Method for dynamically updating inbreak detection rule through network link data
An intrusion detection and link data technology, applied in digital transmission systems, security communication devices, electrical components, etc., can solve problems such as time-consuming and laborious, and achieve the effect of simplifying updates and reducing the probability of intrusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
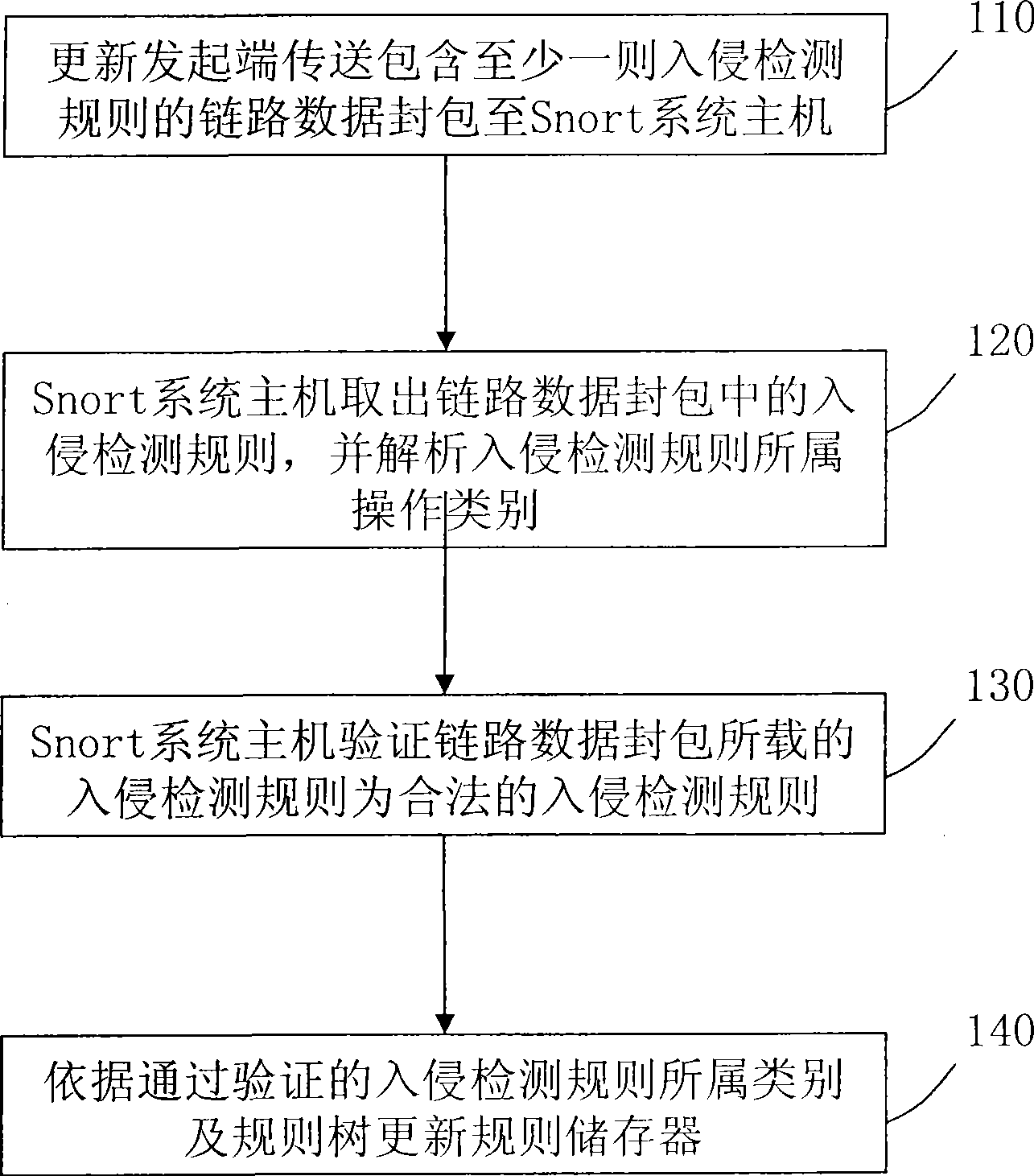
[0034] The purpose of the present invention and the proposed method for updating intrusion detection rules through link data packets are described in detail in the following preferred embodiments. However, the concept of the invention can also be used in other areas. The following examples are only used to illustrate the purpose and implementation method of the present invention, and are not intended to limit the scope thereof.
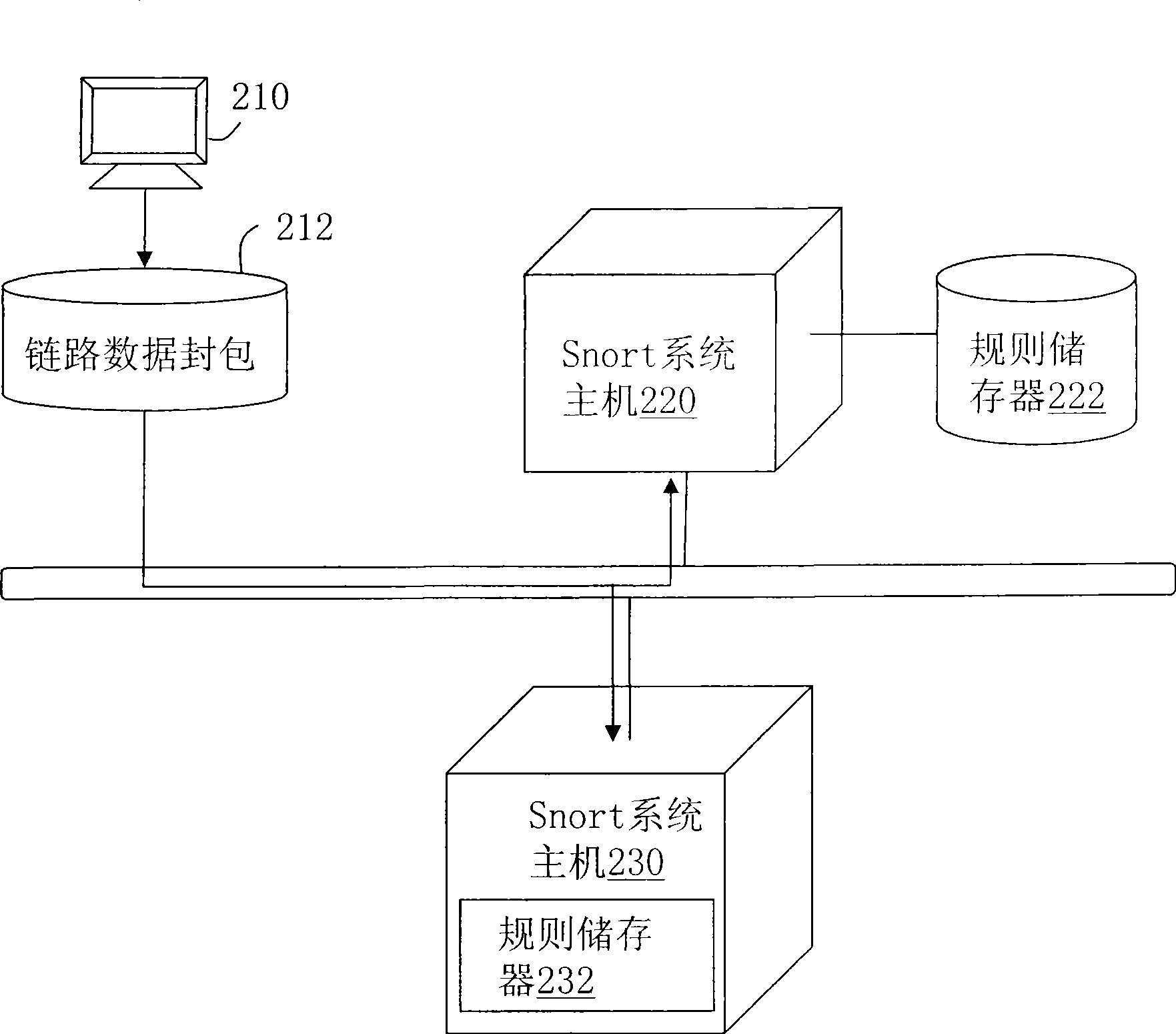
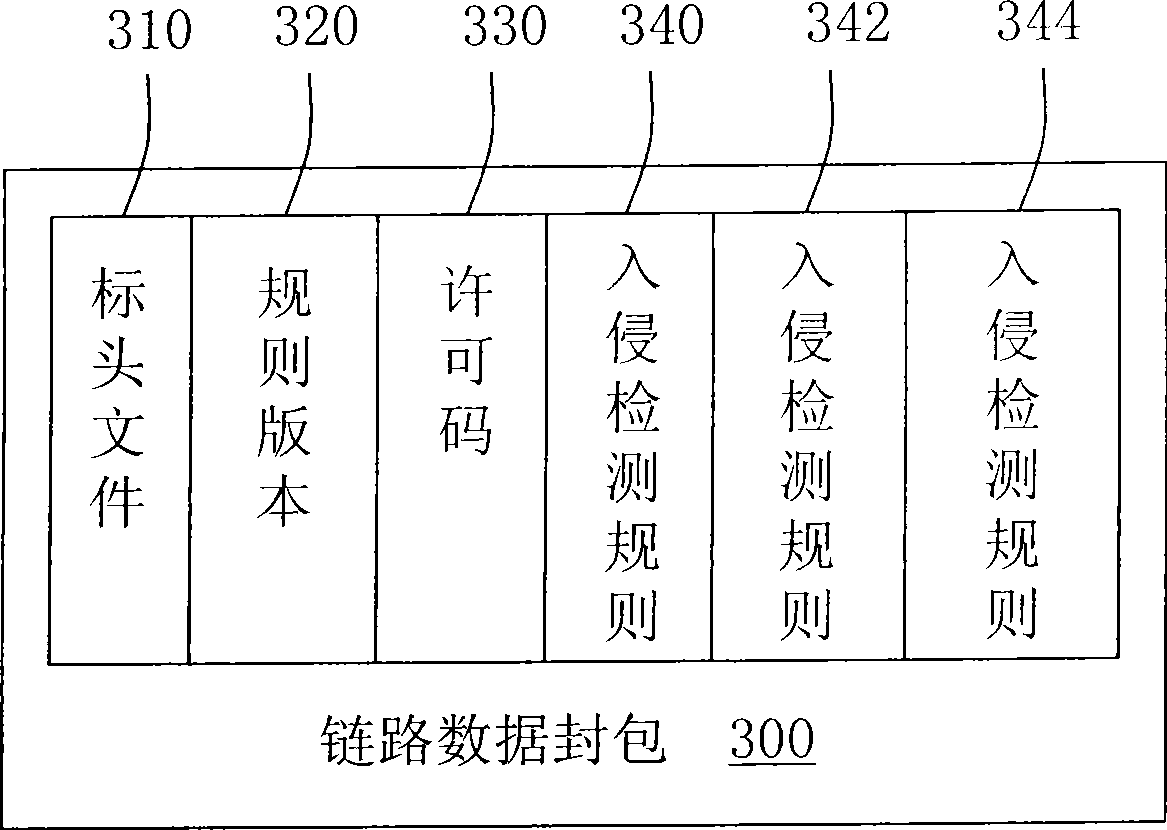
[0035] figure 1 It is a flowchart of a method for updating intrusion detection rules through link data packets in the present invention. Please refer to figure 1 , the proposed method for updating intrusion detection rules is used to dynamically update the rule storage of at least one Snort system host in the local area network. In order to quickly write the intrusion detection rules to be updated into the rule storage corresponding to each Snort system host. The so-called link data packet is the link data of the original network packet, that is, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com