Method and system for maintaining the safe of data base
A database and security technology, applied in the database field, can solve the problem that data is difficult to maintain logical relationship, and achieve the effect of reducing the number of times and the amount of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The system and method for maintaining database security of the present invention will be described in detail below in conjunction with the accompanying drawings.
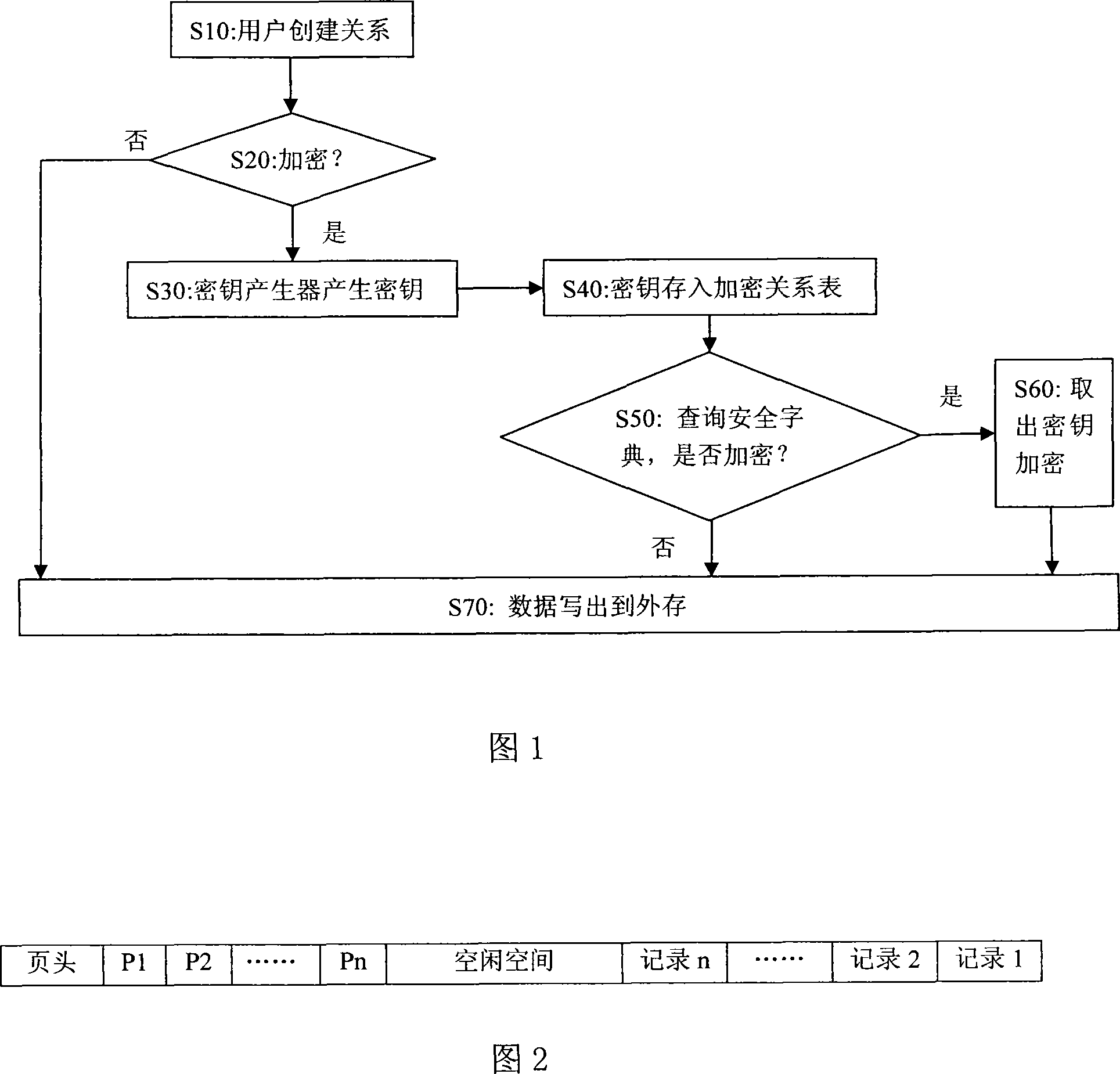
[0027] The method for maintaining database security of the present invention as shown in Figure 1, comprises the following steps:
[0028] Step S10: the user creates a relationship;
[0029] Step S20: Specify whether to encrypt and store the data in it through the extended statement of SQL, if it is necessary to encrypt and store, execute step S30; if it does not need to encrypt and store, execute step S70;
[0030] Step S30: the key generator automatically generates a key;
[0031] Step S40: storing the key in the encryption relationship table in the security dictionary;
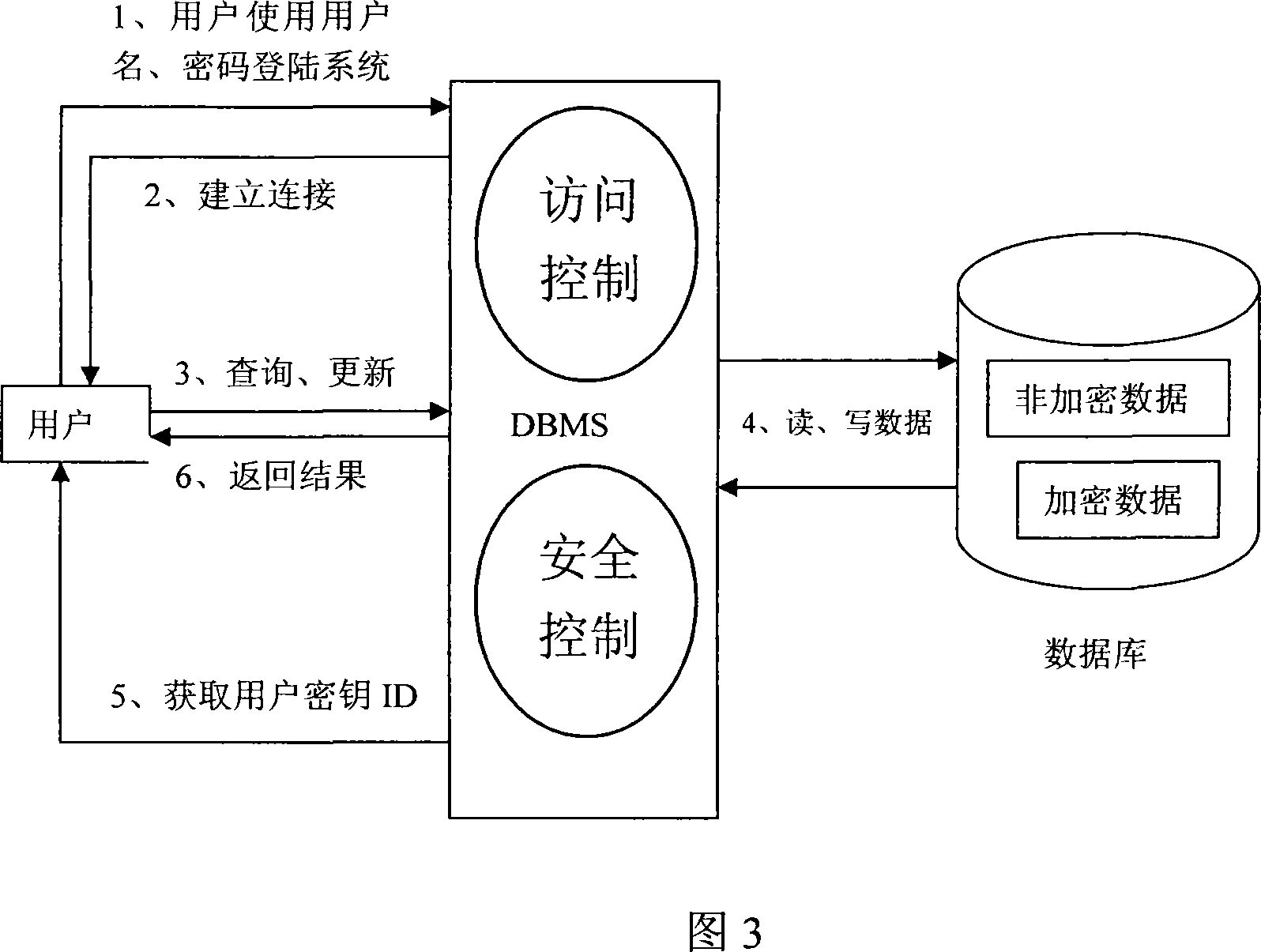
[0032] Step S50: When the DBMS writes the data to the external storage, query the security dictionary in the system table to determine whether encryption is required, if encryption is required, then enter step S60, if encryption is not r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com