Hardware security unit
A hardware security, computing unit technology, applied in computer security devices, instruments, computing, etc., to achieve the effect of flexible operation and improved user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The invention provides a hardware security unit, which solves the problems encountered in the prior art when binary logic judgment is used to serve the entire trust chain.
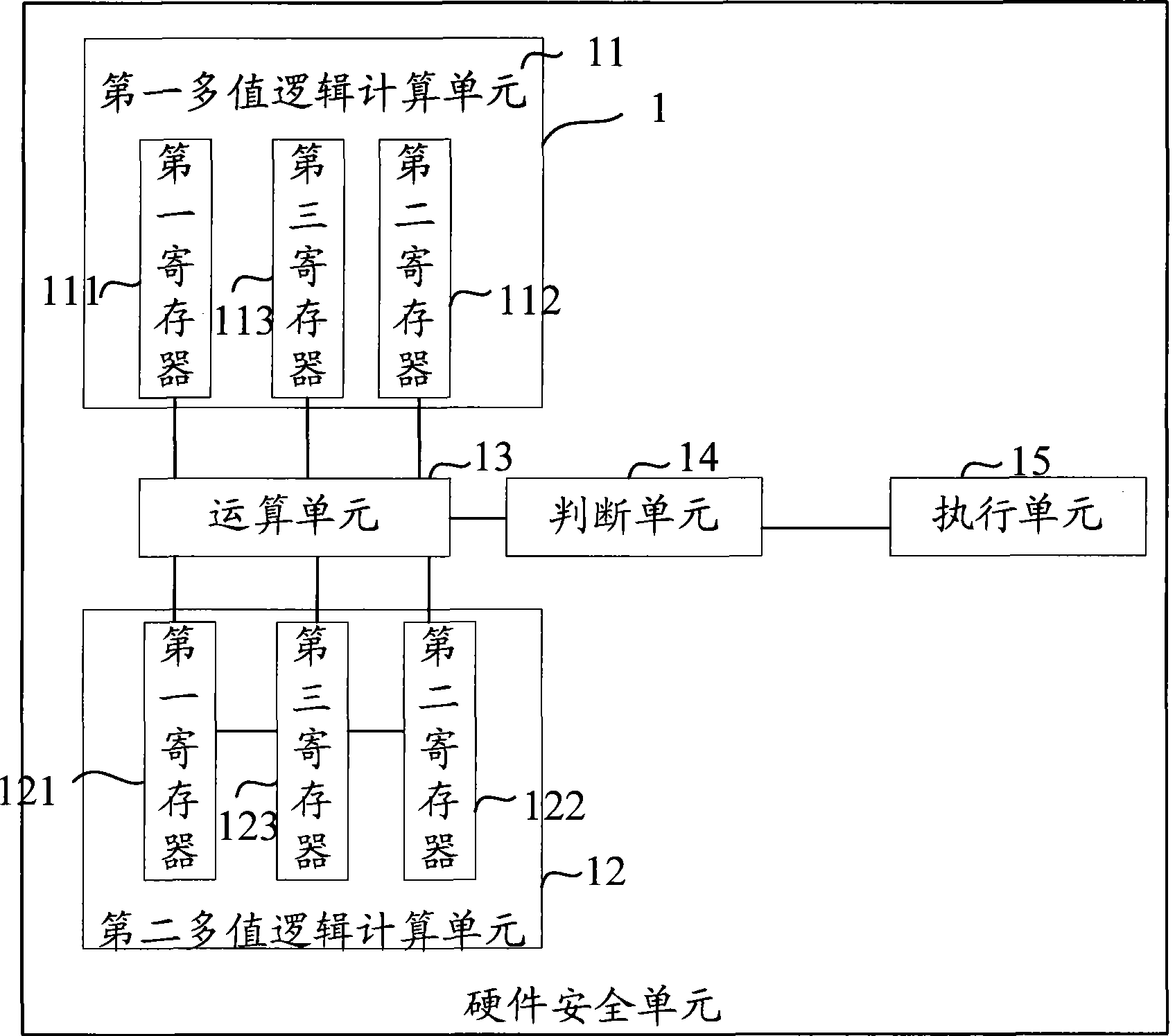
[0034] see figure 1 , which is a structural diagram of the first embodiment of the hardware security unit of the present invention.
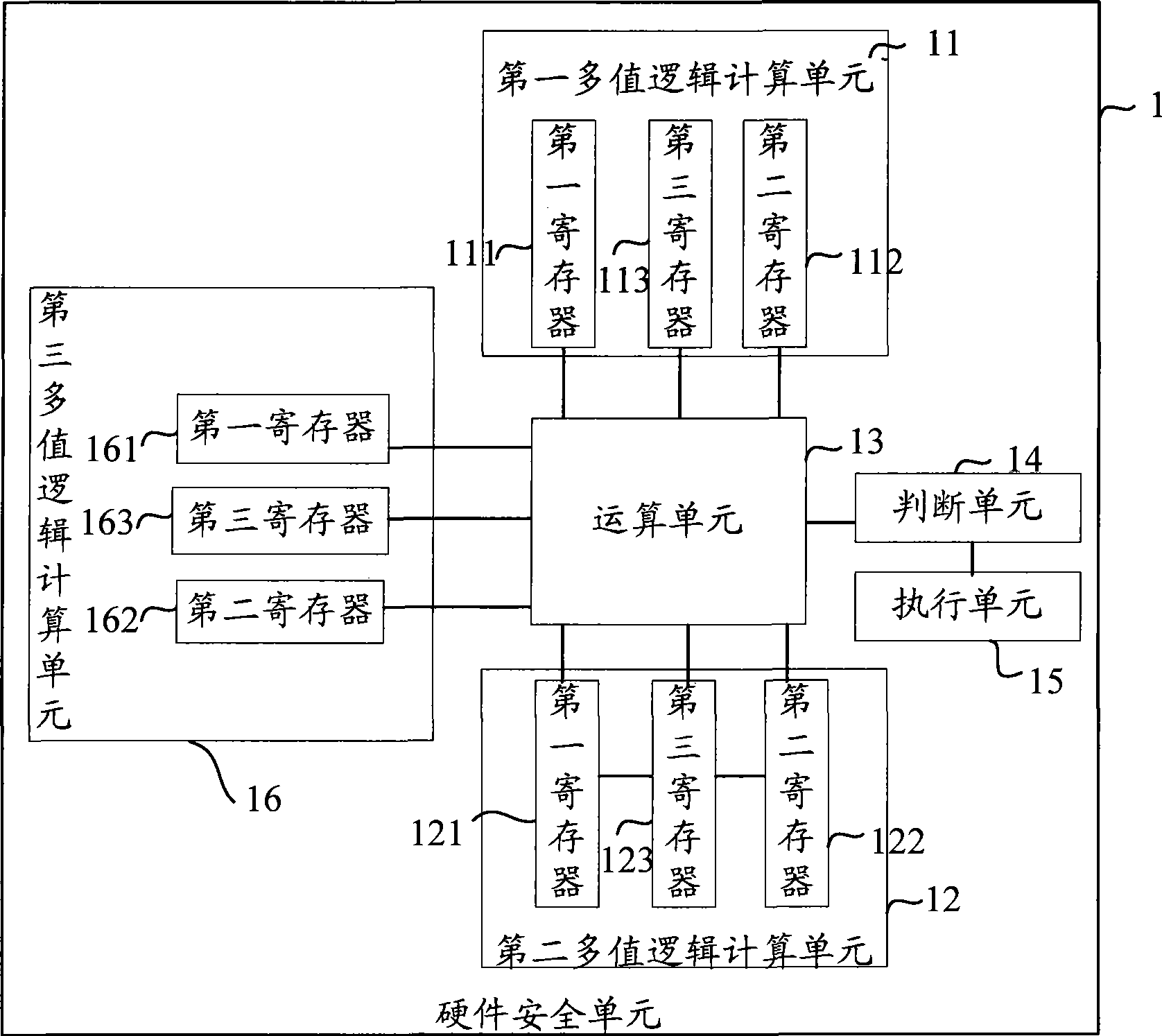
[0035] The hardware security unit 1 in the first embodiment of the present invention adopts two multi-valued logic calculation units, an operation unit 13 , a judgment unit 14 and an execution unit 15 . The two multi-valued logic computing units are specifically a first multi-valued logic computing unit 11 and a second multi-valued logic computing unit 12 .
[0036] Both the first multi-valued logic computing unit 11 and the second multi-valued logic computing unit 12 respectively include three registers.
[0037] The first register 111 of the first multi-valued logic computing unit describes the expected logic state of the specific functional entity corresponding t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com