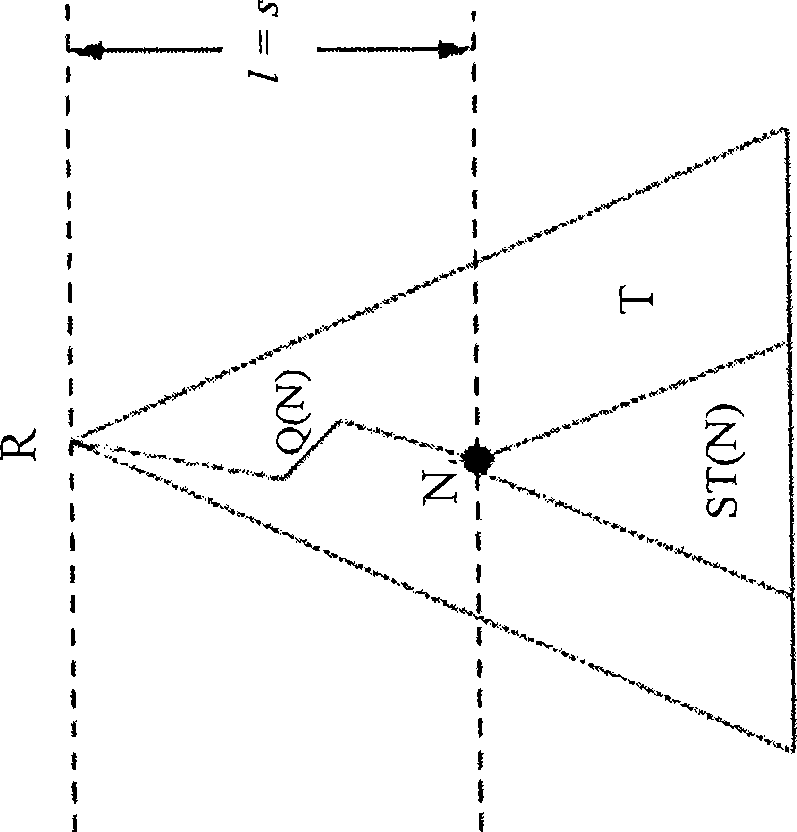
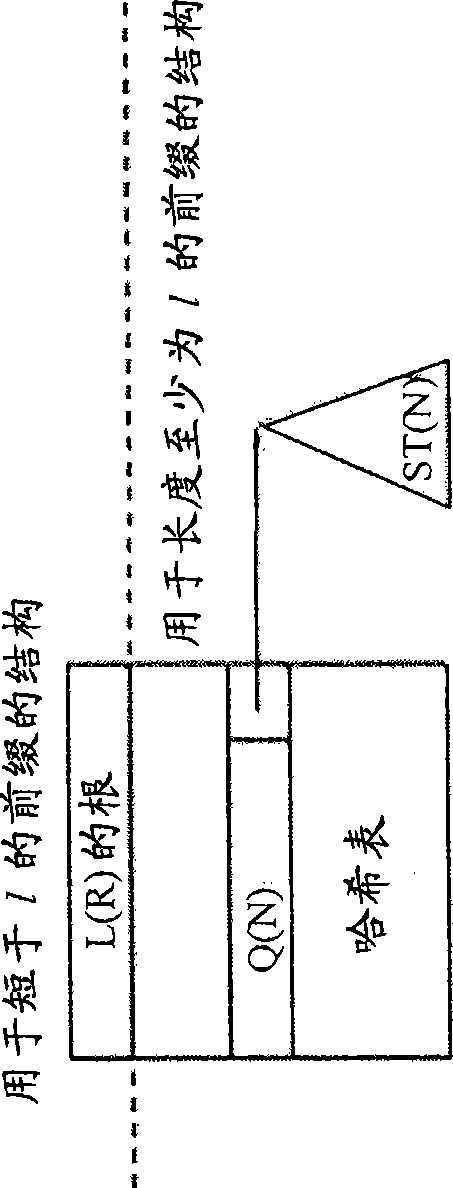
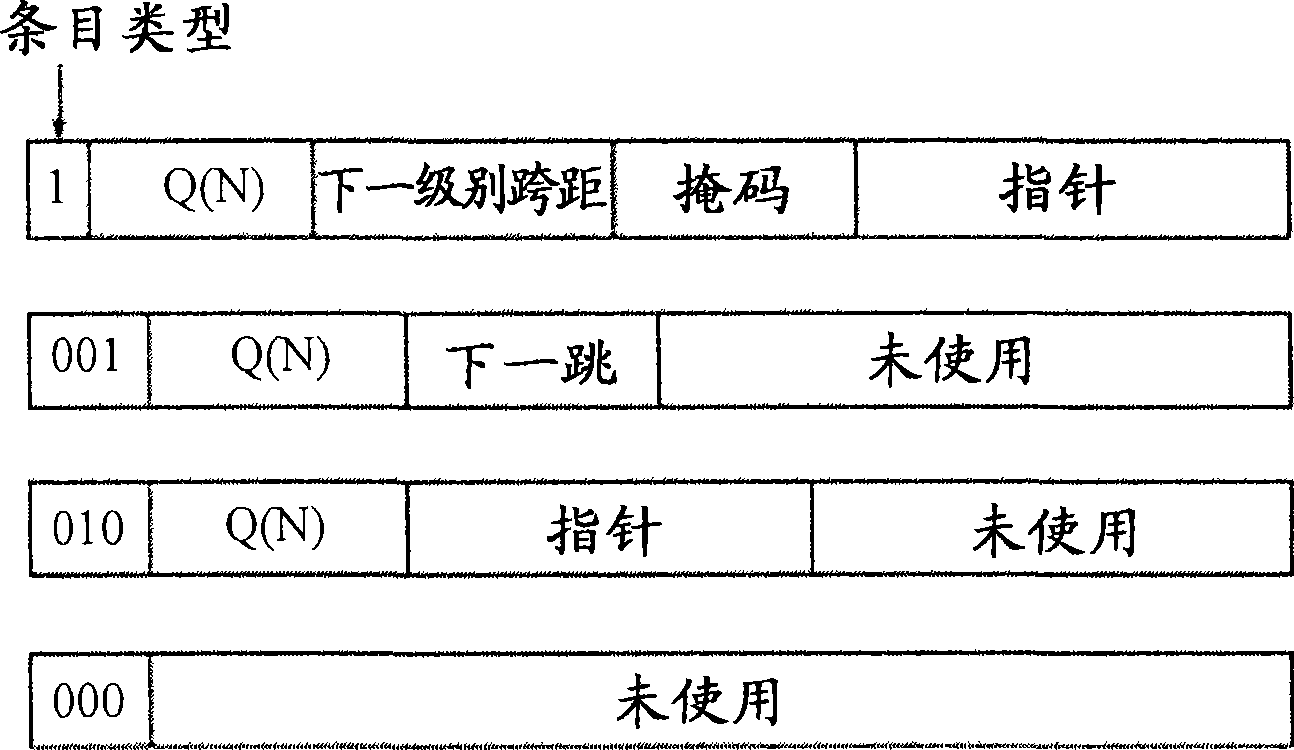
Recursively partioned static ip router tables
A purpose and address technology, applied in the field of IP routing tables, can solve the problems of increasing the number of memory accesses required for searching, increasing the total storage capacity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1-36
[0061] Example 1-36 bit design
[0062] In one implementation example, 36 bits are allocated for each hash entry. For IPv4, 8 bits are used for Q(N), 2 bits for the stride of the next level of segmentation, 8 bits for the mask, and 17 bits for the pointer. Although 8 bits are allocated for Q(N), strides are limited from five to eight. Therefore, two bits are sufficient to represent the next level of spanning. The use of 17-bit pointers enables indexing up to 9Mbits (2 17 ×72) SRAM. For IPv6, the corresponding bit assignments are 7, 2, 7, and 19, respectively. For IPv6, the span is limited from four to seven. So seven bits are enough for the Q(N) sum, and two bits are enough for the next level of stride. The 19-bit pointer is capable of indexing 36Mbit SRAM. For the next hop field, 12 bits are allocated for both IPv4 and IPv6. For the library structure, enhanced libraries were used with the end-node optimization (EBO) version of HSST, as they were shown to be the most e...
example 2-72
[0063] Example 2-72 bit design
[0064] In another implementation example, 72 bits are allocated for each hash table entry. For both IPv4 and IPv6, 17 bits are used for the Q(N), five bits for the stride of the next level of segmentation, 17 bits for the mask, and 19 bits for the pointer. The span is limited between 1 and 17. Also, for the stripped prefix in L(R) * The next hop (if any) is stored in each hash table entry. Implement the partition such that at each node N, using the L(R) partition denoted EBO and the (full) hash table for the remaining partitions, and executing L(R)-{ *}, distributes these extended prefixes to the remaining splits, and then constructs a hash table for the modified set of splits. Type 1 nodes use designated bits to distinguish between the different hash table types they may point to.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com