Large number multiplier based on secondary Booth coding
A multiplier, coding technology, applied in the direction of instruments, electrical digital data processing, digital data processing components, etc., can solve problems such as restricting applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
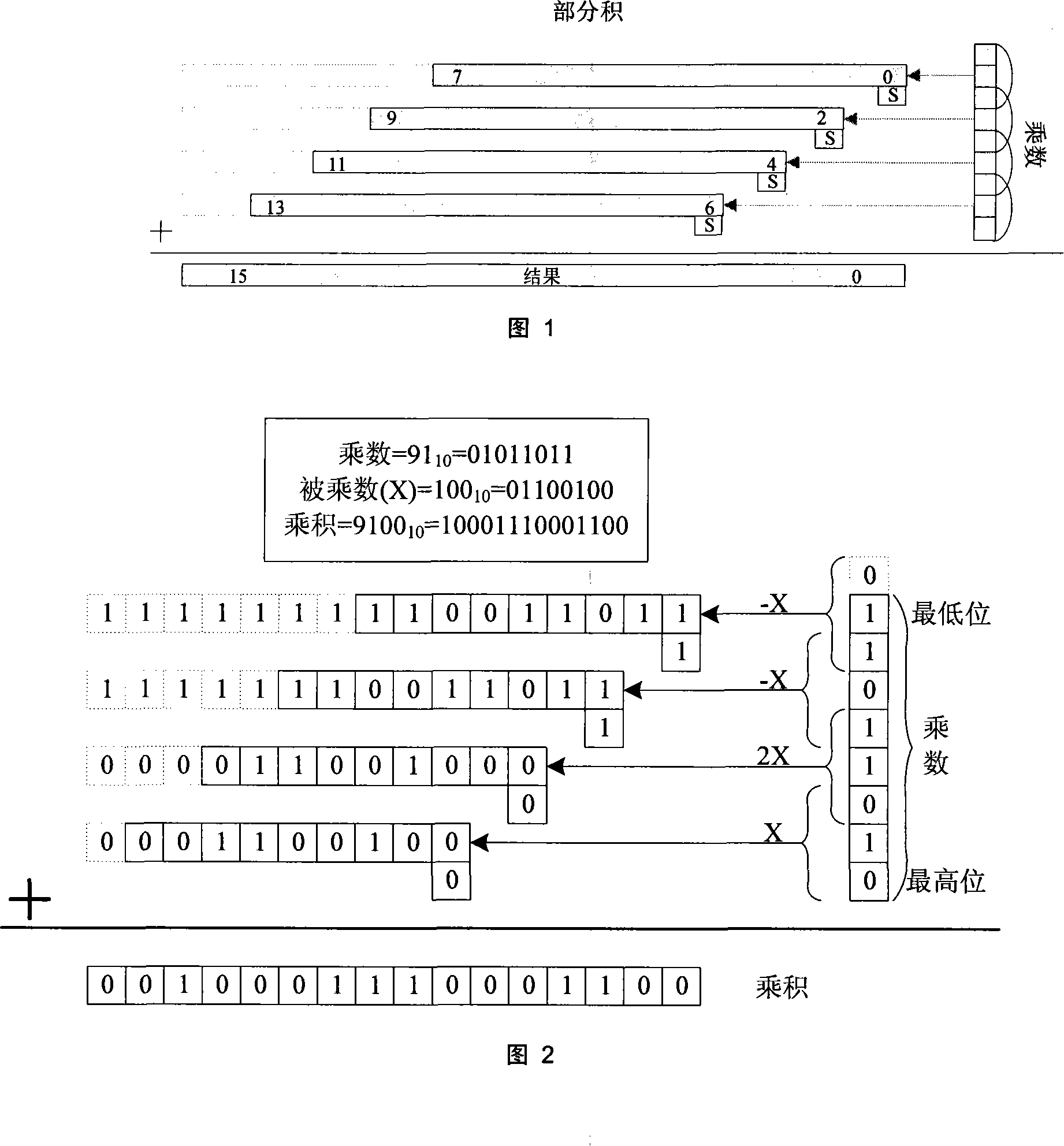
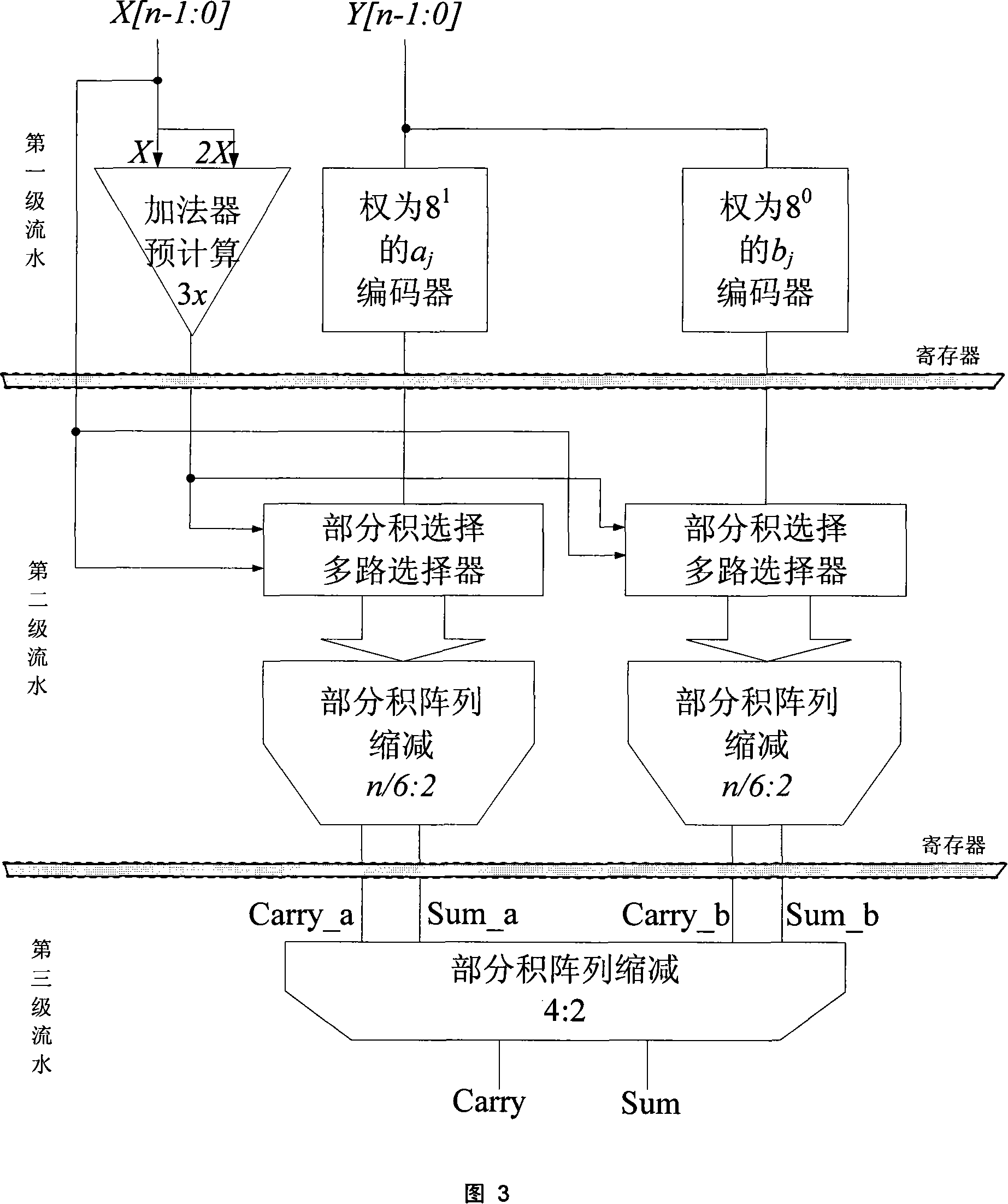
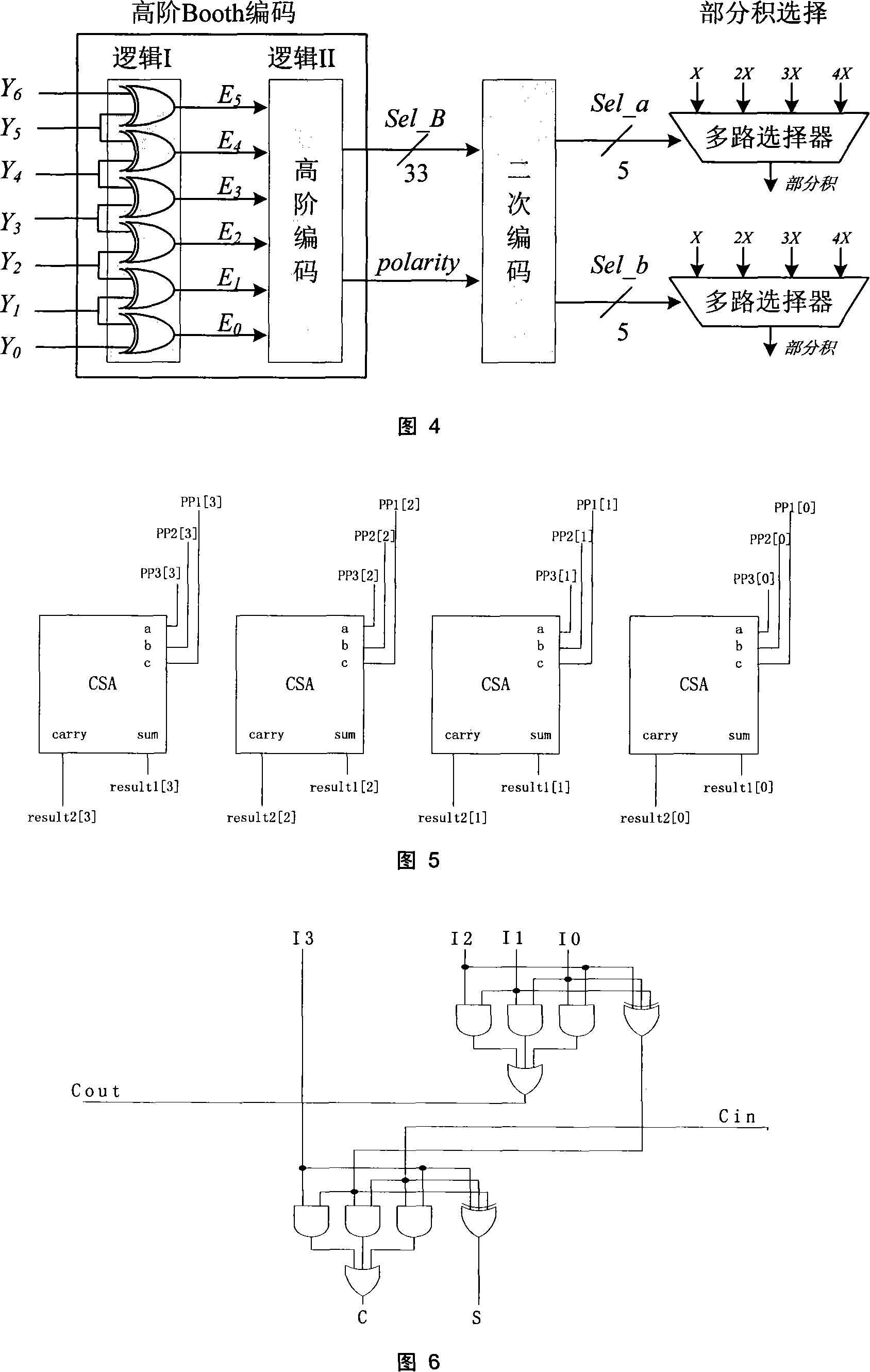
[0066] A notable feature of the present invention is that the high-order Booth64 encoding result is re-encoded by using the secondary encoding Booth64 linear transformation formula B=8a+b, so that the partial product no longer has a large number of odd multiplicand sets {±0 , ±1, ±2, ±3, ..., ±32}, but converted to selection from the set {±0, ±1, ±2, ±3, ±4}, which requires pre-calculation of the odd part to be multiplied The number of numbers is greatly reduced, the area of the multiplier is reduced, the compression rate of the partial product is increased, and the operation speed of the large number multiplier is improved.
[0067] Another feature of the present invention is that it proposes a secondary encoding Booth64 encoder structure. Booth coding logic includes three parts, which are high-order Booth coding, secondary coding and partial product selection logic. Using the information of whether the adjacent bits of the high-order Booth 64 encoding result are equal, ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com