Method for implementing IP credible route based on fault-tolerance and invasion-tolerance
An implementation method and technology of trusted paths, applied in the field of communication, can solve problems such as no definition of judgment modules, insufficient sharing of node trust information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] The present invention will be further described below in conjunction with the accompanying drawings and examples.
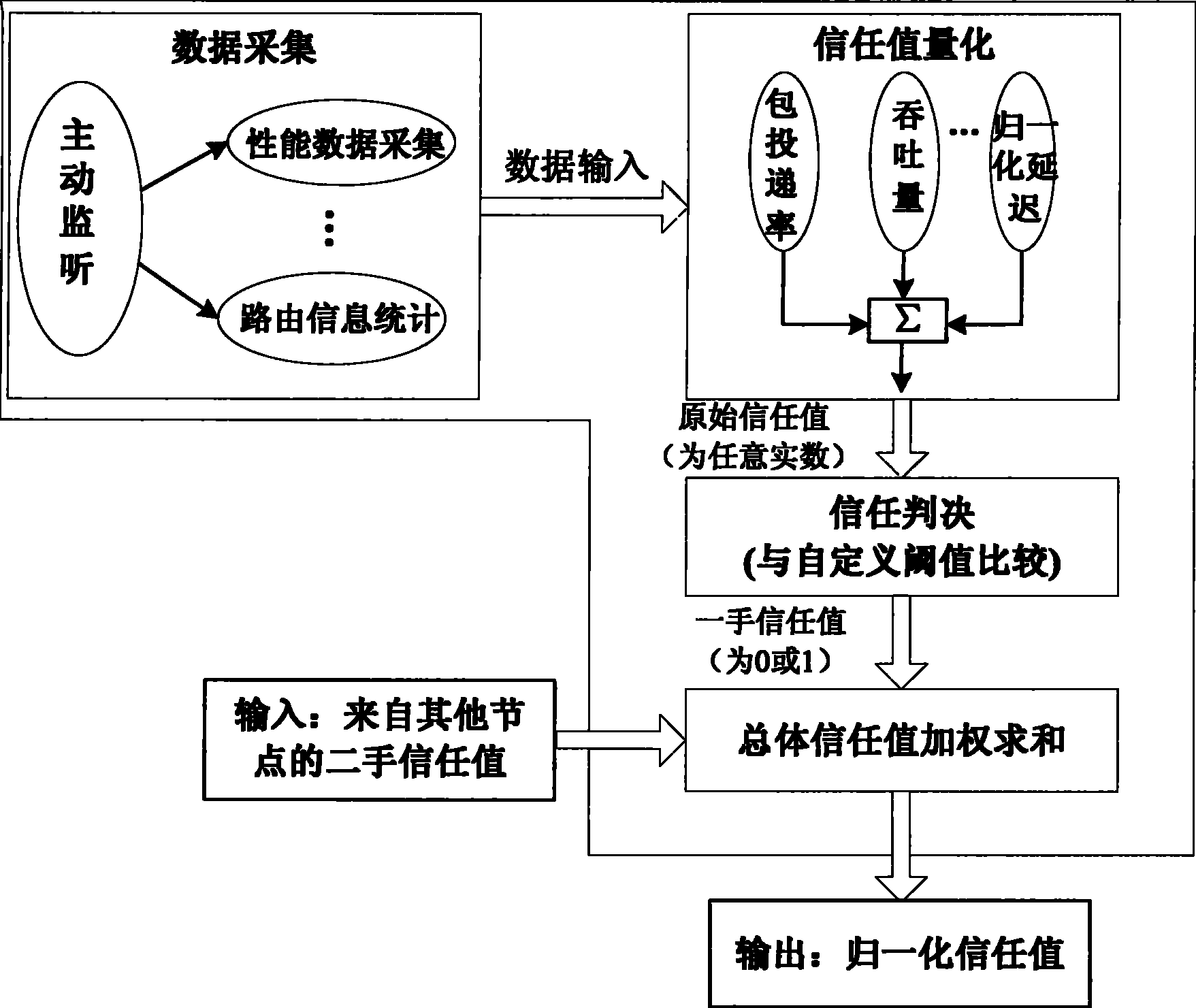
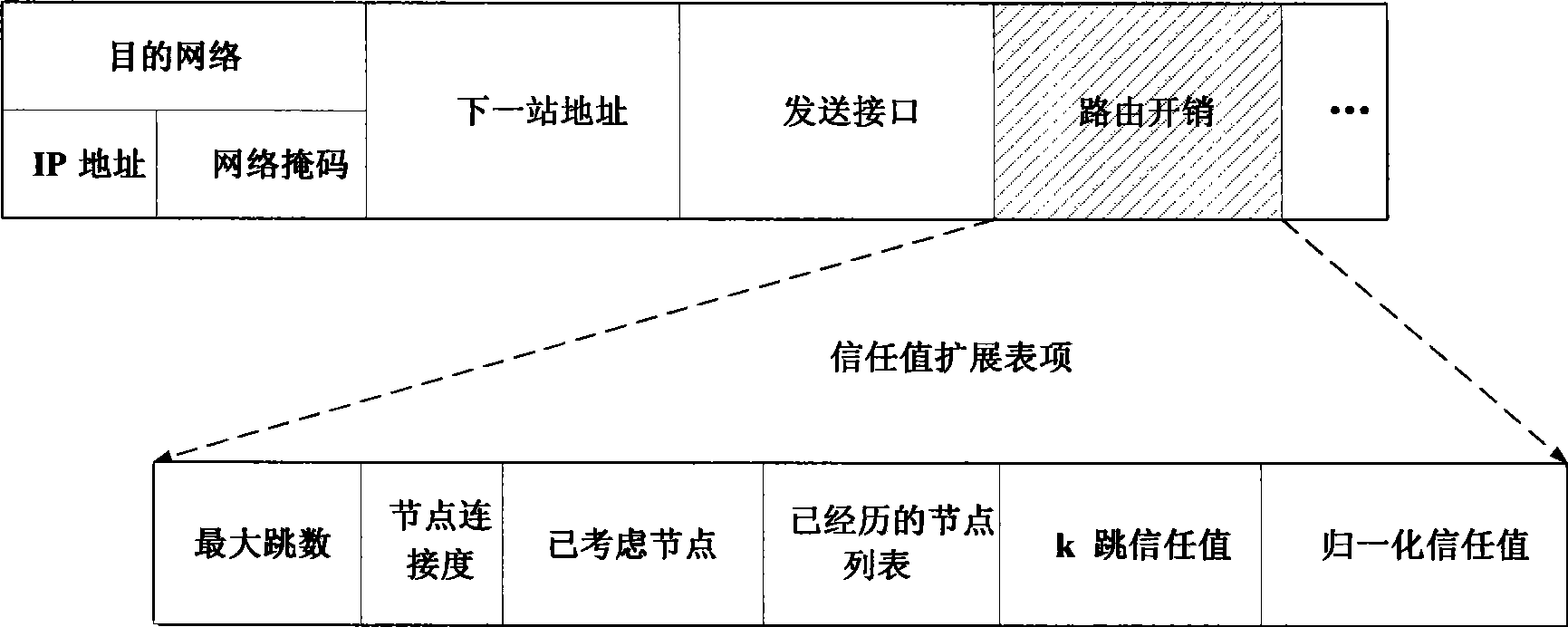
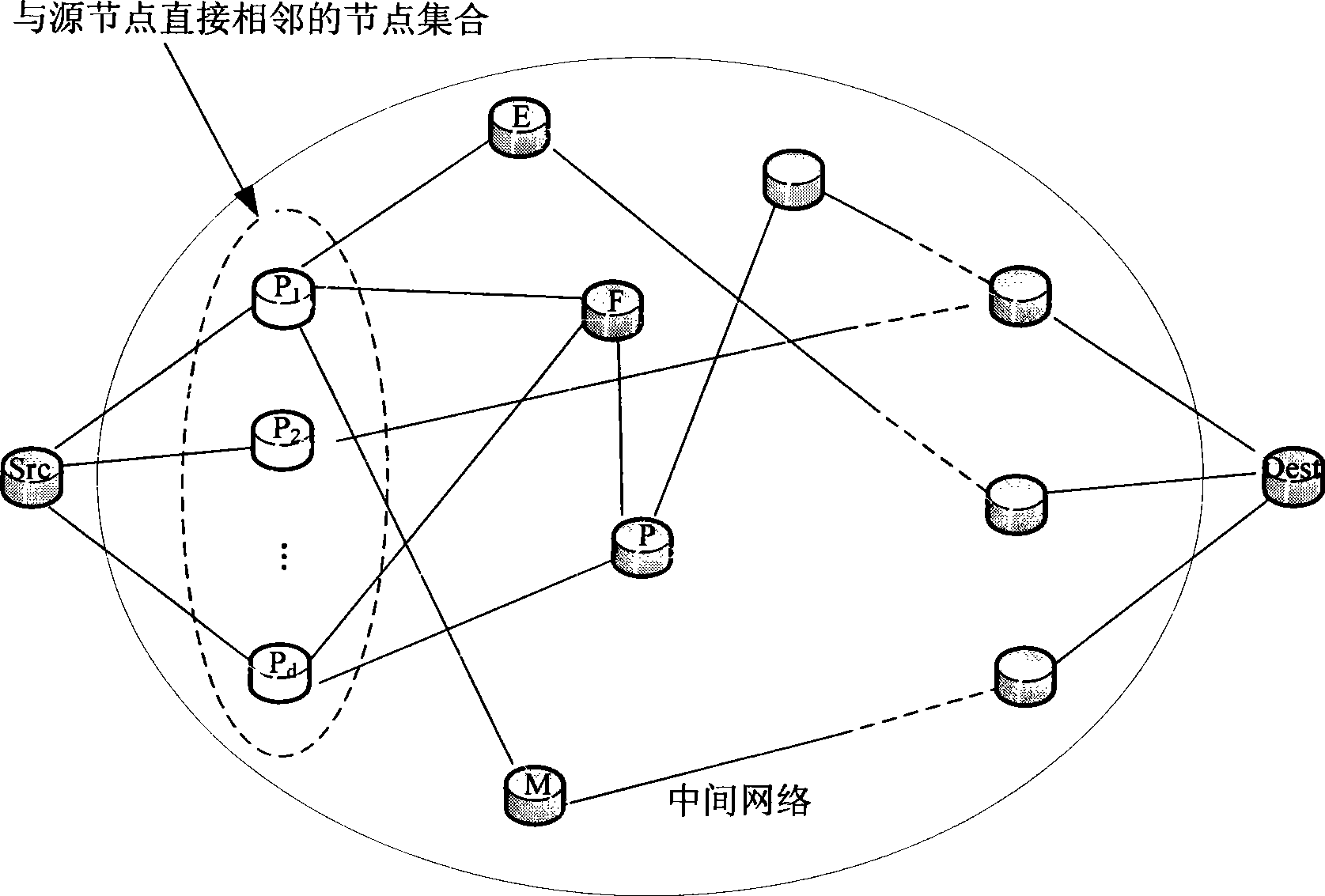
[0076] Aiming at the defects of RFSN design in the implementation of trusted routing, the present invention proposes a corresponding improvement scheme: a method for implementing IP trusted routing based on fault tolerance and intrusion, that is, a secure routing based on trust relationship Strategy. figure 1 The schematic diagram of network node trust monitoring and acquisition functions shown is the core mechanism of the present invention to acquire trust values. The trusted routing implementation method proposed in the invention is applicable to the IP network environment in a general sense, and can detect abnormal network behaviors such as: bad-mouth attacks, conflicting behavior attacks, on-off Attacks and node failures are fault-tolerant and intrusion-tolerant.
[0077] The core design idea of the technical solution of the present invention is as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com