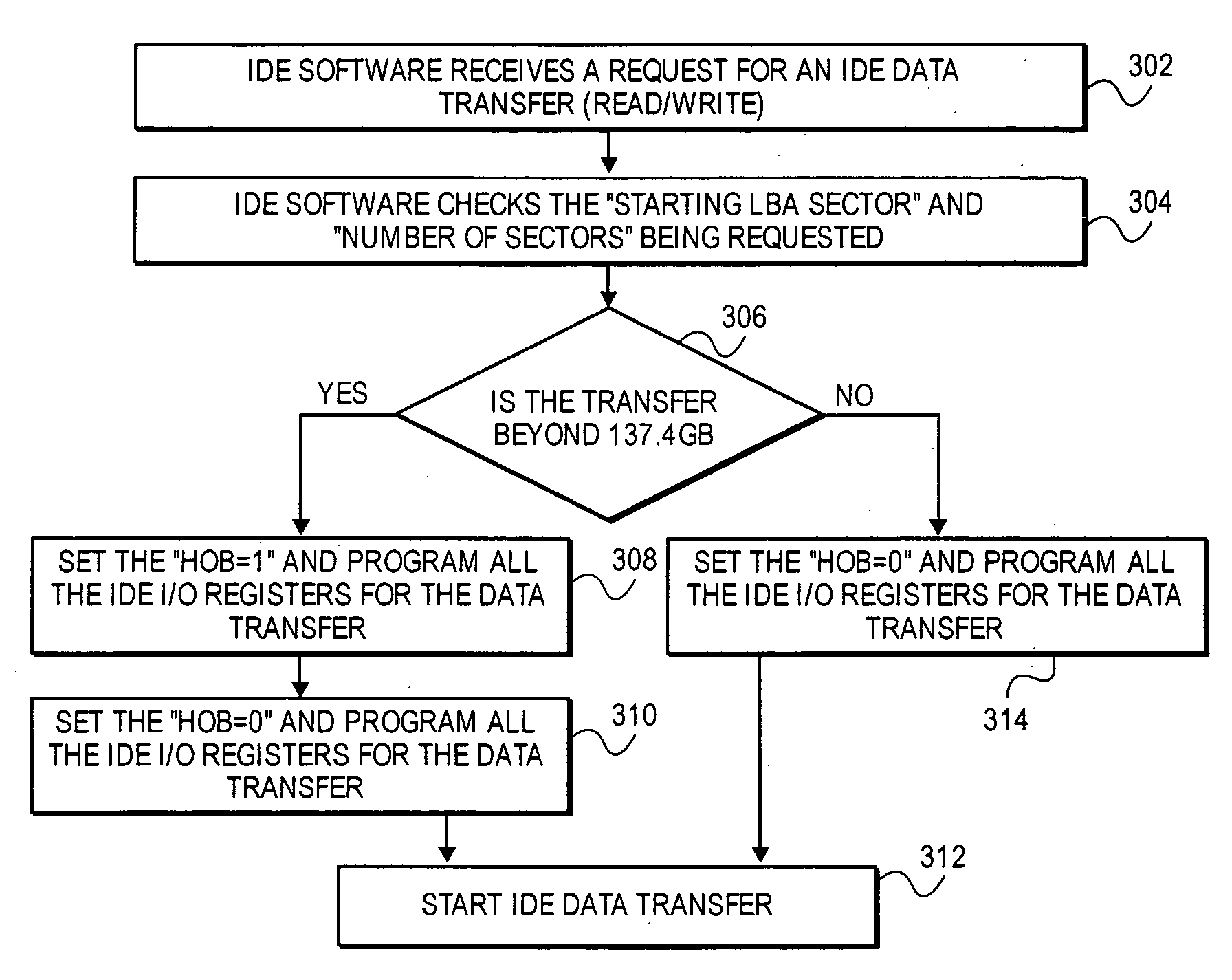
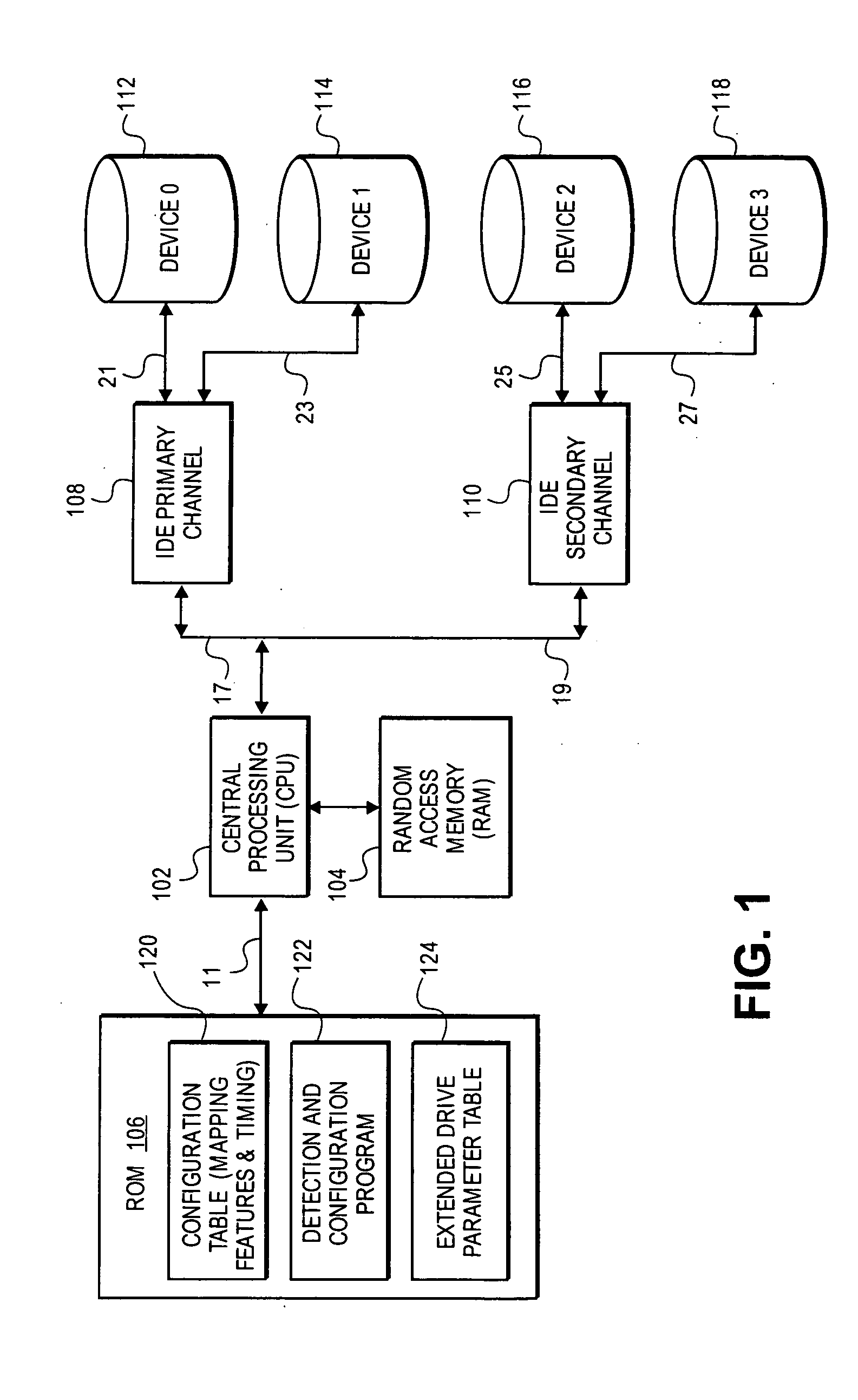
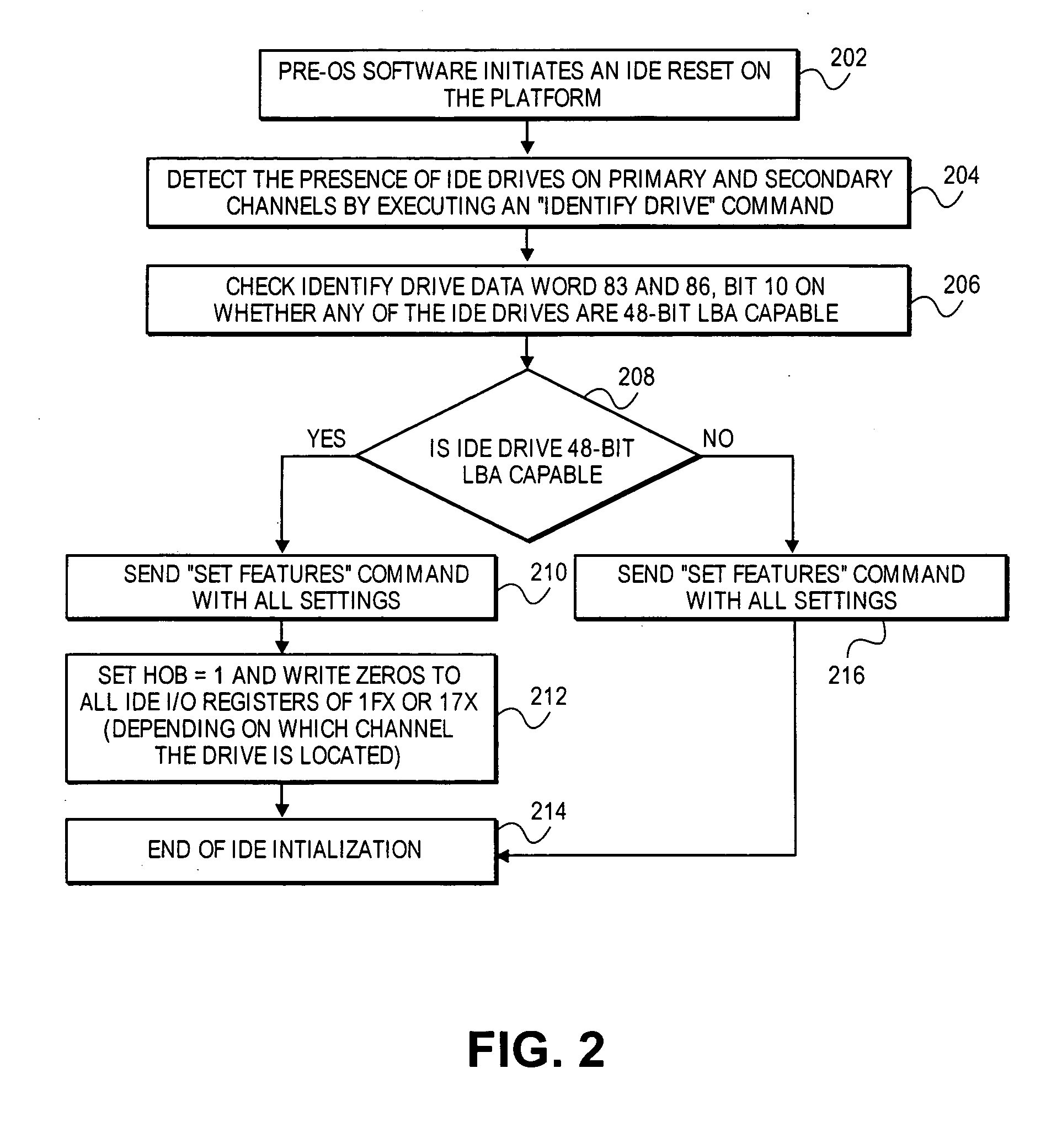
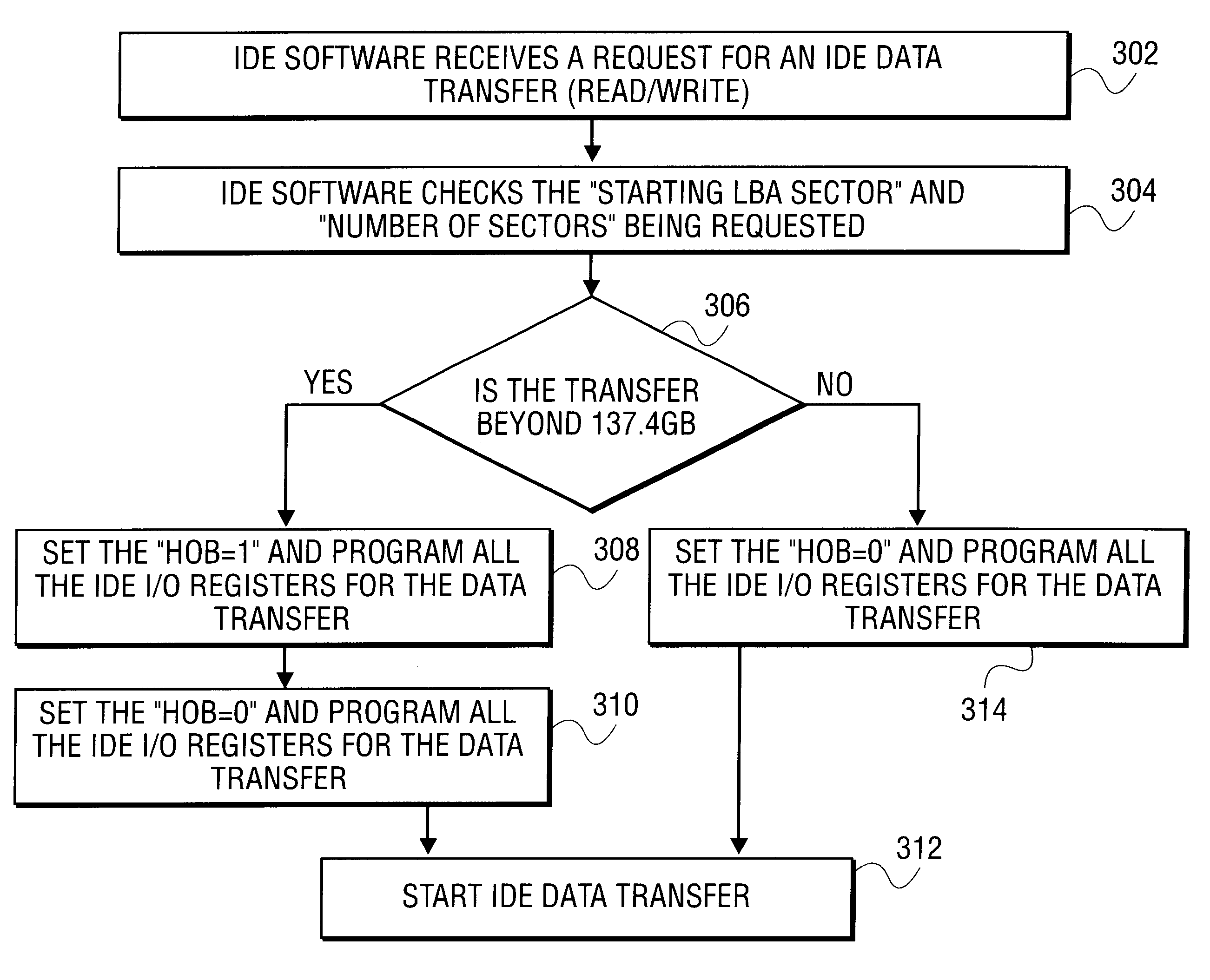
Embodiments of the present invention provide for implementation of data transfers in an efficient manner. The 48-bit LBA mechanism requires two sets of I / O writes to IDE registers on primary channel or secondary channel. The two sets of I / O writes to the primary or secondary channel registers are performed by setting a status register to a first or second state appropriately depending on the data. Embodiments of the present invention provide a single set of writes to I / O registers when the size of the data transfer is equal to or below a threshold value.
Owner:INTEL CORP
Methods and devices for generating and forwarding translated MAC addresses
ActiveUS8077720B2Reduce in quantityIncrease the number ofTime-division multiplexData switching by path configurationNetwork packet48-bit
The number of MAC addresses and corresponding tables that need to be stored to forward messages in a network is substantially reduced. Conventional MAC addresses are converted to translated (sometimes called “virtual”) MAC addresses using a new hierarchical format which redefines the conventional 48-bit, MAC label. Though the MAC label is redefined the packet size remains the same. For example, the number of MAC address tables stored by a HUB node may be reduced from 60,000 to 8 while the number stored at a POP node may be reduced from 120,000 to 8 in a “flat” Ethernet design.
Owner:RPX CORP +1
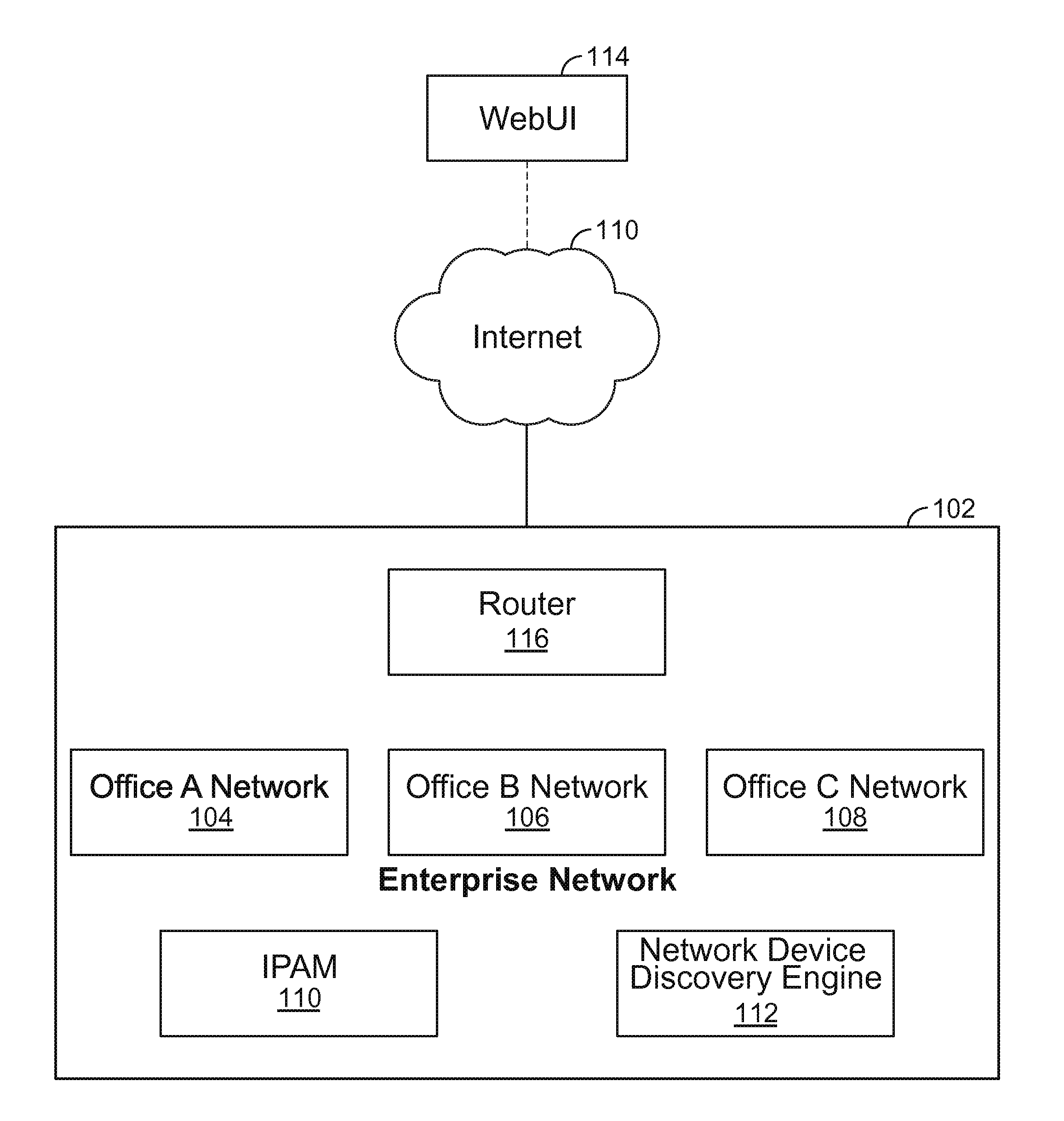
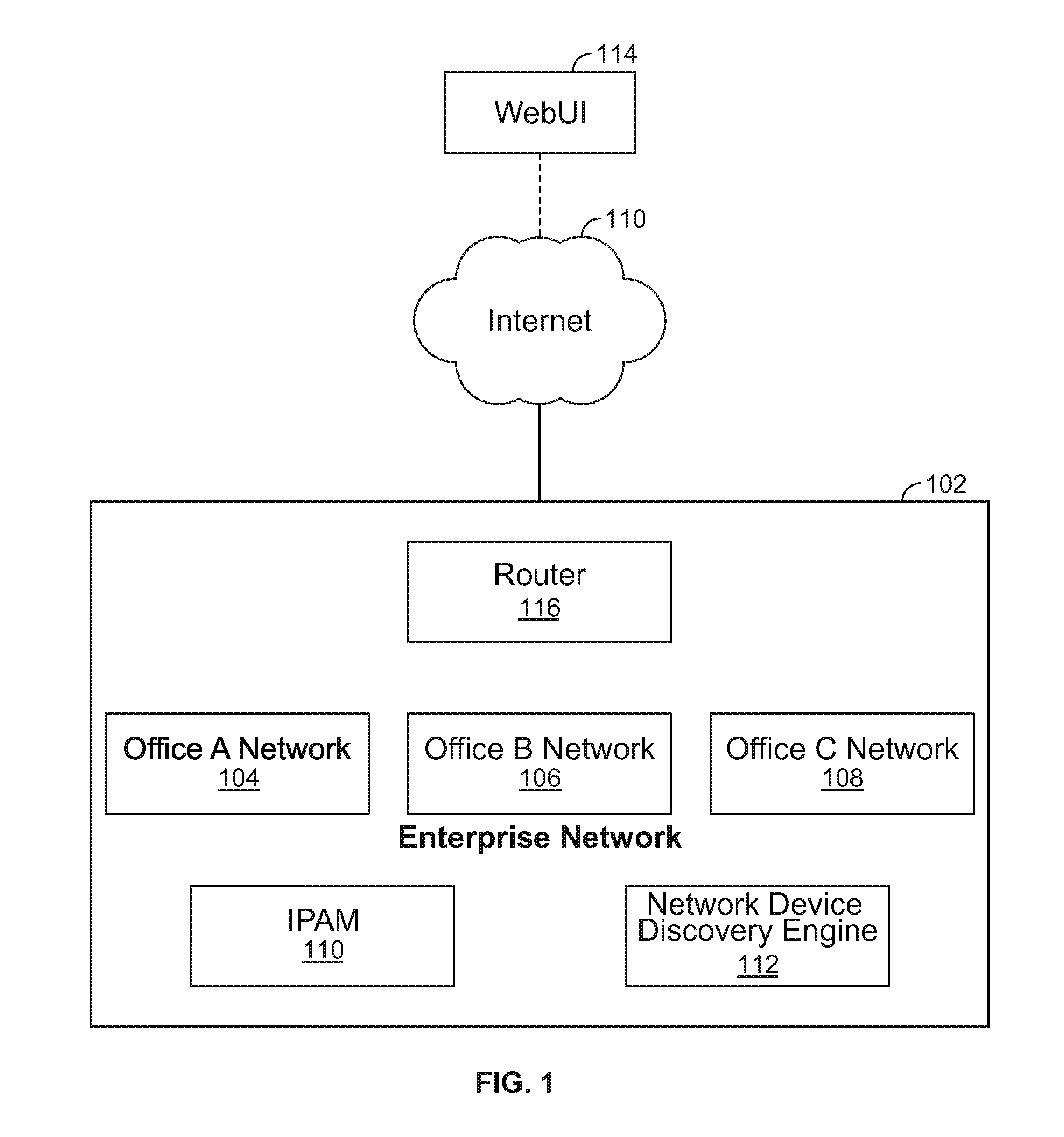
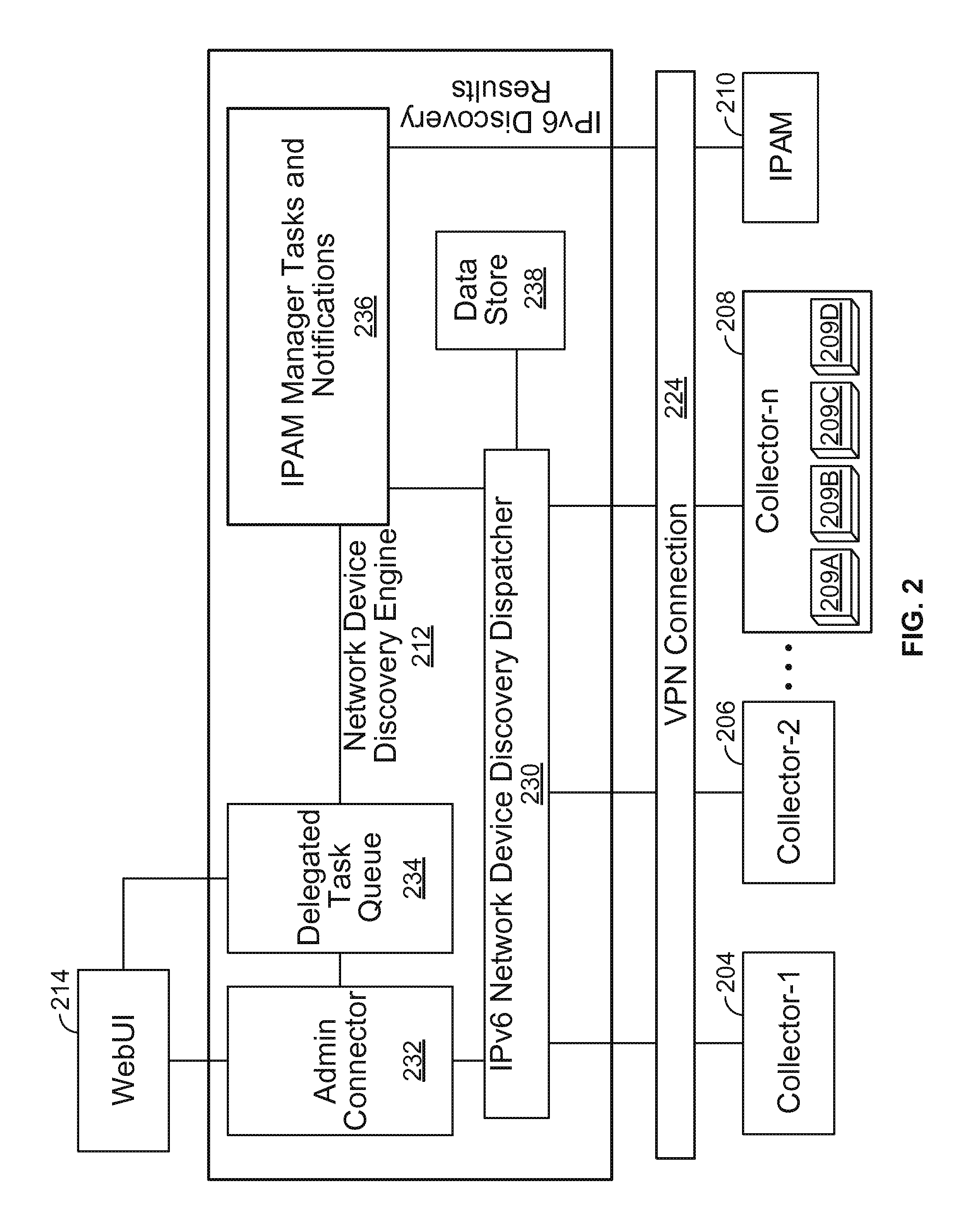
IPv6 network device discovery
Internet Protocol version 6 (IPv6) network device discovery techniques are disclosed. In some embodiments, IPv6 network device discovery includes determining a route entry (e.g., selecting a first route entry that is less than 126 bits and greater than 48 bits) of a route entry table of a seed device (e.g., a router, such as a well connected router); converting the route entry to an anycast address; and sending a probe to the anycast address. For example, using various techniques described herein, an Internet Control Messaging Protocol (ICMP) probe, for example, with incrementing hop count and the subnet-router anycast addresses as targets can be used to fully discover network devices on an IPv6 network.
Owner:INFOBLOX
UMTS authenticating vector generating method based on service network label
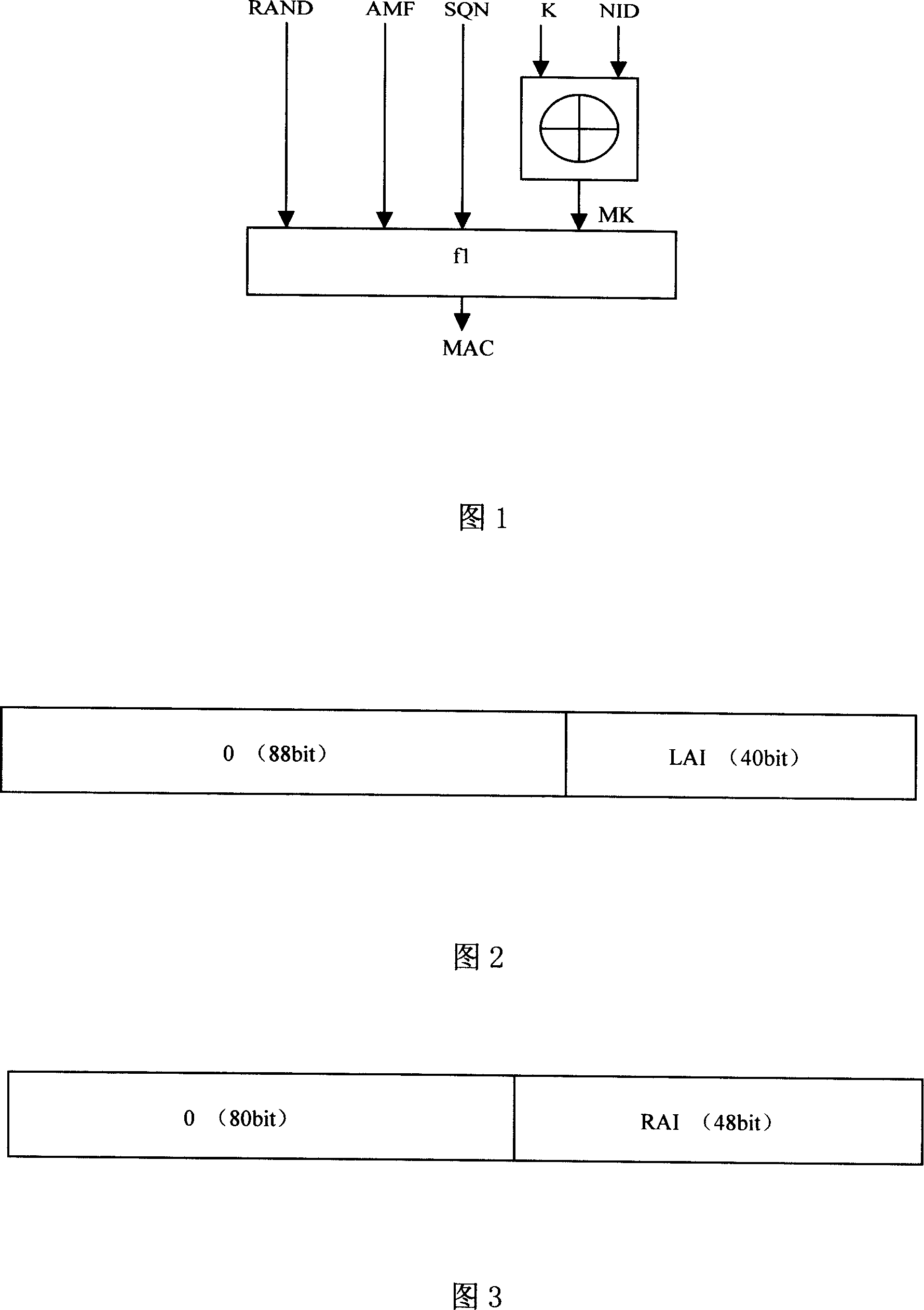
InactiveCN101026863AImprove security strengthPrevent Relocation AttacksRadio/inductive link selection arrangementsSecurity arrangementThird generation48-bit
First, the method calculates intermediate quantity MK,MK=KNID according to formula, where K is cipher key shared by home network and user, NID is as ID of service network with length equal to 128bit. When service network is circuit-switching domain, lower 40 bit of NID are location area indication LAI, and higher 88 bit are zero. When service network is packet switching domain, lower 48 bit of NID are route area indication RAI, and higher 80 bit are zero. Then, using f1 algorithm calculates MAC in AUTH being as one of quintuple of UMTS authentication vectors. The invention can raise security intensity of UMTS network access authentication, being suitable to third generation of mobile communication system.
Owner:上海宇梦通信科技有限公司
Method and device for self adaptive quick loop detection and loop blocking
InactiveCN100479387CDoes not take up bandwidthLow costData switching networksControl layerBroadcast radiation
The invention involves a method and a device for adaptively fast detecting loop circuit and interdiction, in which, the key is continuous detection whether to receive its own data packets sent to the Ethernet in each port. If the data packet is detected, it will be discarded and the port is set to obstruction state for blocking the loop circuit, limiting the broadcast and proliferation of broadcasting storm in the Ethernet, and avoiding influence to the other normal data operations. In the invention, there is no CPU, the visit to source MAC address of control layer and a 12-bit VLAN ID logo by medium of 48-bit Ethernet frames sent and received on the port, as a key information, its logic operation, learning, searching, comparison and so on, enhance adaptability and speed of loop detection and prevention, without occupying network bandwidth and effecting the normal network data transmission.
Owner:WUHAN FIBERHOME NETWORKS
64-bit single cycle fetch scheme for megastar architecture
ActiveUS6918018B2Easy to handleChange is minimalDigital computer detailsConcurrent instruction executionMemory interfaceMemory bank
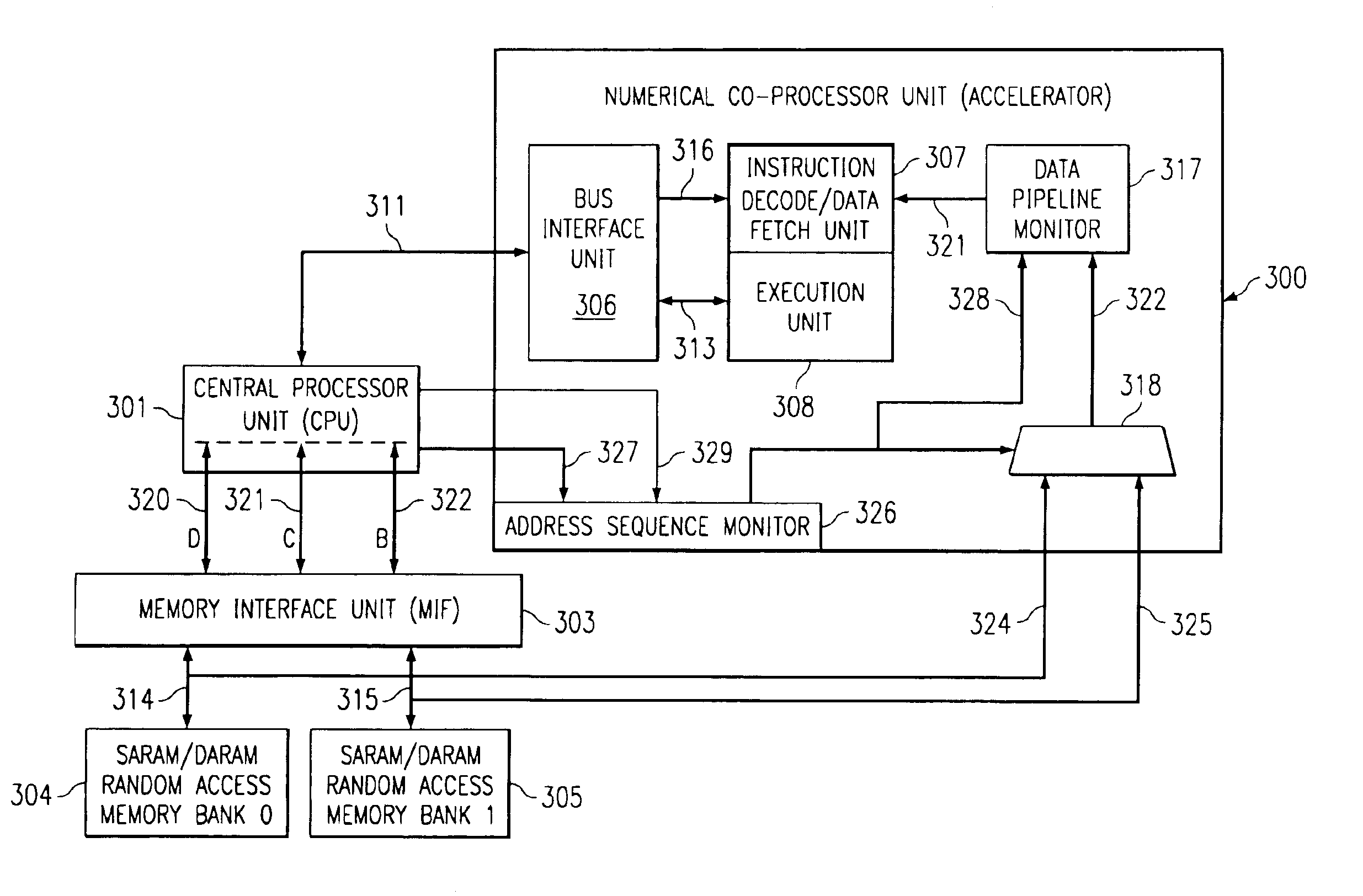
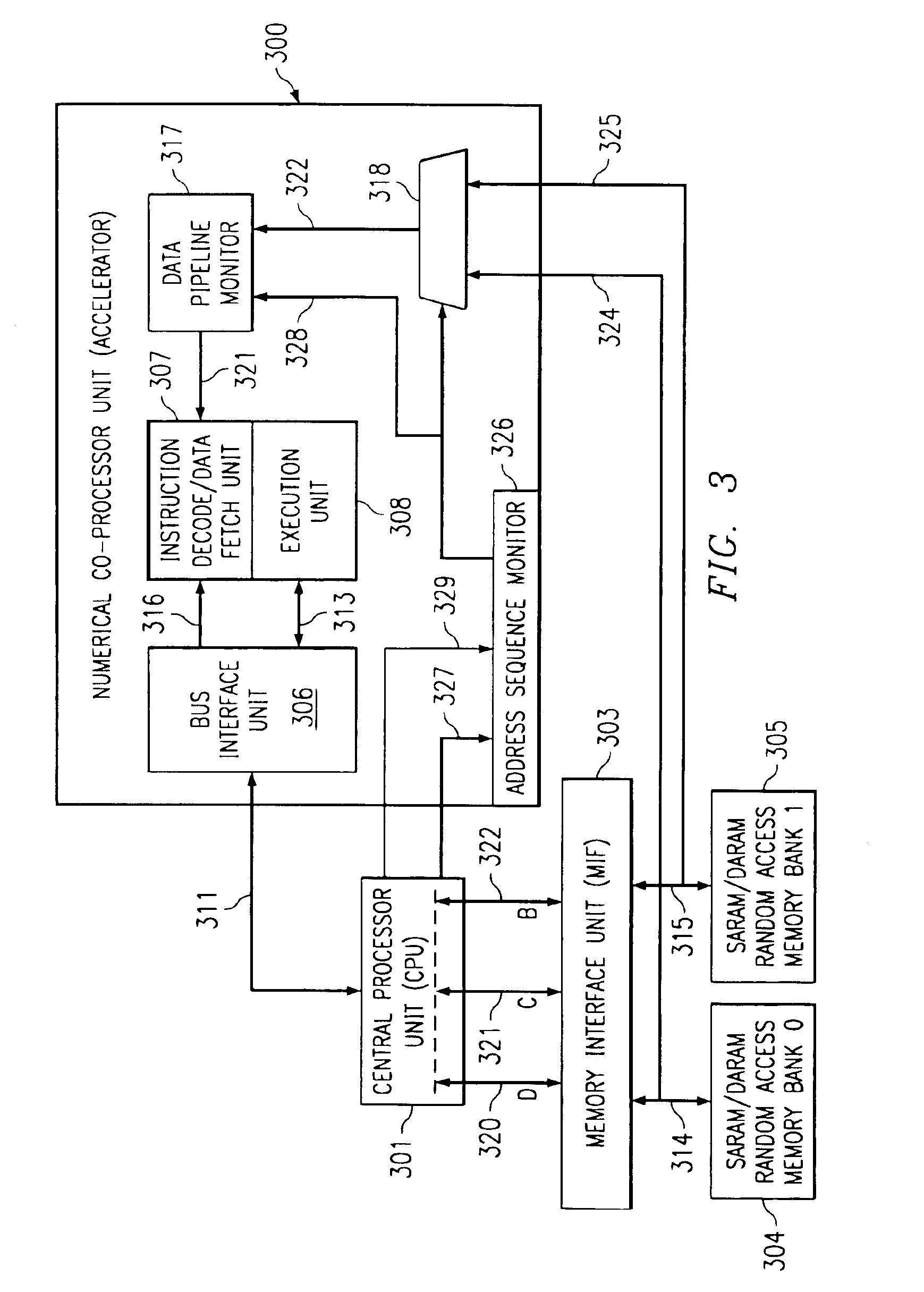
The 64-bit single cycle fetch method described here relates to a specific ‘megastar’ core processor employed in a range of new digital signal processor devices. The ‘megastar’ core incorporates 32-bit memory blocks arranged into separate entities or banks. Because the parent CPU has only three 16-bit buses, a maximum read in one clock cycle through the memory interface would normally be 48-bits. This invention describes an approach for a fetch method involving tapping into the memory bank data at an earlier stage prior to the memory interface. This allows the normal 48-bit fetch to be extended to 64-bits as required for full performance of the numerical processor accelerator and other speed critical operations and functions.
Owner:TEXAS INSTR INC
Apparatus, method, and system for coalesced Z data and color data for raster operations
ActiveUS7847802B1Improve access efficiencyImprove packaging efficiencyMemory adressing/allocation/relocationCathode-ray tube indicatorsData capacityGraphics
A graphics system coalesces Z data and color data for a raster operations stage. The Z data and color data are stored in a memory aligned tile format. In one embodiment, rendering modes in which the tile does not have a data capacity corresponding to Z data or color data for a whole number of pixels have data for at least one pixel split across entries to improve packing efficiency. Rendering modes having a number of bits for Z data or color data that does not equal a power of two such as 24 bits, 48 bits, and 96 bits, may be implemented with a high packing efficiency in tile formats having a data capacity corresponding to a power of 2 bits.
Owner:NVIDIA CORP
Chaotic signal generating circuit
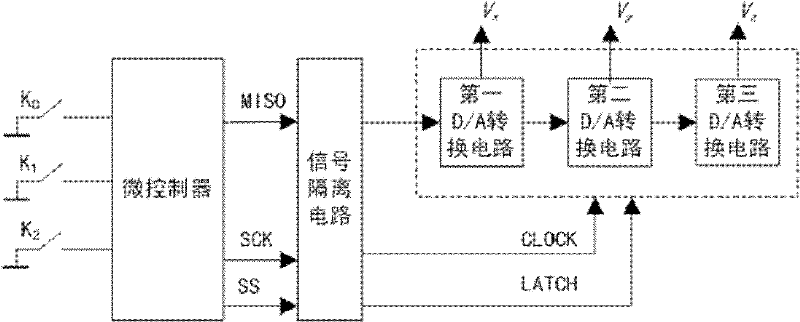
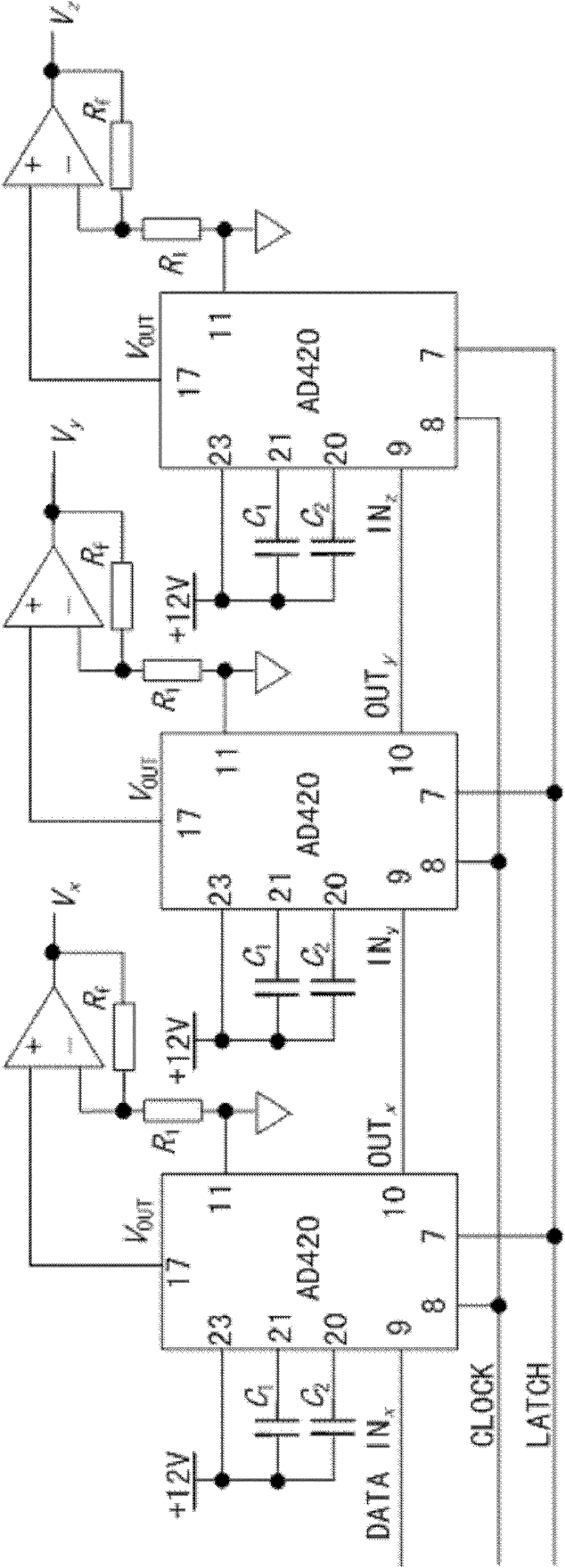
ActiveCN101834718BVerify feasibilityImprove versatilitySecuring communicationMicrocontrollerShift register
The invention relates to a chaotic signal generating circuit, comprising a microcontroller, a signal isolating circuit, three D / A switching circuits; each D / A switching circuit comprises 16-bit shift registers and 16-bit DAC registers and shift registers in each D / A switching circuit are connected in series to form a 48-bit shift register. Serial digital signals output by an SPI interface of the microcontroller are transmitted to a serial data input terminal of a first D / A switching circuit through the signal isolating circuit; clock signals and latch control signals output by the SPI interface are respectively transmitted to a clock input terminal and a latch control signal input terminal of the D / A switching circuit through the signal isolating circuit. In the invention, based on the chaotic circuit of the microcontroller, the Euler algorithm is adopted to carry out discretization processing on the continuous state equation of the improved generalized Lorenz system; as a result, theoperation algorithm which can be appropriately realized by the microcontroller is established and folding directions of chaotic attractors and system operation modes are optional.
Owner:盐城市纺织染整产业园实业开发有限公司
Arithmetic device and encryption/decryption device
InactiveCN1518733ASmall scaleReduce power consumptionEncryption apparatus with shift registers/memoriesGenerating/distributing signalsLeast significant bit48-bit
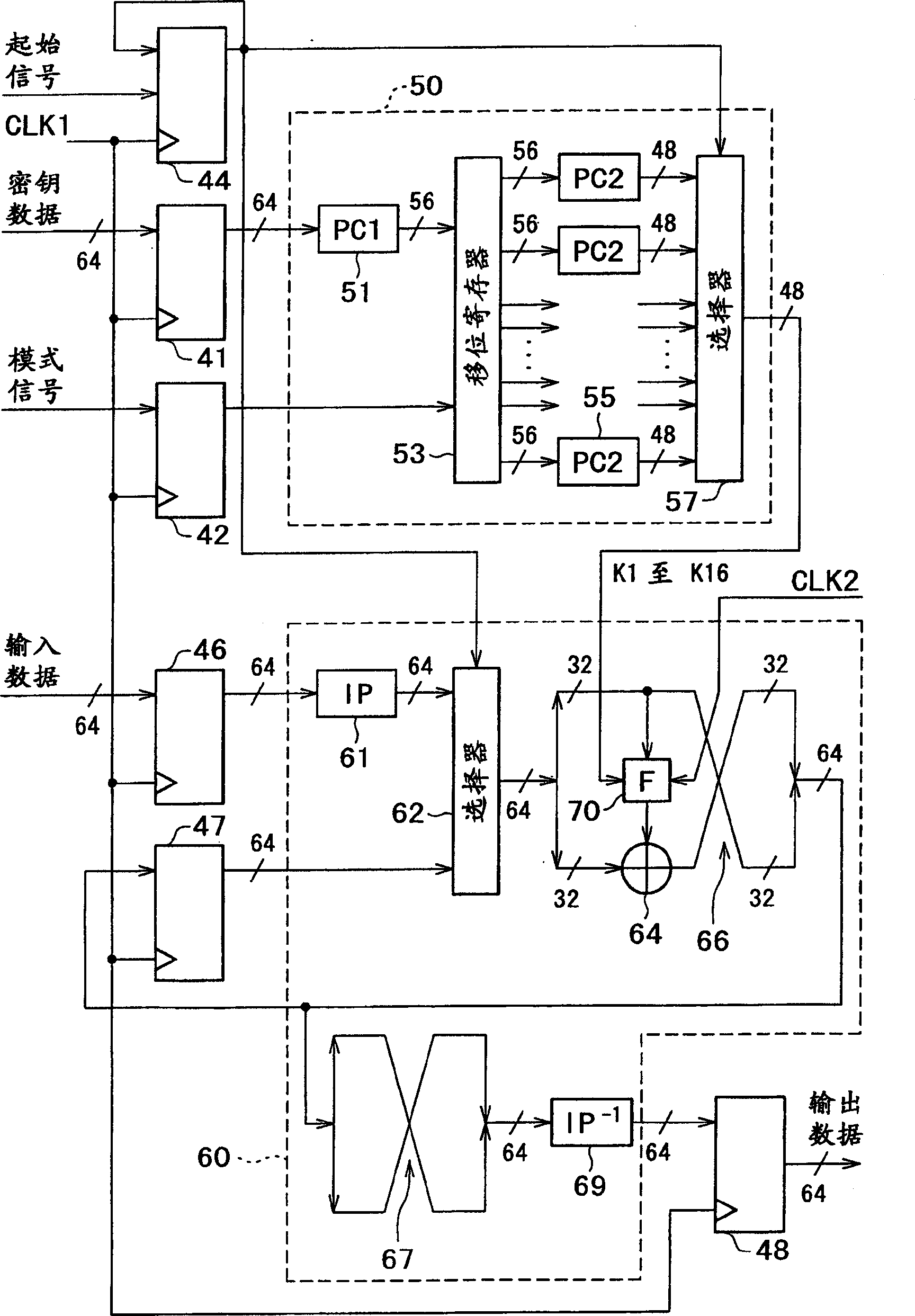
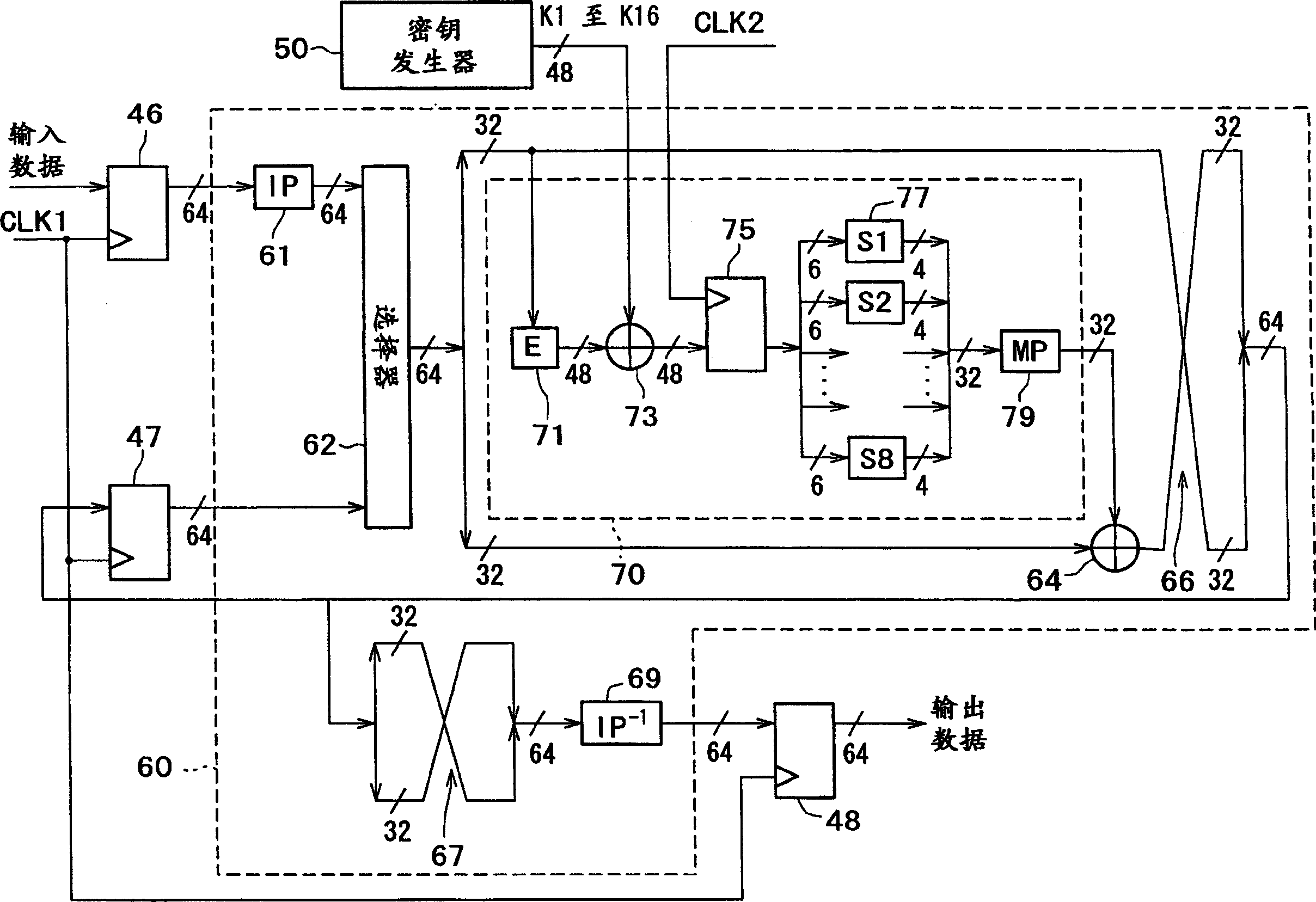
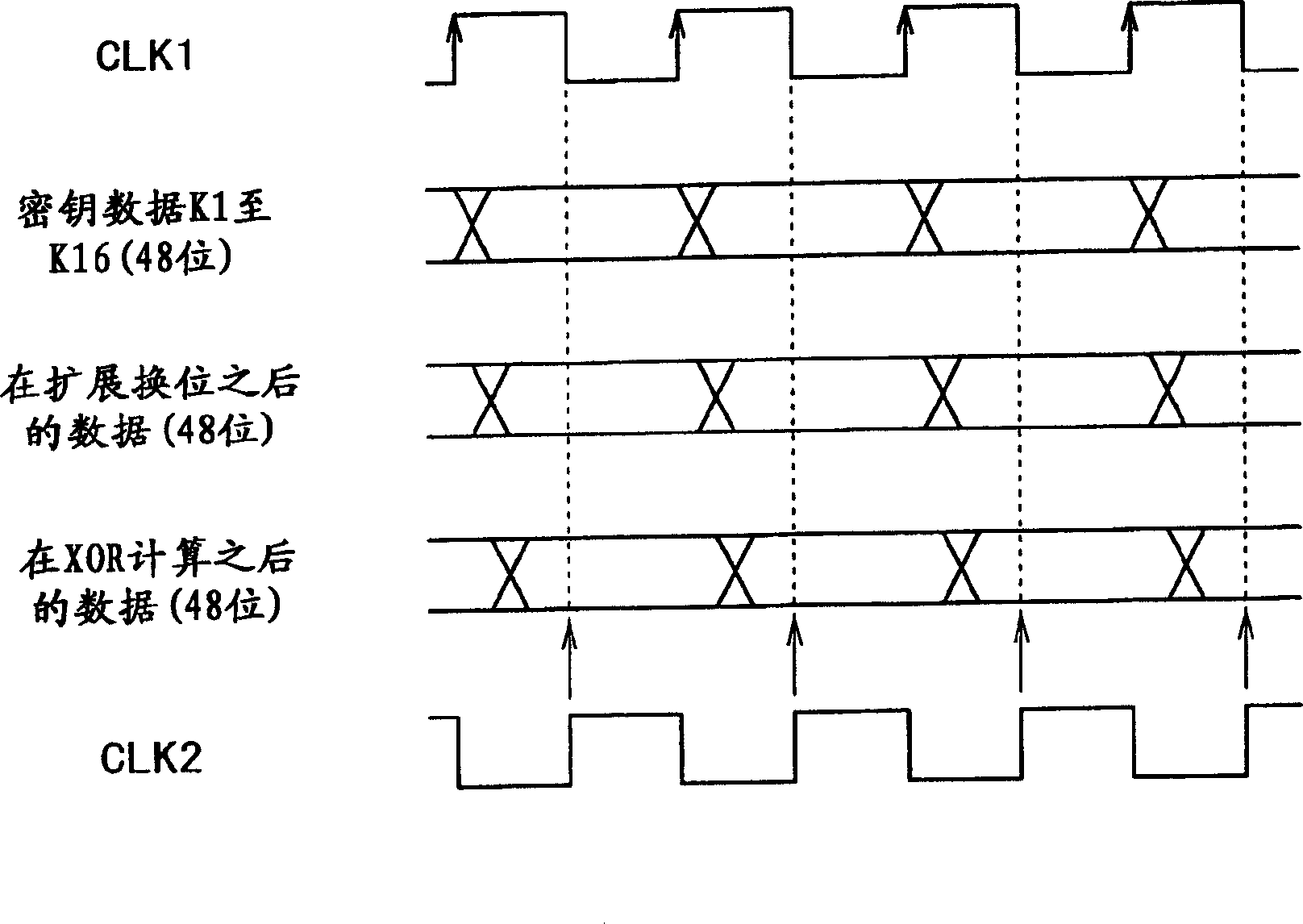
Input data (plain text data or encrypted text data) is latched by a clock CLK1 and its output is initial-inverted, after which it is output from a selector (62). The least significant bit of the output data from the selector (62) is enlarge-inverted, after which it is XOR-ed with key data K1 and latched by a clock CLK2. The 48-bit data after the latch is divided by eight into 6 bits, which is replaced by 4-bit data, synthesized, and inverted. In the arithmetic operation of the second stage and after, data reshuffle-synthesized by a reshuffle-synthesizing circuit (66) is latched by the clock CLK1 and output from the selector (62). After the arithmetic operation of the 16-th stage, the data reshuffled by a reshuffle circuit (67) is contra-inverted. Thus, it is possible to realize an encryption / decryption arithmetic device.
Owner:SONY CORP
CRC (Cyclic Redundancy Check) checking circuit applicable to 64-bit bus bit width and checking method
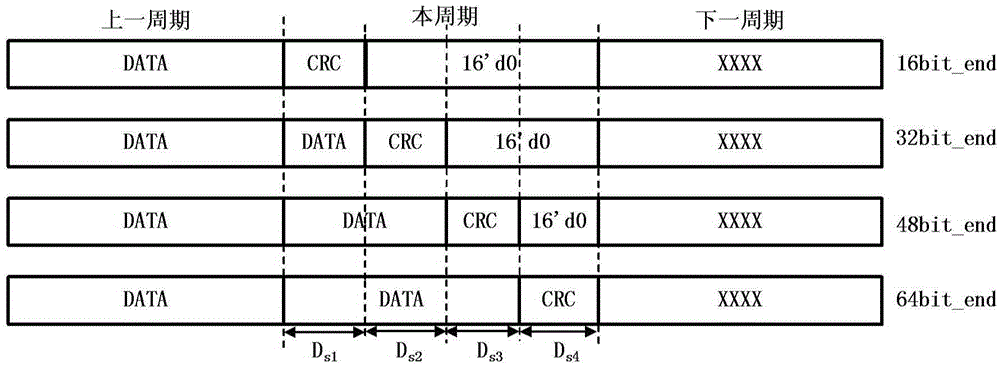
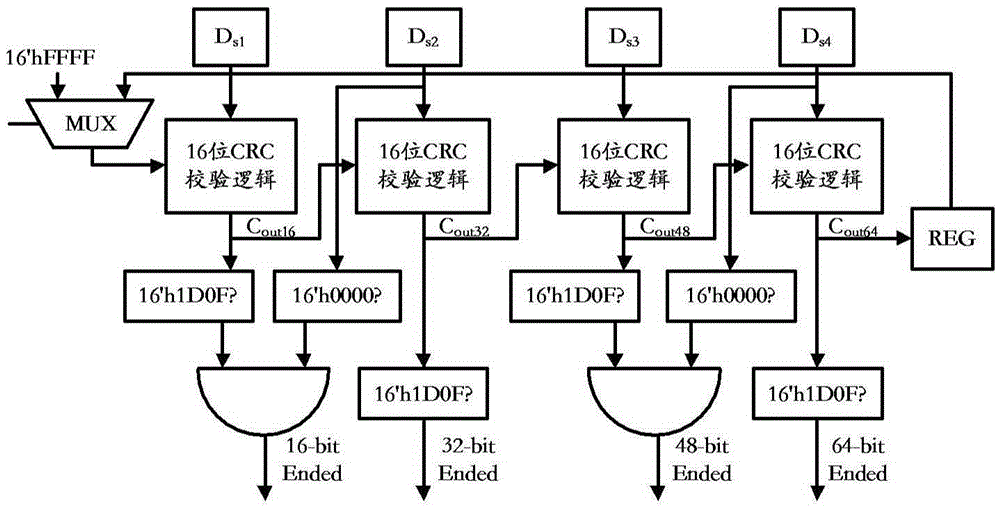
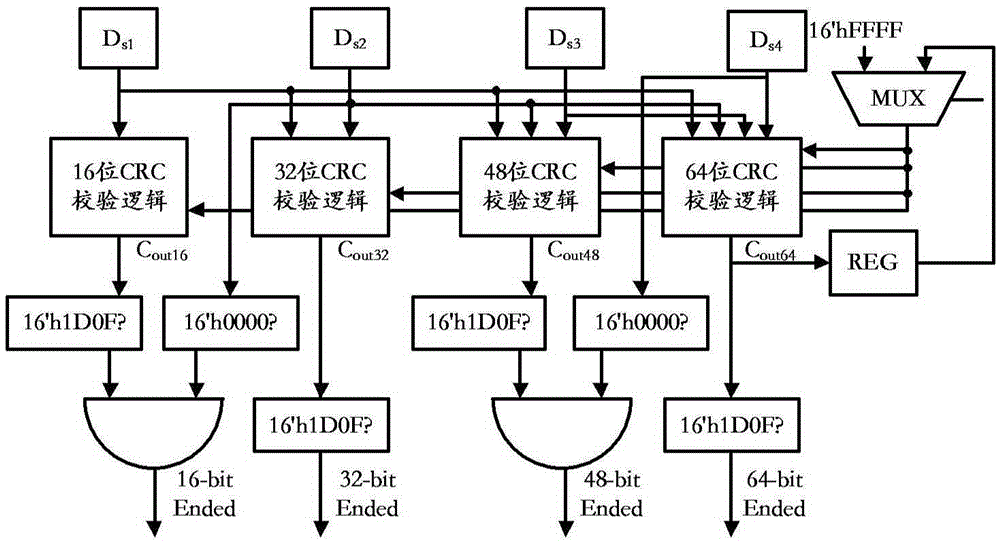
ActiveCN105389229AImplement the verification operationReduce areaRedundant data error correctionEnergy efficient computing48-bitLogic structure
The present invention provides a CRC (Cyclic Redundancy Check) checking circuit applicable to 64-bit bus bit width and a checking method, and can achieve a purpose of reducing the number of CRC-16 checkers only by means of 16-bit and 64-bit parallel CRC checkers plus an equivalent logic structure of delay determination and bitwise negation for transaction packet data in 16-bit, 32-bit, 48-bit and 64-bit alignment formats. The CRC-16 checking circuit provided by the present invention not only can implement checking of transaction packets in different sizes and different formats, but also is obviously improved in terms of area, power consumption and speed.
Owner:锐立平芯微电子(广州)有限责任公司
Method for OFDM communication system to process frame prefix
ActiveCN101686218BSave software and hardware resourcesSave resourcesError preventionMulti-frequency code systems24-bit48-bit
The invention relates to a method for OFDM system to transmit and receive frame prefix. The transmitting method includes that: a base station firstly assembles frame prefix information into package, so as to obtain original 24 bits; then additional 24 bits are calculated and forms 48 bits required by frame prefix coding with the original 24 bits; coding, modulating and four times repetition are carried out on the bit stream of the 48 bits, and the 48 bits are mapped into four sub channels to be transmitted; the receiving method includes that: a receiving terminal firstly extracts correspondingdata in four channels, and demodulating, decoding and de-interlacing are carried out on the data to obtain bit stream of the 48 bits; then verification 24 bits are calculated; the verification 24 bits are compared with the rear 24 bits of the 48 bits, if coincident, decoding is correct, frame configuration information is reported to high layer; or else, decoding is error, and an error message isreturned to the base station. The invention can save system soft hardware resource while the receiving terminal analyzes error.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com