Dynamic password identity authentication method based on accidental character set
A dynamic password and identity authentication technology, applied in the field of identity authentication, can solve the problems affecting the general use of dynamic password technology, the inconvenience of tokens, and the inconvenience of token carrying, so as to reduce the probability of password leakage, easy to remember, Wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
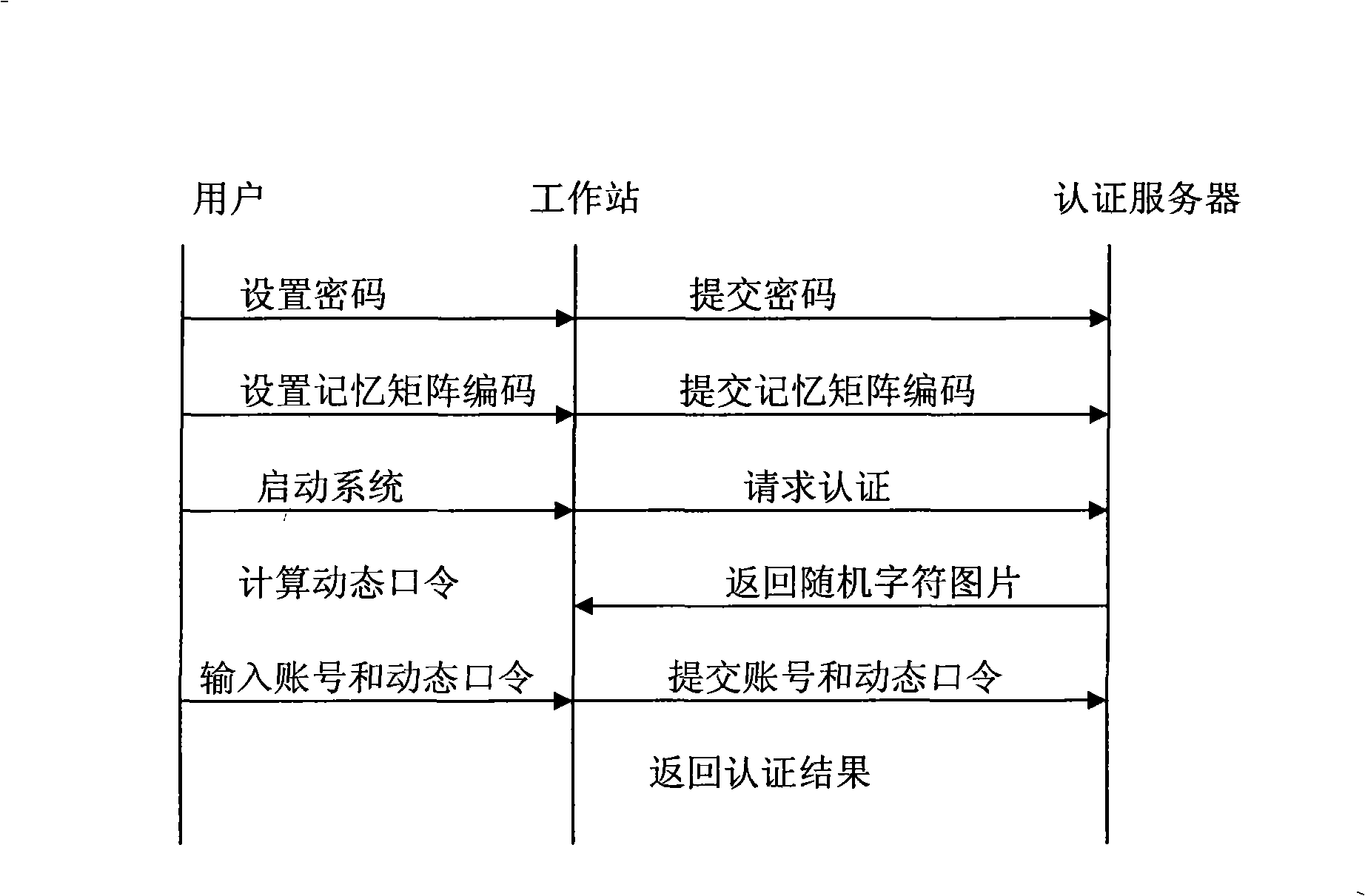
[0035]Embodiment 1: In this embodiment, the password characters in step (1) are composed of 10 Arabic numerals 0-9 and 26 English letters a-z, wherein K=36. In step (2), both the memory matrix and the generation matrix in step (3) are 3×3 square matrices, 36 characters are evenly distributed in the squares in the generation matrix, and all characters do not appear repeatedly. All the characters in the memory matrix form the character set H, and the character set H consists of 10 Arabic numerals 0-9 and 26 English letters a-z. The specific steps are:
[0036] (1) Set user password: abc123
[0037] (2) Set memory matrix encoding, see table 1 below:
[0038] Table 1
[0039] 5
4
3
6
1
2
7
8
9
[0040] (3) Request authentication: when the user logs in, the computer or server randomly generates a generation matrix corresponding to the memory matrix displayed in the form of a picture, see Table 2:
[0041] ...
Embodiment 2
[0045] Embodiment 2: In this embodiment, the password characters in step (1) are composed of 10 Arabic numerals 0-9 and 26 English letters a-z, wherein K=36. In step (2), both the memory matrix and the generation matrix in step (3) are 3×4 square matrices, and 36 characters are evenly distributed in the squares in the generation matrix, and all characters do not appear repeatedly. All the characters in the memory matrix form the character set H, and the character set H consists of 10 Arabic numerals 0-9 and 26 English letters a-z. The specific steps are:
[0046] (1) Set user password: set password: def233d4
[0047] (2) Set memory matrix encoding, see table 3 below:
[0048] table 3
[0049]
l
k
j
i
h
g
f
e
d
c
b
a
[0050] (3) Request authentication: when the user logs in, the computer or server randomly generates a generation matrix corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com