Personal identification process for dynamic cipher password bidirectional authentication based on multiple variables
A technology of dynamic password and authentication method, applied in the fields of two-way authentication and information security, can solve the problems that the system is difficult to popularize and use on a large scale, users are difficult to use, and the construction cost of the authentication system is high.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
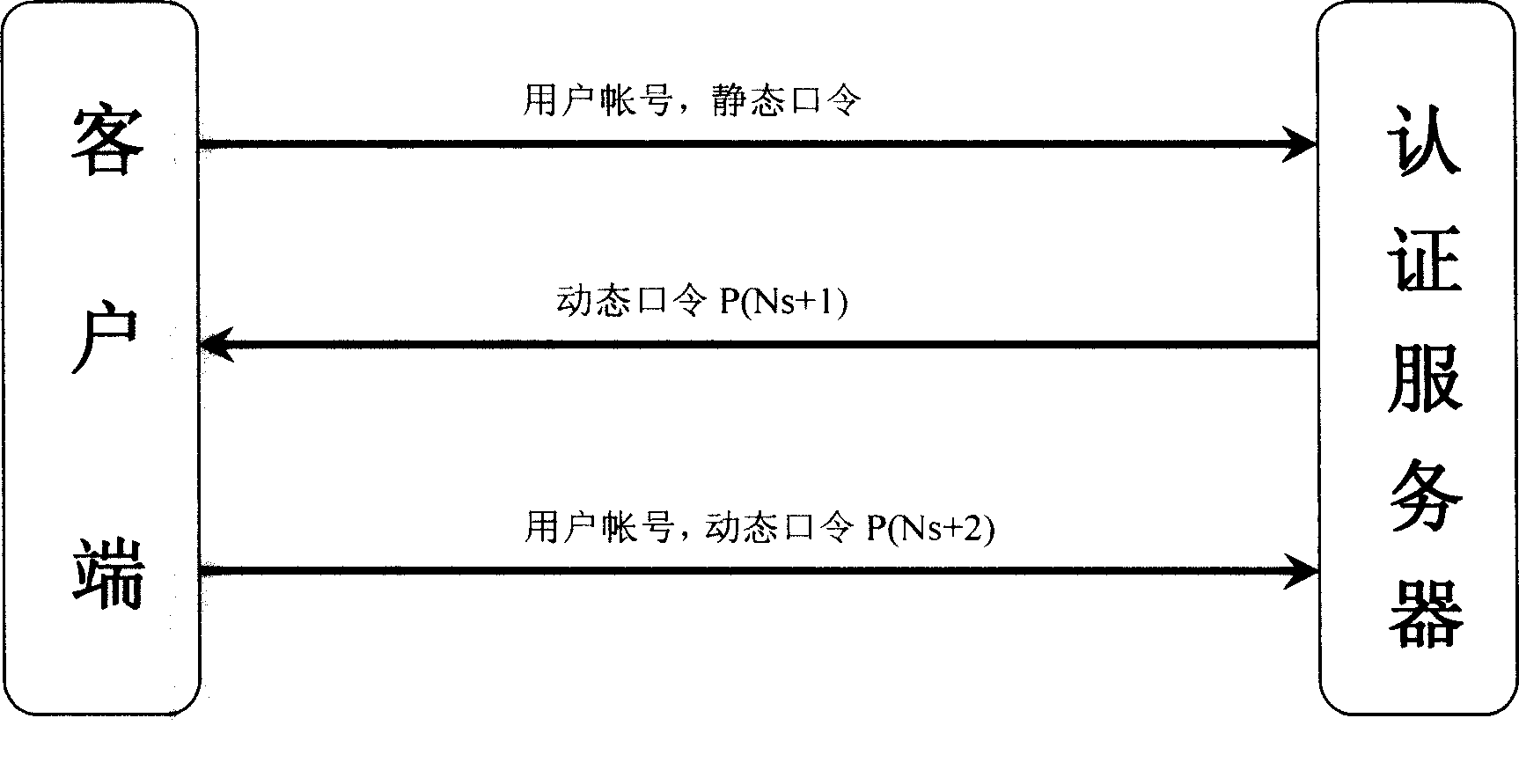
[0052] This example demonstrates the normal login process of the user, the schematic diagram is attached Figure 4 .
[0053] In the first step, the client submits the user account "Test001" and the static password "MyBirthDay+1" to the server, and the user's IP address is "61.134.1.1". After the authentication server receives the data submitted by the user, it retrieves the relevant authentication information according to the user account, and verifies that the user's static password is correct. Then set the flag Fs to 1, increase the synchronous counter value Ns by 1, that is, change from 0 to 1, and record the user's IP address.
[0054] The authentication server forwards the generated dynamic password "17297397" to the user in the second step, and the user judges the authenticity of the server based on this password. The user receives the password sent by the server, and then generates a password on his own password token. At this time, the synchronization counter value ...
example 2
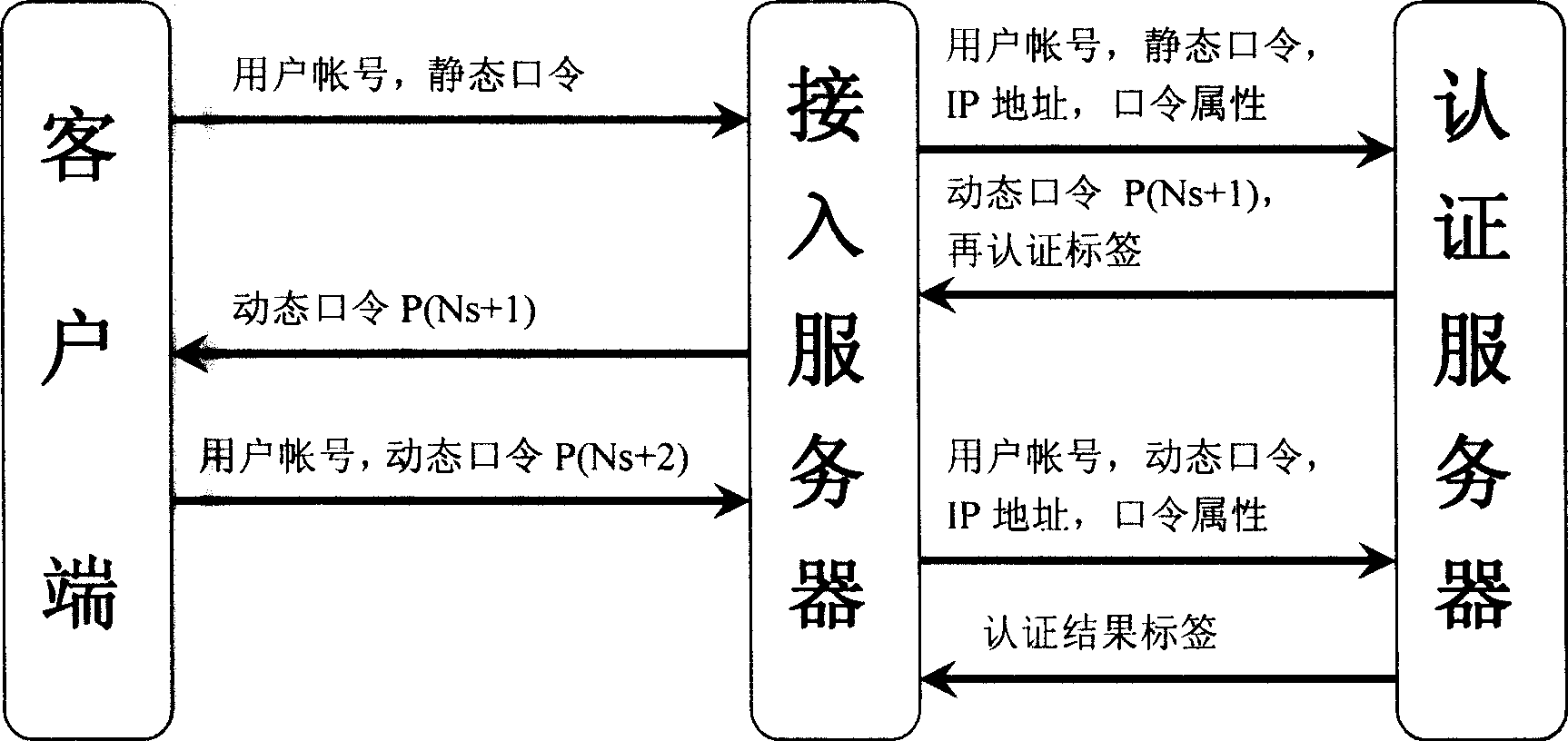
[0057] This example demonstrates the principle of preventing the "Treasure Terminator" Trojan horse attack. The schematic diagram is attached Figure 5 .
[0058] Suppose the attacker has obtained the user's account and static password in Example 1 by using the "Mibao Terminator" Trojan and other Trojans, and intercepted the dynamic password "95017043" submitted by the user to the authentication server in the third step of the authentication process. ”, and the content in the user authentication data packet was modified, and the user’s dynamic password authentication process was unsuccessful. At this time, the status characteristics of the authentication server are as follows: the synchronization count value Ns=2, and the static password authentication success flag Fs=0. The following is the authentication process after the attacker obtains the user's dynamic password:
[0059] The attacker enters the user account "Test001" and the static password "MyBirthDay+1" on the clien...
example 3
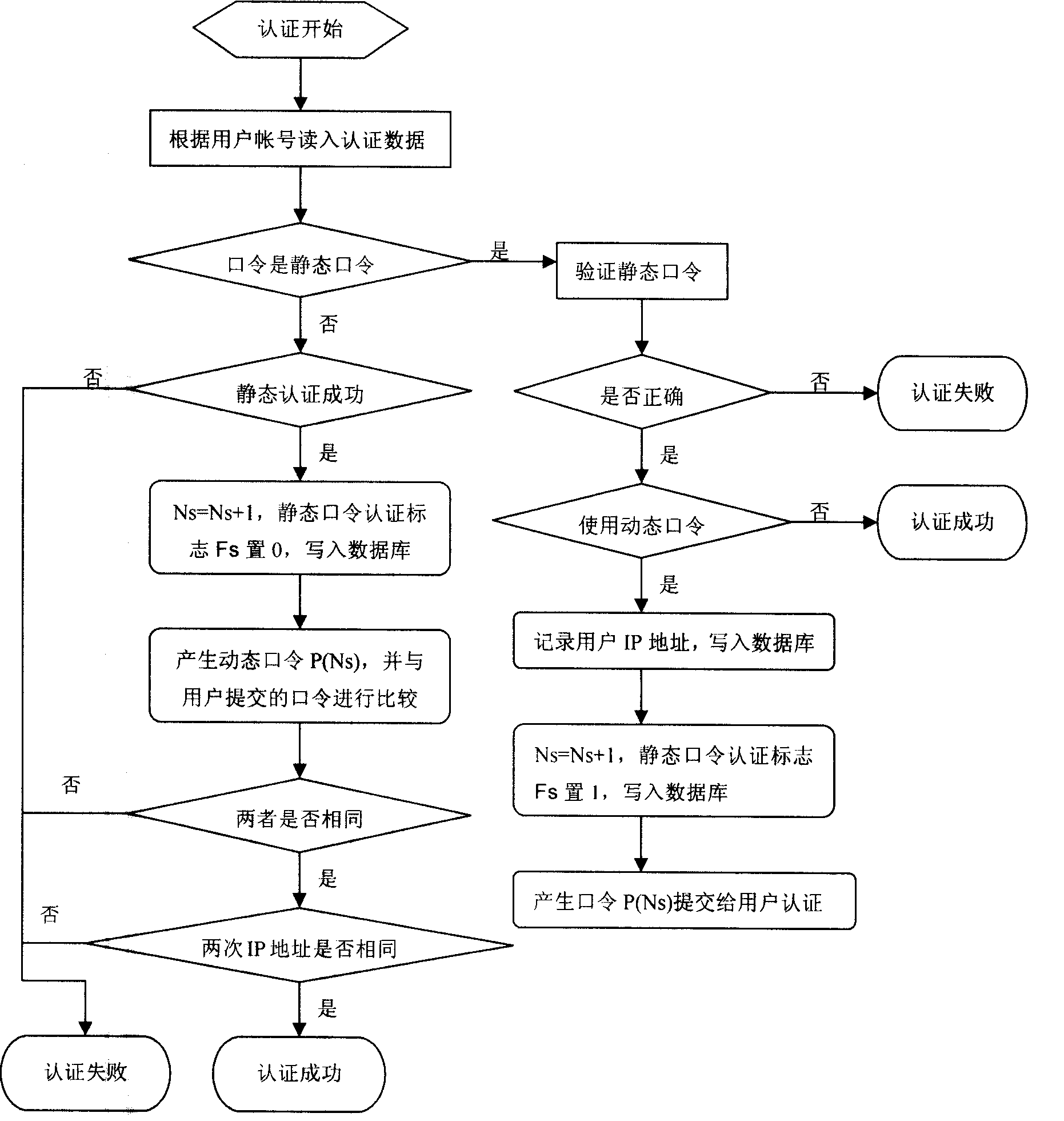
[0063] This example demonstrates the principle of preventing the "parallel session attack", see the attached diagram for the diagram Image 6 .
[0064] The so-called "parallel session attack" means that the attacker deliberately runs multiple protocol processes concurrently, in an attempt to obtain the answer required by a process in multiple running processes.
[0065] The attacker's first step is to enter the user name "Test001" and the correct static password on the machine whose IP address is "61.138.1.2". After the server passes the authentication, a password "20014829" is sent to the attacker. In order to obtain this password Then enter the user name "Test001" and the correct static password on another machine whose IP address is "61.138.1.3", the server sends a password "07196154" after verification, and the attacker can then After completing the first authentication process, enter the password "07196154" on the machine whose IP address is "61.138.1.2", and the synchr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com