Method for encrypting telephone number
A number and calling number technology, applied in the field of phone number confidentiality, can solve the problem that the called party cannot initiate a call contact, and the original caller cannot contact the original caller.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
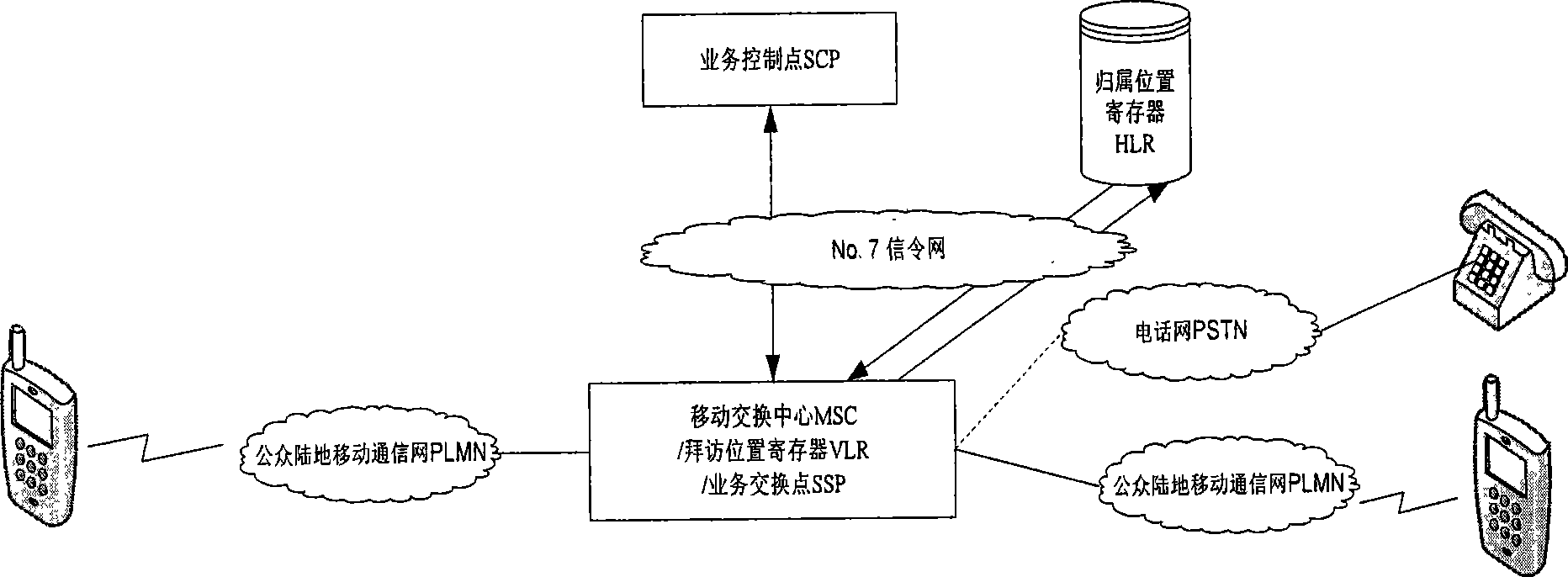
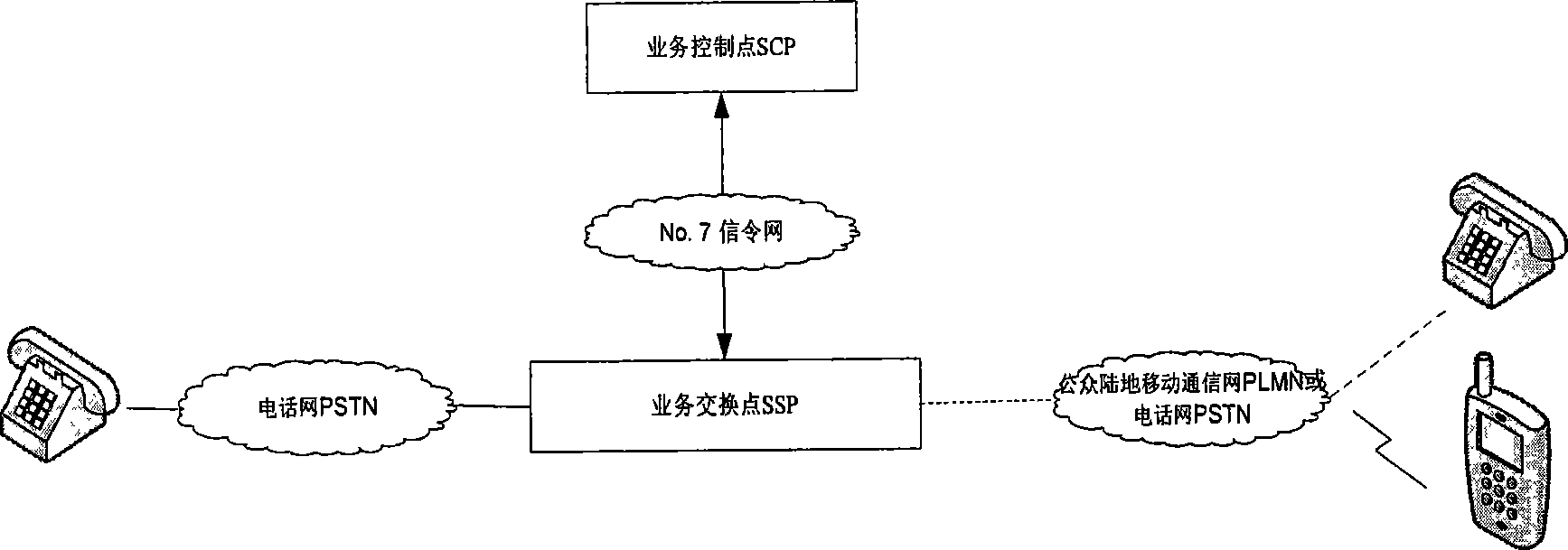
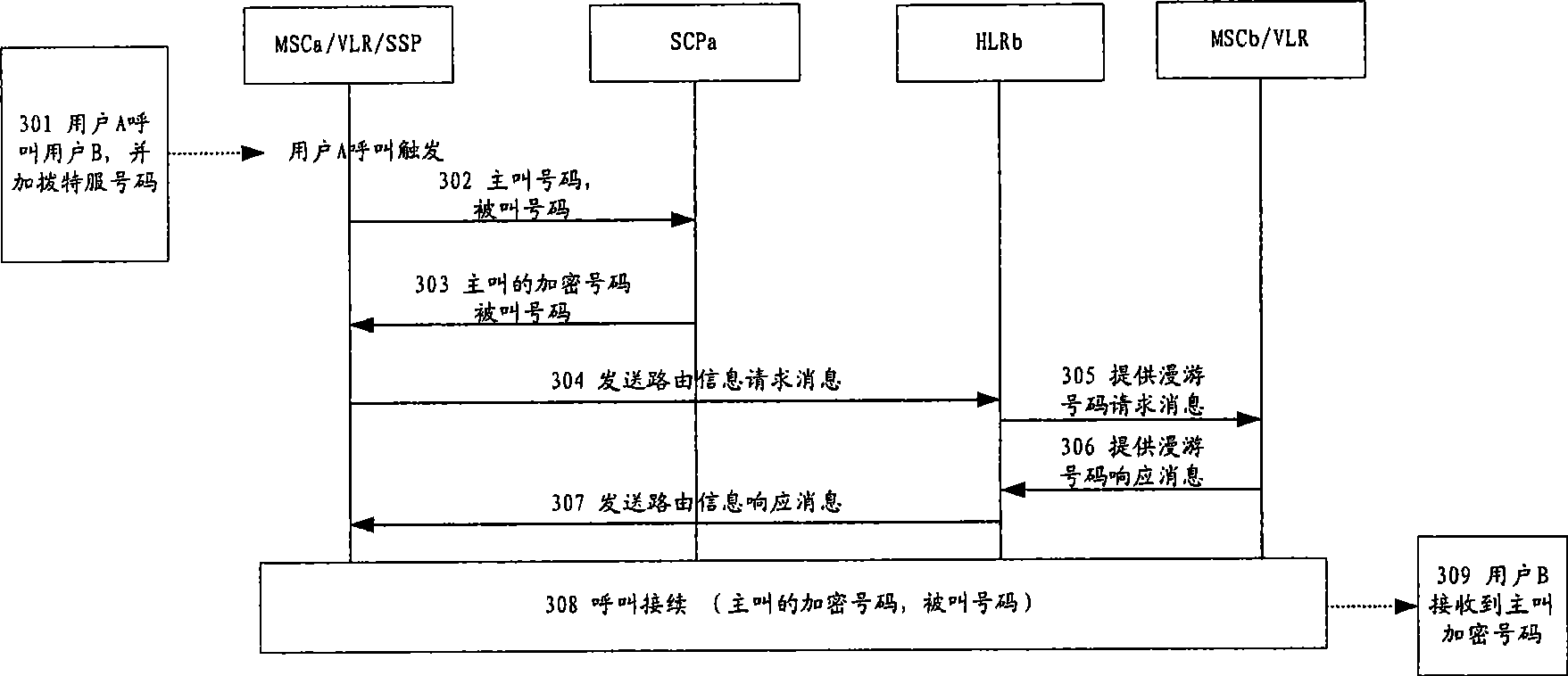
[0024] Below at first provide a system structural representation of the present invention, as figure 1 shown. In this illustration, the calling party is a mobile phone user. The service control point plays a role in controlling and processing intelligent services in the whole network, and mainly completes the telephone number encryption / decryption function in the present invention; the mobile switching center / service switching point mainly completes the service switching function and the call control function; the home location register HLR is mainly used to save the basic information of the mobile phone. The Visited Location Register (VLR: Visited Location Register) mainly stores the relevant information of registered mobile users entering its control area. In this schematic diagram, it is assumed that each mobile switching center has the function of SSP, and also has a built-in visitor location register (VLR). Among them, the service control point and the service exchange...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com