Method of implementing inter-task sharing data
A technology for sharing data and tasks, applied in the field of computer systems, can solve problems such as complex coding, time-consuming, difficult to locate faults, etc., and achieve the effect of simplifying coding and avoiding deadlock problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
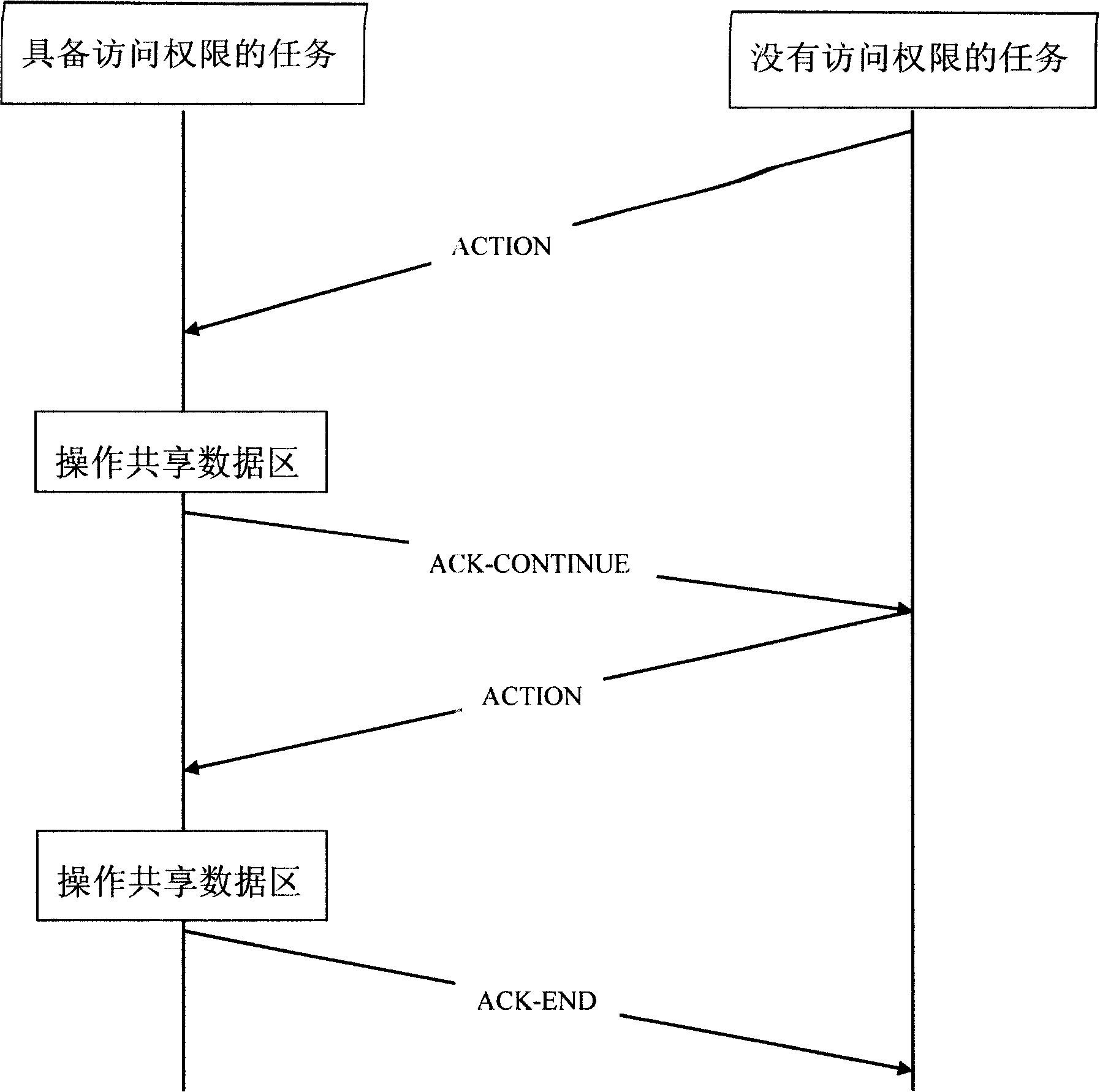
[0037] The method of sharing data between tasks should be free of protection. The key is to allow only one task to access the critical area, and other tasks are not allowed to access the critical area. For example, there are n tasks, and they share the data area D. Then it is stipulated that only one task can access the data area D, and other tasks cannot directly access the data area D, and can only send messages to tasks with access rights. The message specifies the access action, which can be a function name or other numbers that can indicate the action. . After receiving the message, the tasks with access rights execute actions and operate the shared data. After running, send a response message to the initiator of the action. The task that initiates the action determines the follow-up operation according to the response message.
[0038] The message exchange process is as figure 1 As shown, the following is an example of this method to share data between two tasks.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com