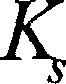Effective key management method and its operation method for sensor network with clustering structure
A sensor network and key management technology, applied in the field of effective key management of clustered sensor networks, can solve problems such as increasing system processing overhead and reducing solution applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
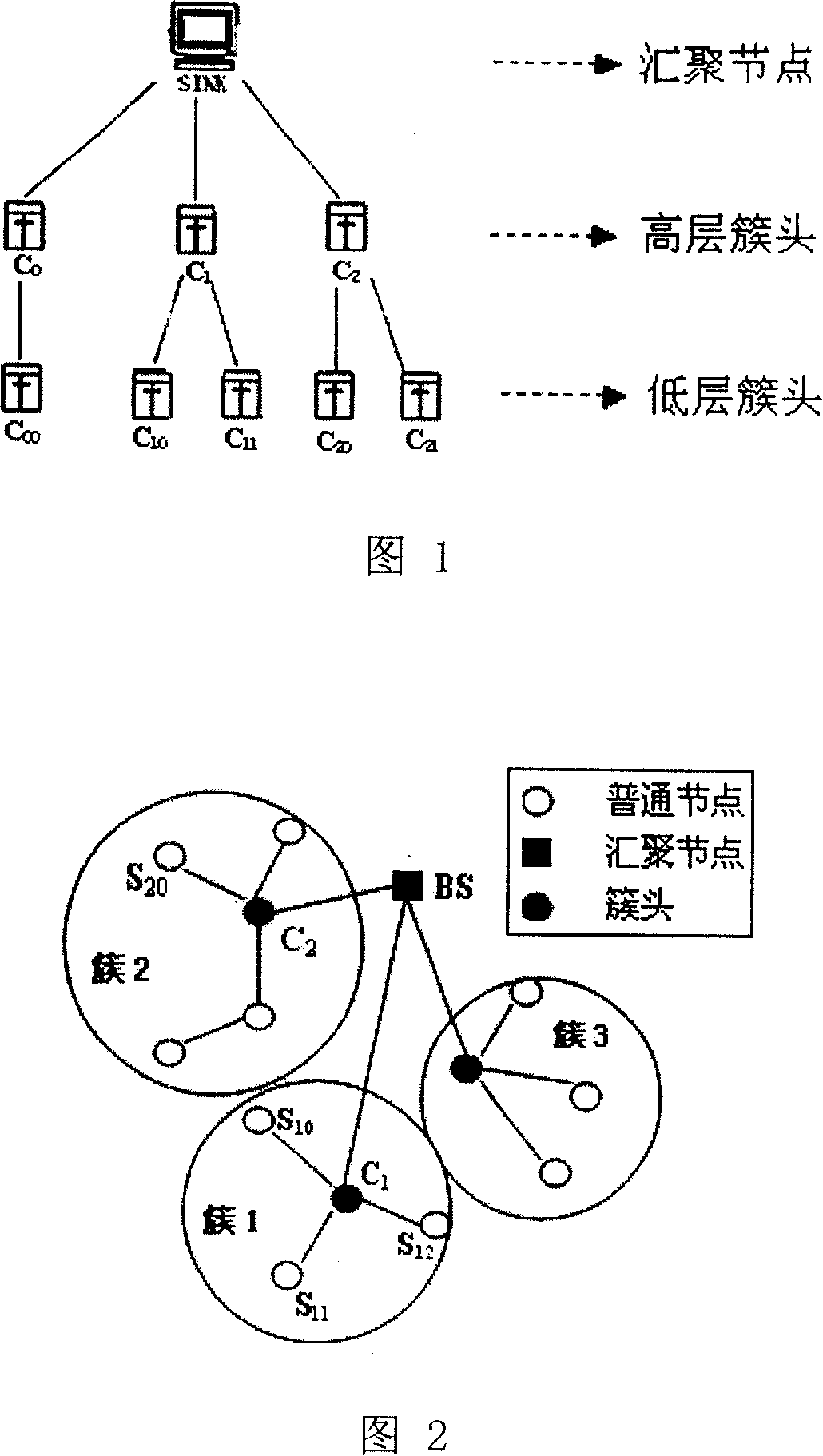
[0032] According to the structured network shown in Figure 1, the nodes in the network communicate in a self-organizing manner, the underlying nodes are responsible for data collection, and the high-level nodes perform necessary data fusion and forwarding. The level is formed by selecting a certain number of cluster heads from the common nodes, and selecting a certain number of cluster heads from the cluster heads as the higher level cluster heads. Cluster head C in the figure 0 , C 1 and C 2 is better than cluster head C 00 、C 10 、C 11 、C 20 、C 21 The higher-level cluster head expands the network level according to the requirements of the communication scale.
[0033] According to Fig. 2, the system of the present invention is divided into a network structure of three clusters. Analyze with cluster Cluster 1: the cluster includes a series of ordinary sensor nodes such as S 10 , S 11 , S 12 and cluster head node C 1 . All cluster members collect the data informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com