Detection method and system for SQL injection loophole
A vulnerability detection and vulnerability technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as false positives, inaccurate methods, and false negatives, and achieve the effect of avoiding inaccuracy and improving efficiency and accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
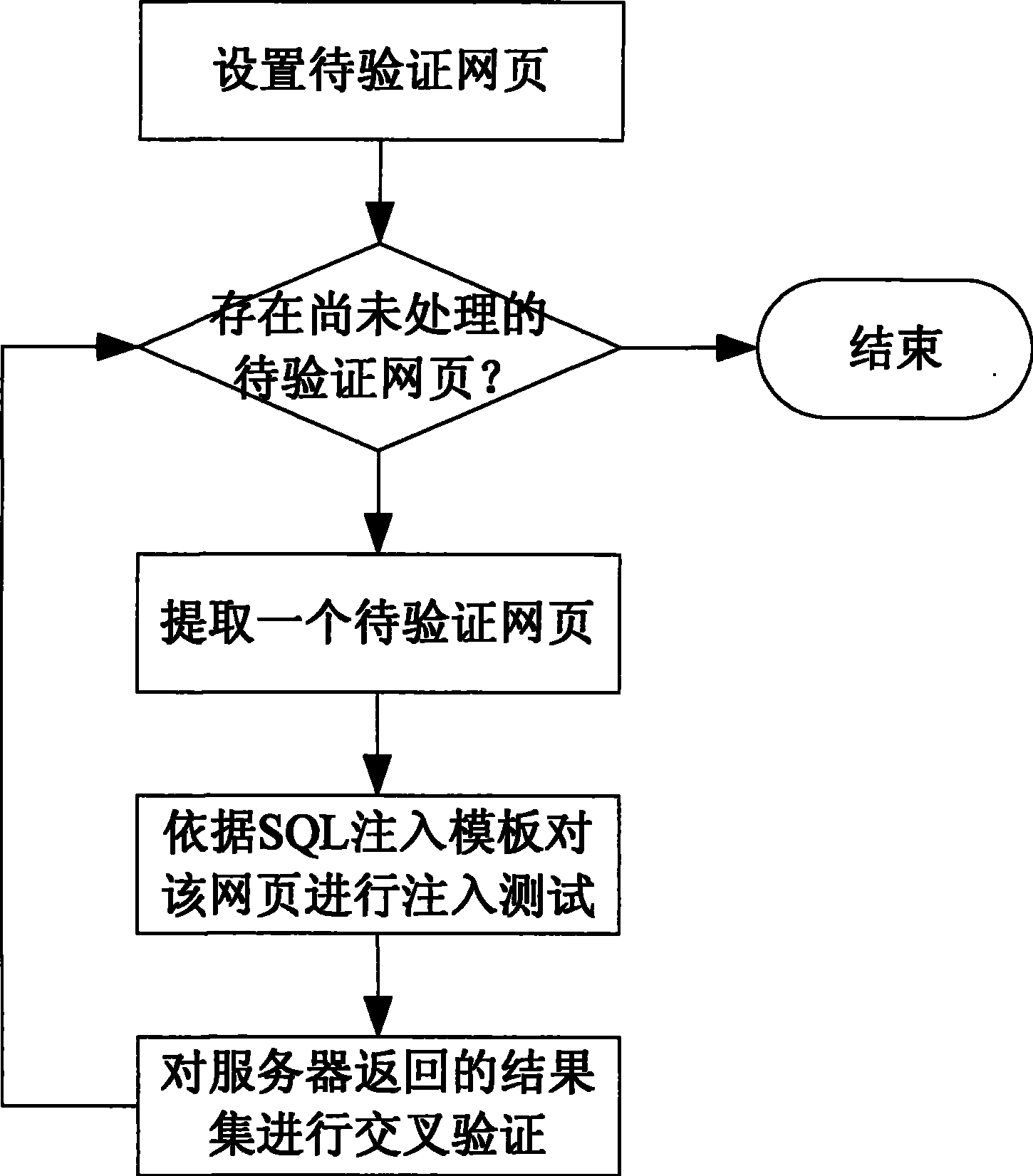
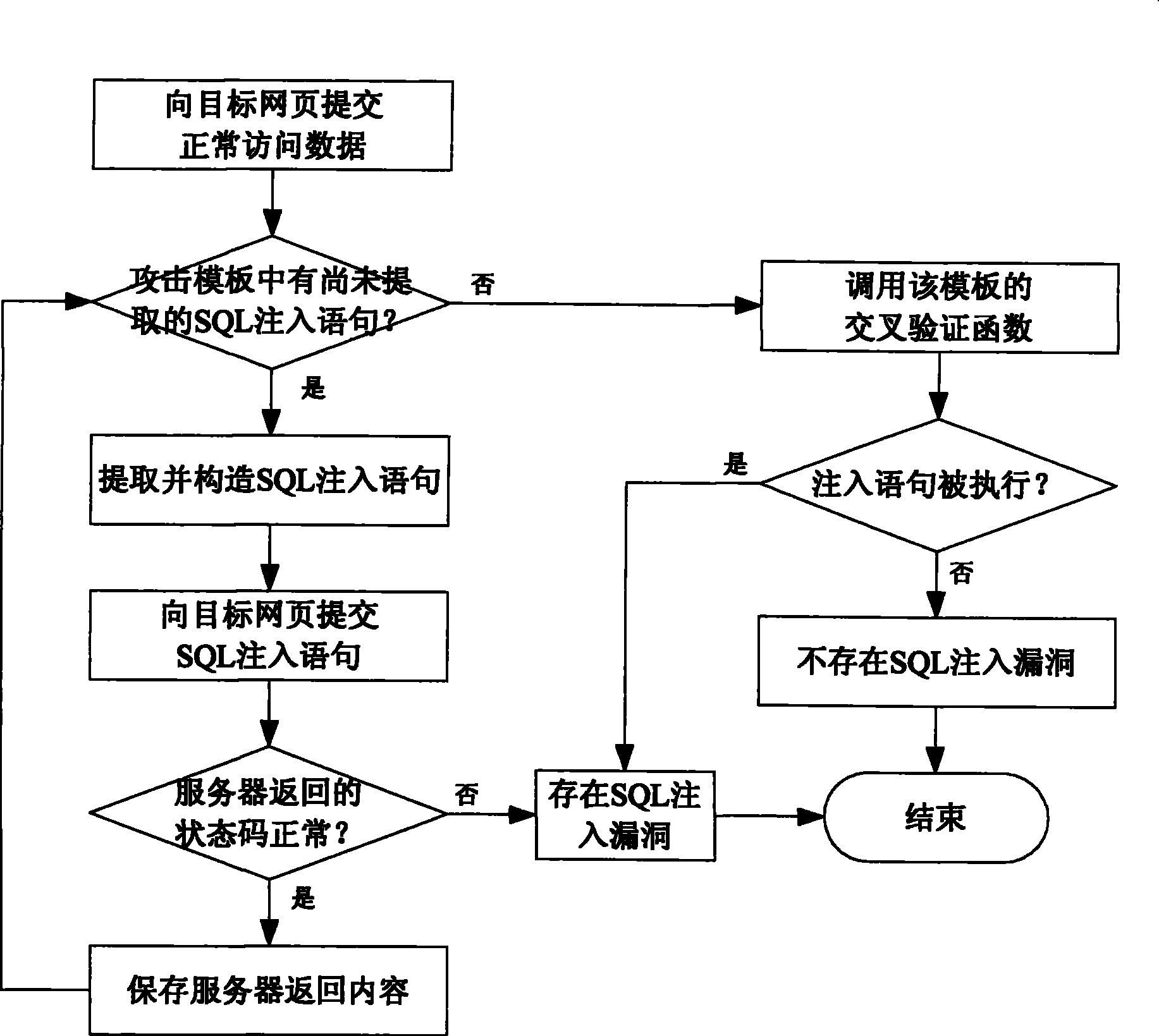
[0029] This embodiment is a specific implementation of the SQL injection vulnerability detection method, and the main operation process is as figure 1 Shown. The basic idea of this embodiment is that it provides a series of SQL injection attack templates, where each template is composed of several SQL injection statements that may cause the server to return different results, and the cross-validation function corresponding to the template. For each web page to be scanned on the server, the SQL injection vulnerability detection system will send normal SQL access requests and specific SQL injection statements to the web page according to the selected template, and receive the results returned by the server. Since each access request is constructed in advance, if these access requests can be executed on the server, different results will be returned. The cross-validation function compares these returned results with each other to determine whether the submitted SQL injection sta...
Embodiment 2
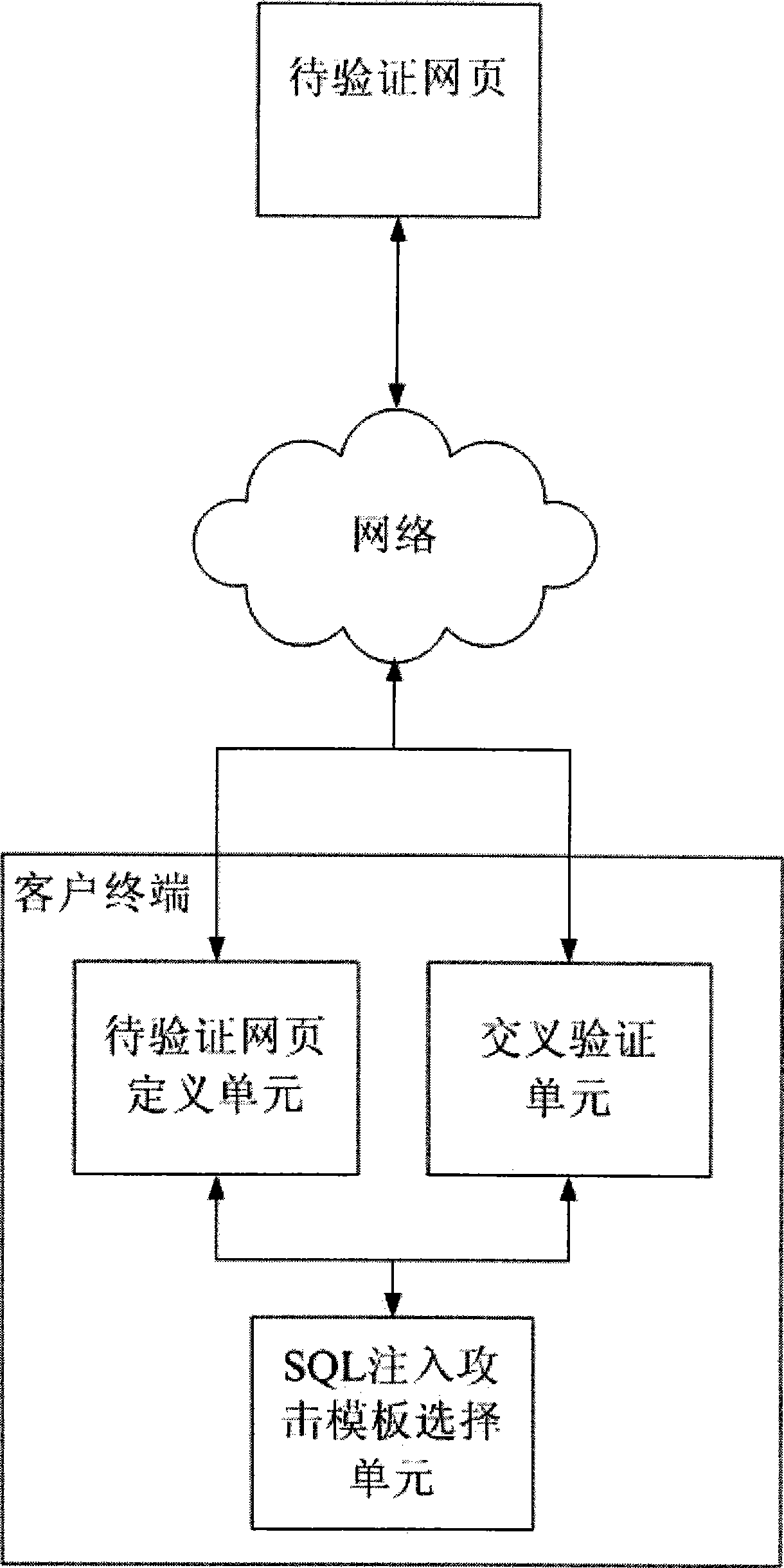
[0061] This embodiment is a system that implements the method described in the embodiment. For a schematic diagram of the system structure, see figure 1 Shown. That is, a SQL injection vulnerability detection system. The system is installed on a user terminal on the Internet and has at least one web page definition unit to be verified connected to a web server. At least one is connected to the definition unit of the web page to be verified, which can provide four SQL injection attack template selection units of the attack template subunits. There is at least one cross-validation unit that gets support from the SQL injection attack template selection unit and connects to the web server. The system includes:
[0062] 1. Web page definition unit to be verified: Define a series of web page addresses that may contain SQL injection vulnerabilities.
[0063] 2. SQL injection attack template selection unit: List available SQL injection attack templates for users to choose.
[0064] 3. Cro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com