USBKey safe protection method
A security protection device, USB interface technology, applied in computer security devices, instruments, user identity/authority verification, etc., can solve the problems of stealing customer accounts, customer losses, etc., to prevent security risks, reduce product costs, and improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
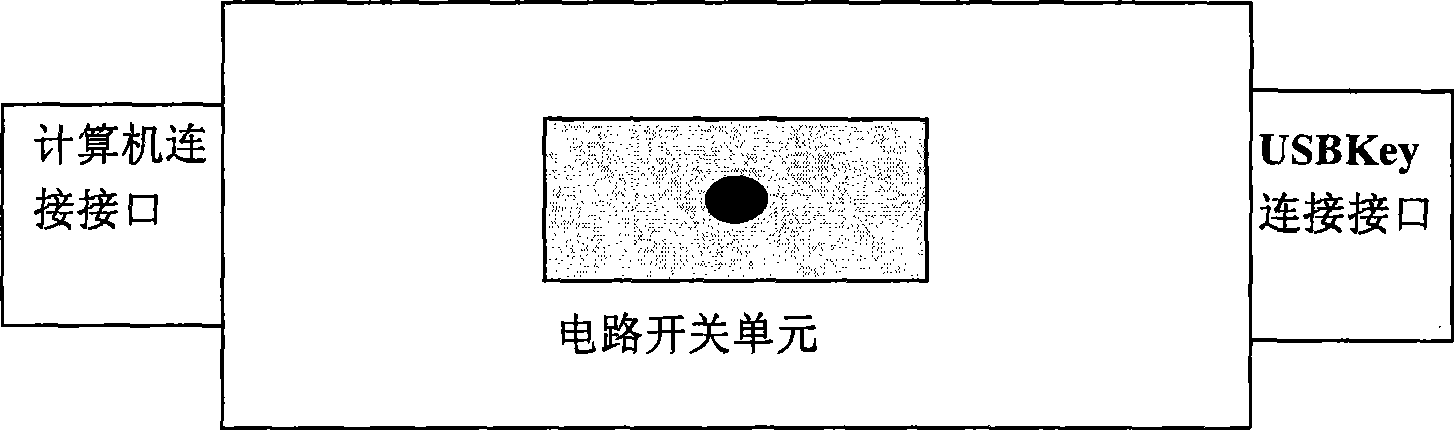
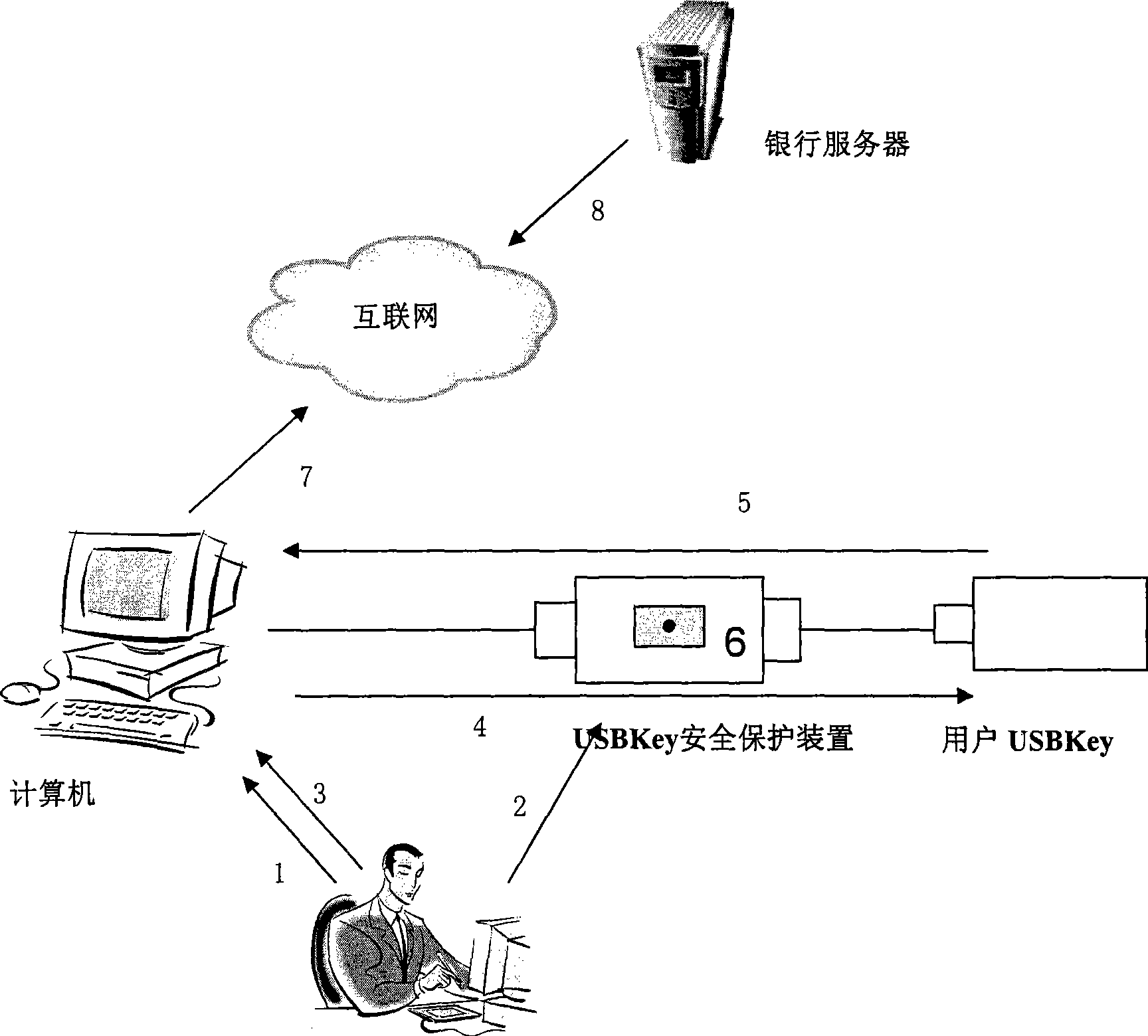
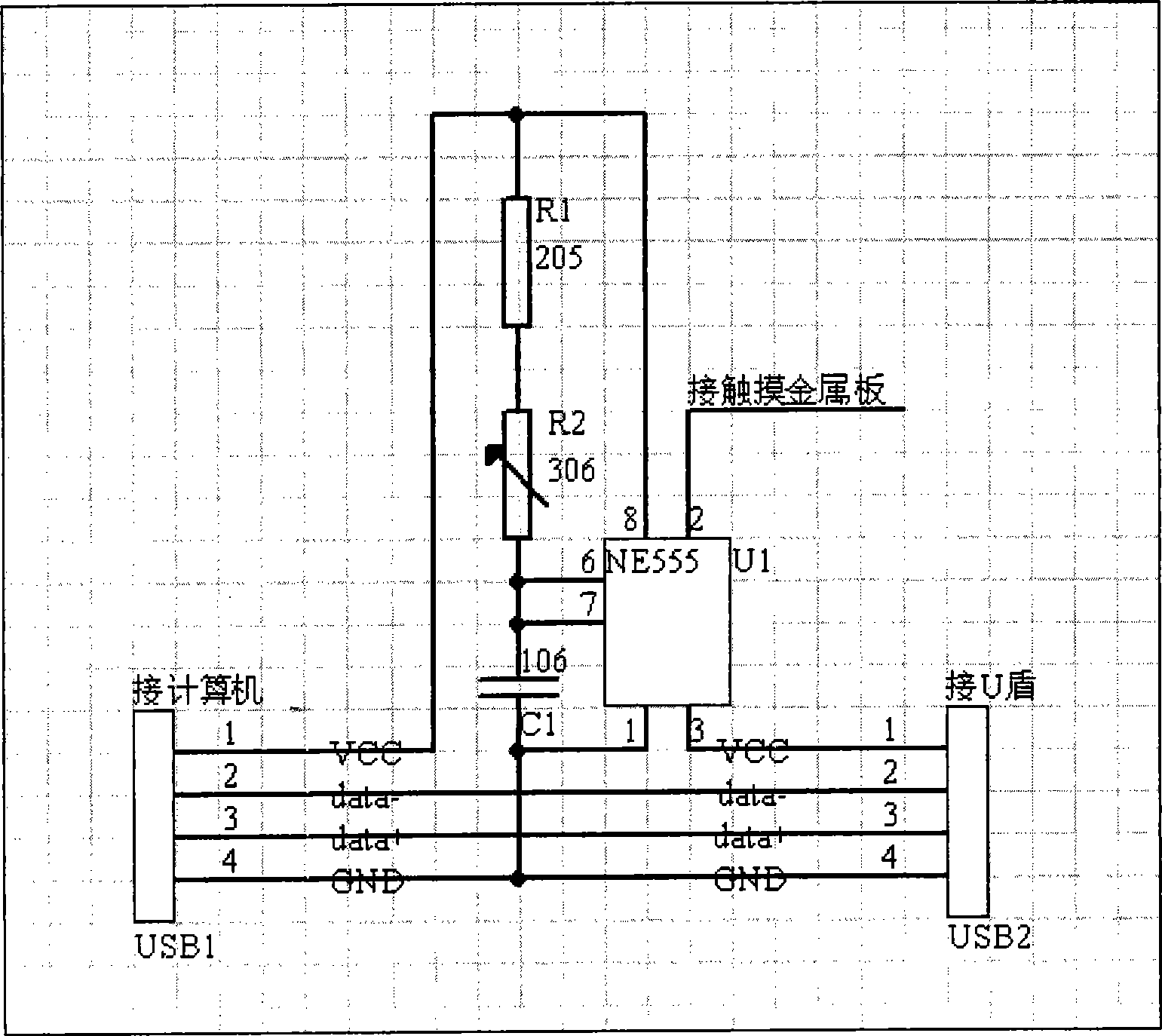
[0026] The present invention adds a physical protection button locally to the user who uses the USBKey for identity authentication and signature. When the user uses the USBKey to operate, the USBKey must be confirmed by using the local physical button before the USBKey can be used normally, thereby effectively preventing the user’s USBKey from being damaged. The problem of remote hijacking by hackers.
[0027] Such as figure 1 as shown, figure 1 It is a structural schematic diagram of a USBKey safety protection device provided by the present invention, and the USBKey safety protection device includes a computer connection interface, a USBKey connection interface and a circuit switch unit. Wherein, the computer connectio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com