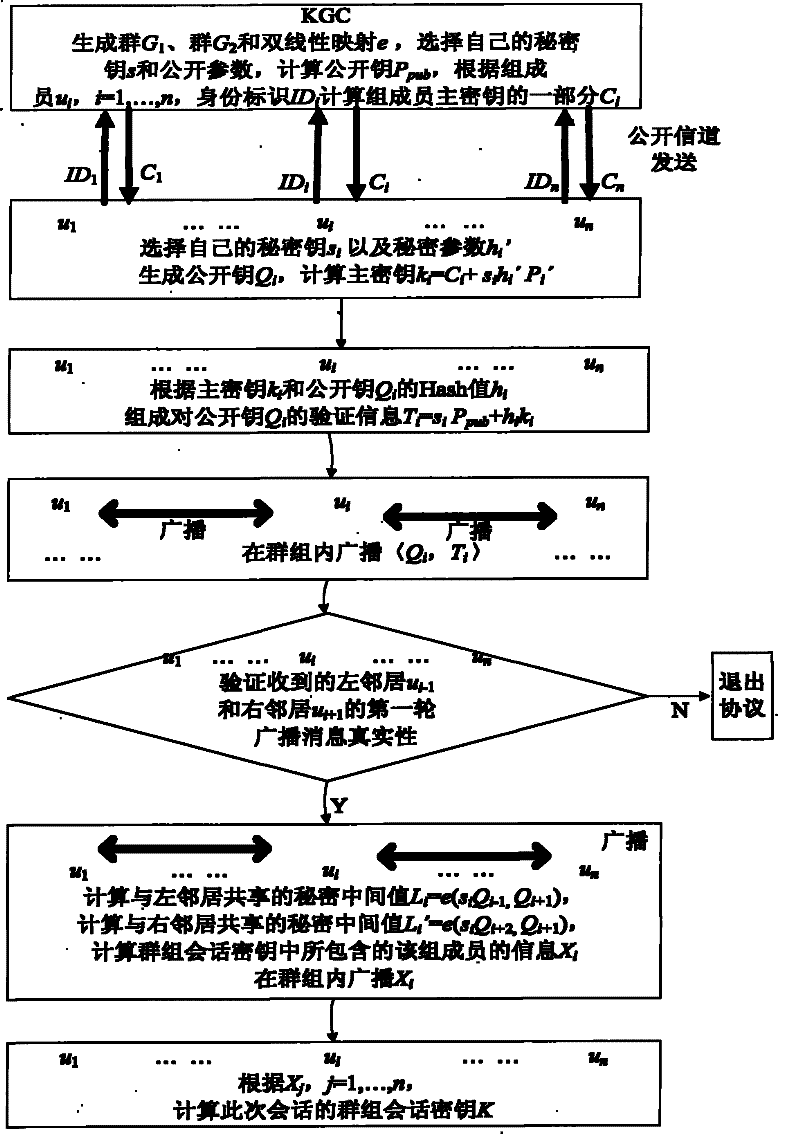
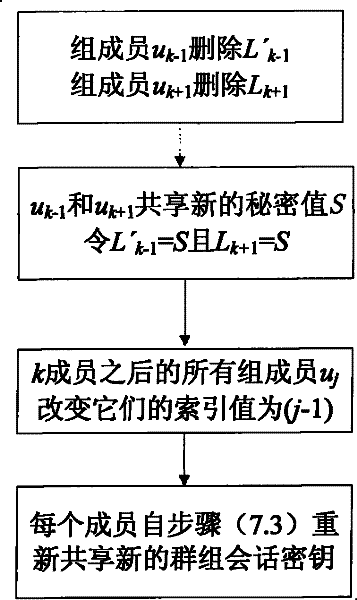
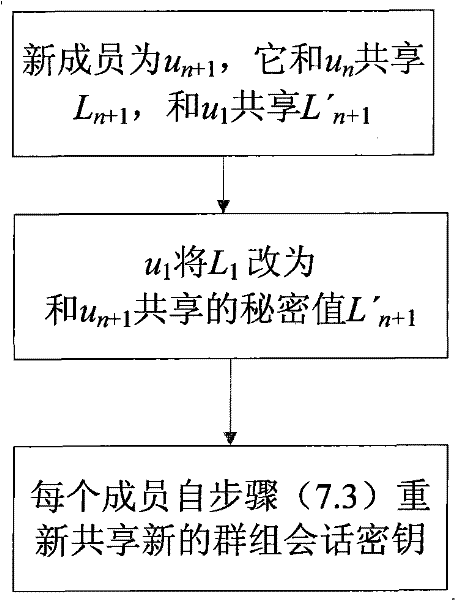
Authentication group key management method based on identity
A technology of group key and management method, applied in the field of identity-based authentication group key sharing and management, can solve the problems of heavy network communication burden and poor calculation effectiveness, and achieve the effect of improving communication and calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] One, the mathematical theory used in the present invention and technical term description:
[0026] 1. Hash function
[0027] The Hash function is a function that changes an input message of arbitrary length into an output message of fixed length, and this output is called the Hash value of the message. A secure Hash function should at least meet the following conditions: ①The input length is arbitrary; ②The output length is fixed, generally at least 128 bits long, in order to resist birthday attacks; ③For each given input, it can be easily ④ Given the description of the Hash function, it is computationally infeasible to find two different input messages Hash to the same value, or given the description of the Hash function and a randomly selected message, It is computationally infeasible to find another message that is different from this message such that they hash to the same value. The Hash function is mainly used for integrity verification and improving the validi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com