Service access authentication method and system
A server and authentication key technology, applied in the field of service access authentication methods and systems, can solve the problems of spending user time, increasing server access delay, expensive users, operators and other service providers, and achieving reduced delay, simplified effect of the way
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
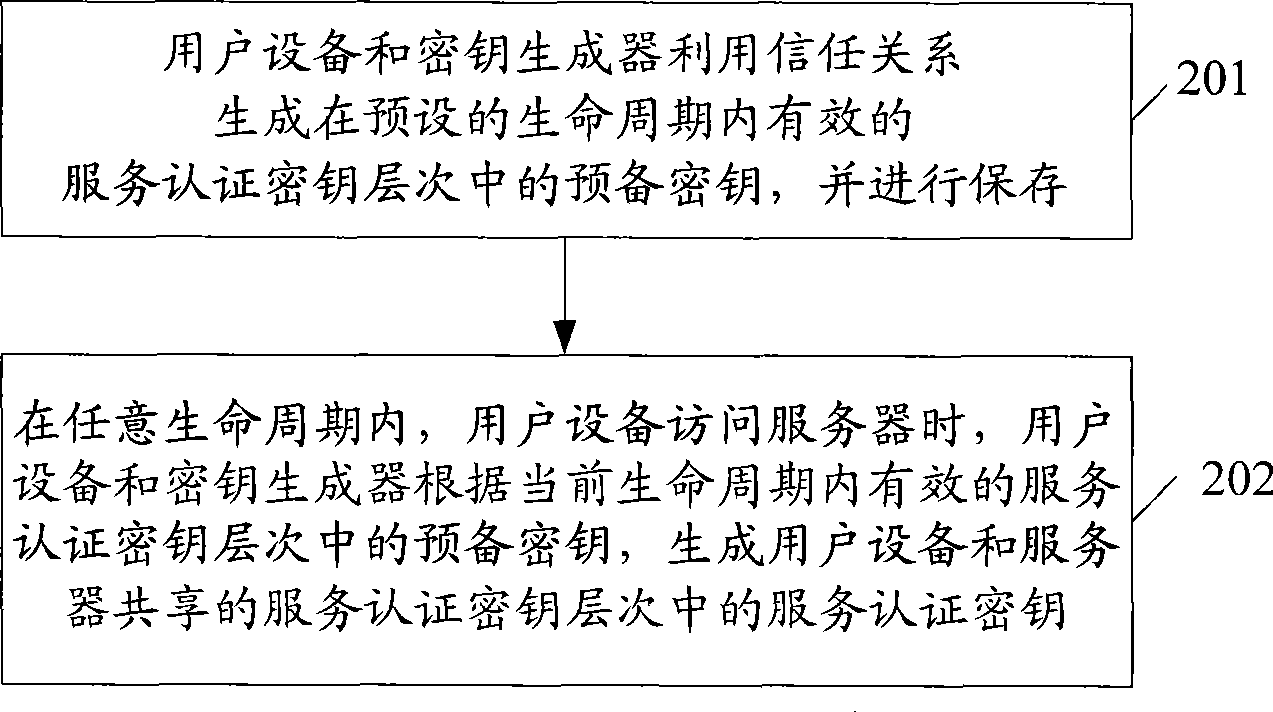
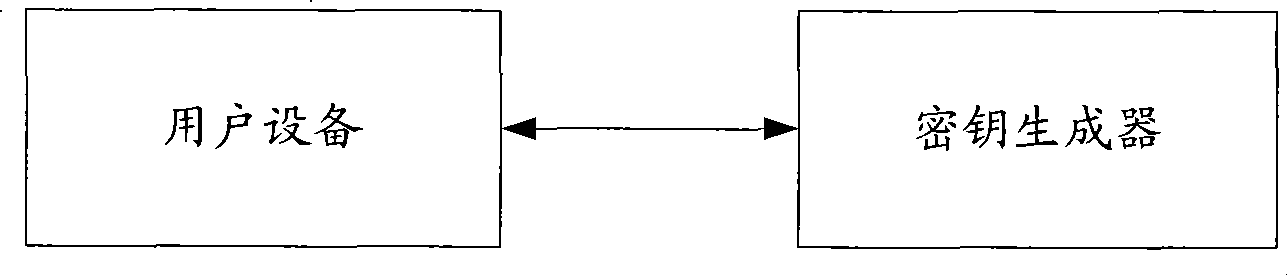
[0071] In this embodiment, an implementation manner of generating a preliminary key during an access authentication process to generate a service authentication key is described in detail. Moreover, in this embodiment, the network model of the Internet network is taken as an example for description.
[0072] EAP is an authentication framework that provides an end-to-end authentication mechanism and supports multiple authentication methods, such as: Extended Authentication Protocol-Message-Digest Algorithm 5 (EAP-MD5), Extended Authentication Protocol-Transport Layer Security (EAP-TLS), Extensible Authentication Protocol-Subscriber Identity Module (EAP-SIM), Extended Authentication Protocol-Tunneled Transport Layer Security (EAP-TTLS) and Extended Authentication Protocol-Authentication and Key Agreement (EAP-AKA), etc., and have good scalability. EAP can run directly on the data link layer, such as Point-to-Point Protocol (PPP) and the Institute of Electrical and Electronics En...
Embodiment 2
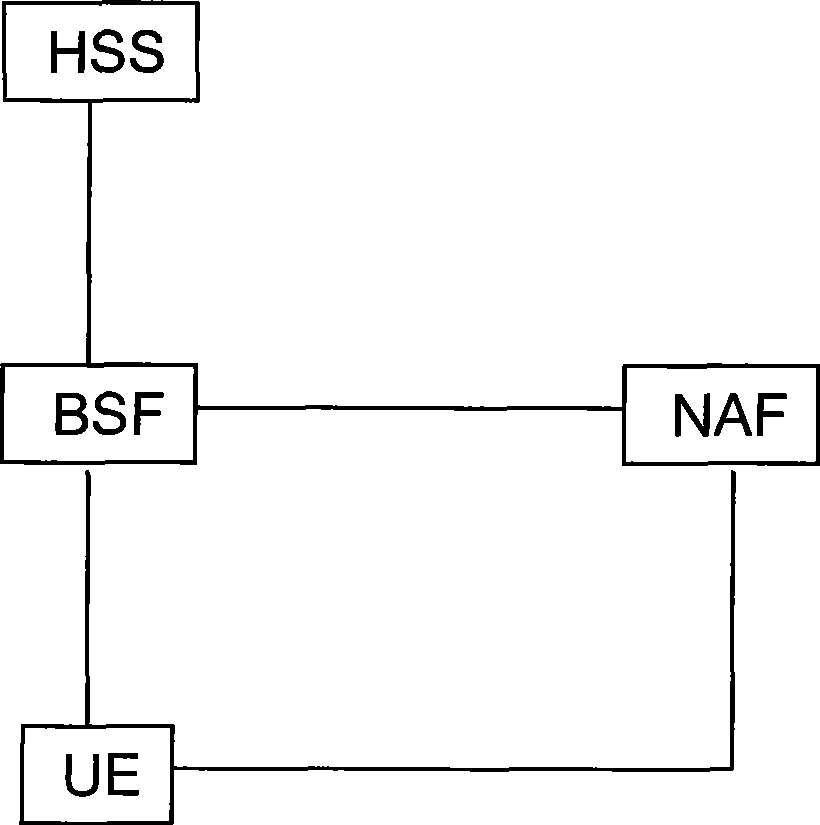
[0126] At present, the cellular mobile communication network is providing services for more than 1 billion users worldwide. The communication network refers to the second-generation mobile communication network and the third-generation network. One of the main advantages of the cellular mobile communication network lies in its wide coverage and vast user group. In the cellular mobile communication system, the authentication mechanisms adopted are SIM card authentication and AKA authentication methods. The following uses the network model of the Universal Mobile Telecommunications System (UMTS) as an example to illustrate specific implementations of the method, system and device for generating a service authentication key in the embodiments of the present invention.
[0127]In this embodiment, the process of generating a service authentication key and using the key for service authentication is divided into two processes: a bootstrap process and a service access authentication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com