Method for implementing IPSEC resistance of replay aggression
An anti-replay and attack packet technology, applied in the field of network communication, can solve problems such as performance degradation and discarded packets, and achieve the effect of checking the accuracy of replay attacks and improving the IPSec anti-replay attack function.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
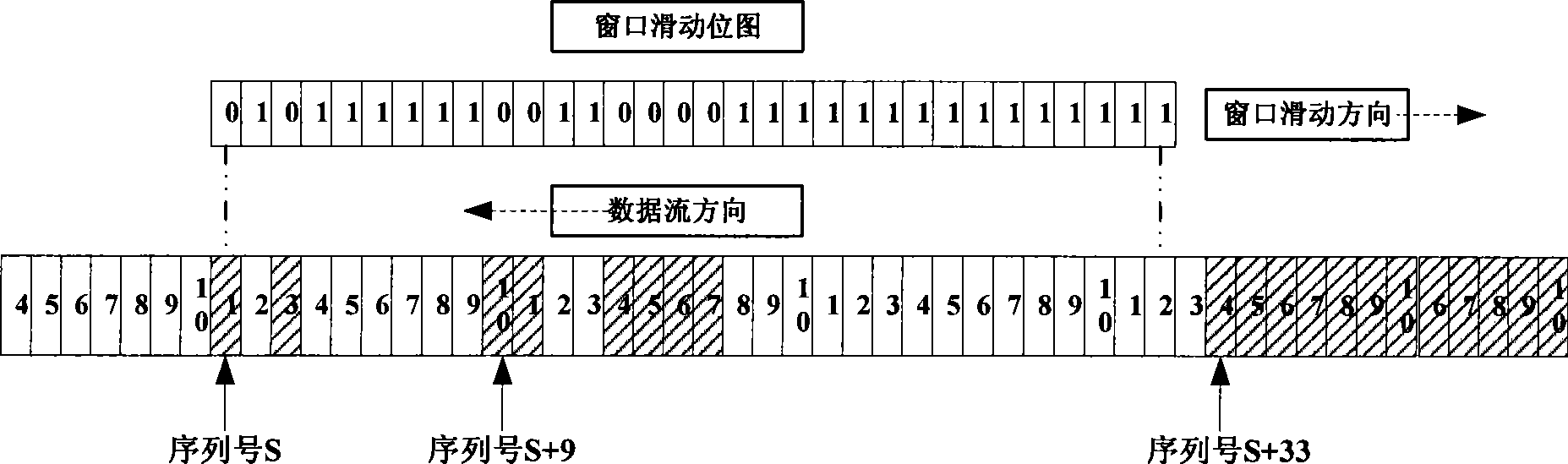
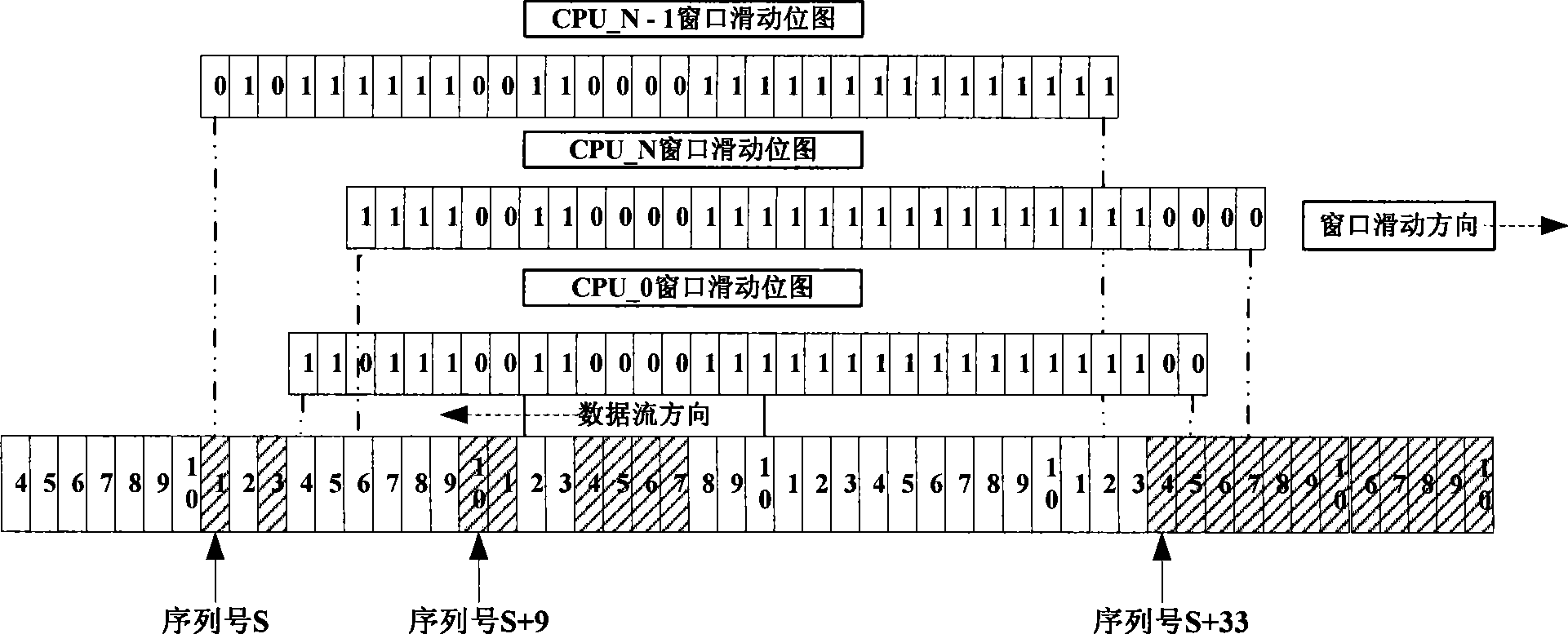
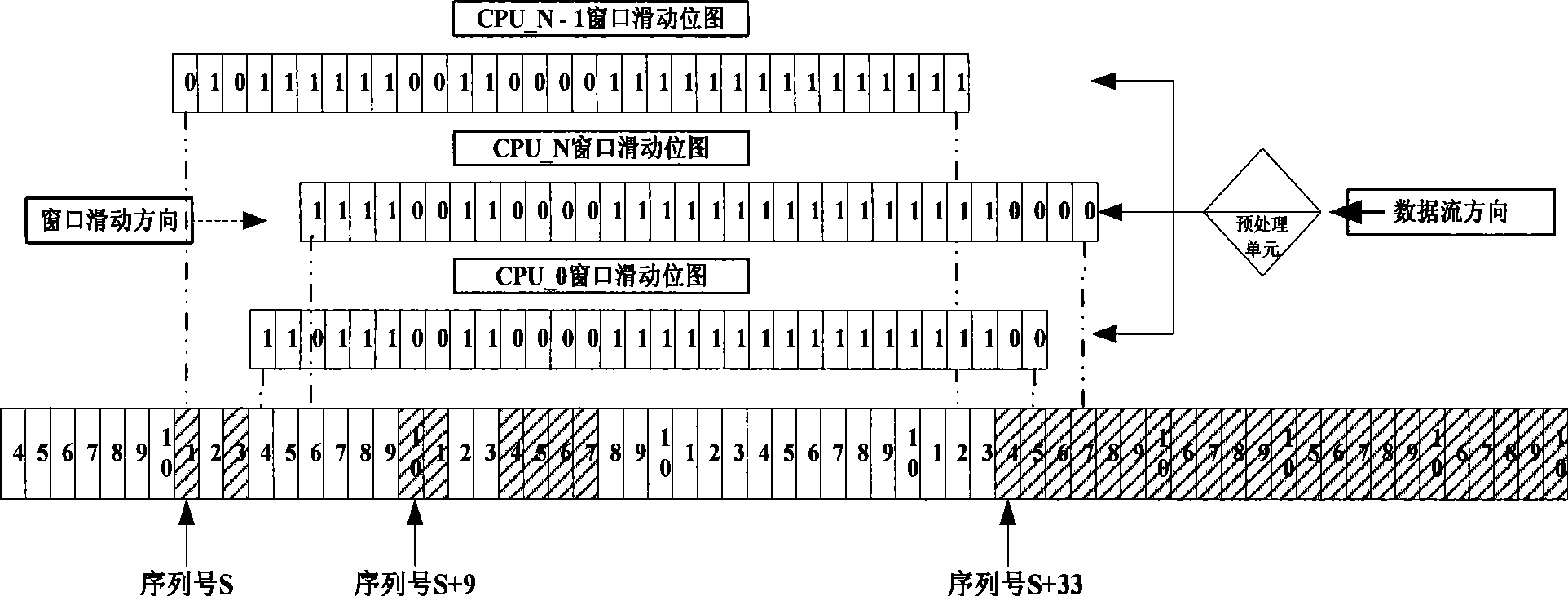
[0036] Below, refer to the attached Figure 1~5 The method for realizing IPSEC anti-replay attack under the multi-core framework of the present invention is described in detail.
[0037] Regardless of whether it is in a multi-core or single-core architecture, each CPU or processing unit checks for replay attacks, relying on a unique, monotonically increasing sequence number.
[0038]The receiving party that provides IPSec service performs replay check immediately after the received message passes the authenticity check, needs to update the serial number, and completes the confidentiality check (decryption). Set the corresponding bitmap in the "sliding" window. If the sequence number of the current message exceeds the size of the "sliding" window, you need to "slide" the window to the right. During this period, there is a "time" window, and other processing units may receive messages within this "time" window. If the lock mechanism is not used, the serial number can also be up...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com