Teaching and testing device for network information security
A technology of network information and experimental equipment, which is applied in the field of network information security teaching experiment equipment, can solve problems such as difficulty in learning for students, lack of teaching experiment system, and lack of network information security teaching facilities, so as to achieve increased security and comprehensive content of network information security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
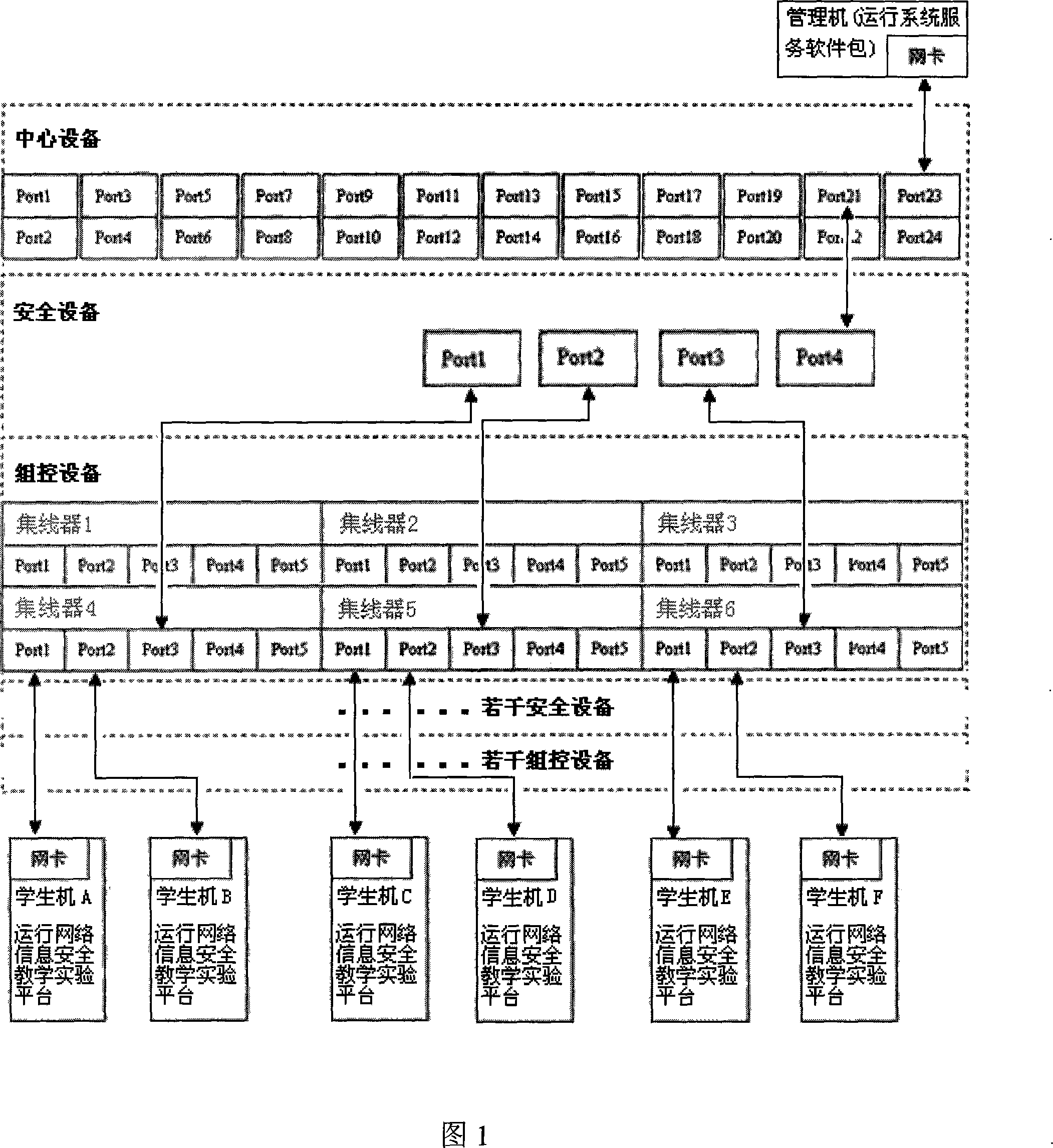
[0021] hardware system
[0022] The group control device consists of six 5-port / 100M hubs. The central equipment is a 24-port / 100M switch, and the security equipment is composed of public control PC and Endian Firewall release2 Linux open source operating system. Among them, the public control PC adopts Taiwan SYS-7464VEA motherboard, built-in 1 Intel Mobile PIII 650MHz CPU, 4 onboard 10Base / 100Base TX network cards and 2 USB2.0 interfaces, and the public control PC adopts 256M DDR333 notebook memory and 80G easy extension hard drive,
[0023] The network information security teaching experiment system takes 6 people as an experimental group, and allocates a security device and 3 hubs, and a group control device can support up to two experimental groups.
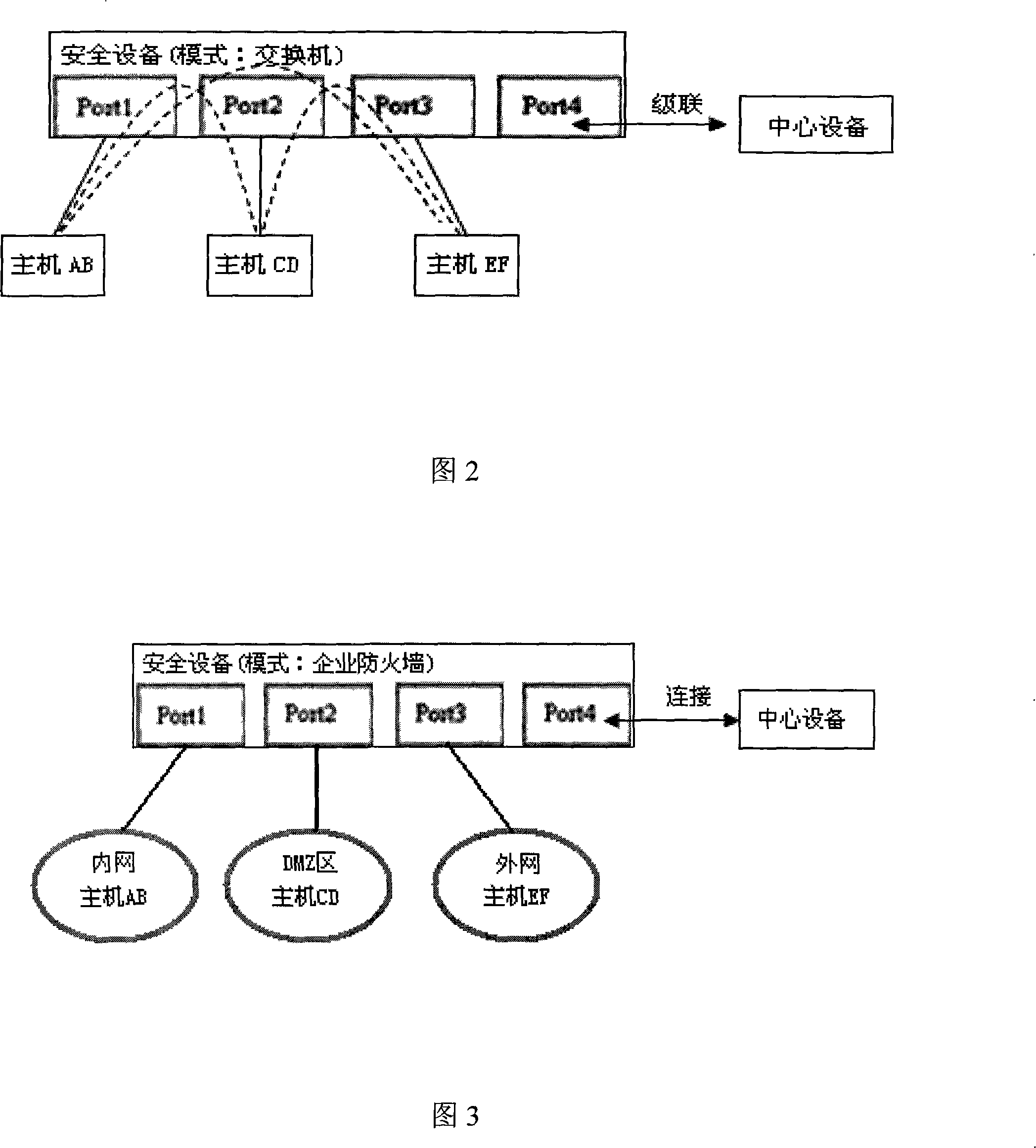
[0024] As shown in Figure 1: The hardware connection method of the experimental device is an example of connecting one group control device, one security device (one experimental group) and the central device. The role nam...
Embodiment 2
[0038] The working principle of the device will be further explained with an experiment of learning an asymmetric encryption algorithm (RSA encryption algorithm).
[0039] Before carrying out the experiment, you can learn the preparatory knowledge through the experimental teaching materials or related topics provided by the experimental platform. The experiment requires two experimental hosts (experimental roles are defined as host A and host B) to work together under the same shared module. Both hosts A and B start the network information security experiment platform in the Windows virtual machine, open the network information security toolbox, and enter the [RSA encryption algorithm] interface from the tool wizard; host A generates public and private keys in the public key tab ( You can observe the RSA public and private key generation and encryption and decryption process in the demonstration area), use the generated private key to perform RSA encryption on a piece of plain...
Embodiment 3
[0041] Assuming that two remote hosts want to carry out safe and reliable information transmission in the network, they transmit files in the network through the combination of symmetric key encryption and asymmetric key encryption.
[0042] Take host A sending and host B receiving as an example to illustrate the implementation:
[0043] Host A generates an RSA public-private key pair, and informs host B of the public key, and keeps the private key by itself; similarly, host B generates an RSA public key pair, informs host A of the public key, and keeps the private key by itself; host A enters the network information On the security experiment platform, open the toolbox and select the "encryption and decryption" tool. Use the public key tab in the RSA encryption algorithm to generate a public-private key pair, and then send the public key to host B in the form of an email, and keep the private key by yourself; host A uses the encryption tab in the DES encryption algorithm to g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com