Method, branch node and center node for transmitting multicast in IPsec tunnel
A central node and branch node technology, applied in the field of data communication, can solve problems such as increased operation and maintenance costs, video service delays, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
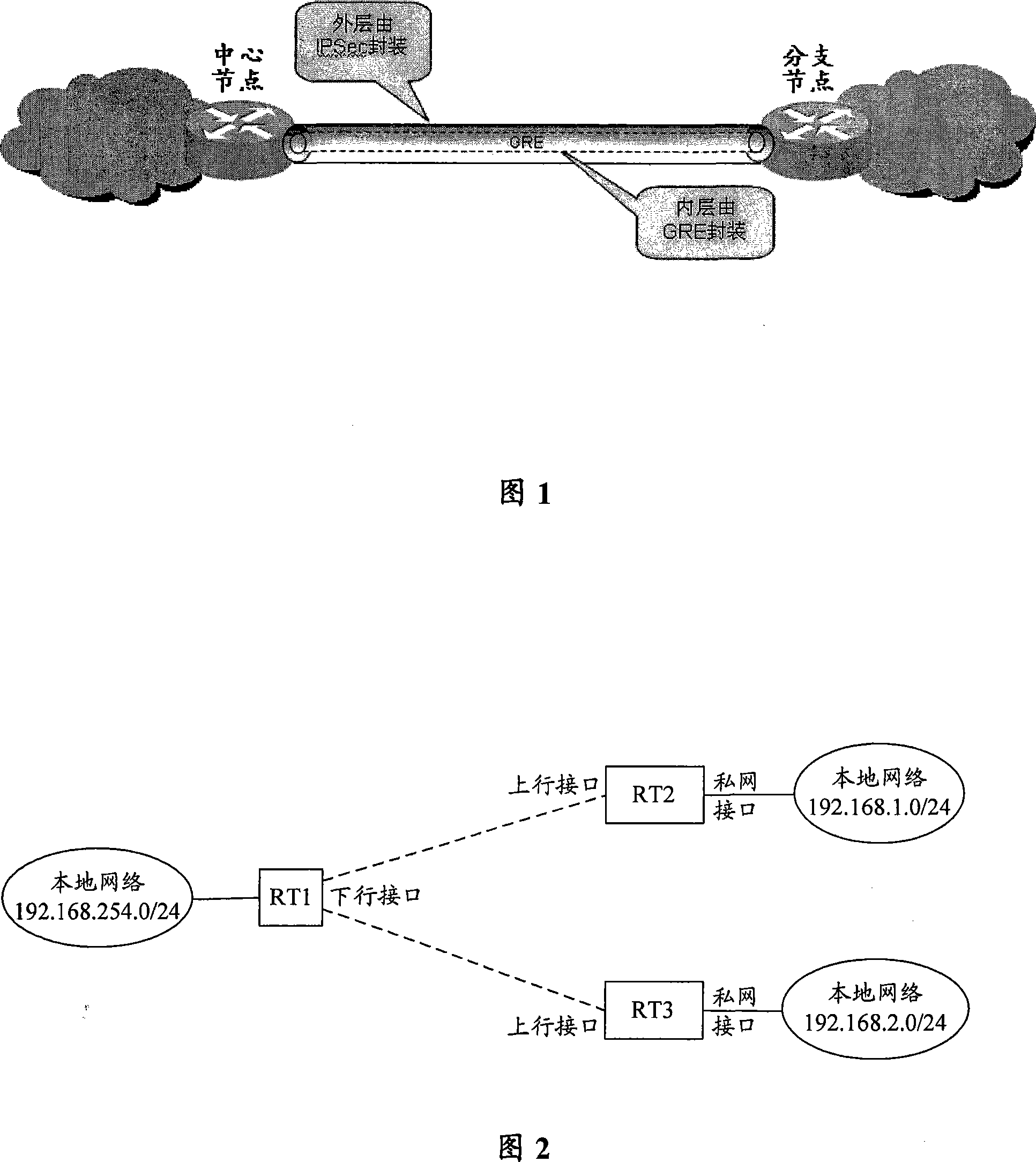
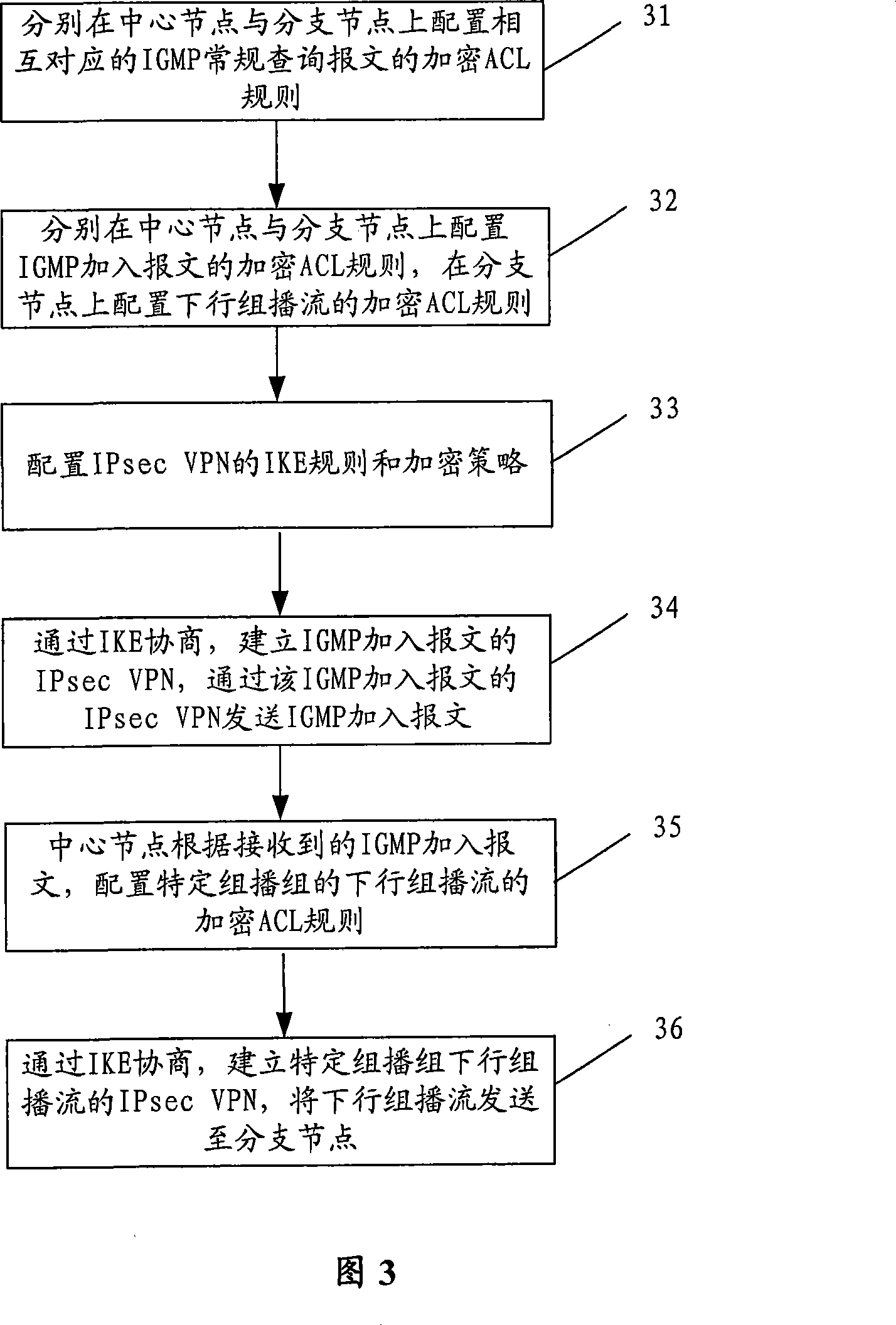
[0082] In order to better understand the method for transmitting multicast in the IPsec tunnel described in the embodiment of the present invention, a common WAN multicast on-demand scheme is firstly introduced: in this scheme, the central node enables the IGMP function as a queryer, and the branch nodes enable The IGMP proxy proxies on-demand requests for the branch network. According to the normal multicast on-demand process, first, the client generates an on-demand request, that is, an IGMP join message, and applies to join a certain multicast group G, and then the routing and switching node generates an IGMP multicast entry according to the above join message, namely ( * , G) entry, and at the same time, the interface that receives the IGMP join message is used as the outgoing interface of the multicast group. If there is a source S of the multicast group, the routing and switching node will generate (S, G) multicast table item, and send the multicast stream to all outgoin...
Embodiment 2
[0115] Referring to FIG. 5 , it is a flowchart of a method for transmitting multicast in an IPsec tunnel according to another embodiment of the present invention. The difference between this embodiment and the method described in the embodiment of FIG. 4 is that the central node and the branch nodes run the PIM protocol to maintain the multicast routing, instead of using the IGMP proxy to realize the multicast forwarding, and the nodes running the PIM protocol send greetings (hello) PIM protocol messages such as messages and pruned messages, maintain PIM multicast entries, and the PIM multicast entries include multicast source address, multicast group address, inbound interface, outbound interface list, timer and flag and other information. For example, the PIM protocol is run on the downlink interface of the central node, and the PIM protocol is run on the uplink interface of the branch nodes, so that the central node and the branch nodes send and receive PIM protocol packets...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com