Sql sentence audit method and system for oracle database binding variable
A technology for binding variables and databases, which is applied in the field of SQL statement auditing to achieve high extraction efficiency, simple implementation and good performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
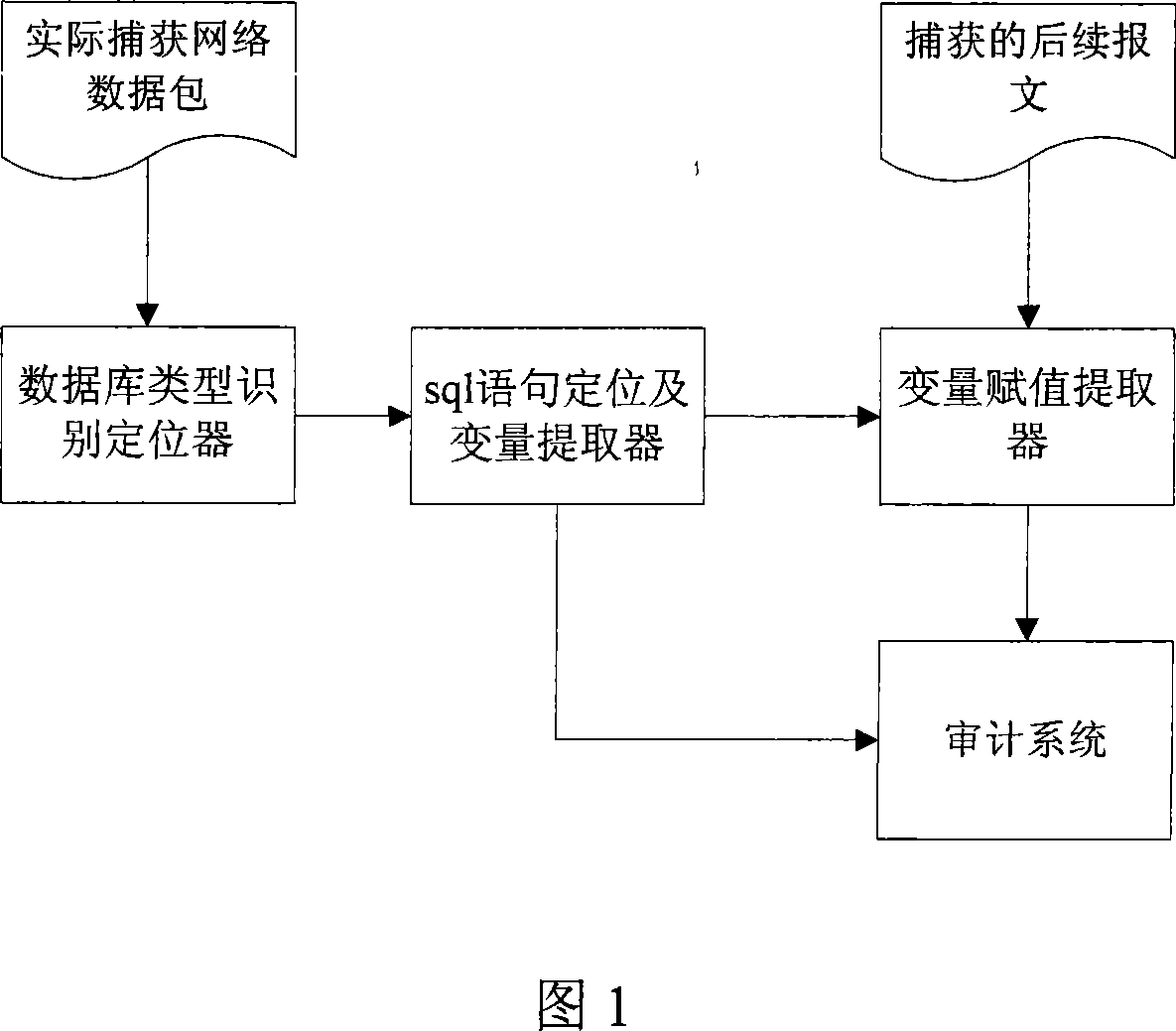
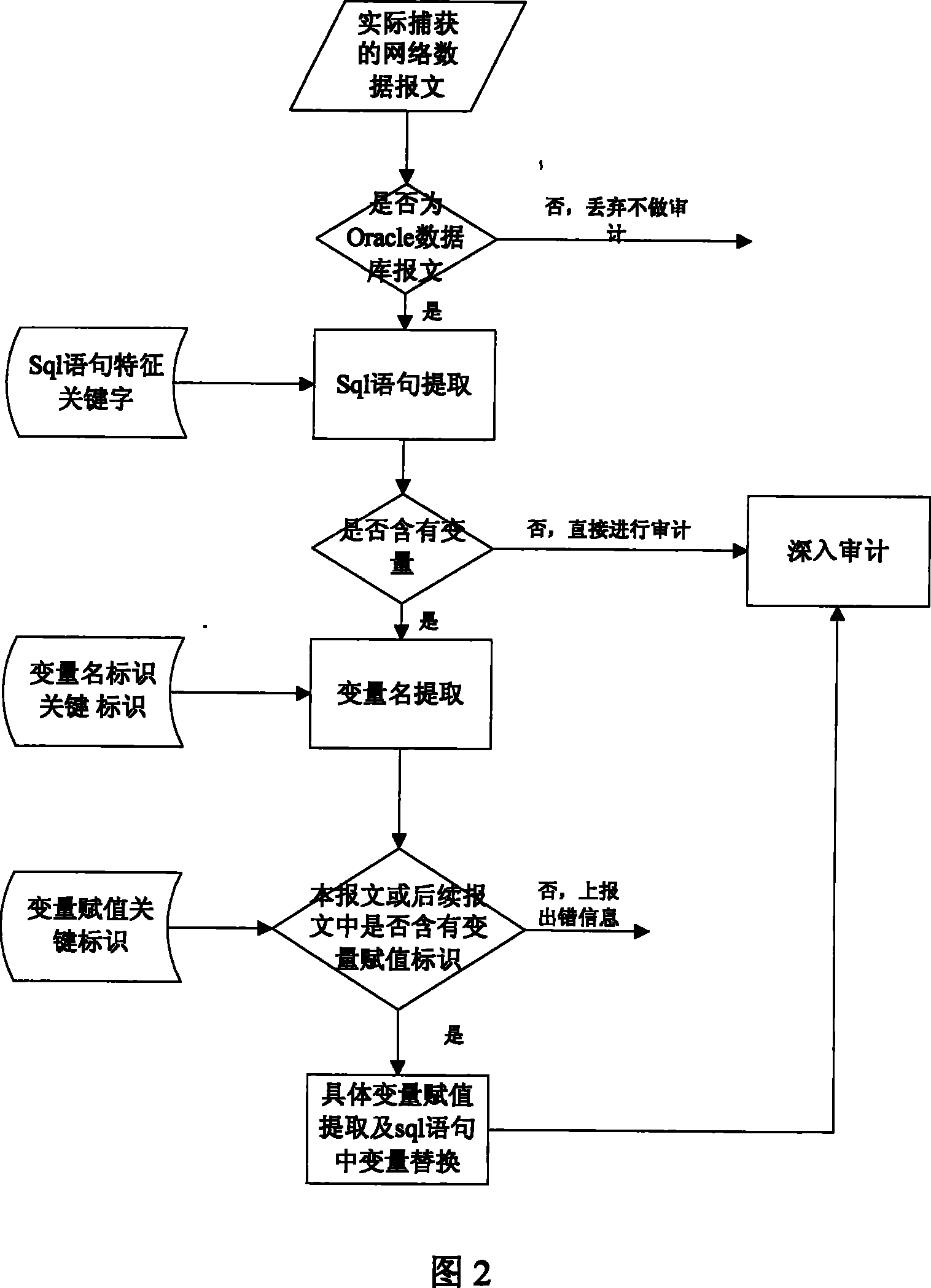
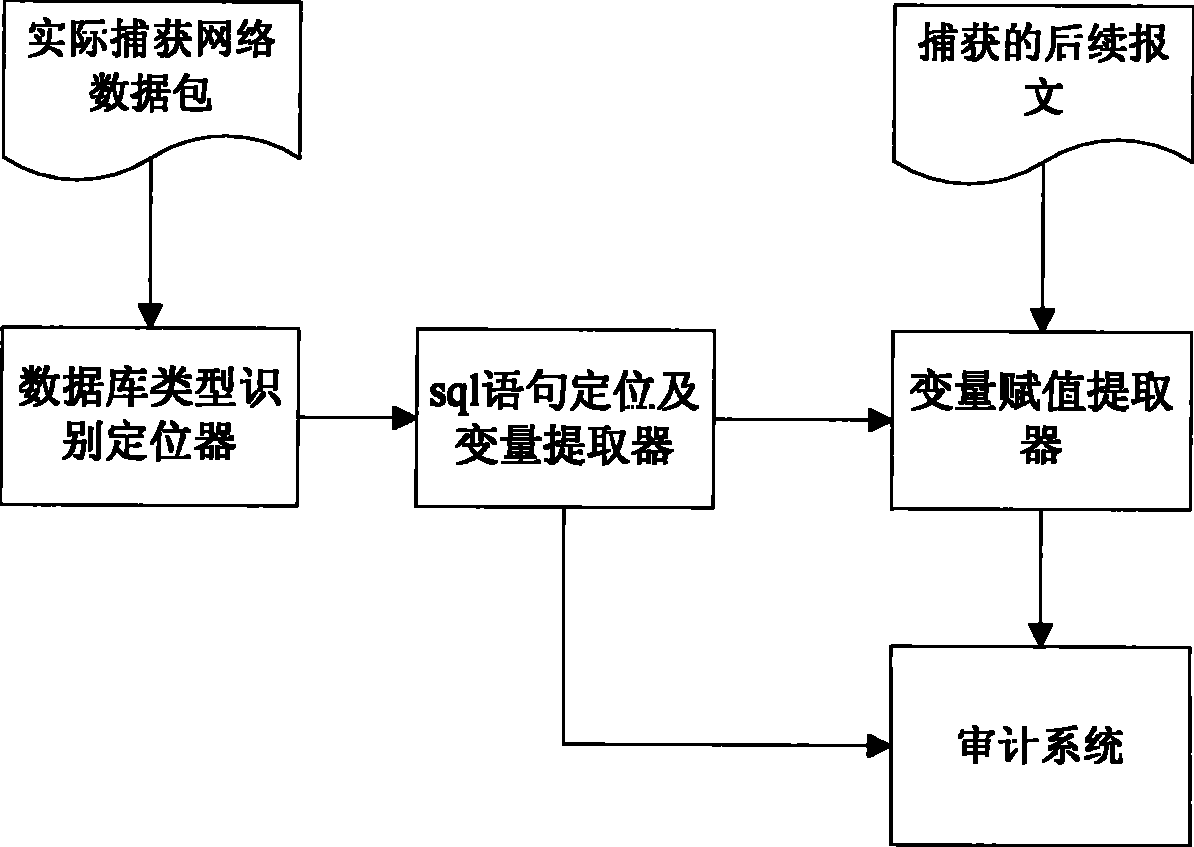
[0024] This embodiment is the basic mode of the audit method of the sql statement of the oracle database binding variable. The system used is shown in Figure 1. Including database type identification locator, sql statement location and variable extractor, variable assignment extractor and audit system, the operation process is shown in Figure 2. Said method comprises the following steps:
[0025] Database type identification and positioning step;
[0026] SQL statement positioning and variable extraction steps;
[0027] Variable assignment extraction step;
[0028] audit steps.
[0029] ① Database type identification and positioning steps. Different databases use different communication protocols, for example, Sybase database and sqlserver database use TDS protocol, Oracle database uses TNS protocol, Informix database uses its self-designed informix protocol, and so on. These databases will exchange some system information with each other during the initial connection an...
Embodiment 2
[0034] This embodiment is a preferred solution for the step of identifying and locating database types in Embodiment 1. The sub-steps included in the database type identification and location step:
[0035] Use the data packets exchanged during the initial connection interaction between the database client and the server used in the actual network environment to determine whether the current environment is an oracle database;
[0036] The output of this stage is used as the premise of sql statement positioning and variable extraction in the next stage.
[0037] The basic idea of this embodiment is:
[0038] Firstly, during the connection process between the database client and the server, use the protocol analysis method to find as much information as possible that can identify the database type and host status, including the static characteristics and ports of the protocol used. Because these information are unique identifiers of each database, and generally do not have t...
Embodiment 3
[0040] This embodiment is an optimal solution for the sql statement location and variable extraction steps in the first or second embodiment. The sub-steps in the sql statement positioning and variable extraction steps include:
[0041] Using the multi-pattern matching method to extract the sql statement that identifies the database operation behavior for the actually captured oracle database interaction data message;
[0042] In the extracted sql statement, a multi-pattern matching algorithm is used to extract the included variables;
[0043] Output the extracted sql statement containing variables and variable names as the operation object of in-depth audit.
[0044] This embodiment is carried out on the premise that the database type used in the current network environment has been determined to be an oracle database in the phase of identifying and locating the database type. In the process of data interaction between the database client and the server, the operation infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com