Patents
Literature
36 results about "Perfect hash function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
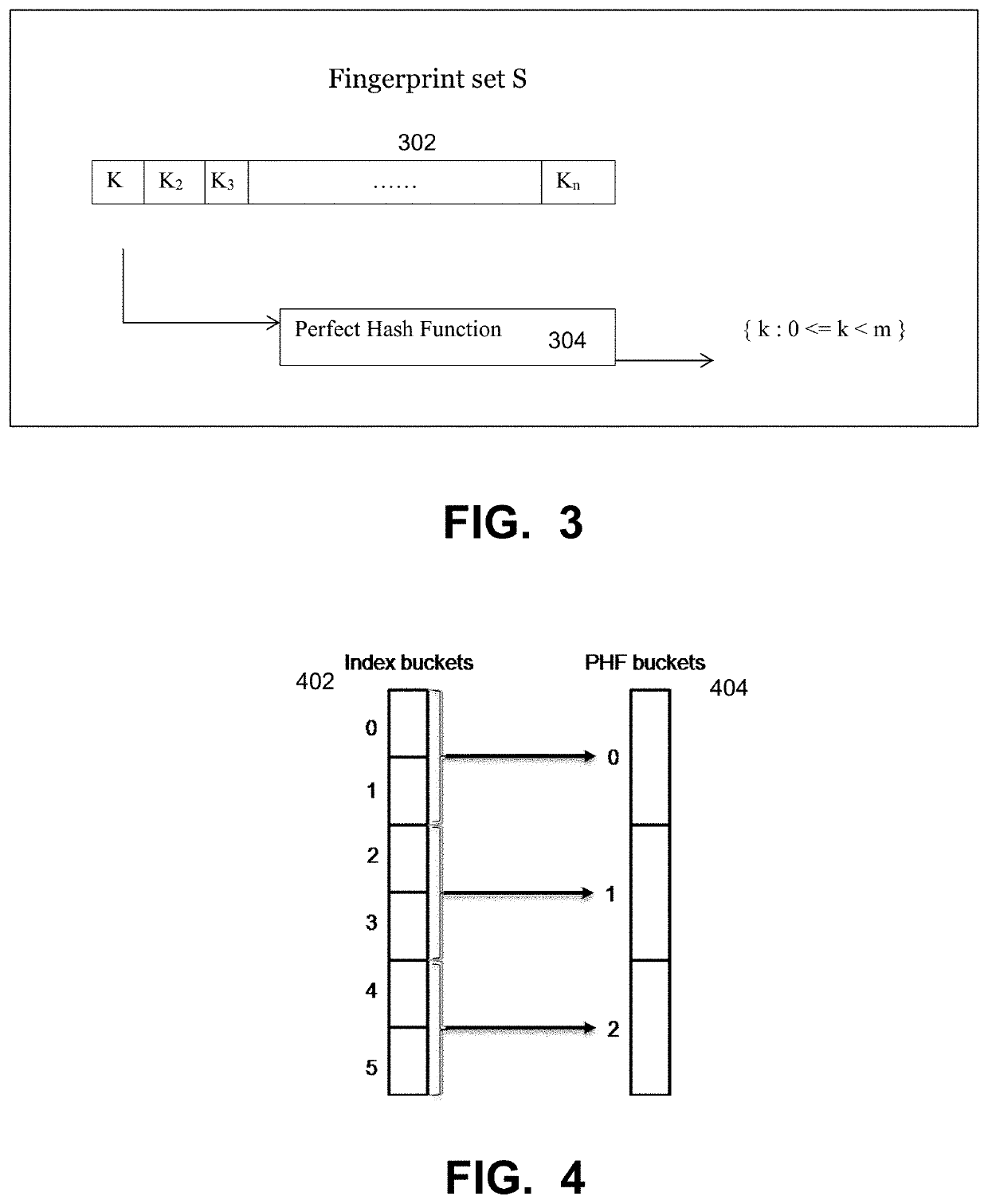
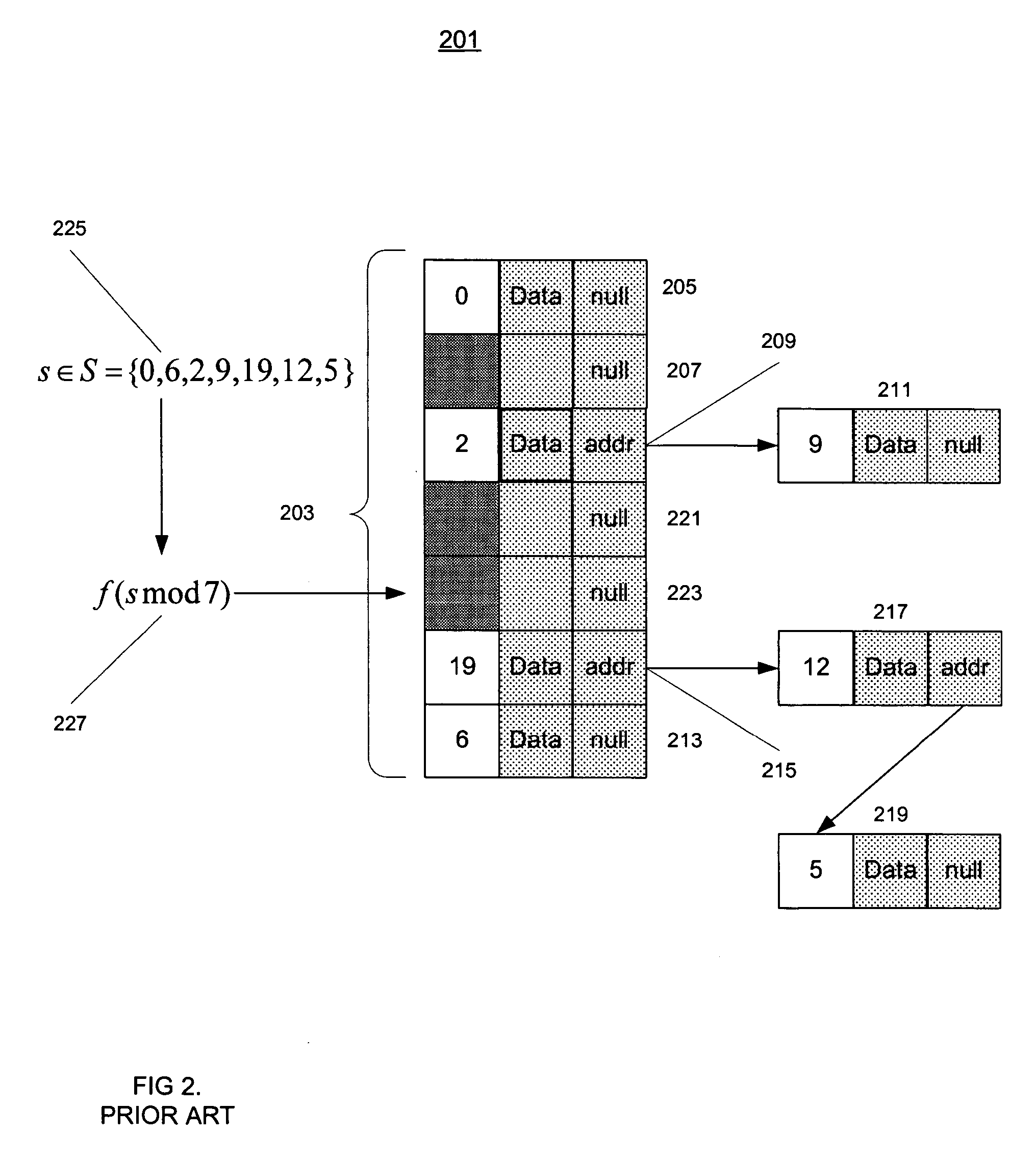
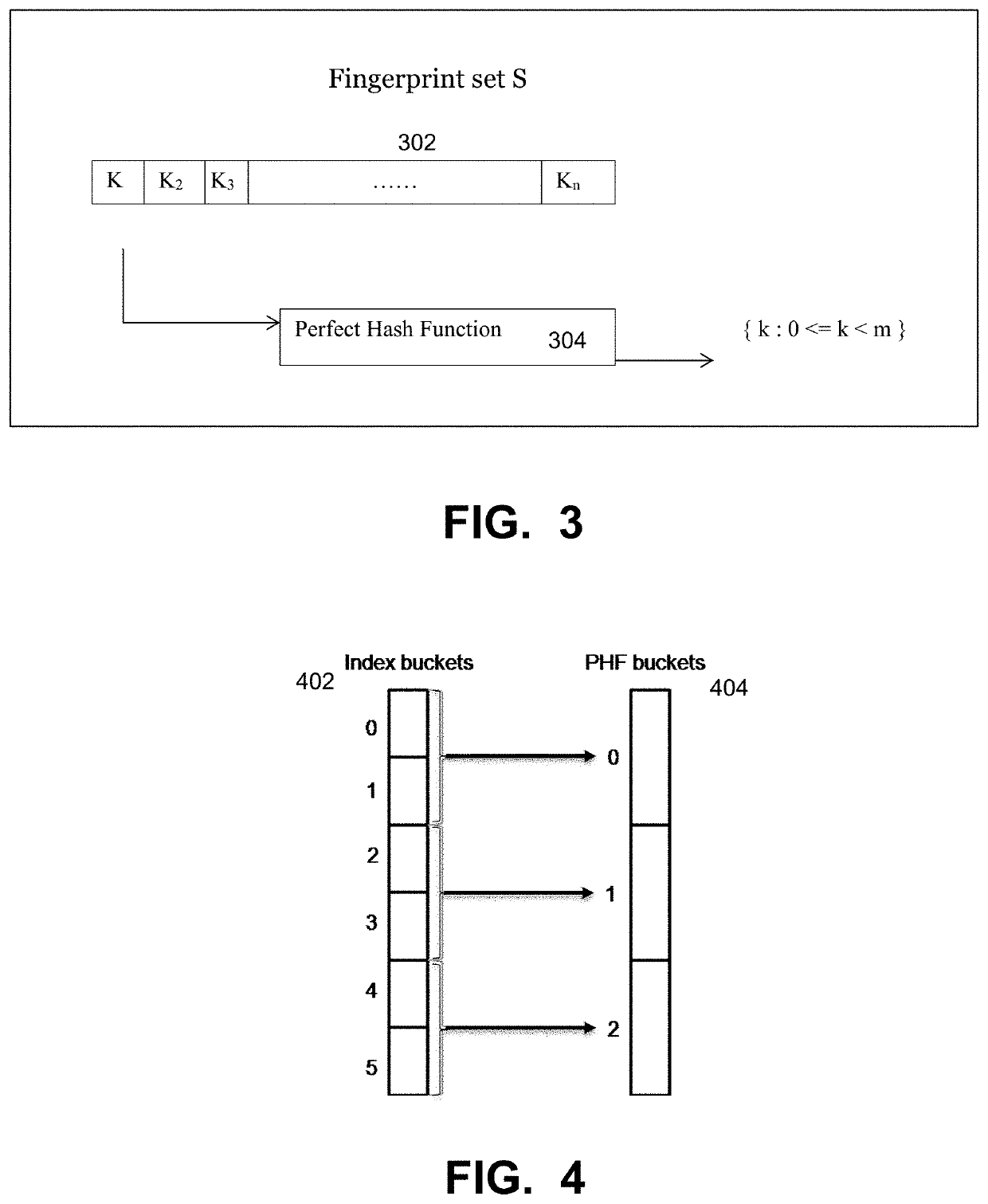
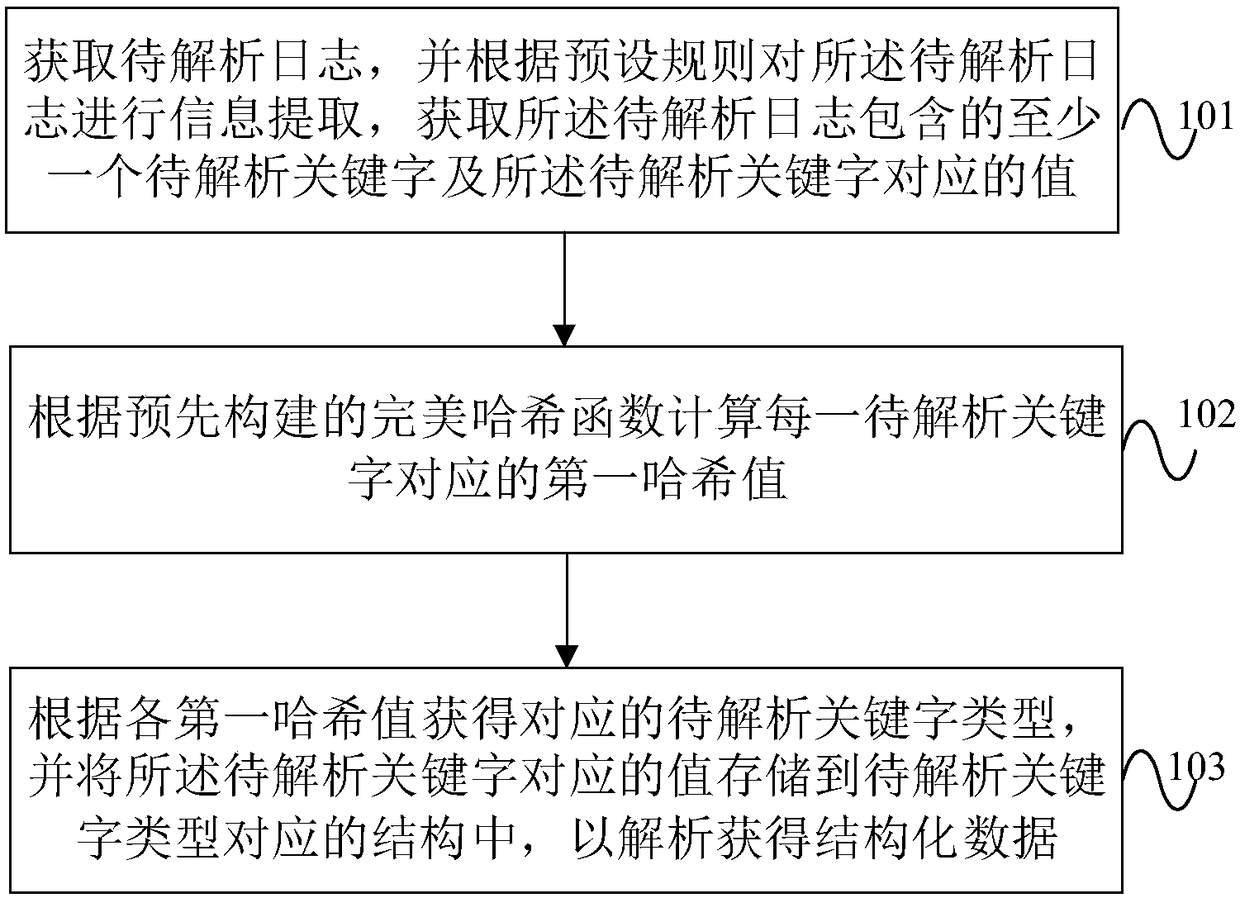
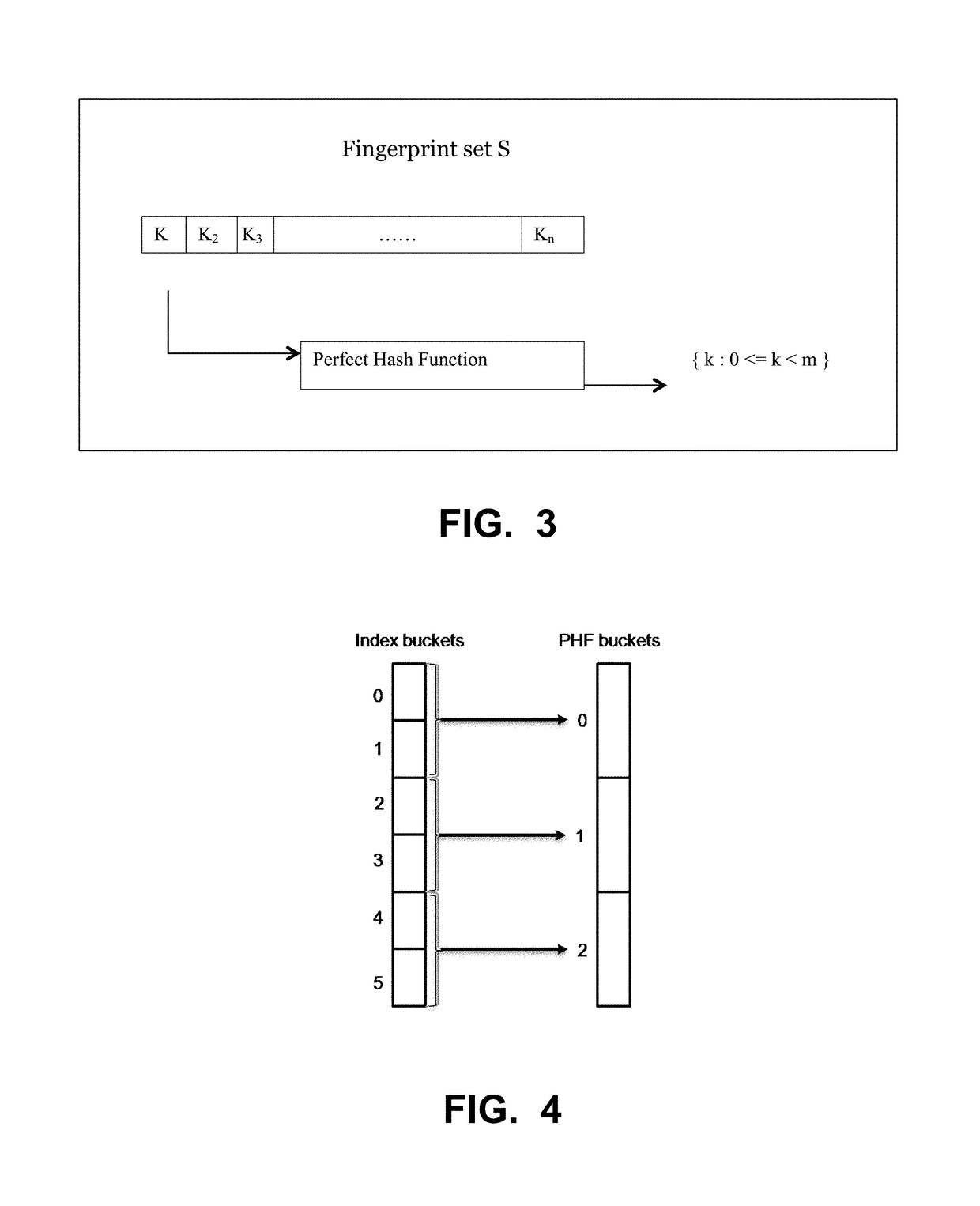
In computer science, a perfect hash function for a set S is a hash function that maps distinct elements in S to a set of integers, with no collisions. In mathematical terms, it is an injective function.
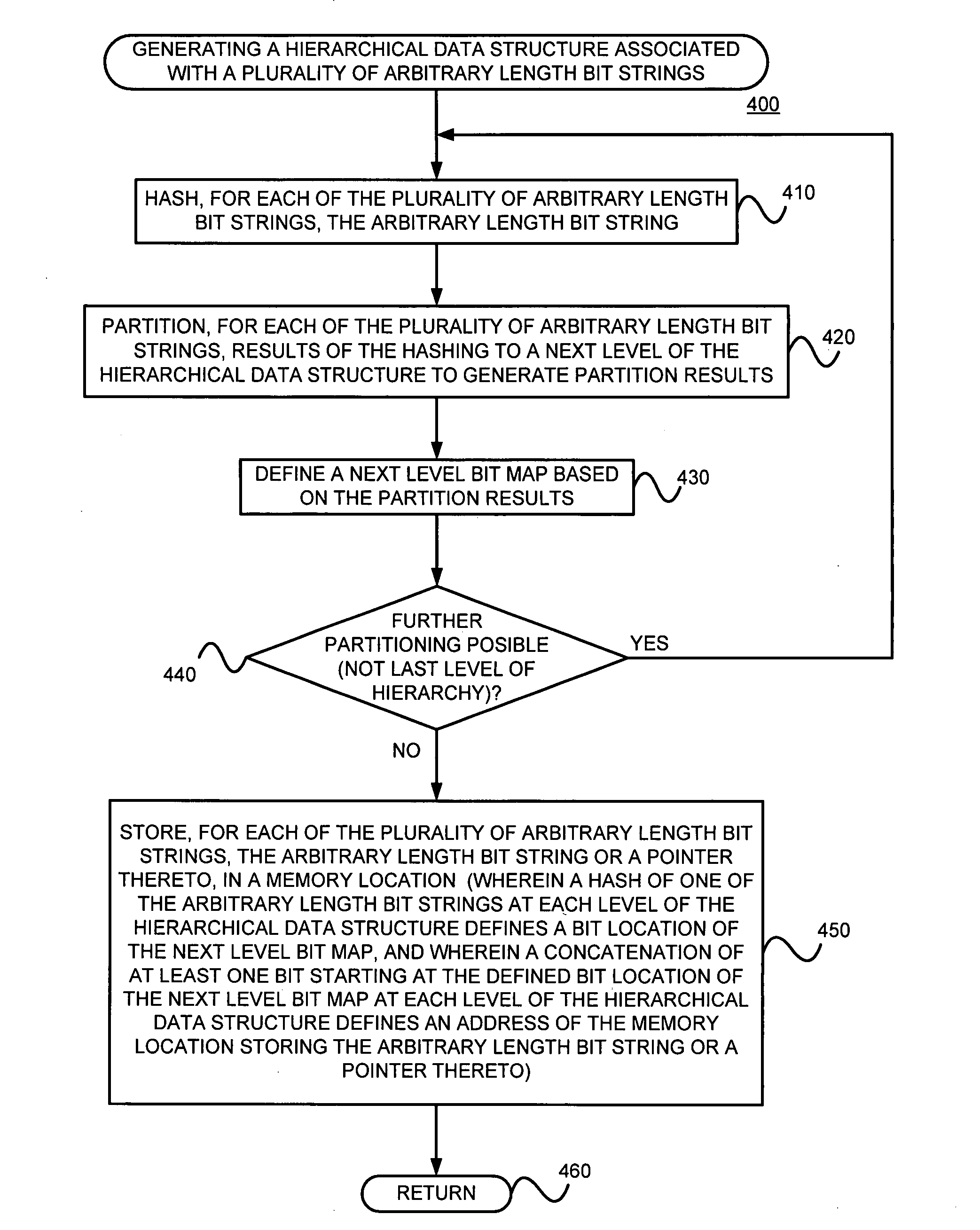
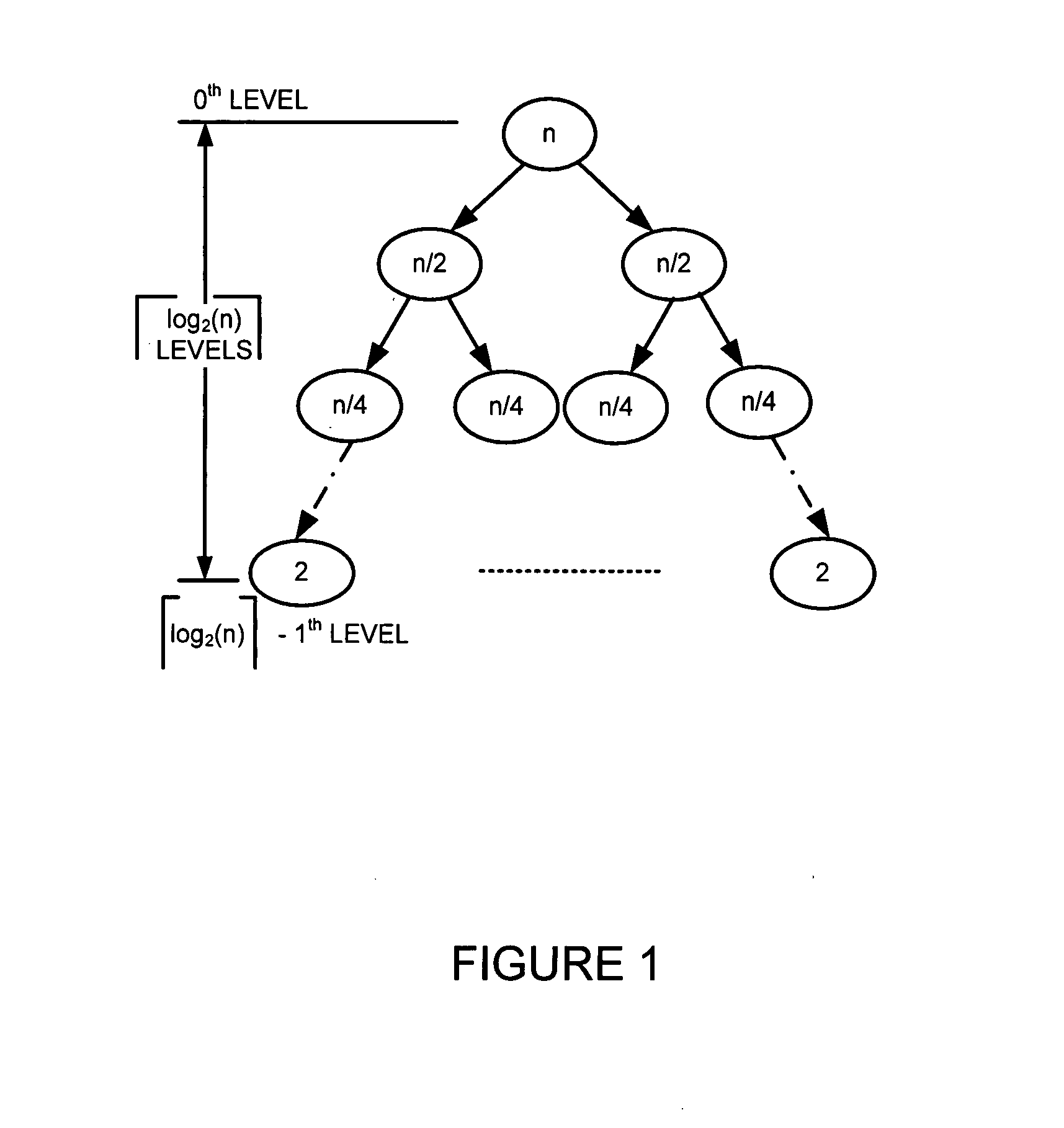
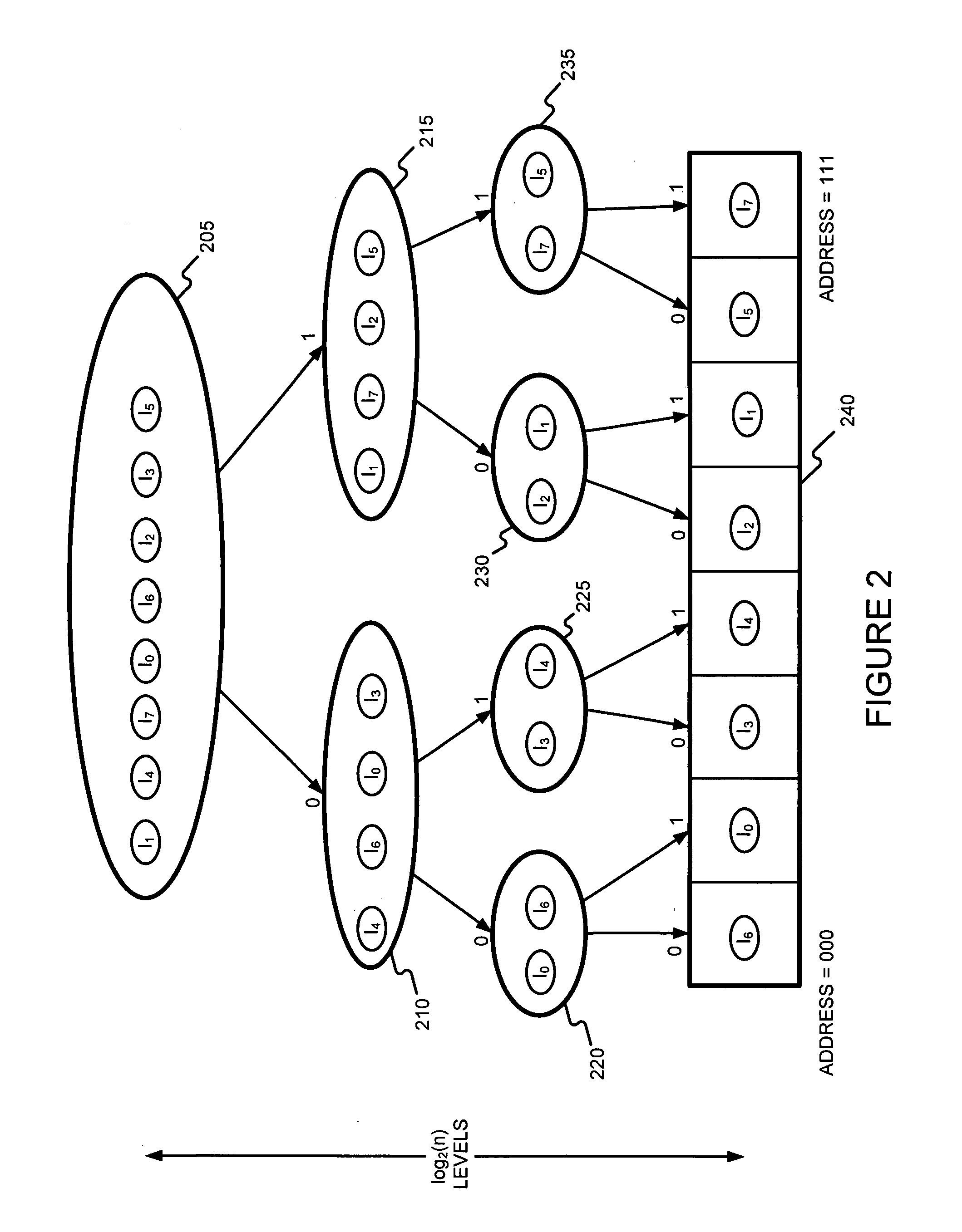
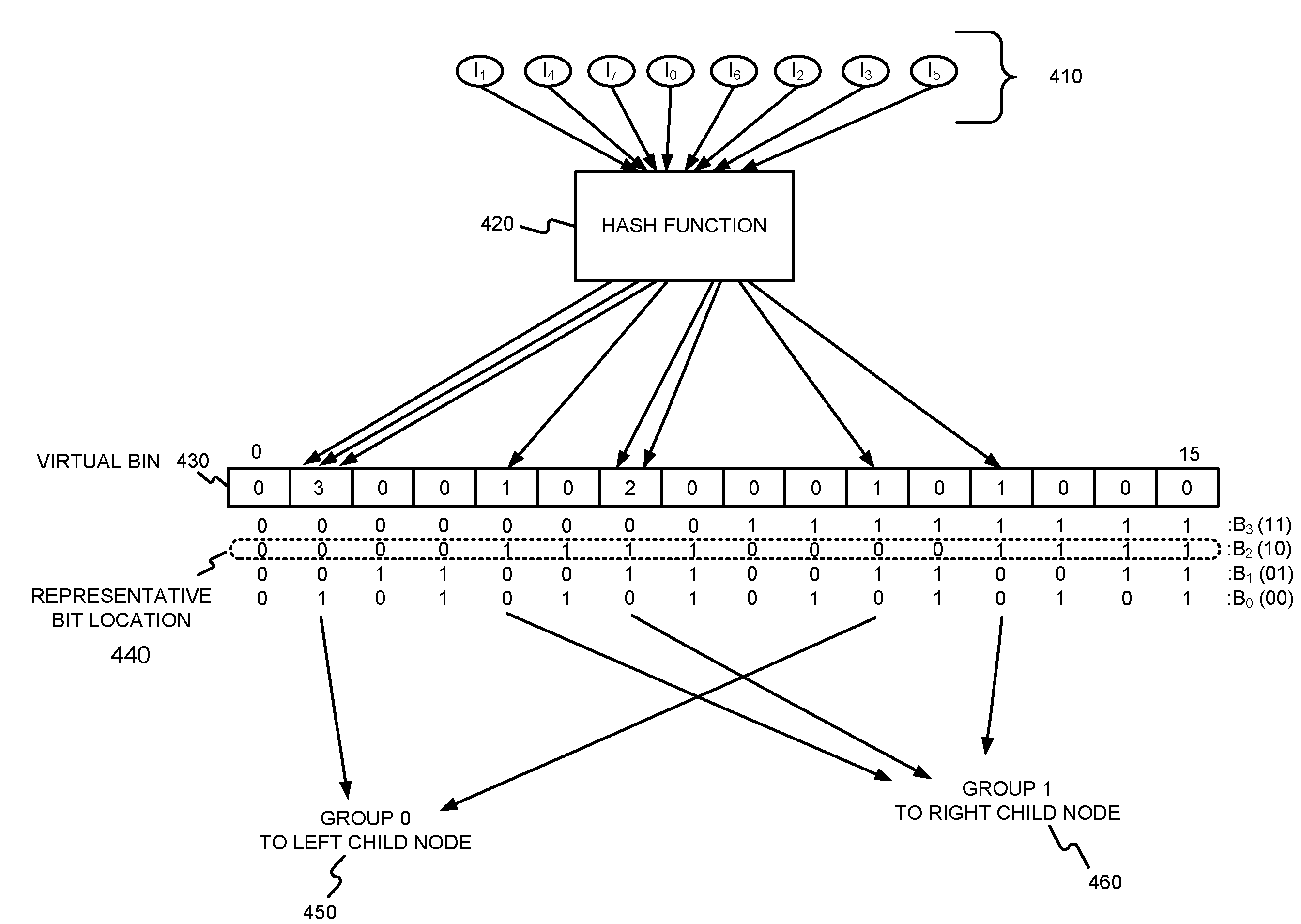
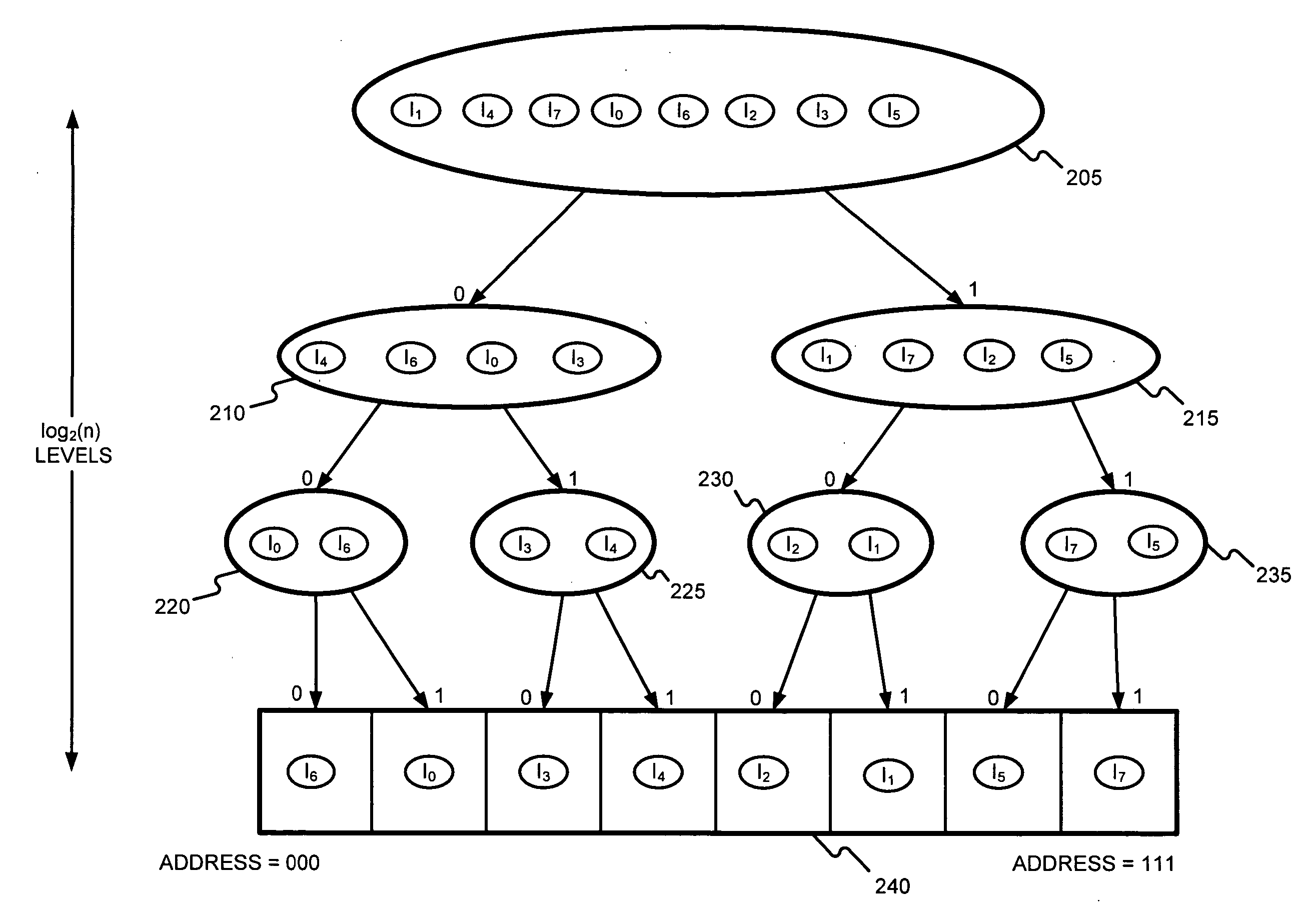
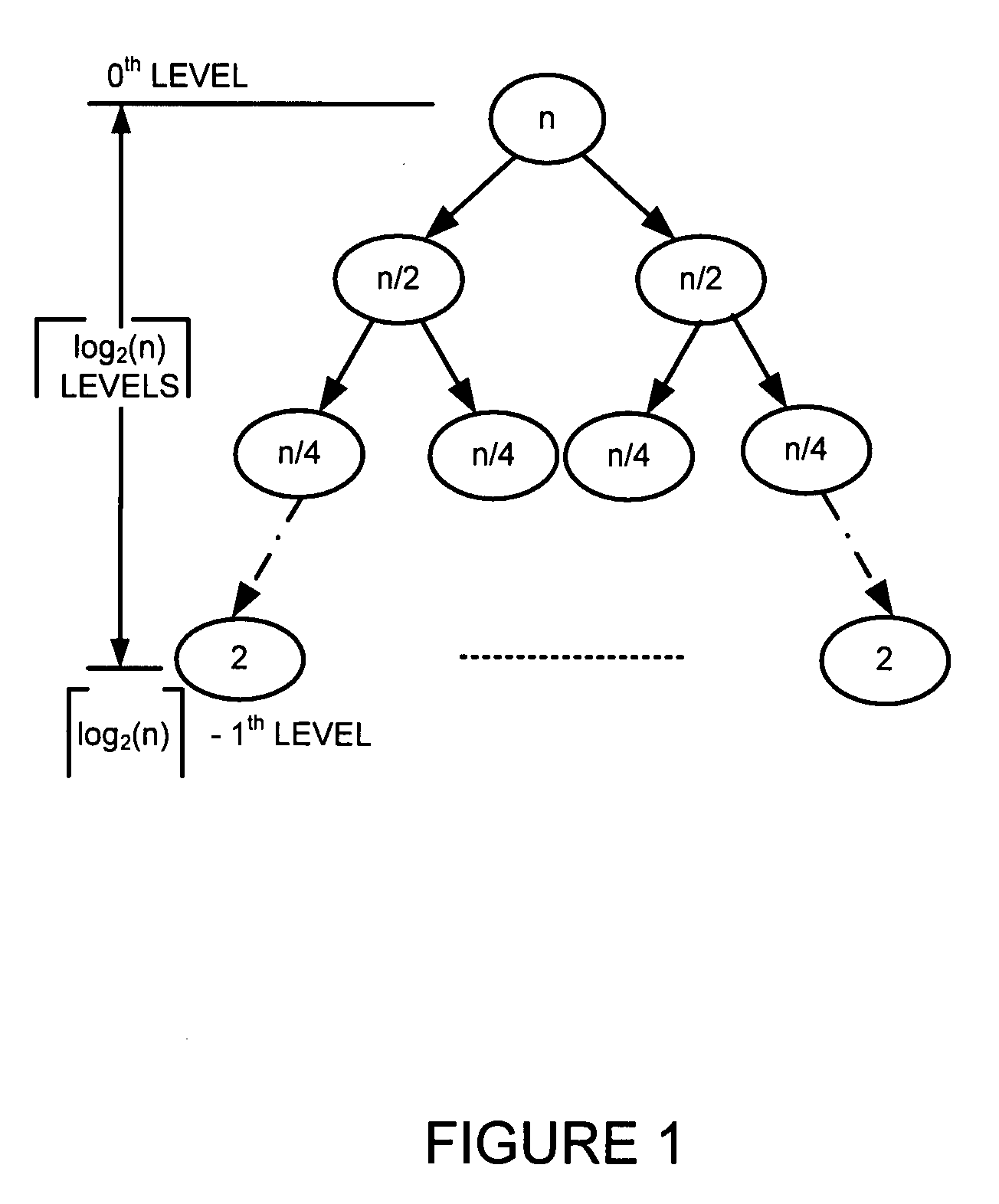
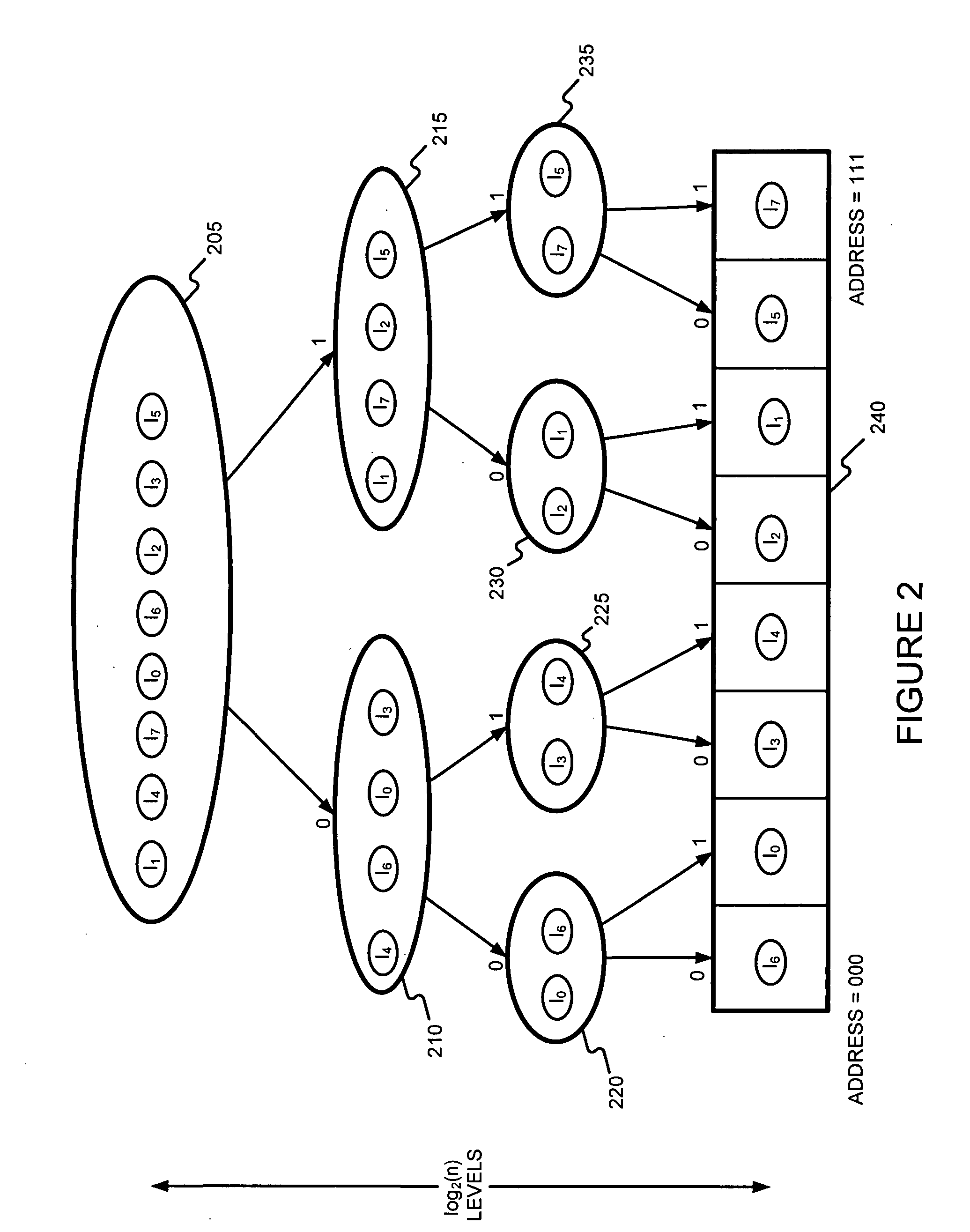
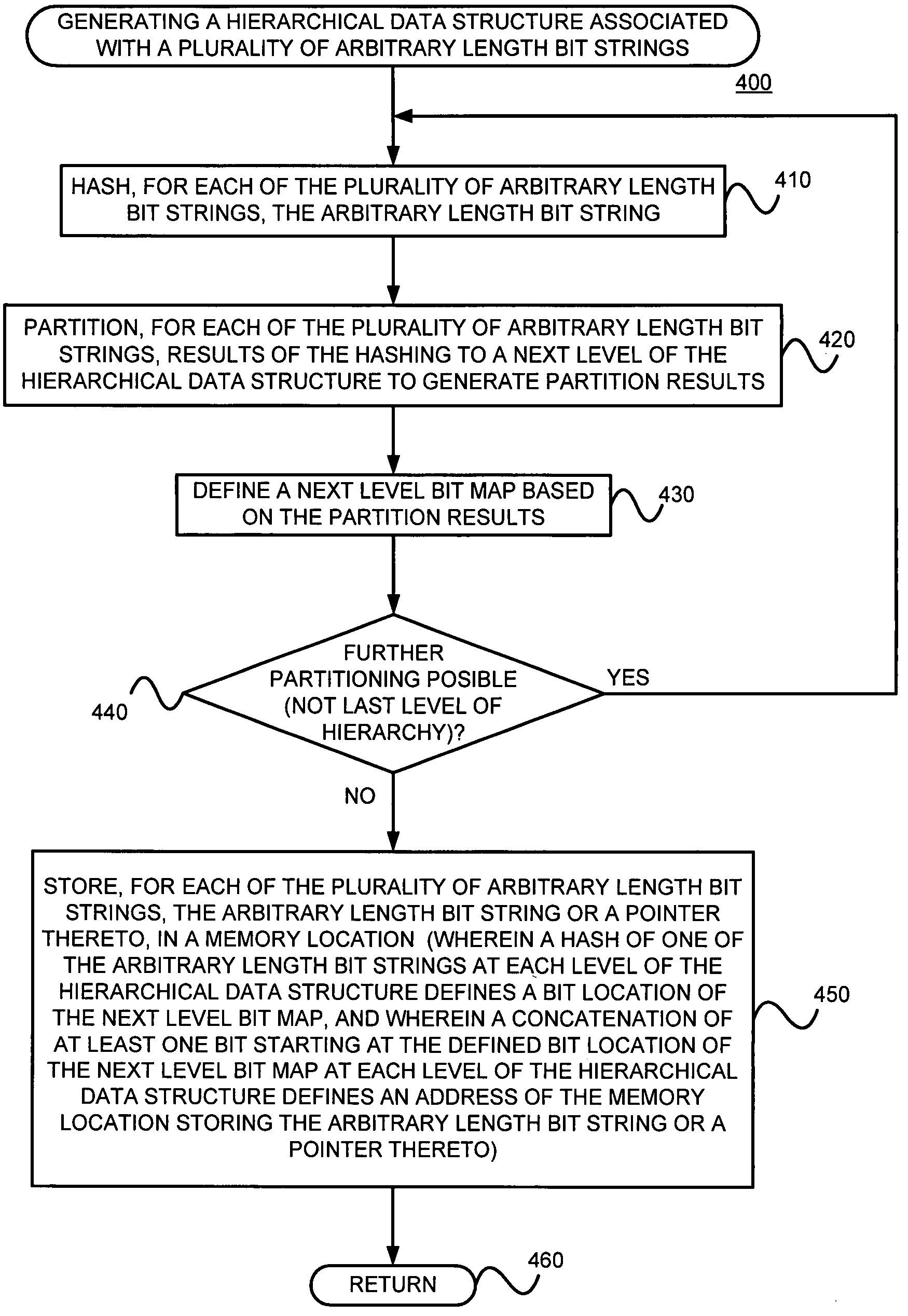
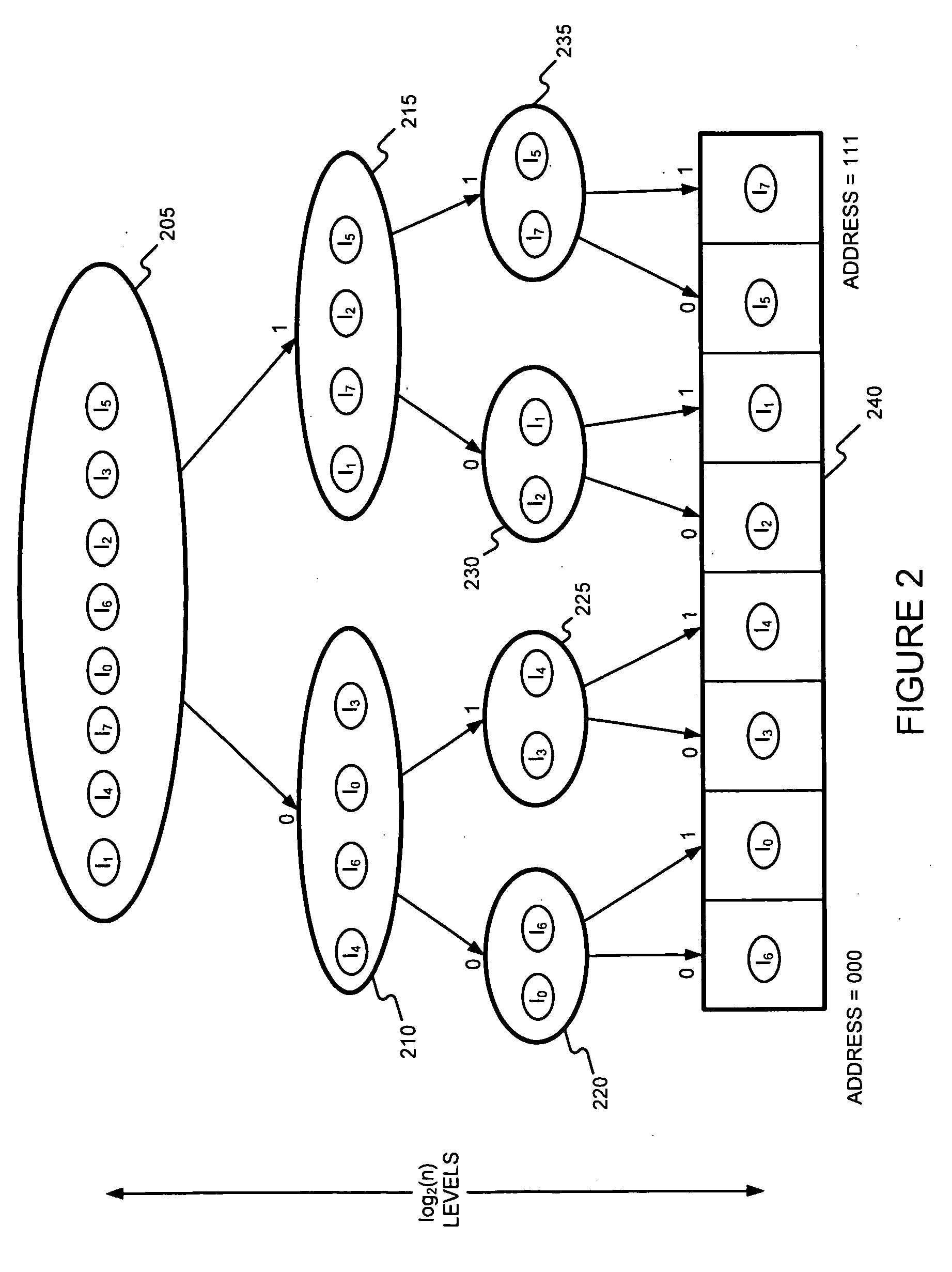
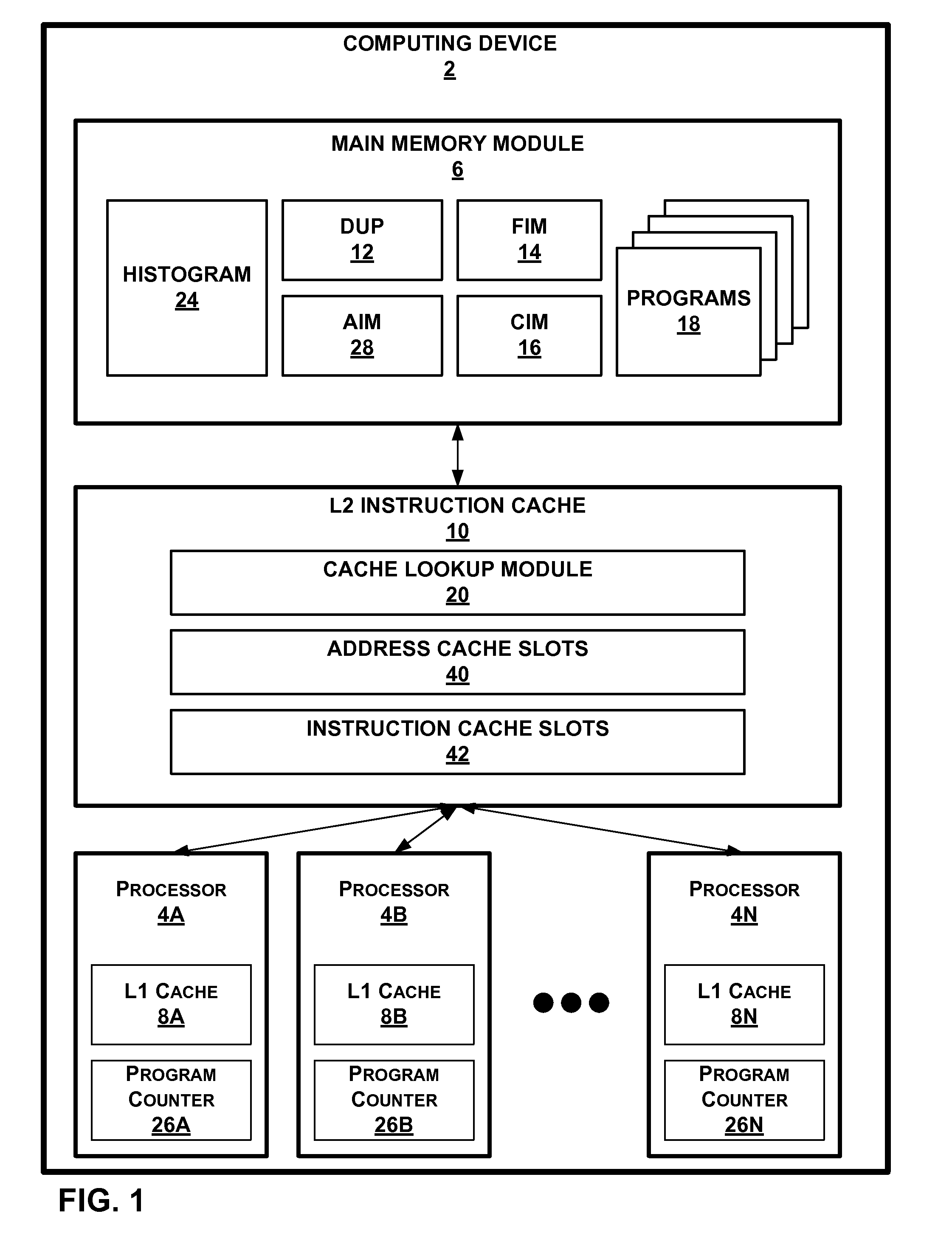
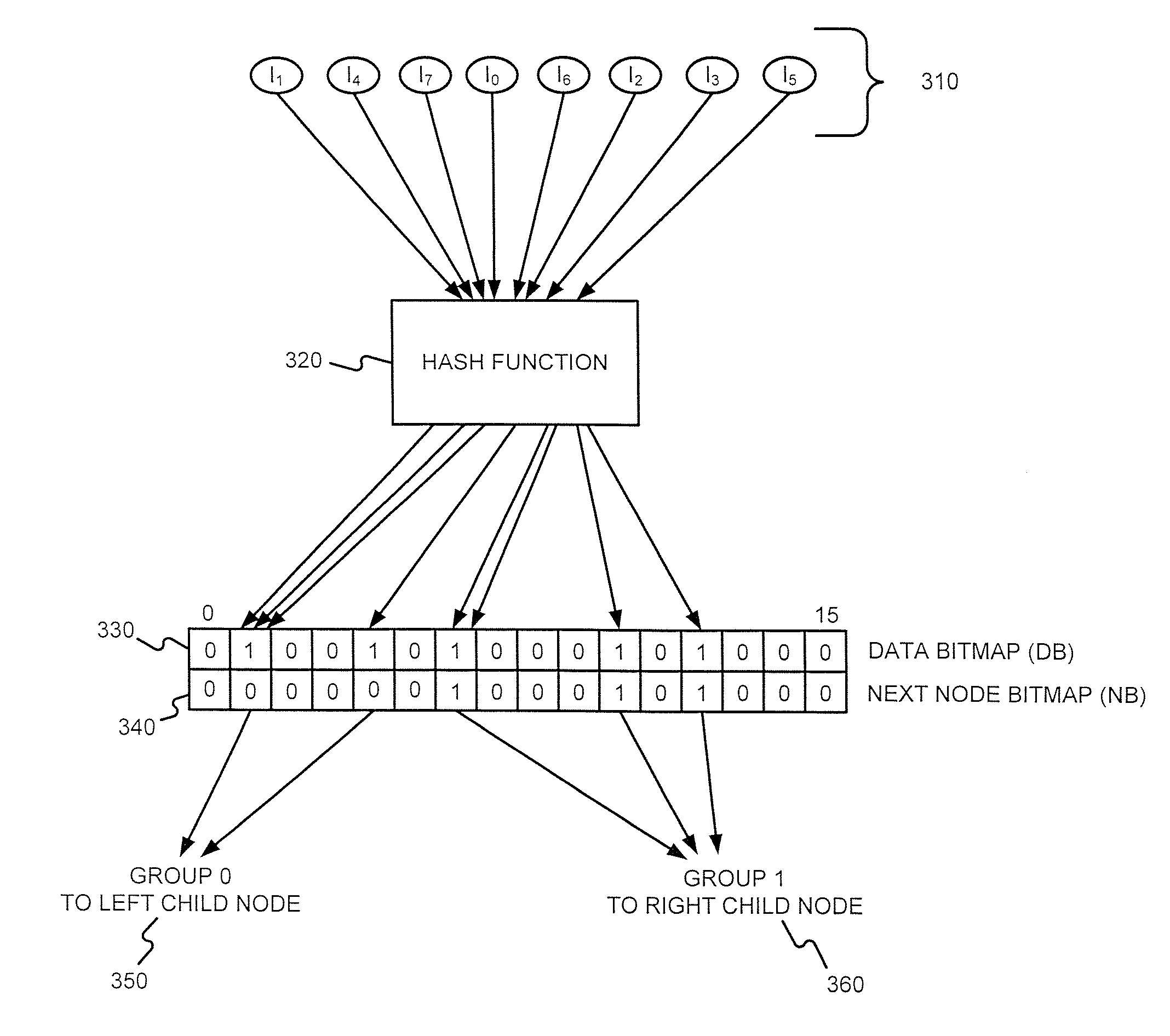
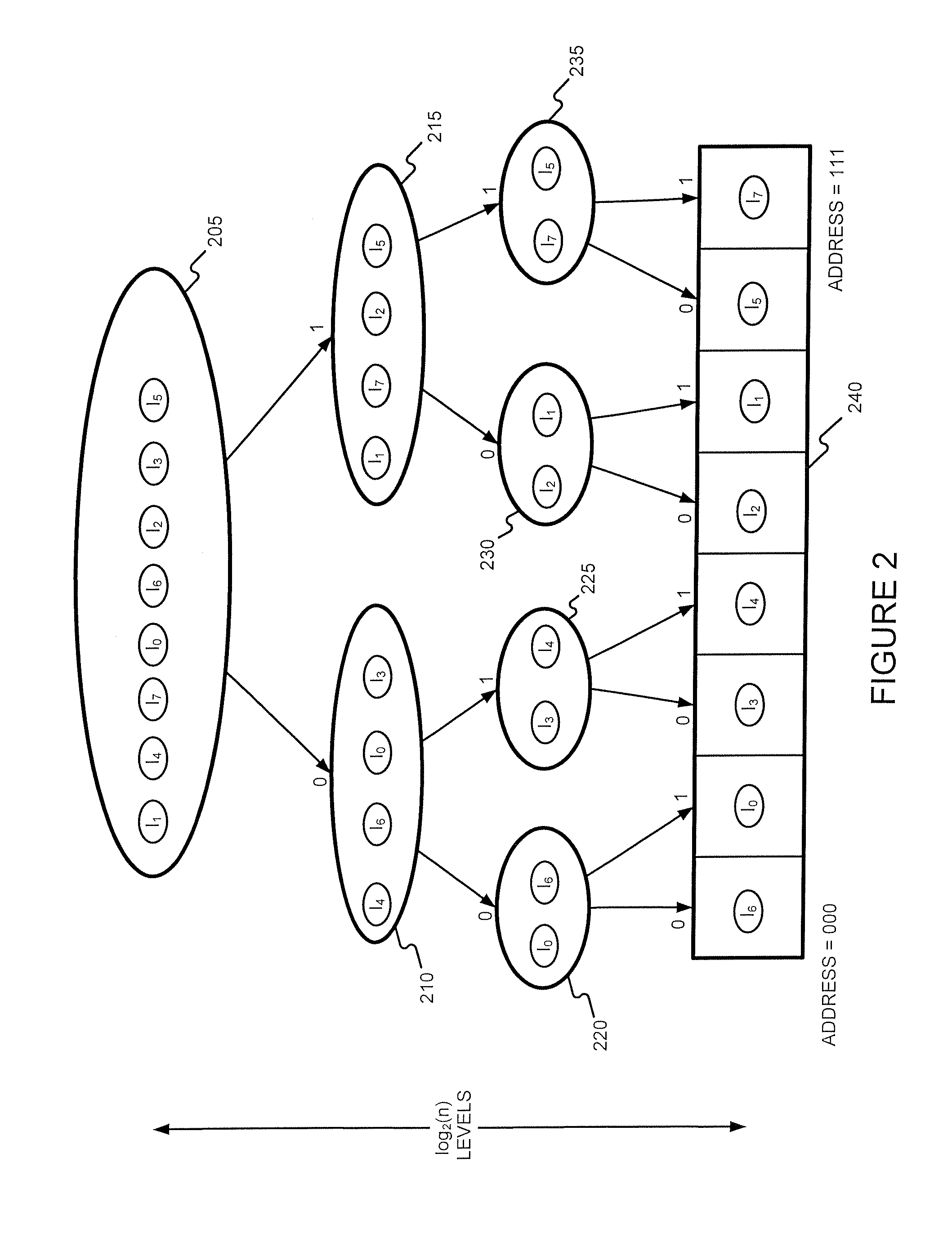
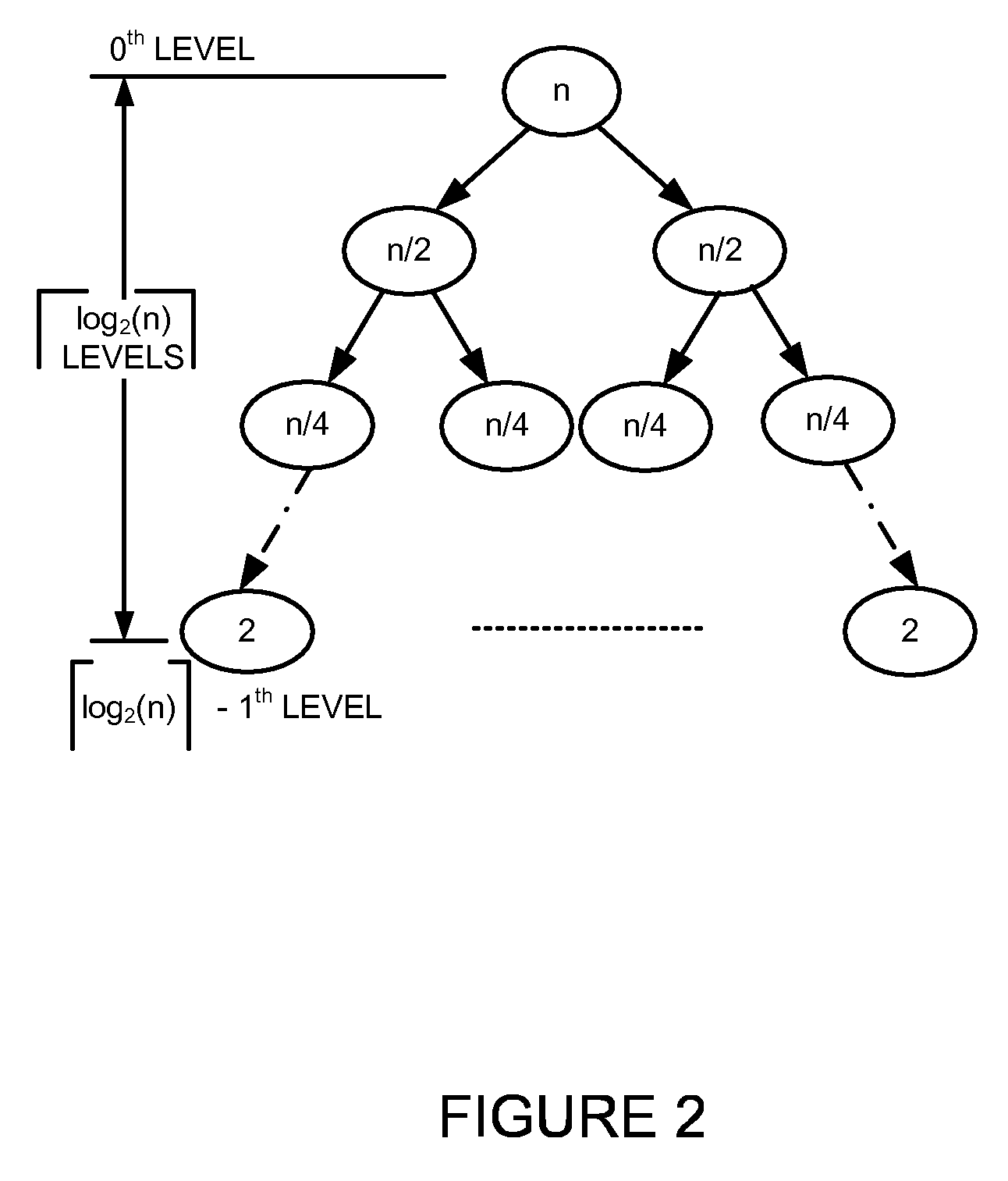
Generating a hierarchical data structure associated with a plurality of known arbitrary-length bit strings used for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit string
ActiveUS20080133583A1Easy to updateImprove search rateDigital data processing detailsComputer security arrangementsTheoretical computer sciencePerfect hash function
Generating and using a high-speed, scalable, and easily updateable data structure are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
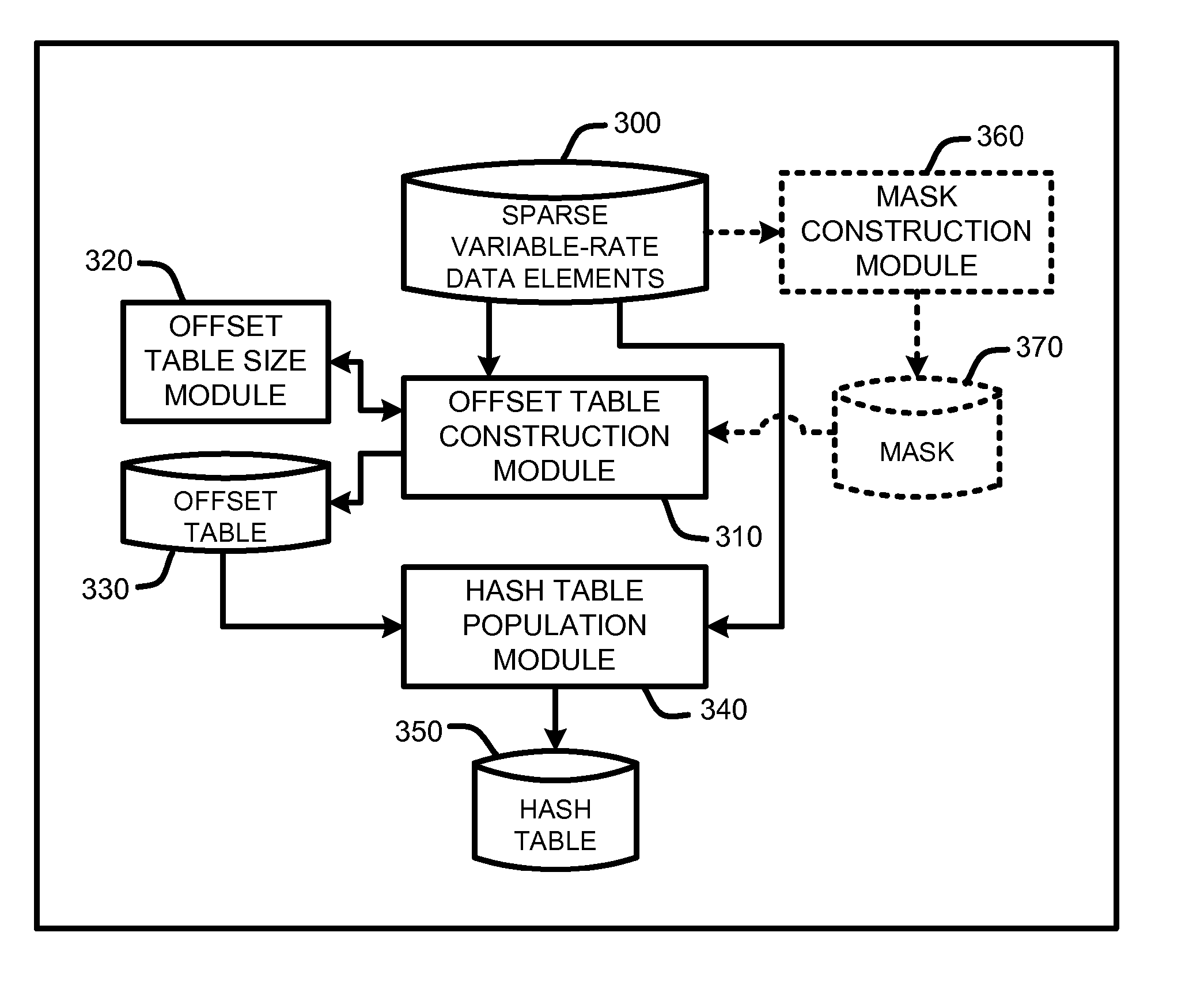
Perfect hashing of variably-sized data
InactiveUS20070245119A1Efficient random accessEliminate needDigital data information retrievalMemory adressing/allocation/relocationTheoretical computer sciencePerfect hash function
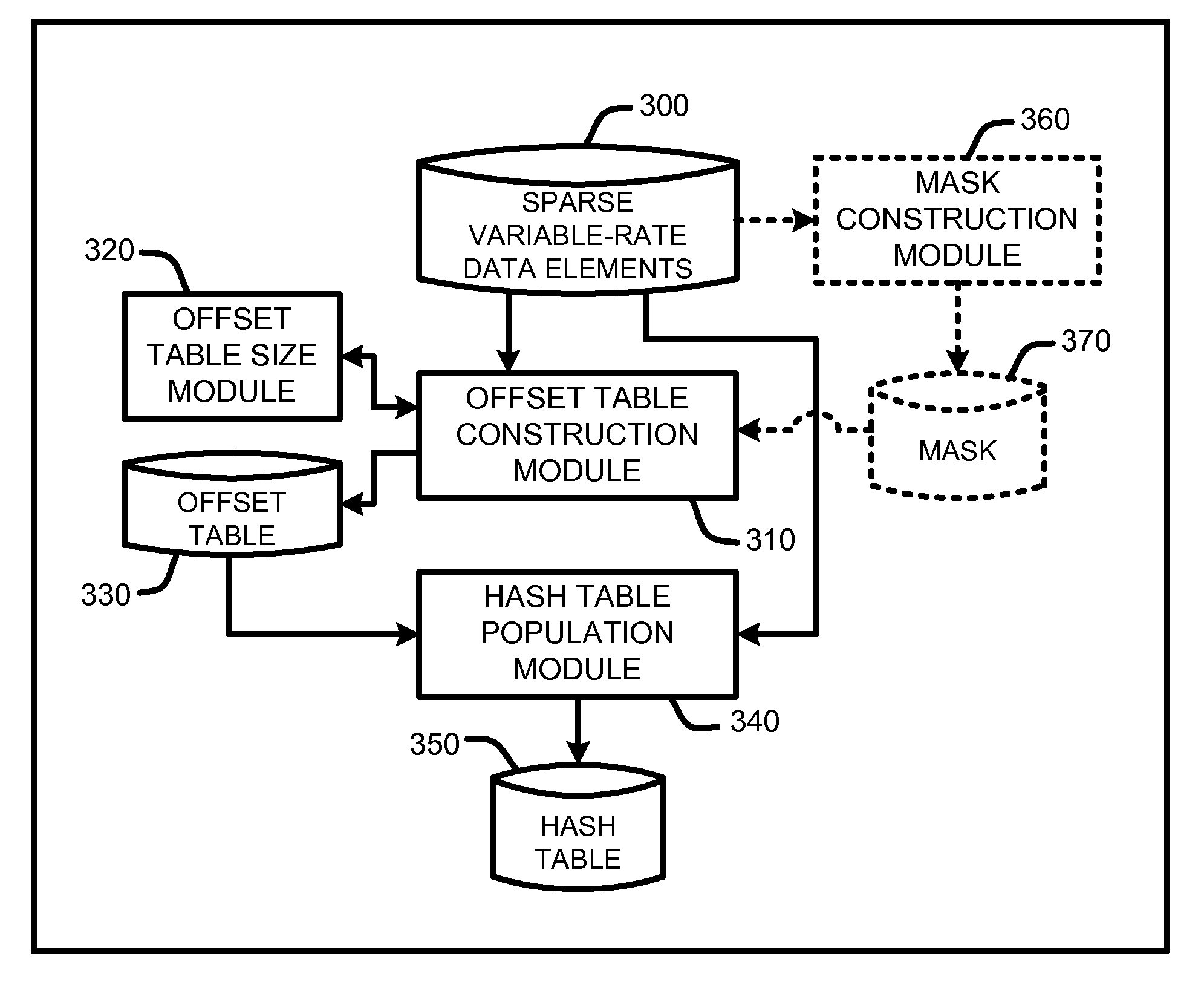
A “Variable-Rate Perfect Hasher” maps sparse variable-rate data of one or more dimensions into a hash table using a perfect hash function. In various embodiments, perfect hash tables are populated by first computing offset table address for each data point of a domain of sparse variable-rate data elements. Offset vectors are then computed for each offset table address based in part on the size of each data element by evaluating offset vectors in order of a sum of the data point addresses mapping to each offset vector. These offset vectors are then stored in the offset table. For each data point, the corresponding offset vector is then used to compute a hash table address. Data elements are then perfectly hashed into the hash table using the computed hash table addresses. The resulting hash tables support efficient random access of the variable-sized data elements stored therein.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for managing data objects of a data storage system
ActiveUS20100049735A1Digital data information retrievalSpecial data processing applicationsHash functionPerfect hash function
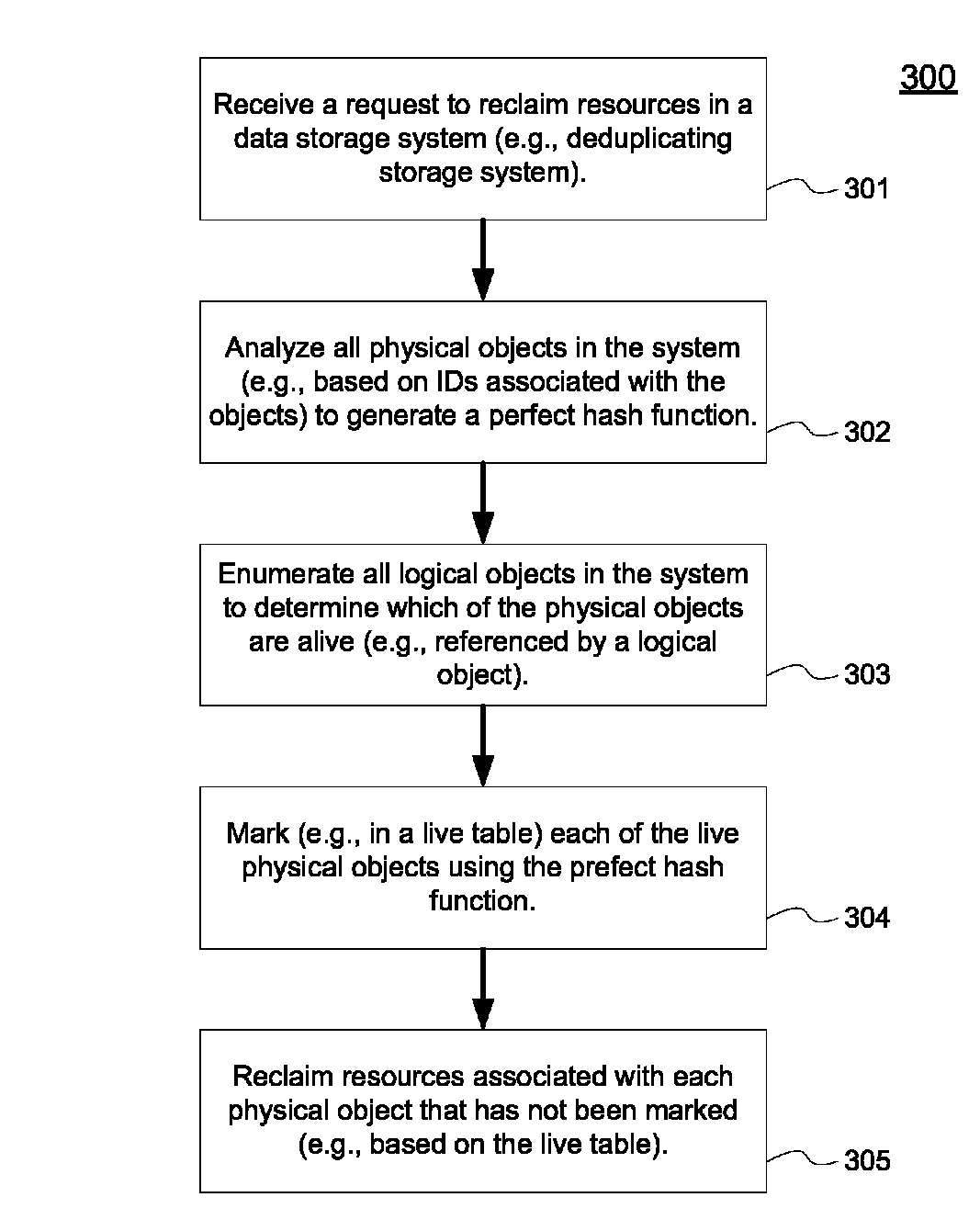
Techniques for managing data objects of a data storage system are described herein. According to one embodiment, a perfect hash function is generated for data objects stored in a data storage system. For each of the data objects, a hash operation is performed using the perfect hash function to indicate whether the respective data object is alive. Resources associated with the respective data object is reclaimed if it is determined that the respective data object is not alive based on a result of the hash operation using the perfect hash function, where the reclaimed resources are released back to the data storage system as free resources. Other methods and apparatuses are also described.
Owner:EMC IP HLDG CO LLC
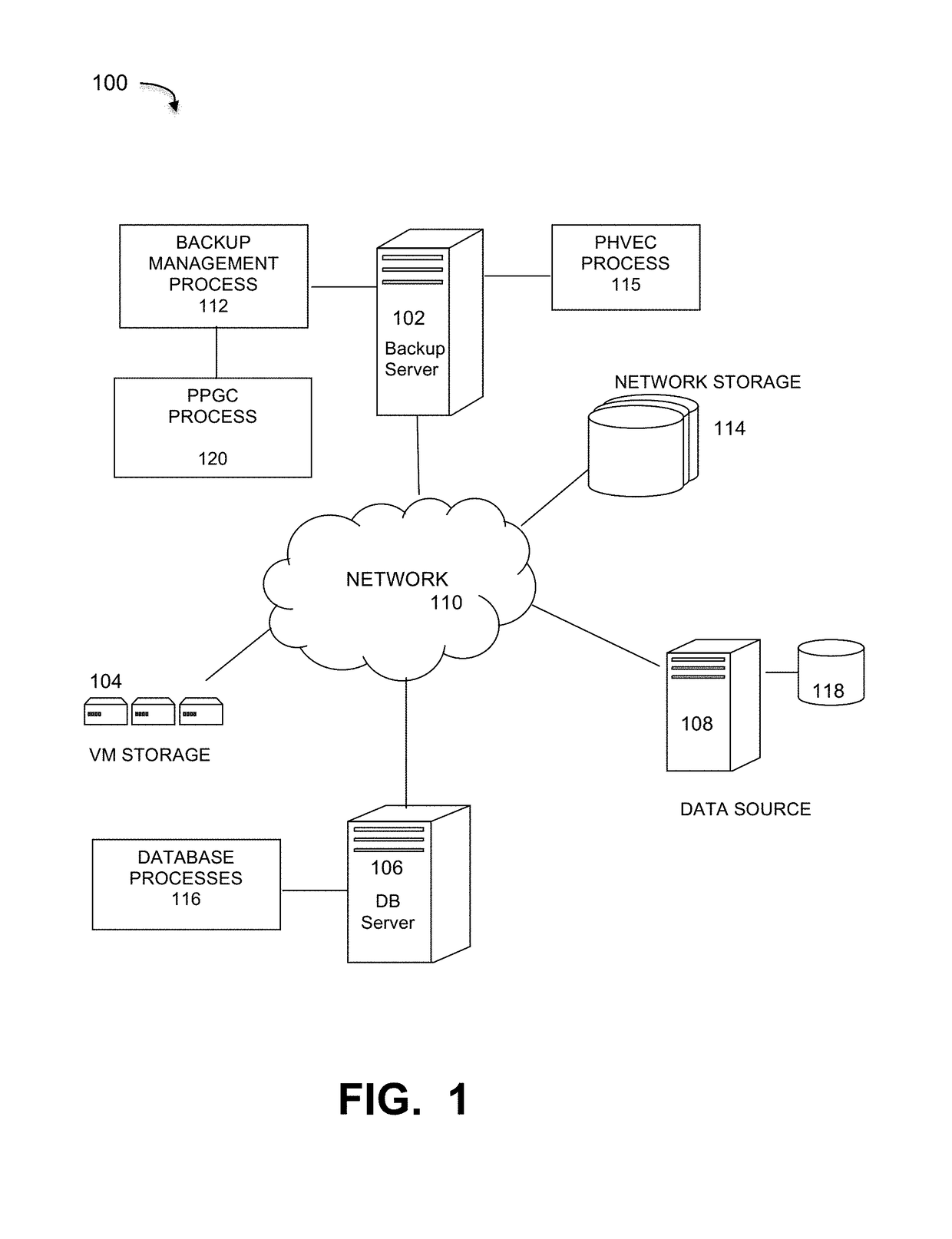
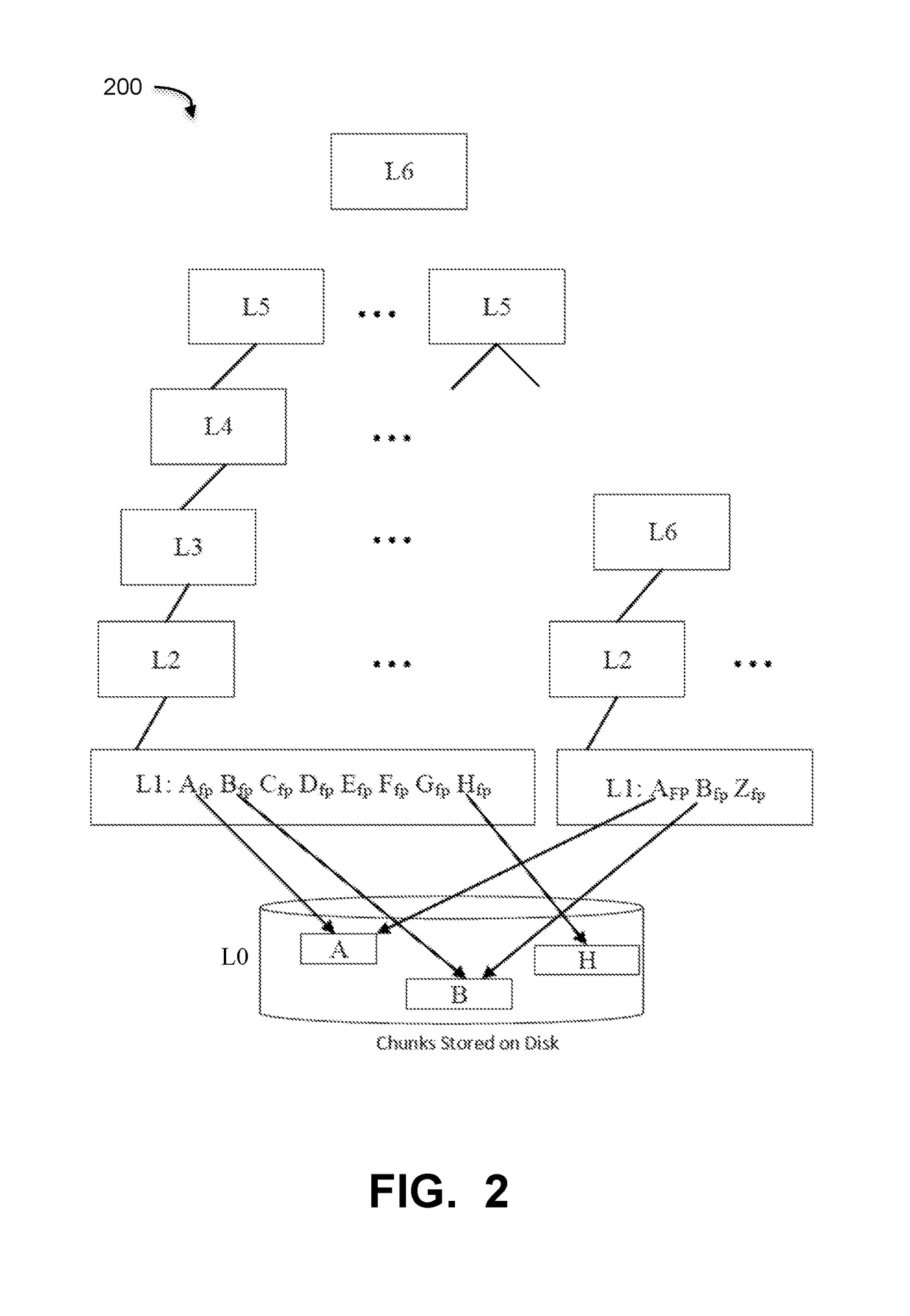
Efficient physical garbage collection using a perfect hash vector
ActiveUS10108543B1Memory architecture accessing/allocationInput/output to record carriersWaste collectionPerfect hash function
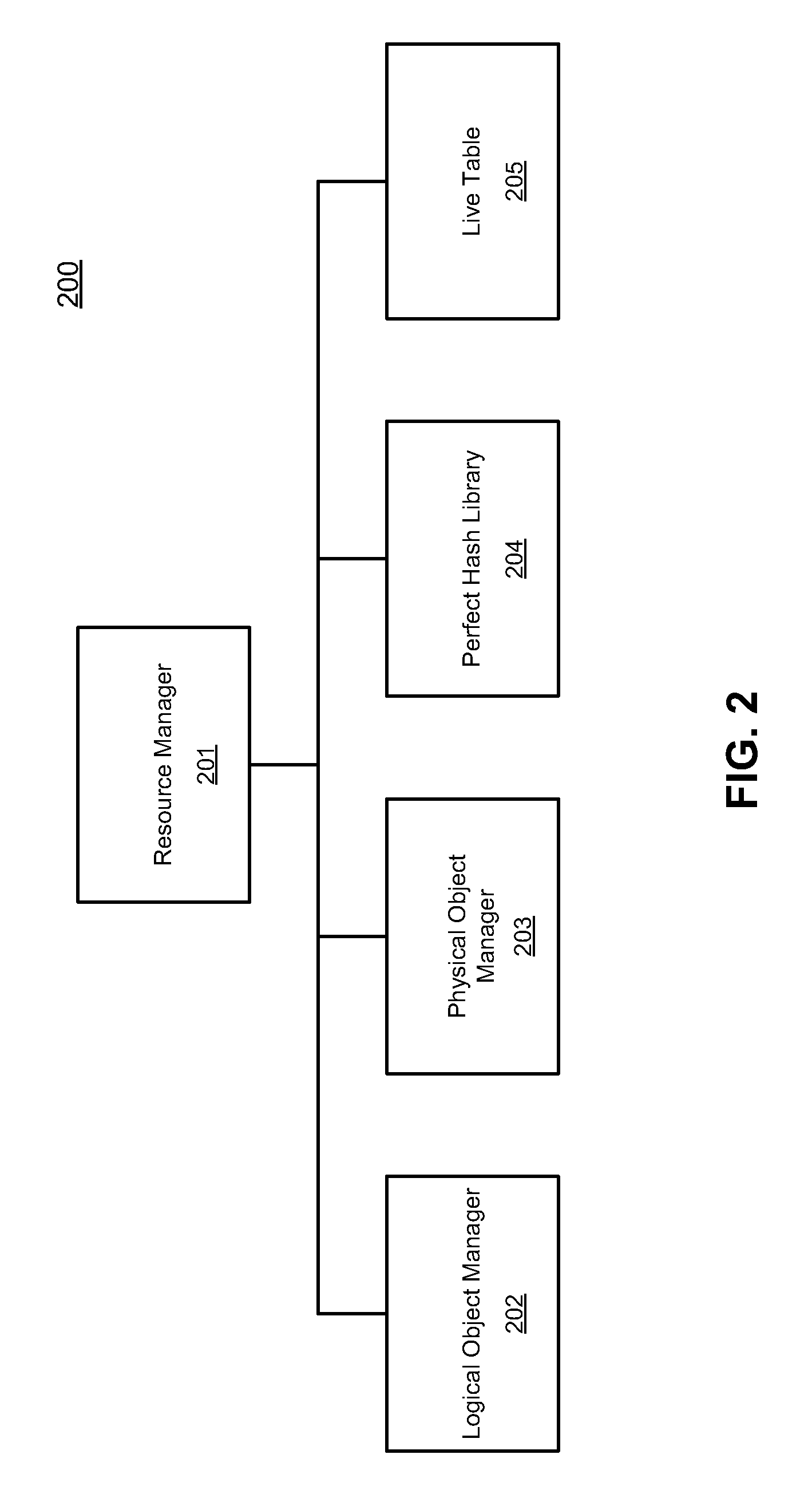
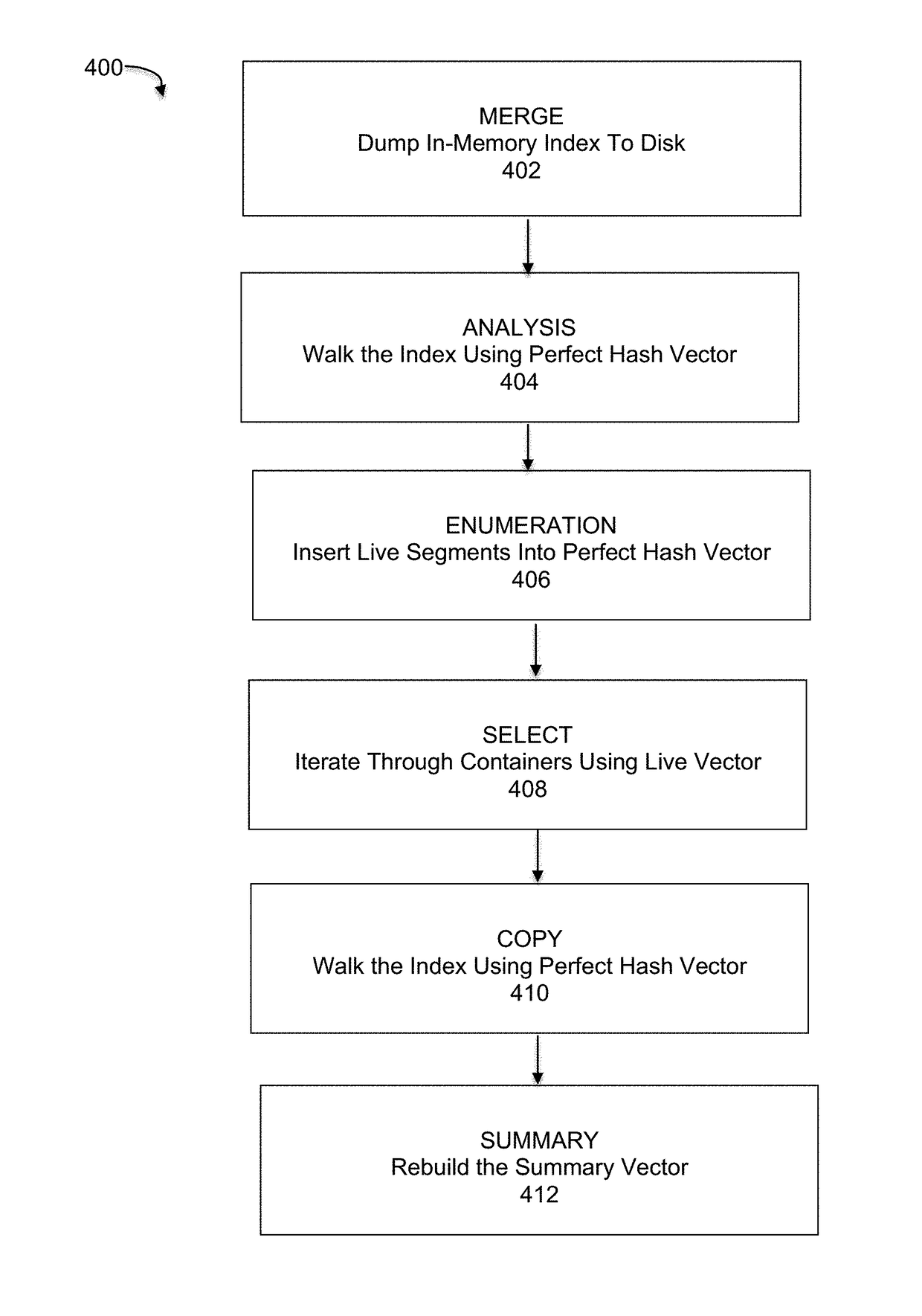
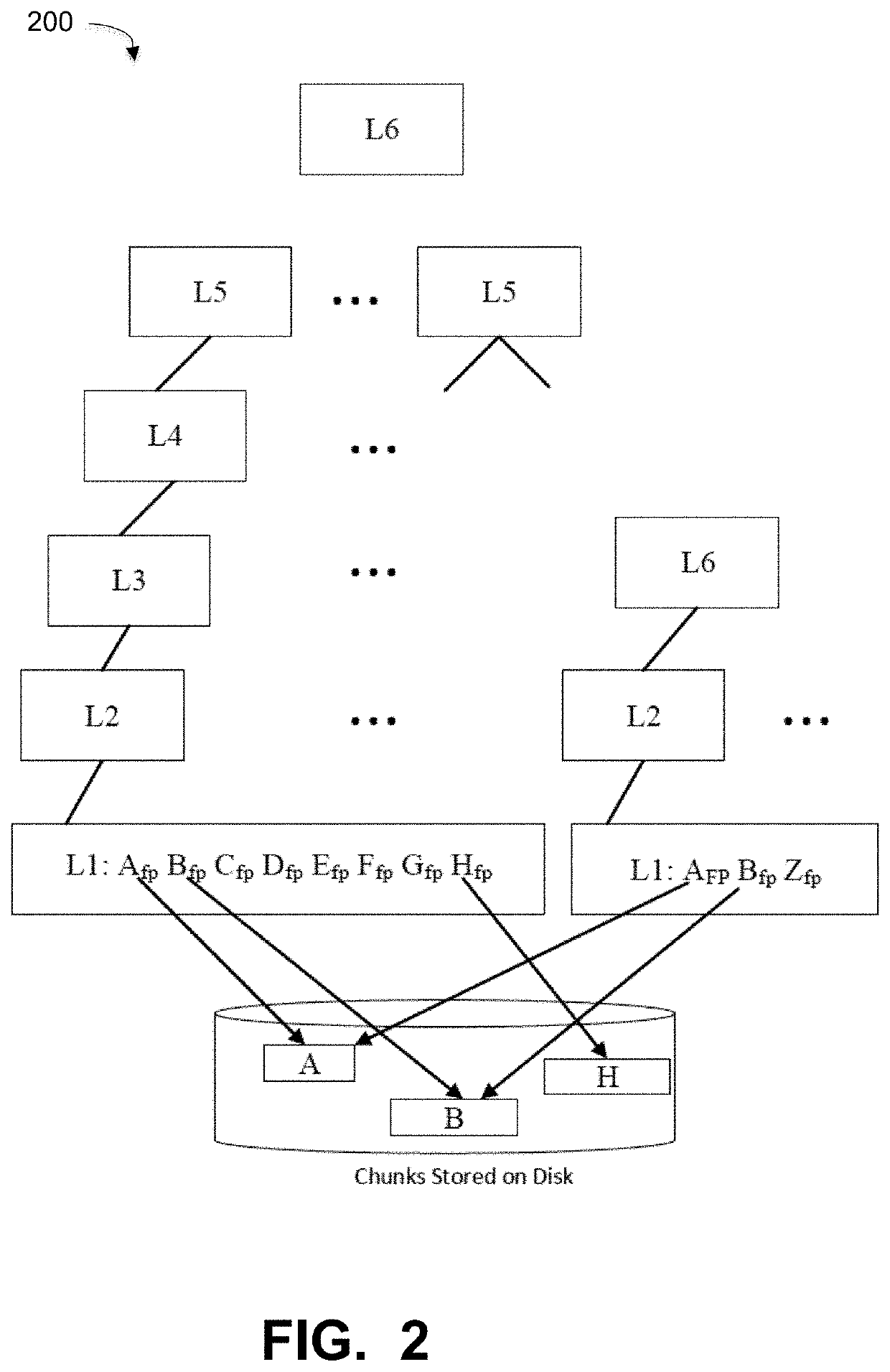
Embodiments are directed to perfect physical garbage collection (PPGC) process that uses a perfect hash vector instead of large Bloom filters of the regular physical garbage collection process for the live and live instance vectors and consolidates both into a single live vector using the perfect hash vector. A method of PPGC includes an analysis phase walking an index containing a mapping of fingerprints to a container ID for a plurality of containers and building a perfect hash function for a walk vector and a live vector, wherein the live vector uses a perfect hash vector, an enumeration phase inserting live segments in memory into the perfect hash vector, a select phase traversing the plurality of containers and selecting containers that meet a defined liveness threshold and a copy phase copying live segments out of the selected containers.
Owner:EMC IP HLDG CO LLC
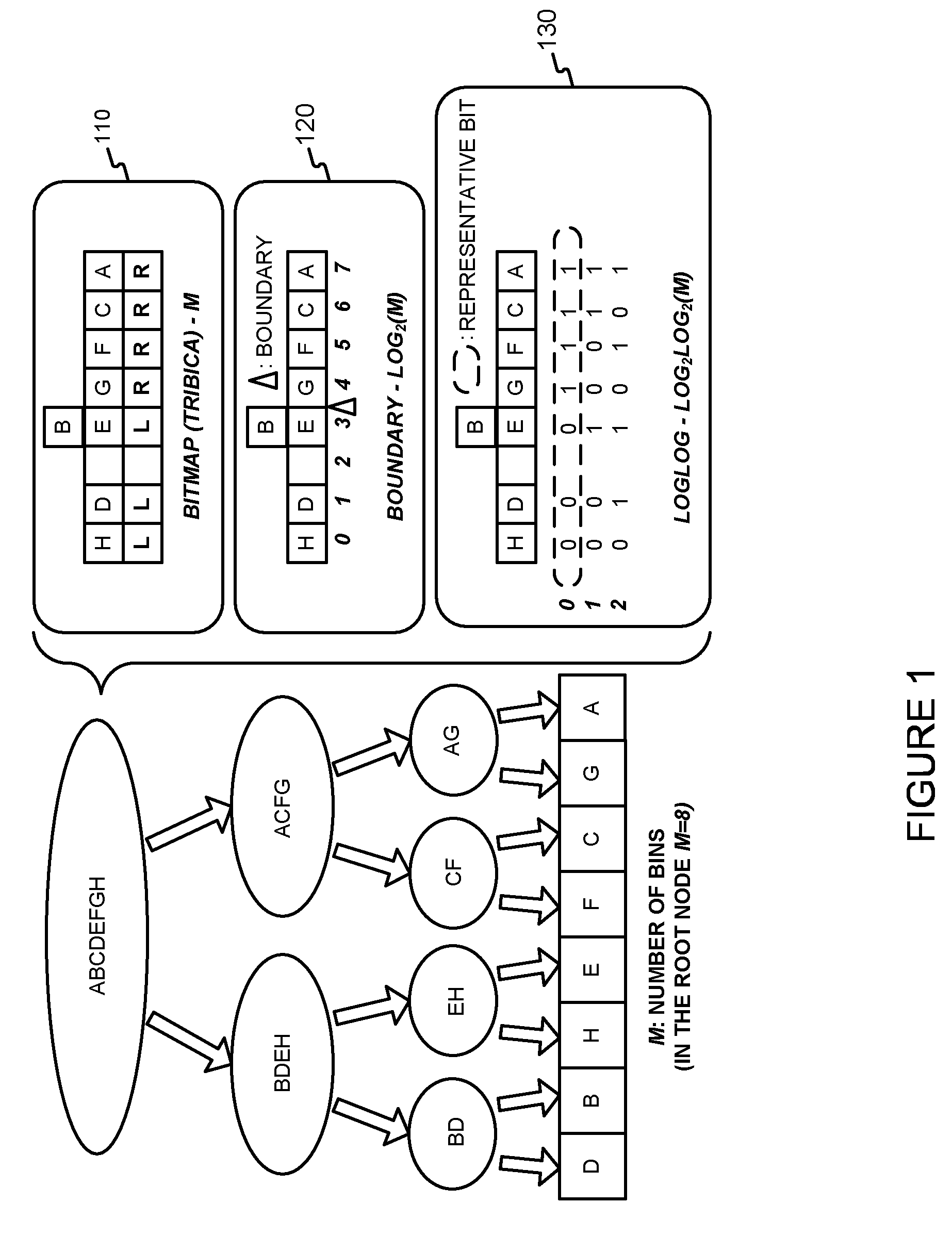
Generating a log-log hash-based hierarchical data structure associated with a plurality of known arbitrary-length bit strings used for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit strings
InactiveUS20100199066A1Easy to updateEasily achieve DPIDigital data information retrievalCode conversionPerfect hash functionTheoretical computer science
Generating and using a high-speed, scalable and easily updateable data structures are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Memory efficient perfect hashing for large records
ActiveUS20200117546A1Redundant operation error correctionSpecial data processing applicationsHash functionPerfect hash function
Embodiments for a memory efficient perfect hashing for large records. A container ID set is divided into multiple fixed range sizes. These ranges are then mapped into perfect hash buckets until each bucket is filled to uniformly distribute the container IDs across different perfect hash buckets so that the number of CIDs in every perfect hash bucket is the same or nearly the same. Individual perfect hash functions are created for each perfect hash bucket. With container IDs as keys, the process maps n keys to n positions to reduce any extra memory overhead. The perfect hash function is implemented using a compress, hash, displace (CHD) algorithm using two levels of hash functions. The level 1 hash functions divides the keys into multiple internal buckets with a defined average number of keys per bucket. The CHD algorithm iteratively tries different level 2 hash variables to achieve collision-free mapping.
Owner:EMC IP HLDG CO LLC
Method and apparatus for finding a perfect hash function and making minimal hash table for a given set of keys
InactiveUS20060248079A1Digital data information retrievalDigital data processing detailsTheoretical computer sciencePerfect hash function
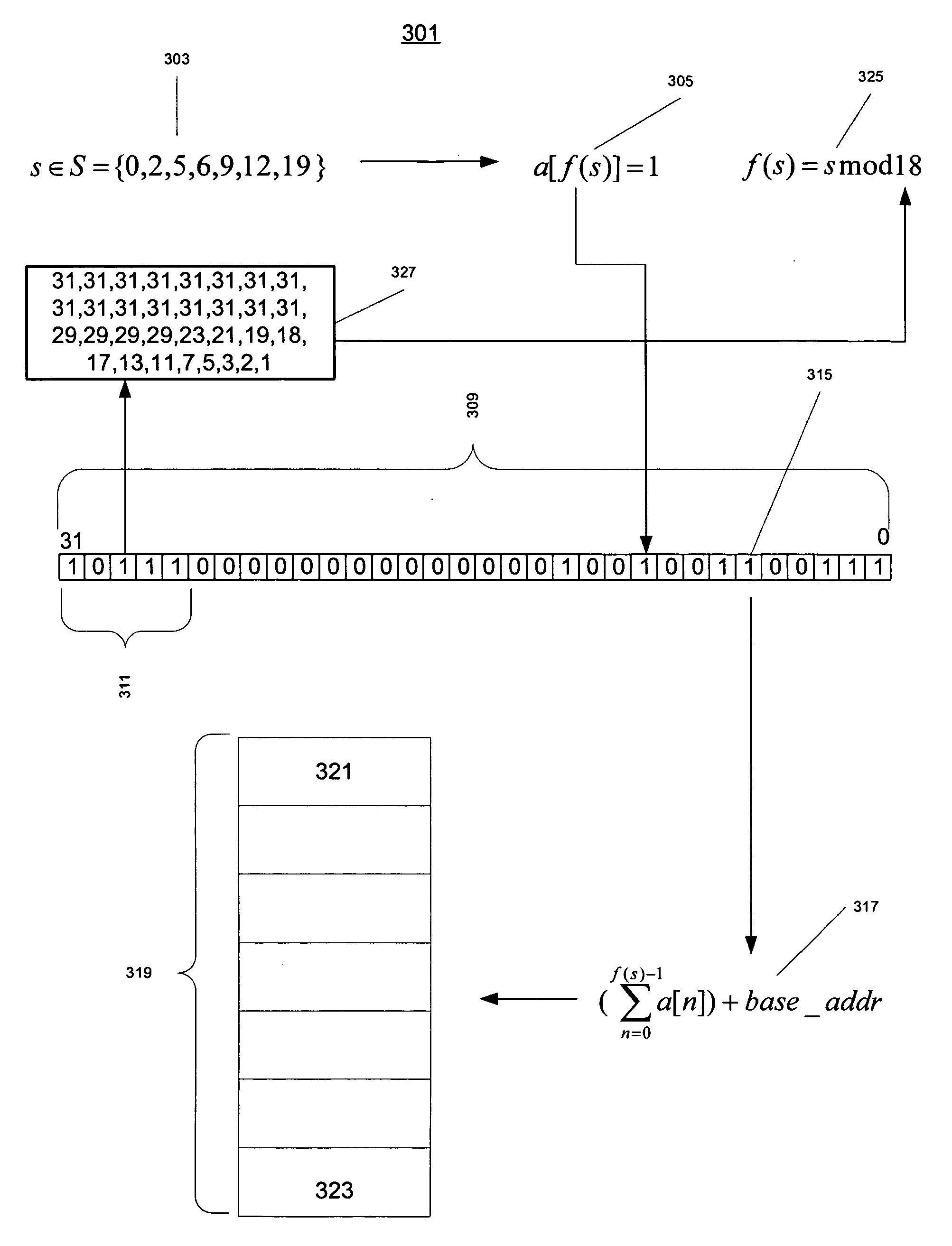
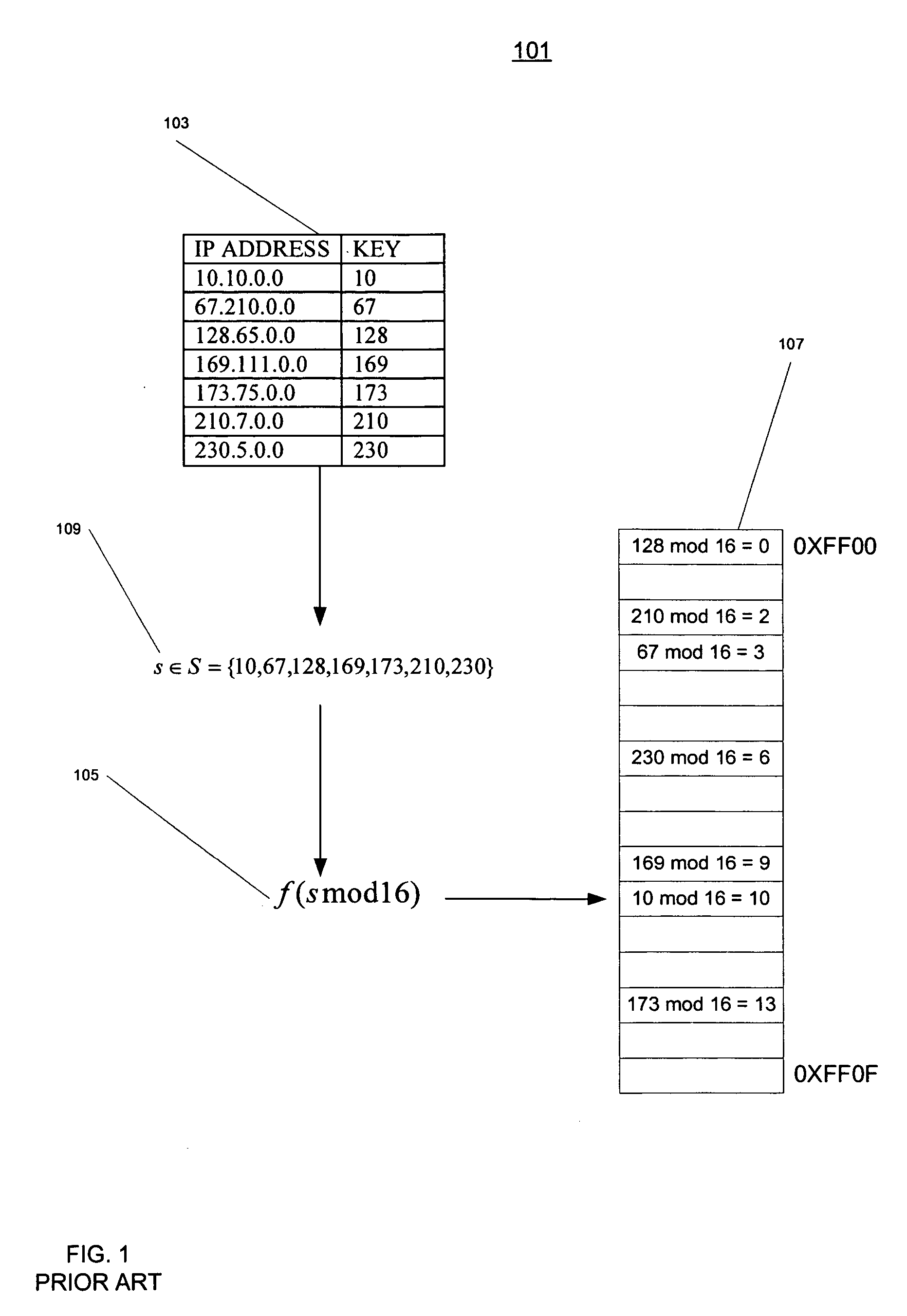
A representation used in a computer system to represent a set of data items that correspond to and are accessible by means of a set of keys. The representation includes an array of the data items and a bit string associated with the array. Each key is mapped onto a bit of the bit string by means of a hash function that is perfect for the set of keys. The mapped bit is set. The data item corresponding to the key has a position in the array that corresponds to the position of the bit for the key in the bit string. Methods for reading and writing the representation are disclosed as well as a technique based on the mod operation and a set of co-prime numbers for finding a perfect hash function for a given set of keys.
Owner:FREESCALE SEMICON INC
Detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit strings using a hierarchical data structure
ActiveUS20080111716A1Easy to updateImprove search rateDigital data information retrievalMemory loss protectionTheoretical computer sciencePerfect hash function
Generating and using a high-speed, scalable, and easily updateable data structure are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Method and apparatus for managing data objects of a data storage system
ActiveUS8316064B2Digital data information retrievalMemory adressing/allocation/relocationHash functionPerfect hash function
Techniques for managing data objects of a data storage system are described herein. According to one embodiment, a perfect hash function is generated for data objects stored in a data storage system. For each of the data objects, a hash operation is performed using the perfect hash function to indicate whether the respective data object is alive. Resources associated with the respective data object is reclaimed if it is determined that the respective data object is not alive based on a result of the hash operation using the perfect hash function, where the reclaimed resources are released back to the data storage system as free resources. Other methods and apparatuses are also described.
Owner:EMC IP HLDG CO LLC
Generating a hierarchical data structure associated with a plurality of known arbitrary-length bit strings used for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit string
ActiveUS7805460B2Easy to updateEasily achieve DPIDigital data processing detailsComputer security arrangementsPerfect hash functionTheoretical computer science
Generating and using a high-speed, scalable, and easily updateable data structure are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Recursively partitioned static IP router tables
InactiveUS7990979B2Less accessibleLess memory requiredData switching by path configurationIp routerPerfect hash function
Owner:UNIV OF FLORIDA RES FOUNDATION INC
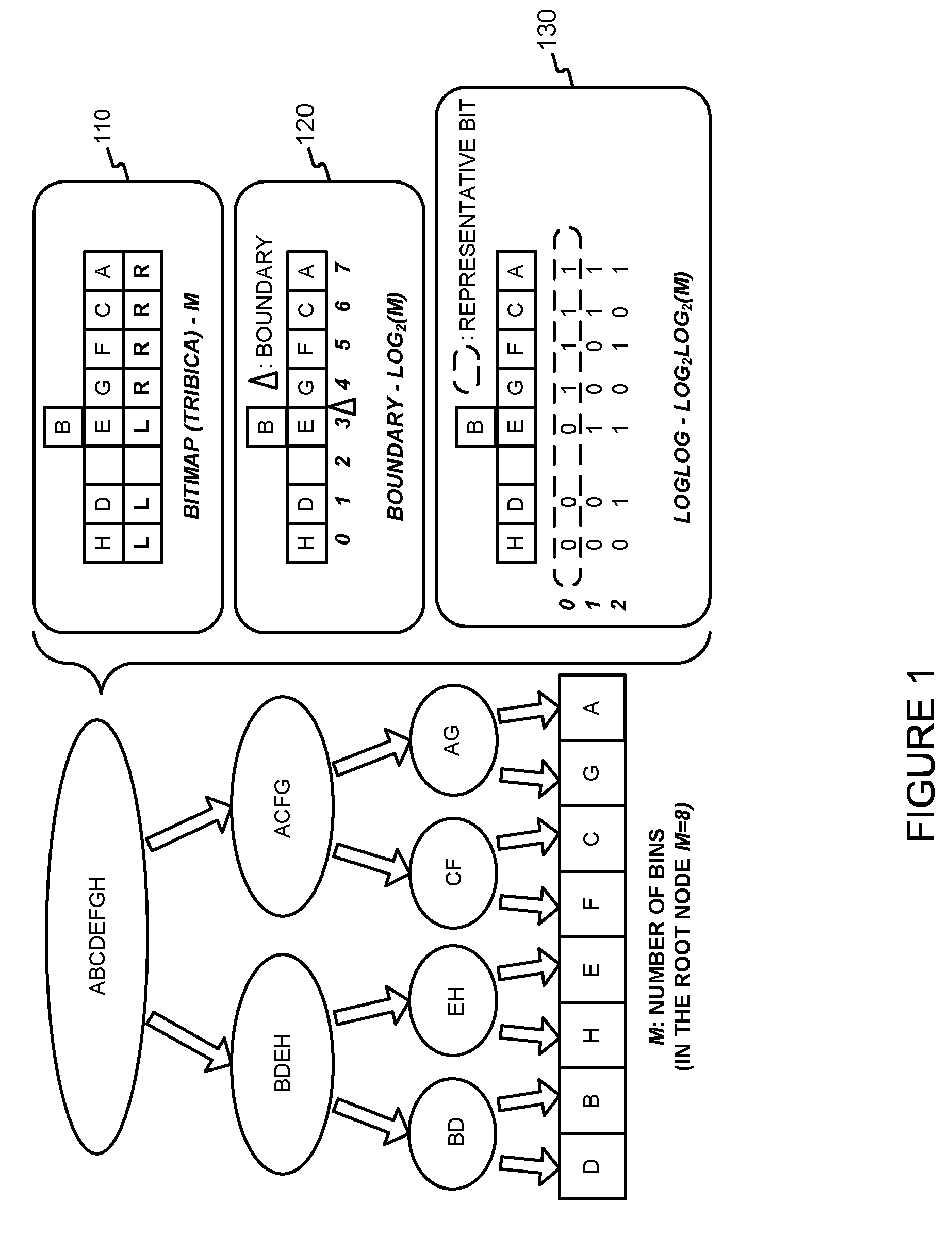
Generating a boundary hash-based hierarchical data structure associated with a plurality of known arbitrary-length bit strings and using the generated hierarchical data structure for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit springs
InactiveUS7868792B2Efficient representationEasy constructionDigital data information retrievalCode conversionAlgorithmTheoretical computer science
A high-speed, space-efficient, scalable and easily updateable data boundary hash-based structure is generated and used. The proposed boundary hash-based data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Systems and methods for implementing dynamically configurable perfect hash tables
ActiveUS9384145B2Memory adressing/allocation/relocationComputation using denominational number representationComputer hardwarePerfect hash function
Owner:ORACLE INT CORP
Perfect hashing of variably-sized data
InactiveUS7965297B2Eliminate needEfficient accessDigital data information retrievalMemory adressing/allocation/relocationTheoretical computer sciencePerfect hash function
Owner:MICROSOFT TECH LICENSING LLC
Generating a boundary hash-based hierarchical data structure associated with a plurality of known arbitrary-length bit strings and using the generated hierarchical data structure for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit strings
InactiveUS20100194608A1Efficient representationEasy constructionDigital data information retrievalCode conversionTheoretical computer sciencePerfect hash function
A high-speed, space-efficient, scalable and easily updateable data boundary hash-based structure is generated and used. The proposed boundary hash-based data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
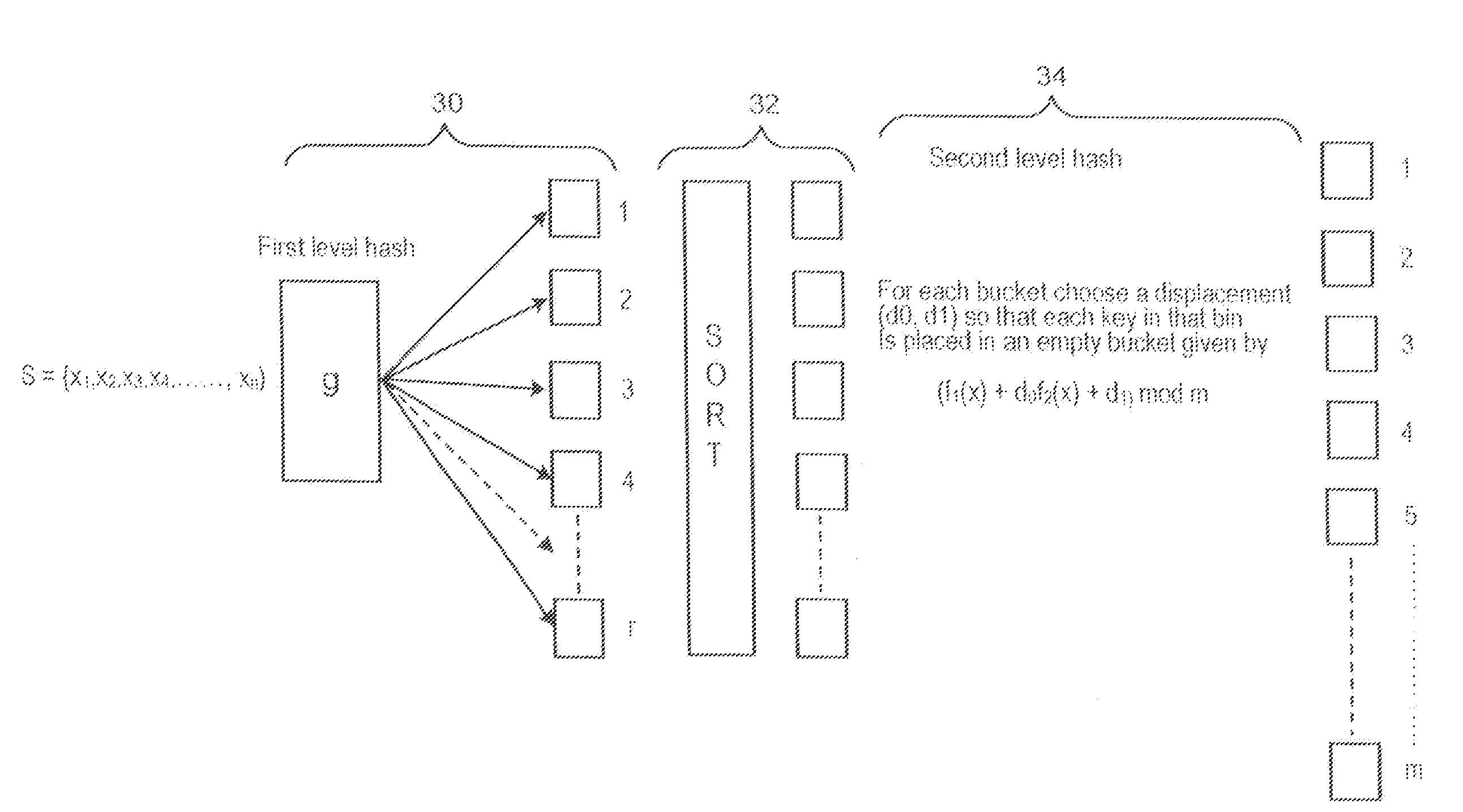
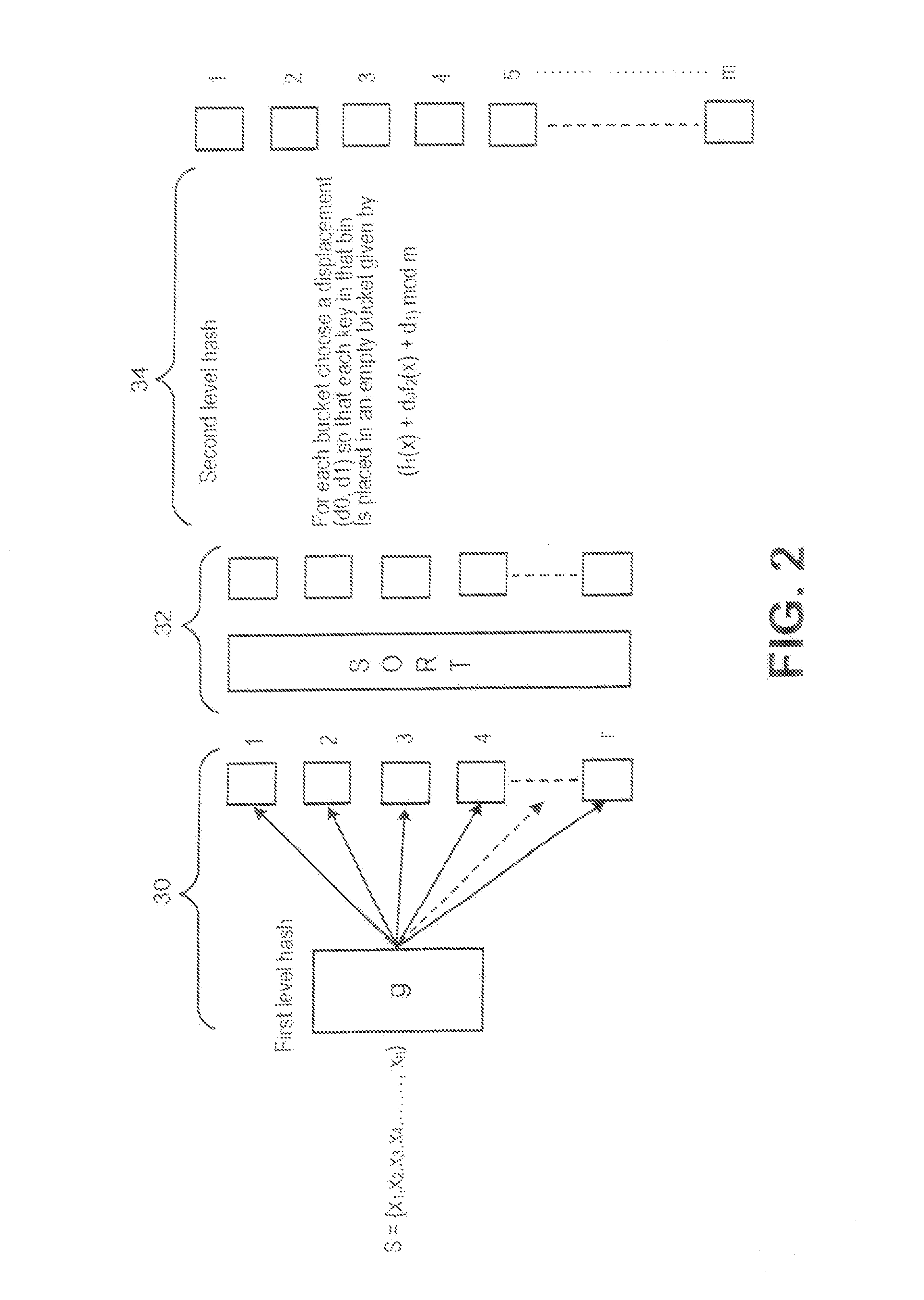
Secure perfect hash function
InactiveUS20160359631A1Digital data information retrievalUser identity/authority verificationComputer hardwareCryptographic hash function
A secure perfect hash function that has properties similar to those of cryptographic hash functions without compromising features of a perfect hash function such as speed and collision-free outputs is provided. A cryptographic hash function is utilized to process the set S and the. output is divided into three sub-outputs of required length. Each output can now be treated as a separate hash function (g(x), f1(x), f2(x)), S is split into r buckets Bi, 0≦i<r, using the hash function g. Buckets Bi are permuted in a pseudorandom fashion. For each bucket Bi, a displacement pair (d0, d1) is chosen randomly from the sequence {(0,0), (0,1), . . . (0, m−1), (1,,0),(1,1), . . . , (1, m−1), . . . ,(m−1, m−1)} such that each element of Bi is placed in an empty bin given by (f1(x)+d0f2(x)+d1) mod m. The index of this displacement is stored in the sequence.
Owner:PITNEY BOWES INC
Recursively Partitioned Static IP Router Tables
InactiveUS20100135305A1Few memory accessLess accessibleData switching by path configurationIp routerPerfect hash function
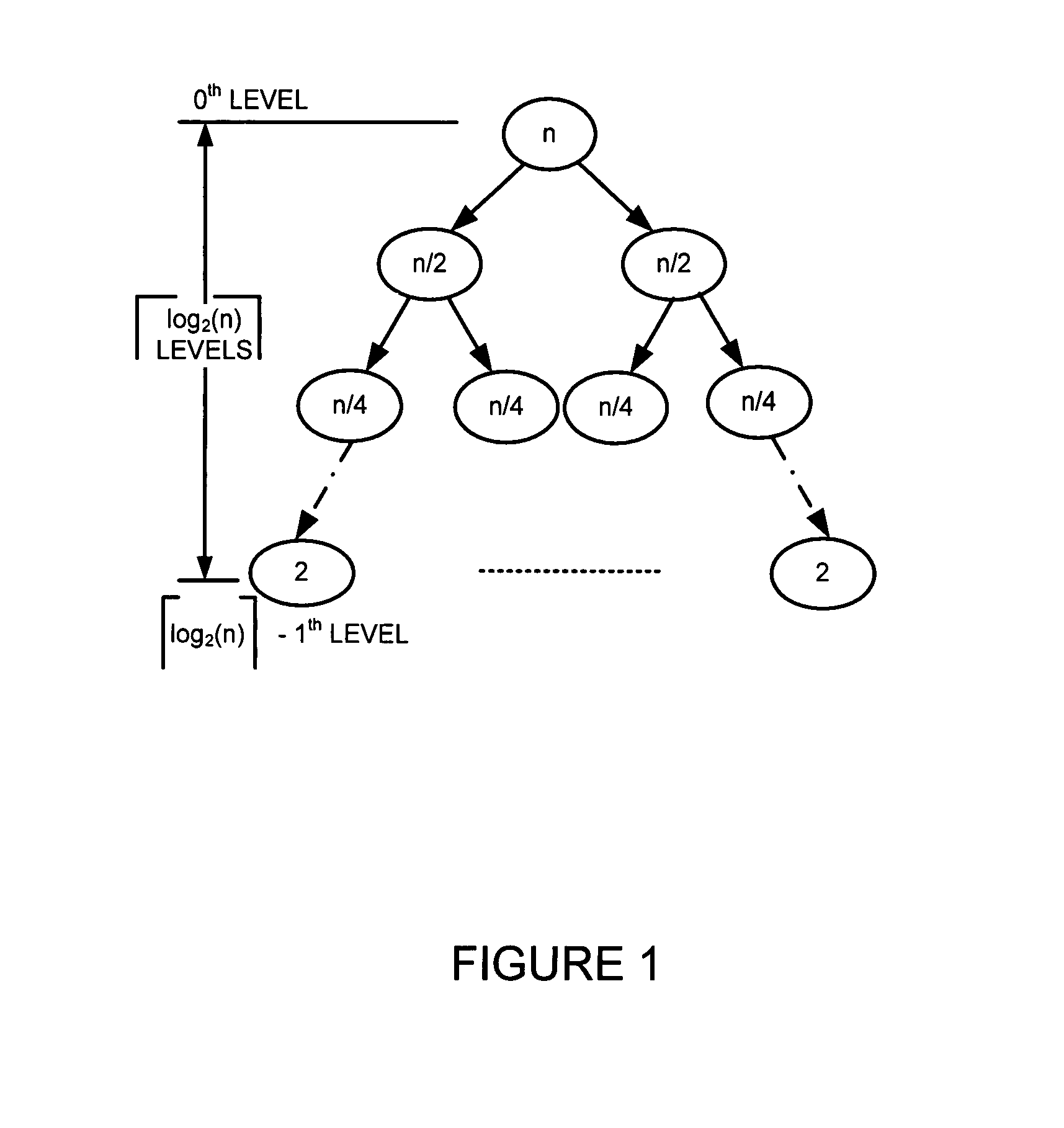
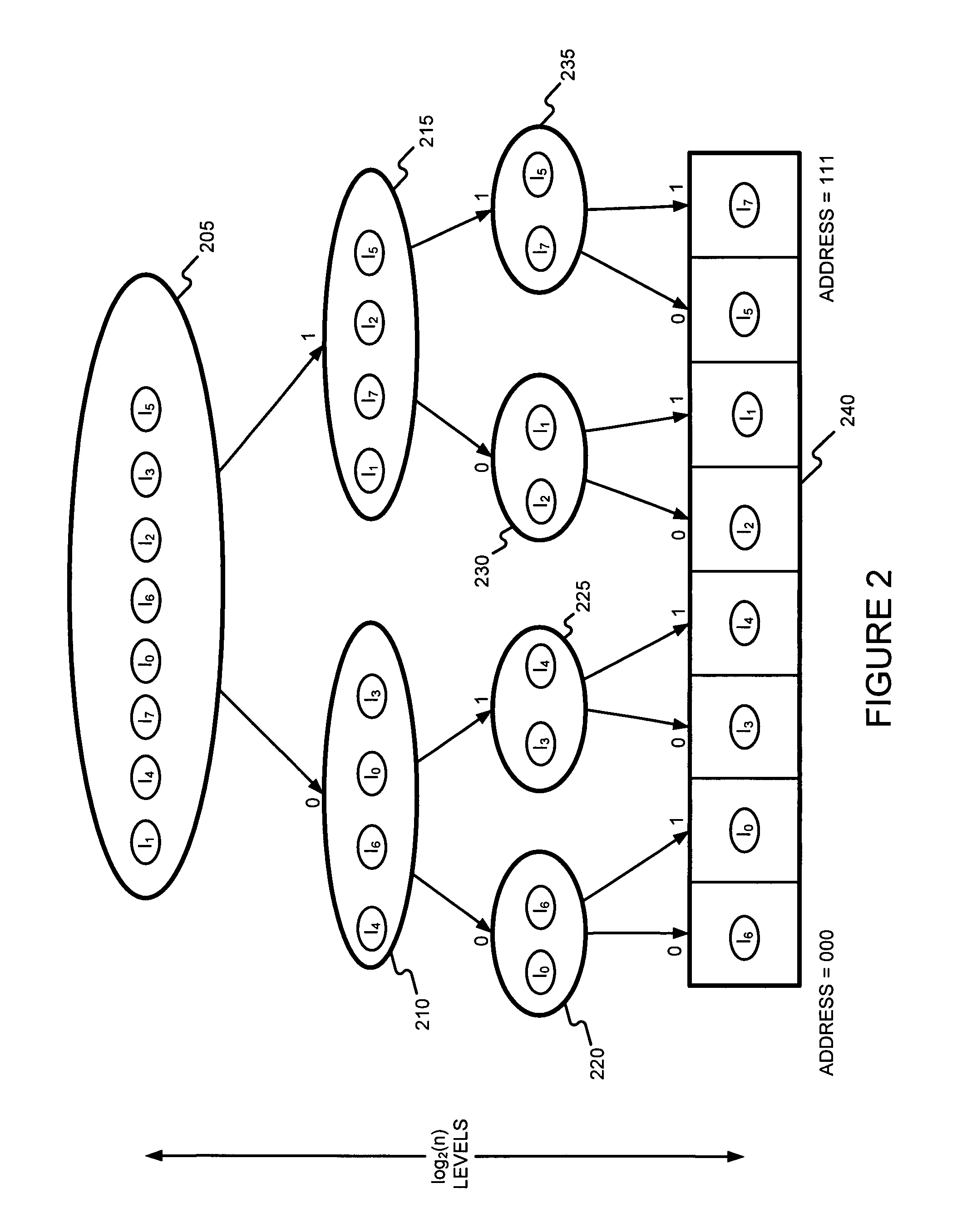
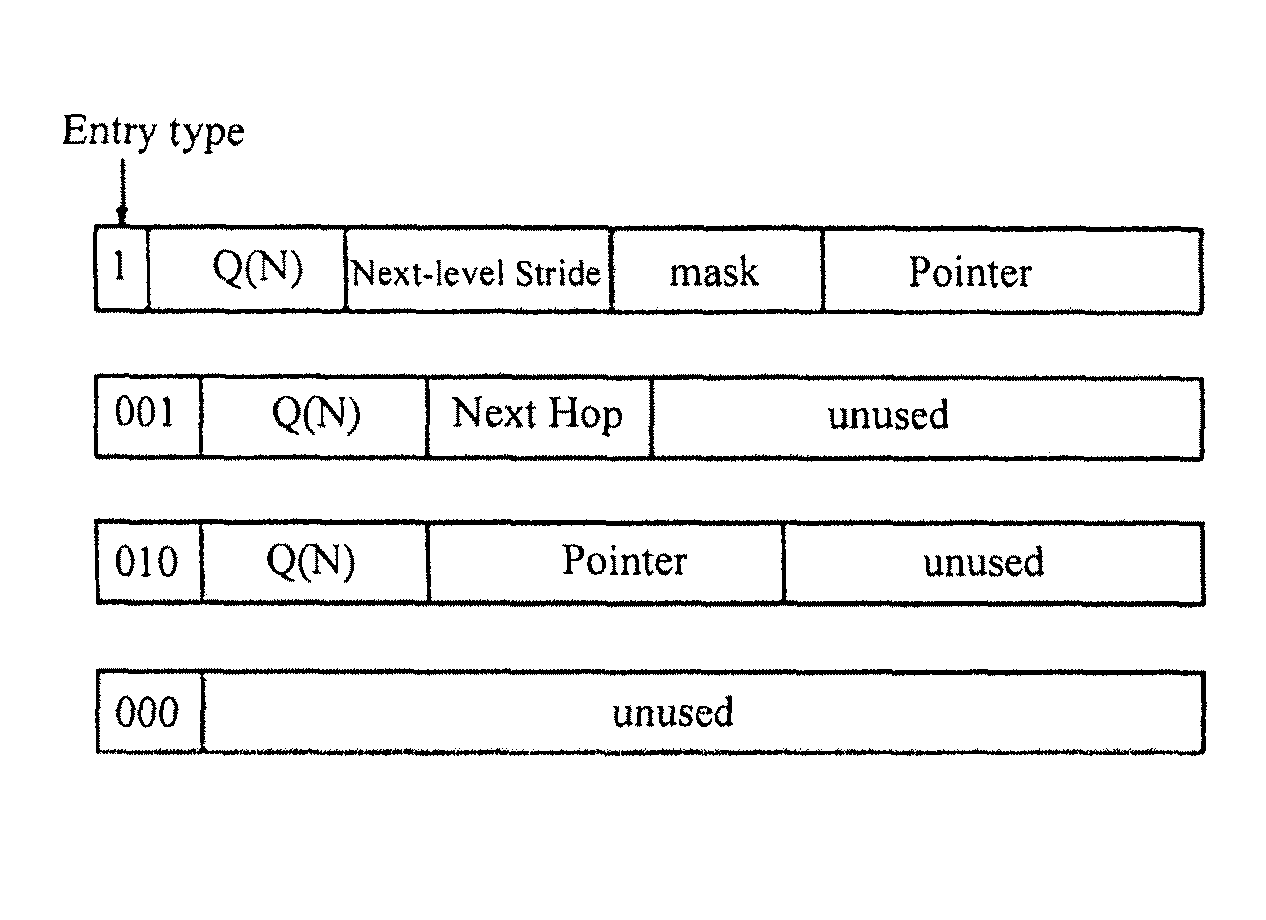
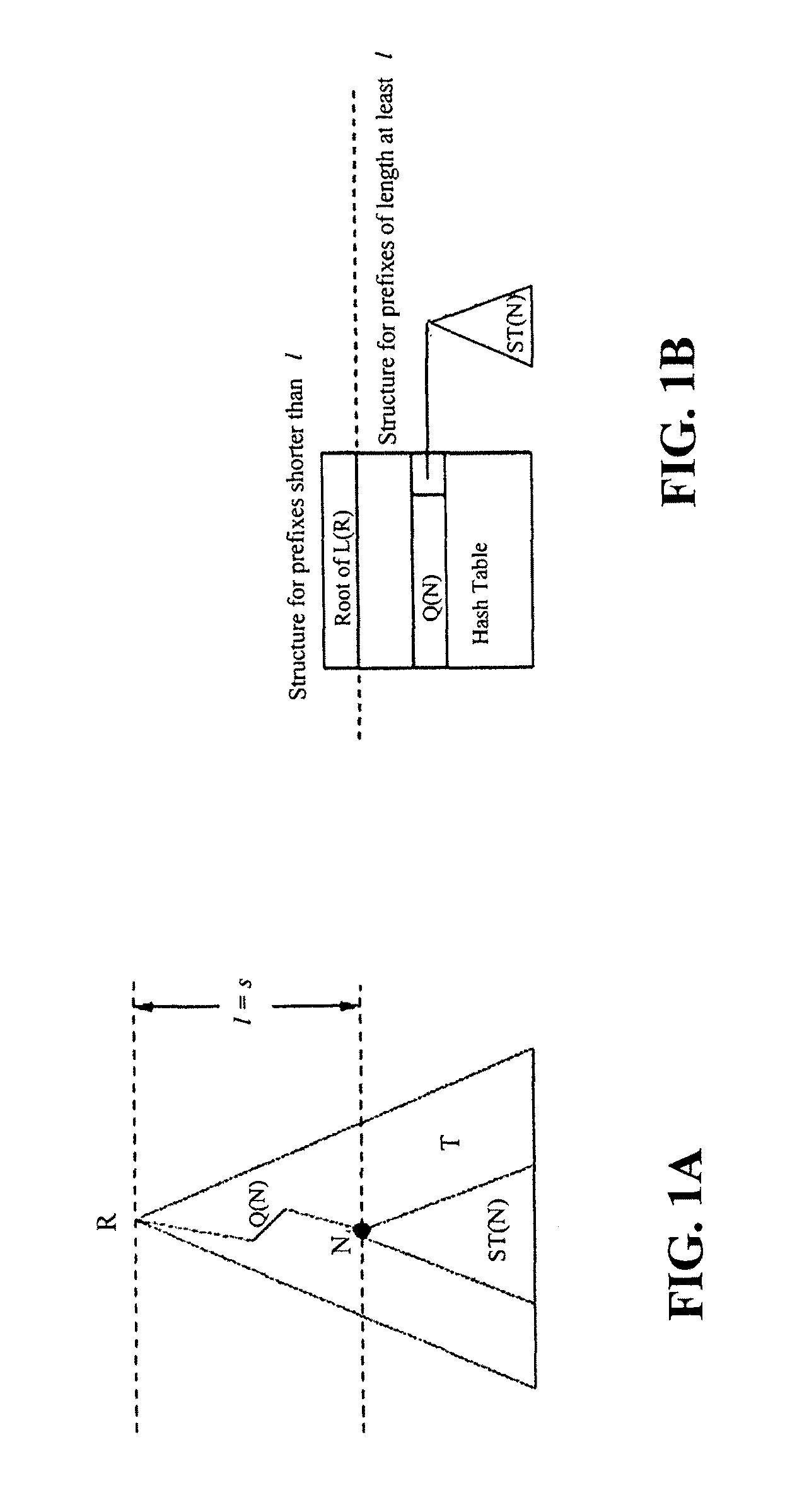
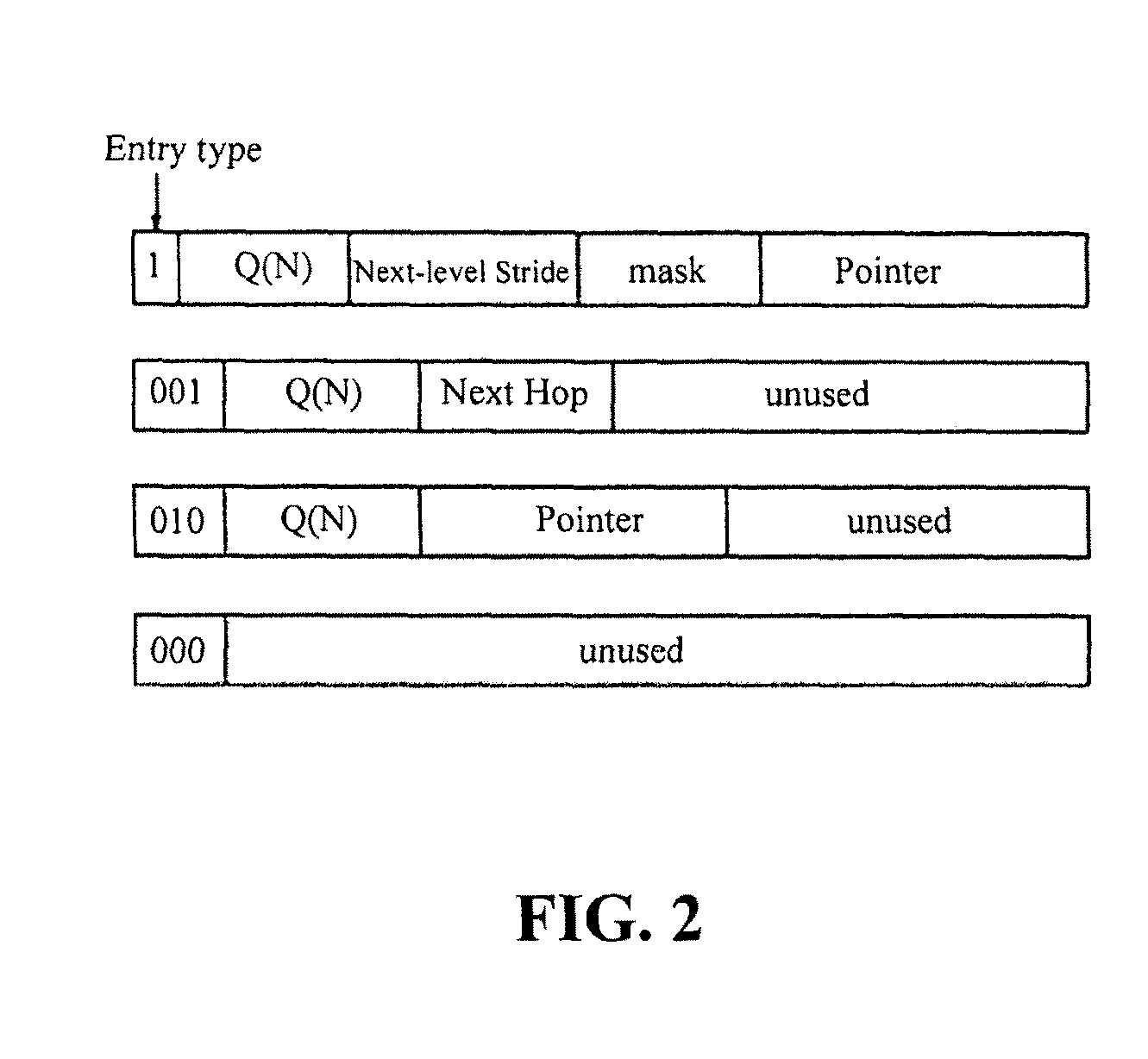
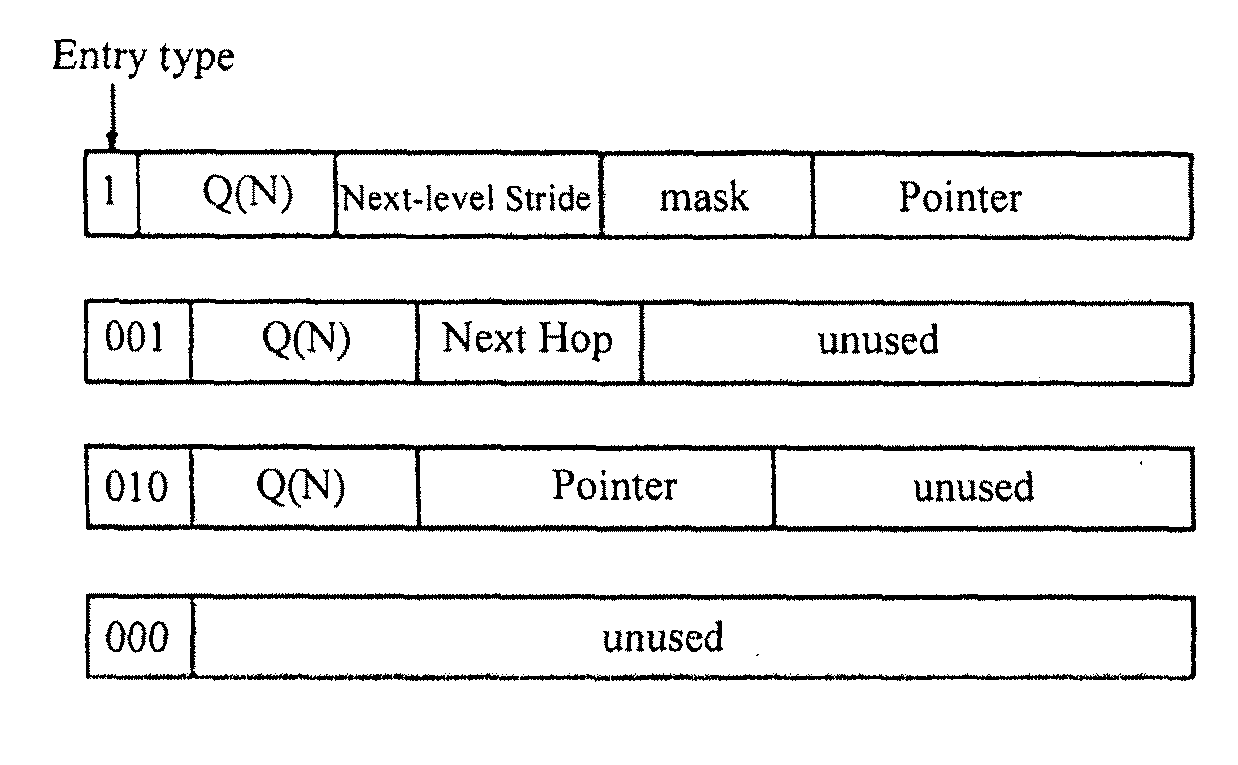
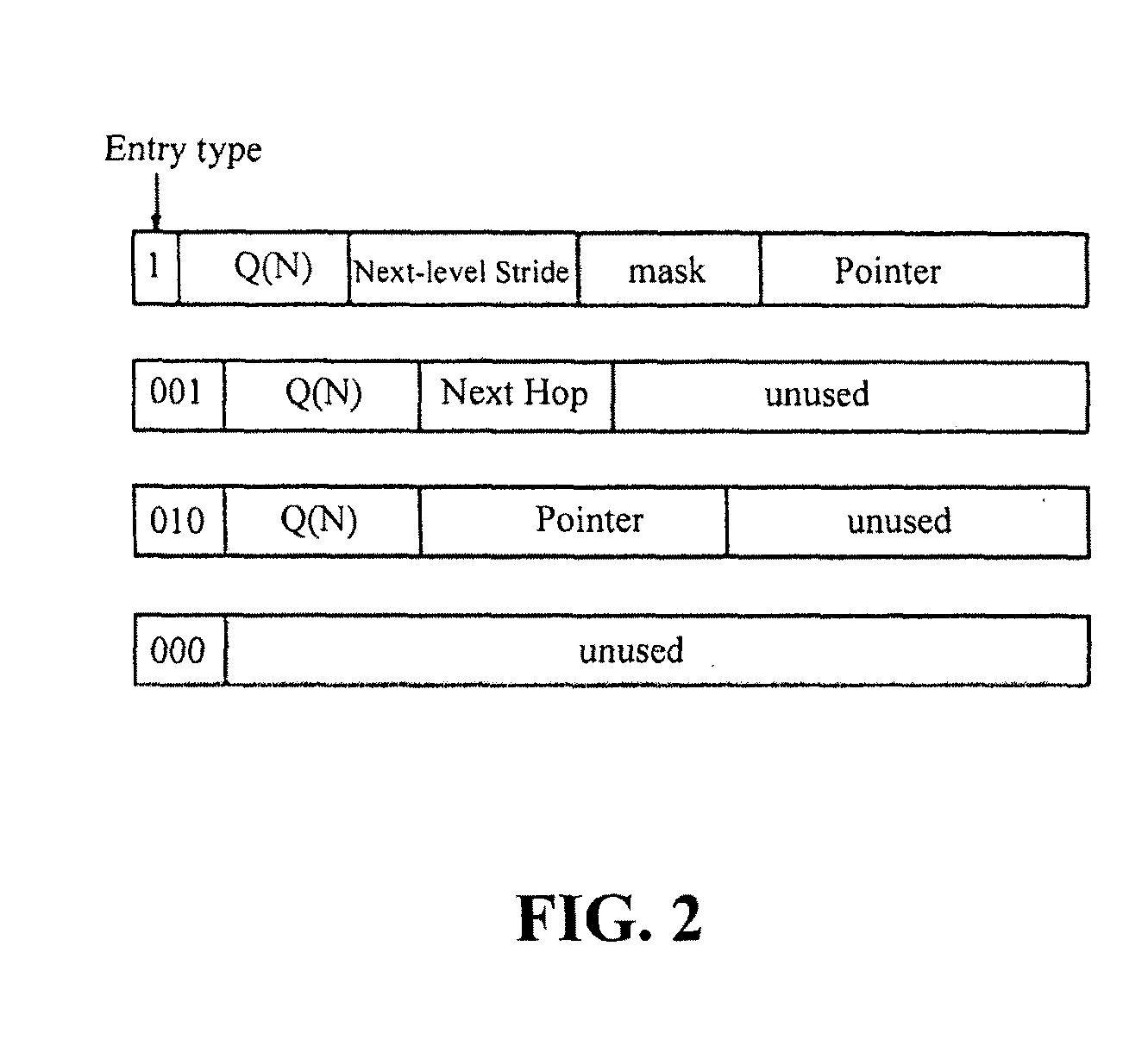
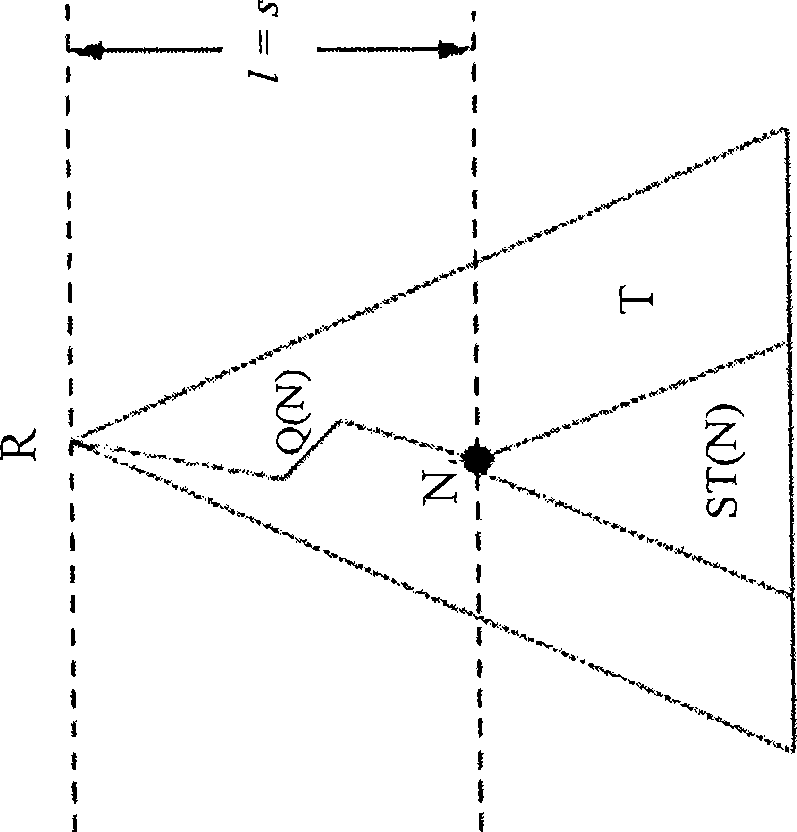
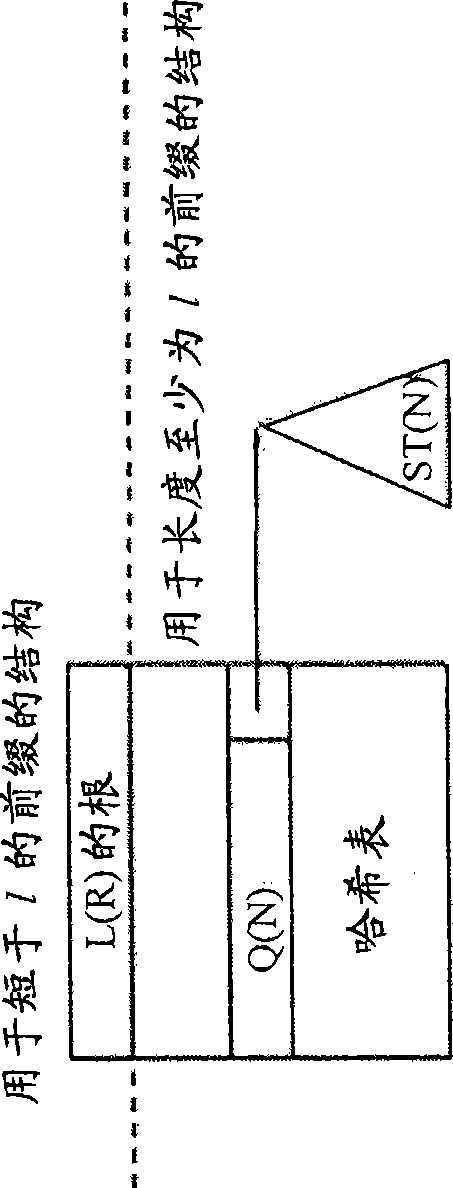
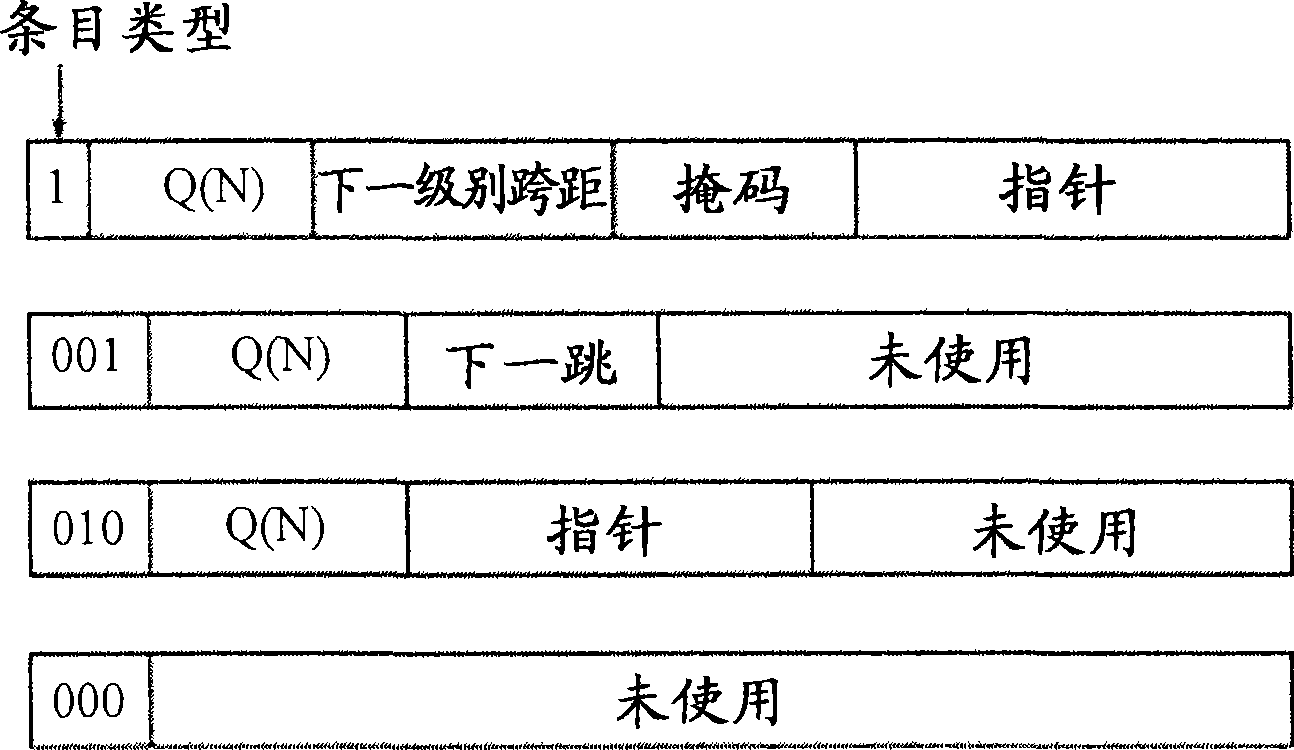
A recursively partitioned static router-table, the data structure incorporating a first-level partition including subtries and an auxiliary trie. A node of the subtrie includes a path Q(N) from the root R of a trie T to a root N of the subtrie, a stride s for a next-level partition, a mask that characterizes a next-level perfect hash function, and a pointer to the hash table for the next-level partition. At least one of the trie T, the first-level partition, the auxiliary trie, and the next-level partition is represented by a base structure selected from the group consisting of MBT and HSST.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Cache using perfect hash function
InactiveUS7966442B1Energy efficient ICTMemory loss protectionParallel computingPerfect hash function
In general, this disclosure describes techniques of storing data in and retrieving data from a cache of a computing device. More specifically, techniques are described for utilizing a “perfect hash” function to implement an associative cache within a computing device. That is, the associative cache implements a fully associative map between a predetermined set of addresses and data values, employing only a single tag fetch comparison.
Owner:JUMIPER NETWORKS INC
Memory efficient perfect hashing for large records
Embodiments for a memory efficient perfect hashing for large records. A container ID set is divided into multiple fixed range sizes. These ranges are then mapped into perfect hash buckets until each bucket is filled to uniformly distribute the container IDs across different perfect hash buckets so that the number of CIDs in every perfect hash bucket is the same or nearly the same. Individual perfect hash functions are created for each perfect hash bucket. With container IDs as keys, the process maps n keys to n positions to reduce any extra memory overhead. The perfect hash function is implemented using a compress, hash, displace (CHD) algorithm using two levels of hash functions. The level 1 hash functions divides the keys into multiple internal buckets with a defined average number of keys per bucket. The CHD algorithm iteratively tries different level 2 hash variables to achieve collision-free mapping.
Owner:EMC IP HLDG CO LLC
Log parsing method and device based on perfect hashing
ActiveCN108228875AFast learningImprove the efficiency of log parsingSpecial data processing applicationsPerfect hash functionData mining
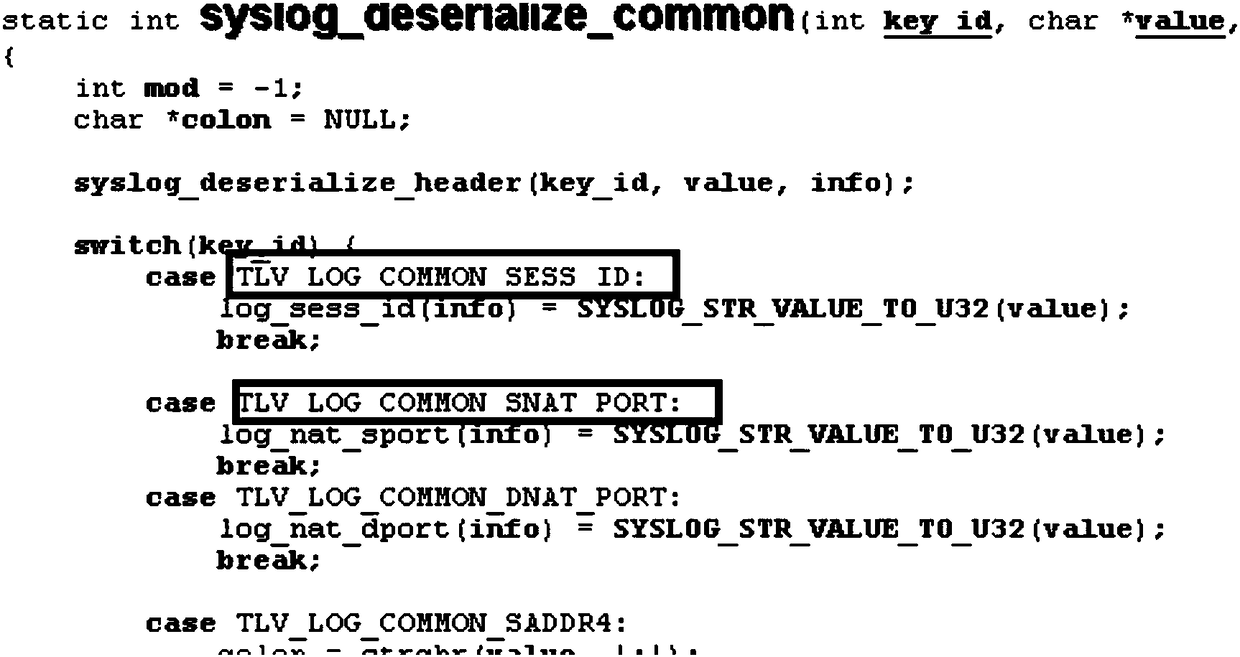
The embodiment of the invention provides a log parsing method and device based on perfect hashing. The method includes the steps of obtaining a to-be-parsed log, conducting information extraction on the to-be-parsed log according to a preset rule, and obtaining to-be-parsed keywords and corresponding values of the to-be-parsed log; according to a perfect hash function created in advance, calculating a first hash value corresponding to each to-be-parsed keyword; according to each first hash value, obtaining corresponding to-be-parsed keyword types, saving the corresponding value of each to-be-parsed keyword into a corresponding structure of the corresponding to-be-parsed keyword type for parsing to obtain structural data. The device is used for executing the method. According to the embodiment, by adopting a hash locating method for identifying the to-be-parsed keywords, there is no need to match characters of the to-be-parsed keywords one by one, the keywords can be obtained fast through hash locating, and therefore the efficiency of parsing the log is improved.
Owner:BEIJING QIANXIN TECH
Detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit strings using a hierarchical data structure
InactiveUS20120206279A1Easy to updateEasily achieve DPIDigital data information retrievalCode conversionAlgorithmTheoretical computer science
Generating and using a high-speed, scalable, and easily updateable data structure are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Generating a log-log hash-based hierarchical data structure associated with a plurality of known arbitrary-length bit strings used for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit strings
InactiveUS8212695B2Easy to updateEasily achieve DPIDigital data information retrievalCode conversionPerfect hash functionTheoretical computer science
Generating and using a high-speed, scalable and easily updateable data structures are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
NUMA-aware perfect hash algorithm
ActiveUS10146697B1Input/output to record carriersMemory adressing/allocation/relocationProcessing corePerfect hash function
Embodiments are directed to perfect physical garbage collection (PPGC) process that uses a NUMA-aware perfect hash vector. The process splits a perfect hash vector (PHVEC) into a number of perfect hash vectors, wherein the number corresponds to a number of nodes having a processing core and associated local memory, directs each perfect hash to a respective local memory of a node so that each perfect hash vector accesses only a local memory, and assigns fingerprints in the perfect hash vector to a respective node using a mask function. The process also performs a simultaneous creation of perfect hash vectors in a multi-threaded manner by scanning the Index once.
Owner:EMC IP HLDG CO LLC
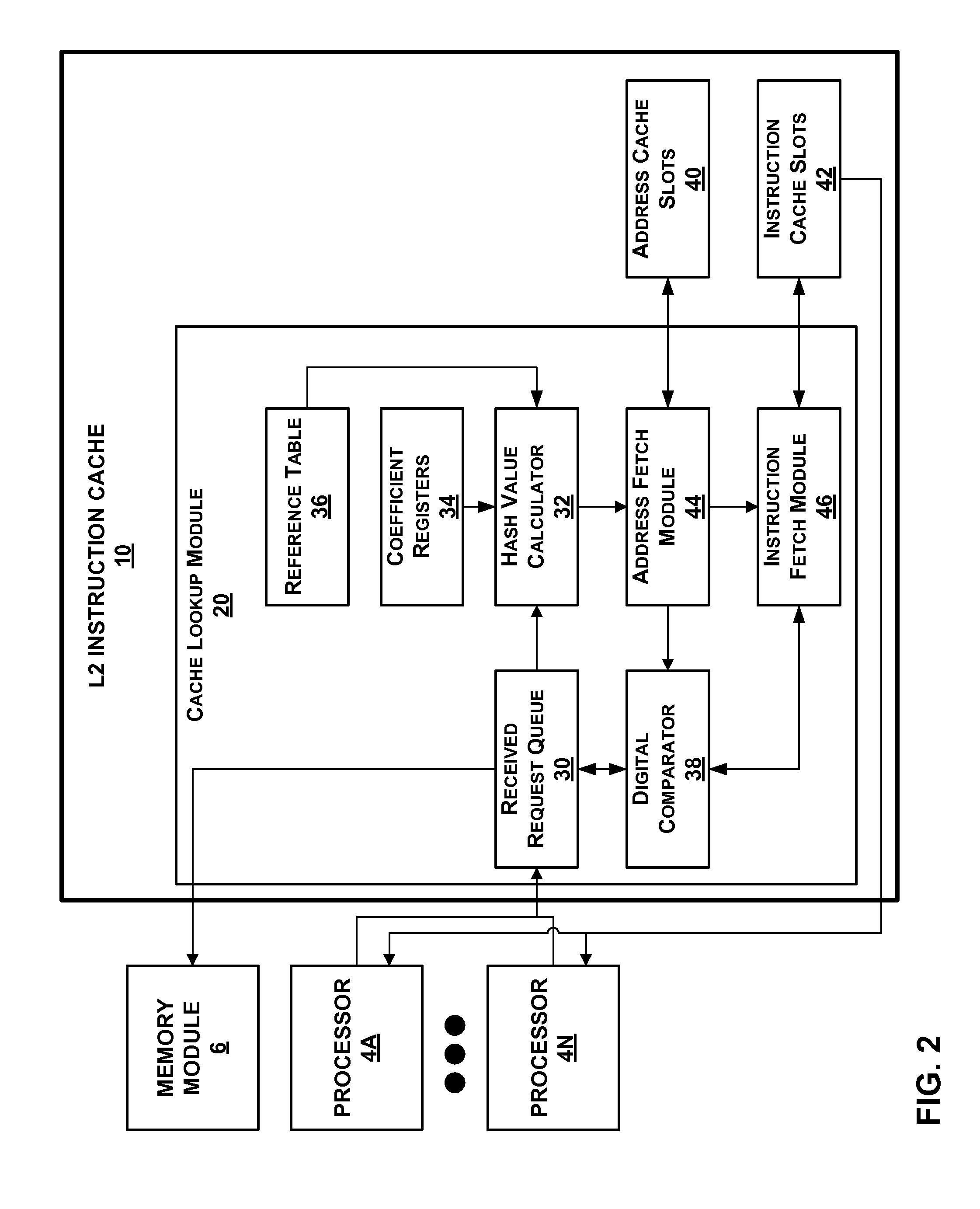
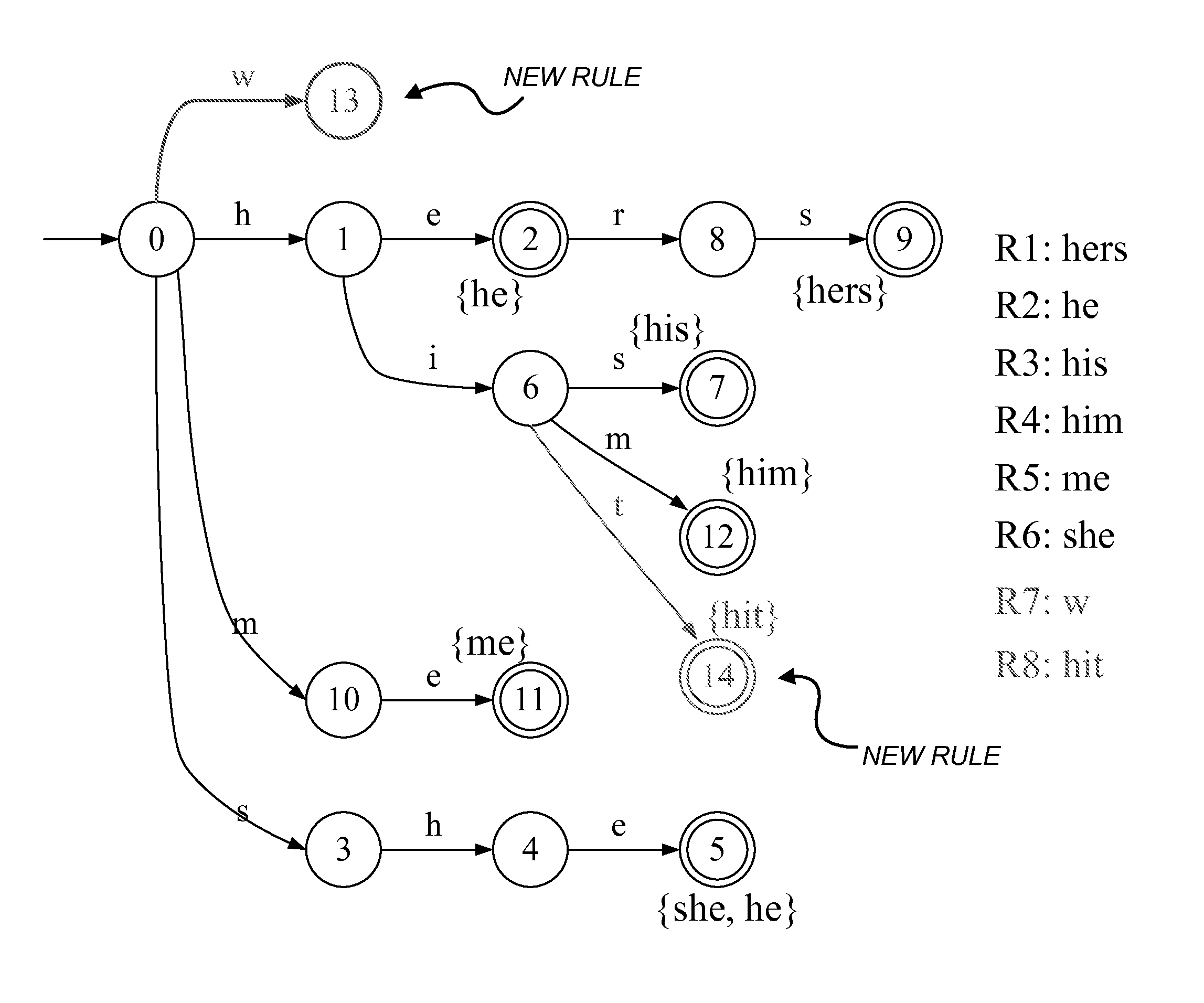
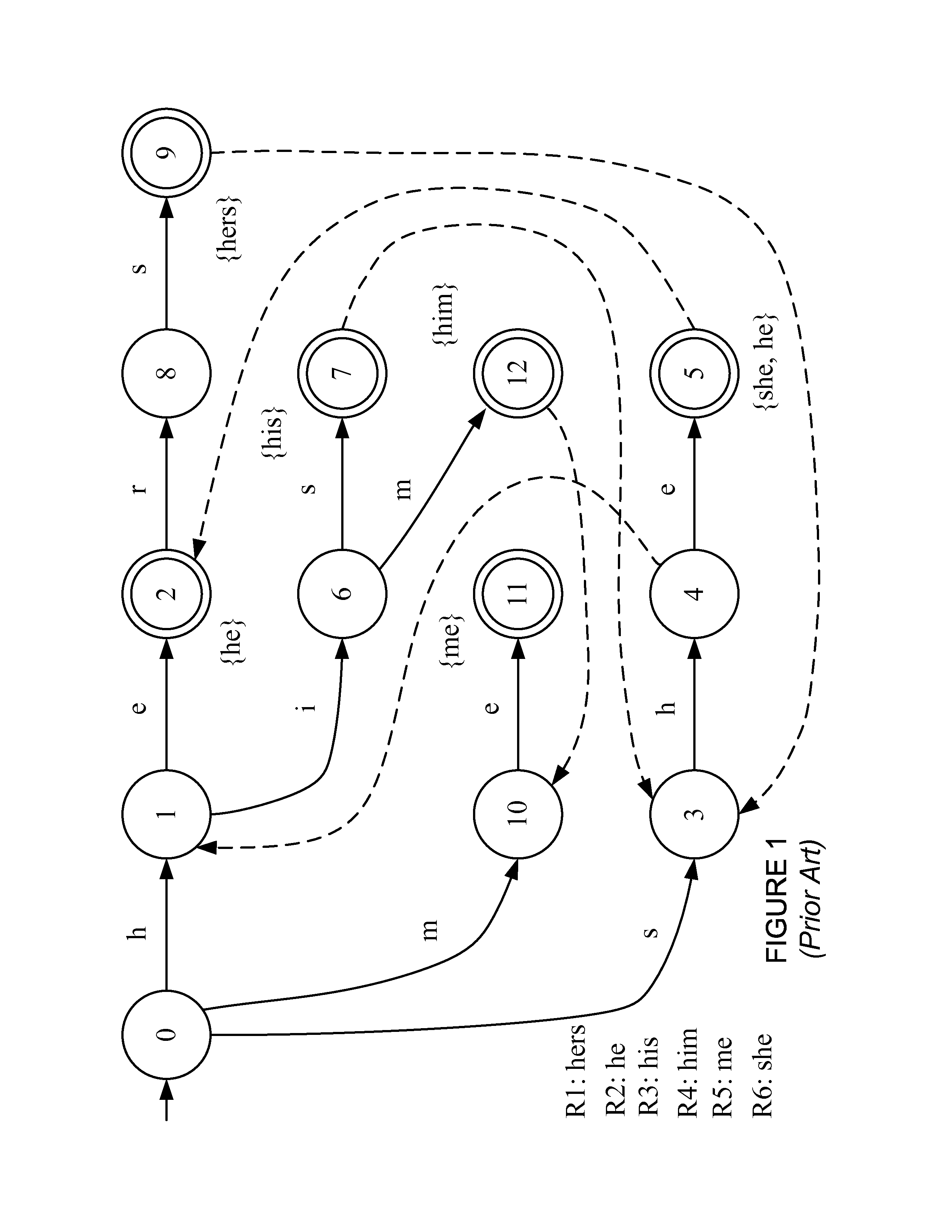
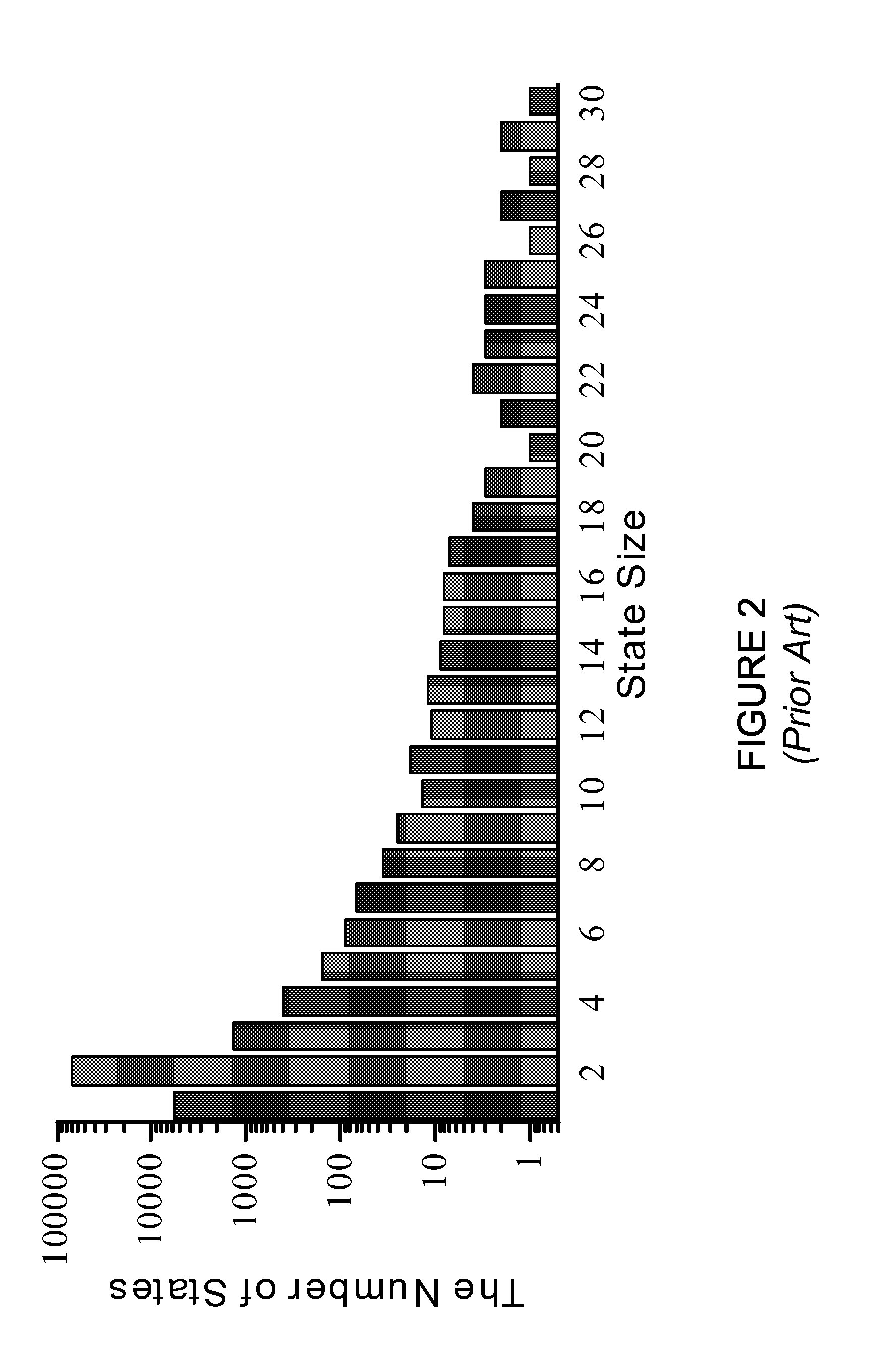
Updating a perfect hash data structure, such as a multi-dimensional perfect hash data structure, used for high-speed string matching
ActiveUS8775393B2Digital data processing detailsOther databases indexingTheoretical computer sciencePerfect hash function
A representation of a new rule, defined as a set of a new transition(s), is inserted into a perfect hash table which includes previously placed transitions to generate an updated perfect hash table. This may be done by, for each new transition: (a) hashing the new transition; and (b) if there is no conflict, inserting the hashed new transition into the table. If, however, the hashed new transition conflicts with any of the previously placed transitions, either (A) any transitions of the state associated with the conflicting transition are removed from the table, the hashed new transition is placed into the table, and the removed transitions are re-placed into the table, or (B) any previously placed transitions of the state associated with the new transition are removed, and the transitions of the state associated with the new transition are re-placed into the table.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
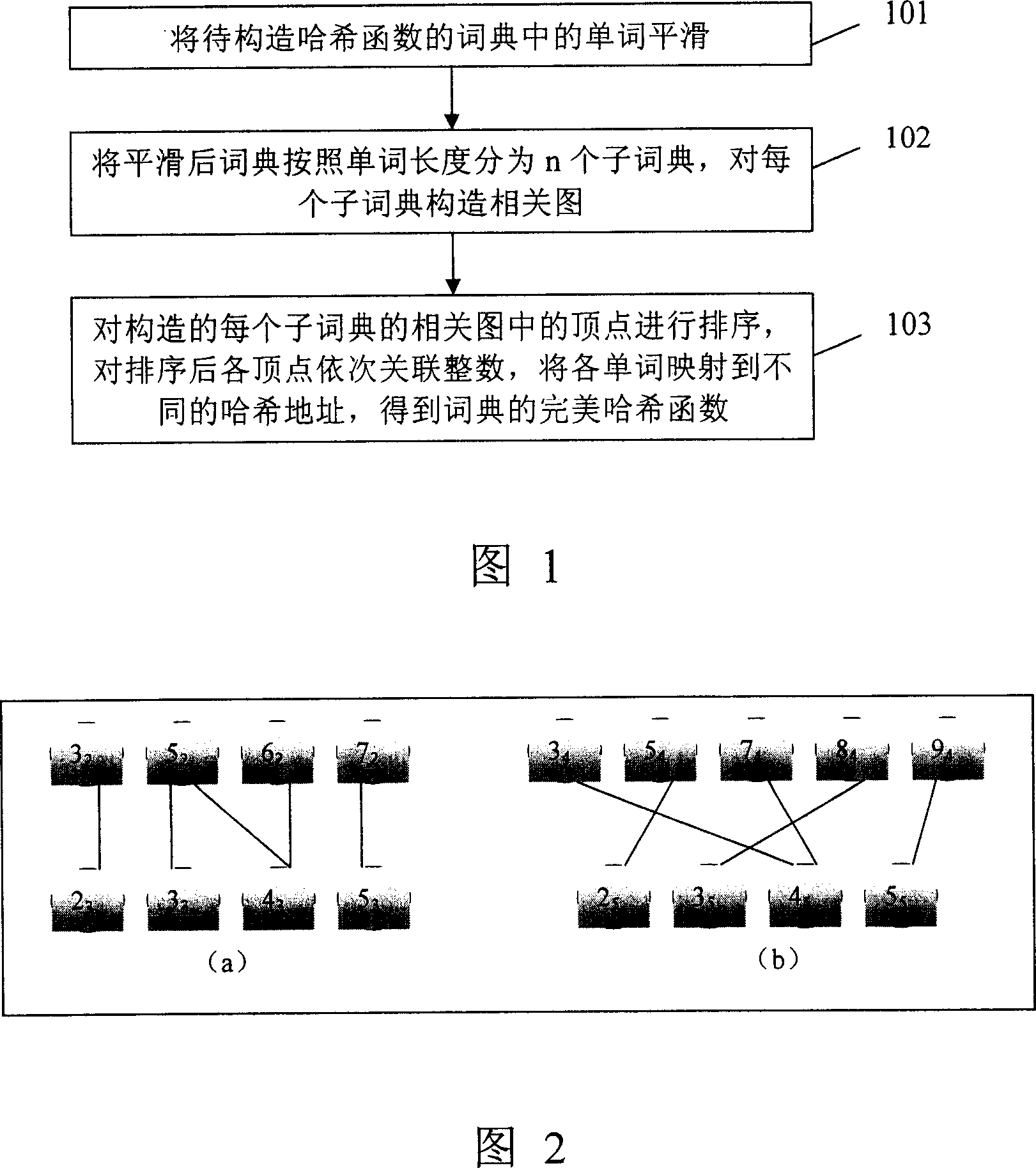
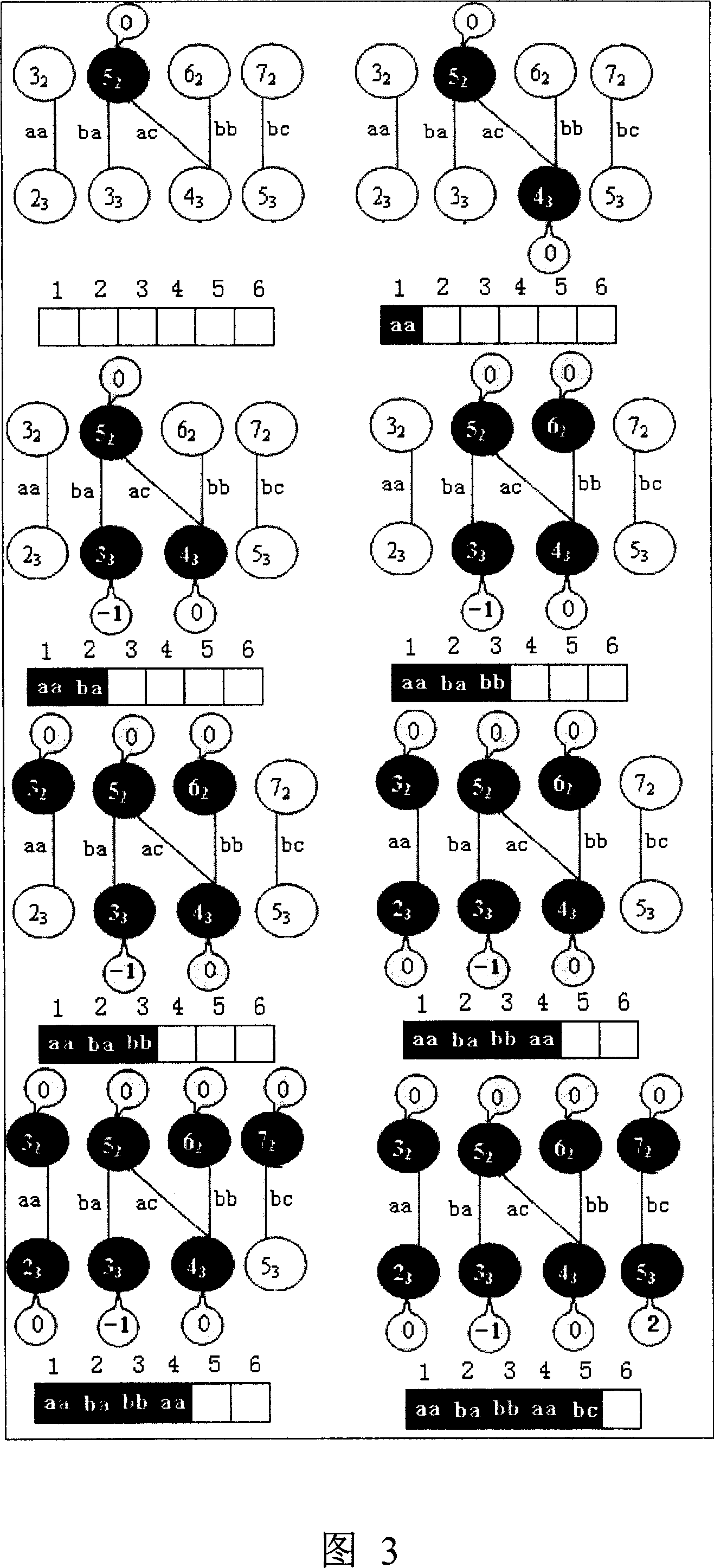
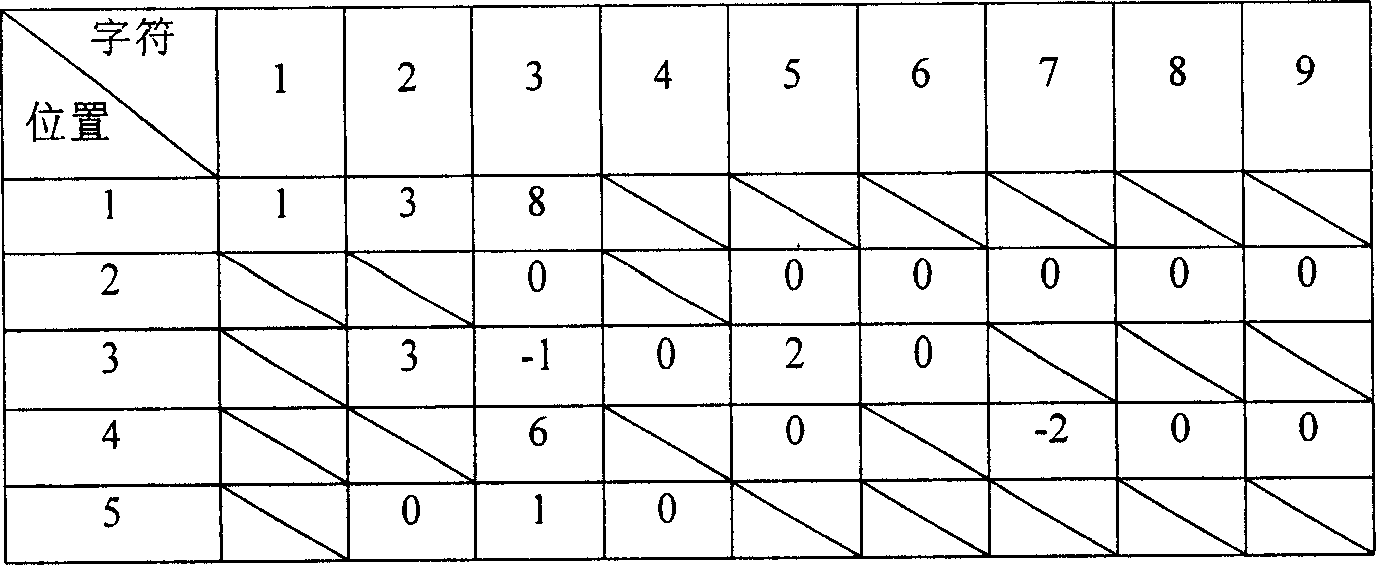
Method for constructing perfect Hash function for processing bulk dictionary
ActiveCN1996306ASave work spaceShorten construction timeSpecial data processing applicationsAlgorithmPerfect hash function
The invention relates to a perfect function for processing large scale dictionary, comprising smoothing the word in the dictionary and dividing the smoothed word dictionary into n sub dictionaries with relevant structural charts, with n being the natural number, sequencing the points of these relevant charts and mapping each word to various address to get the perfect function of the dictionary. It can include millions of words' dictionary to form perfect Hash function to process large character collection like Chinese, with reduced time and working space.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
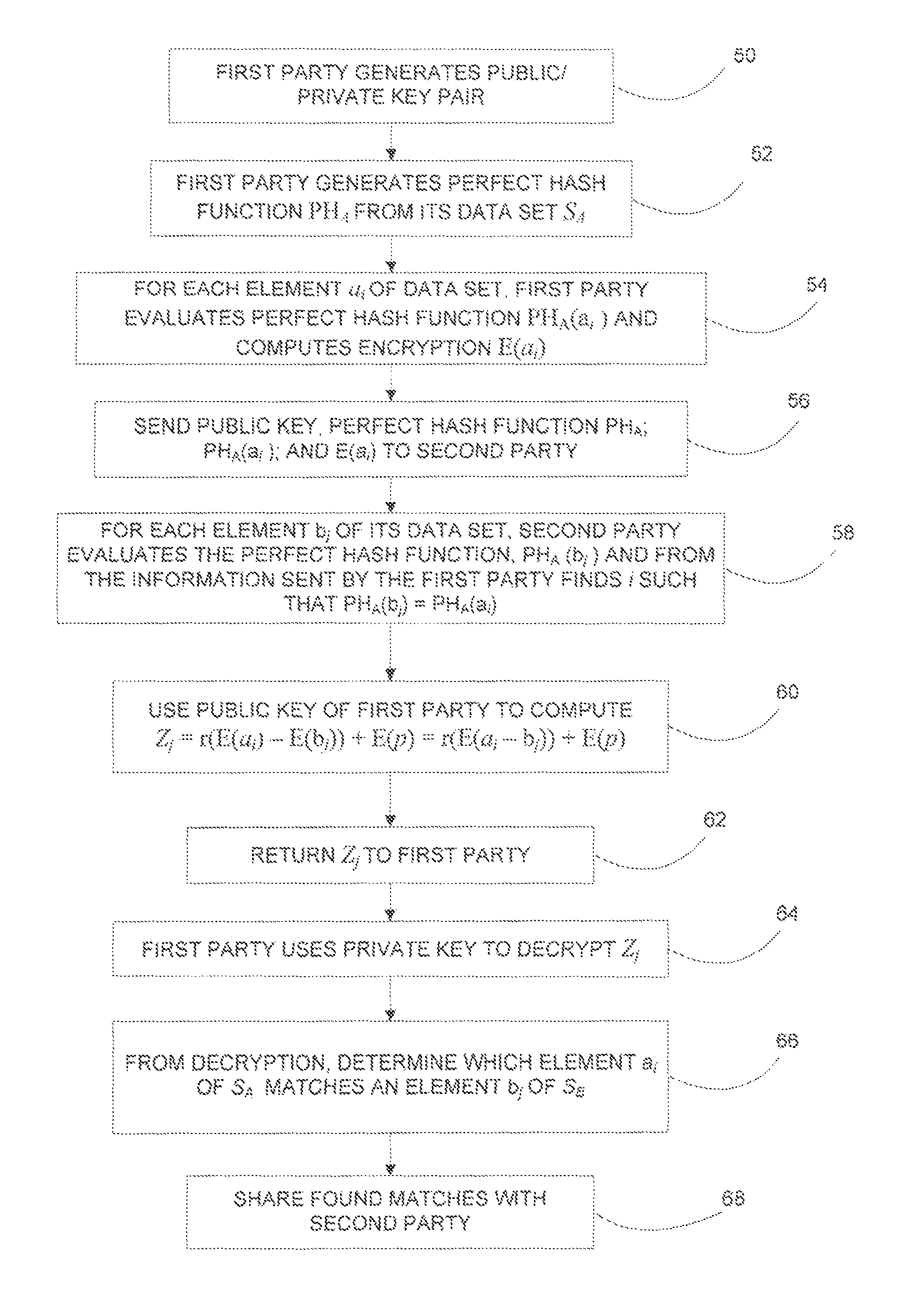
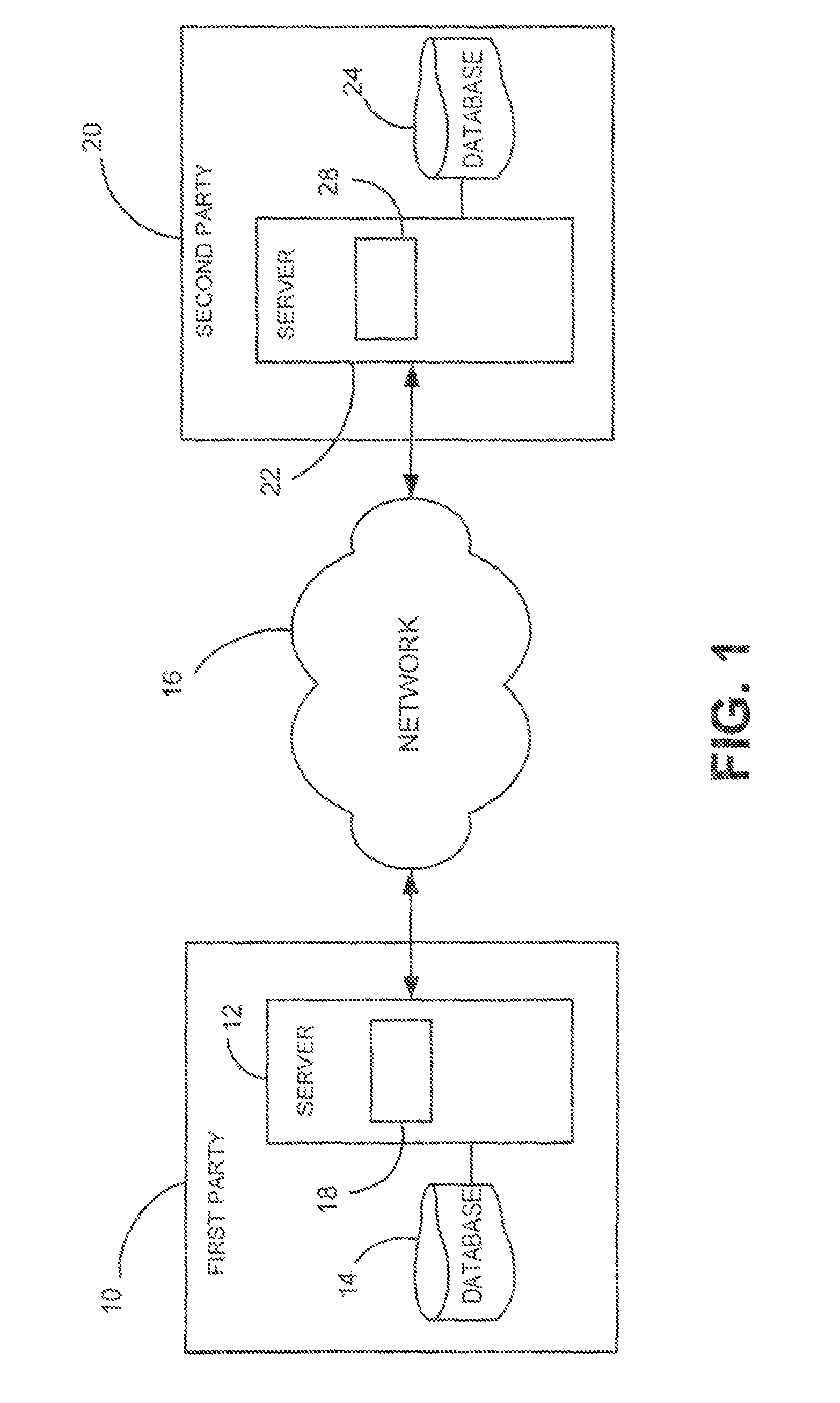
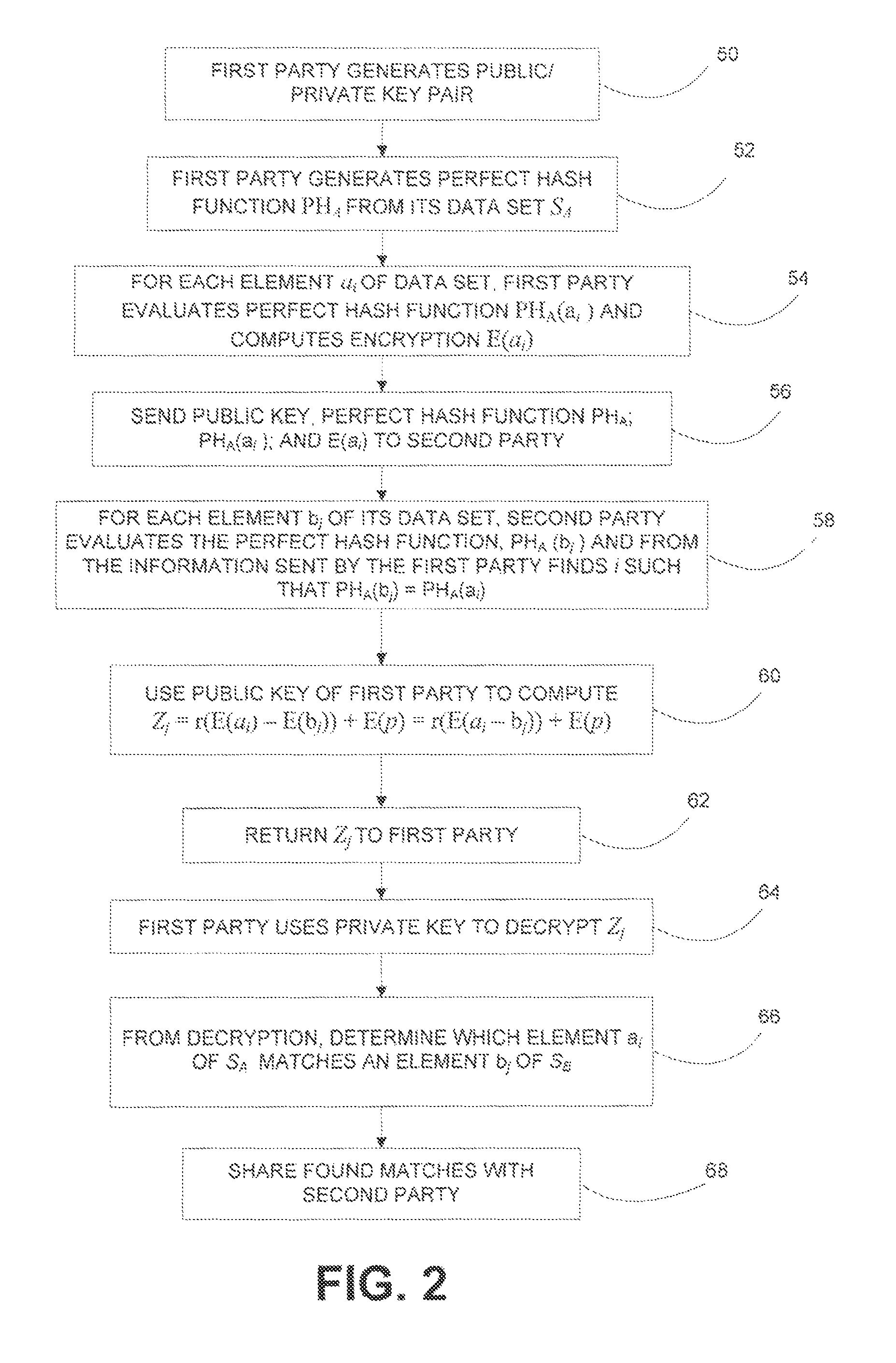
System and method for matching data sets while maintaining privacy of each data set
ActiveUS9443092B2Secure and efficient matchingKey distribution for secure communicationDigital data protectionThird partyData set
A system and method that allows two parties to find common records in their data sets without having to actually share the data sets with each other or a third party. Two primitives, perfect hash functions and public key cryptography, are combined in a unique way to obtain a secure and efficient private matching solution. Since the data that is exchanged is always encrypted during the match process, neither party reveals its data to the other party. This solution enables two parties to match sensitive data such as PII (Personally Identifiable Information) or PHI (Protected Health Information) without having to disclose the data to other or to any third party. One or both of the parties only learn of matching records without learning any information about the records that do not match.
Owner:PITNEY BOWES INC
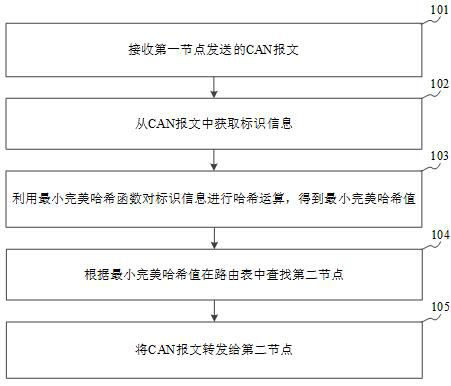
Gateway message forwarding method and device, storage medium and gateway
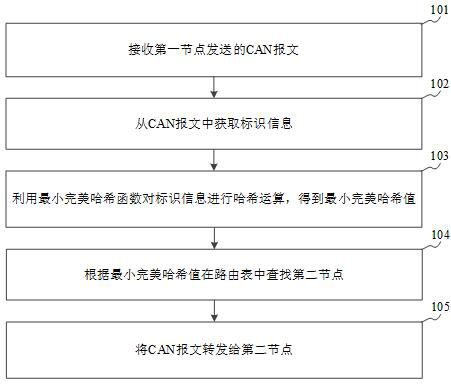
ActiveCN112491723AForward in real timeReduce latencyEncryption apparatus with shift registers/memoriesBus networksRouting tablePerfect hash function
The embodiment of the invention discloses a gateway message forwarding method and device, a storage medium and a gateway, and belongs to the technical field of communication. The method comprises thefollowing steps: receiving a CAN message sent by a first node; acquiring identification information from the CAN message; performing hash operation on the identification information by utilizing a minimum perfect hash function to obtain a minimum perfect hash value; searching a second node in a routing table according to the minimum perfect hash value; and forwarding the CAN message to the secondnode. According to the embodiment of the invention, the minimum perfect hash value is calculated for the identification information through the minimum perfect hash function, and the minimum perfect hash values calculated according to different identification information are different, so that hash collision is avoided, CAN messages of all nodes can be forwarded in real time, and the time delay ofmessage forwarding is reduced.
Owner:上海励驰半导体有限公司
Recursively partioned static ip router tables
InactiveCN101507191AReduce accessLess total storage requirementsData switching by path configurationIp routerPerfect hash function
A recursively partitioned static router-table, the data structure incorporating a first-level partition including subtries and an auxiliary trie. A node of the subtrie includes a path Q(N) from the root R of a trie T to a root N of the subtrie, a stride s for a next-level partition, a mask that characterizes a next-level perfect hash function, and a pointer to the hash table for the next-level partition. At least one of the trie T, the first-level partition, the auxiliary trie, and the next-level partition is represented by a base structure selected from the group consisting of MBT and HSST.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Gateway message forwarding method, device, storage medium and gateway
ActiveCN112491723BForward in real timeReduce latencyEncryption apparatus with shift registers/memoriesBus networksRouting tablePerfect hash function
The embodiment of the application discloses a gateway message forwarding method, device, storage medium and gateway, which belong to the technical field of communication. The method includes: receiving a CAN message sent by a first node; obtaining identification information from the CAN message; performing a hash operation on the identification information using a minimum perfect hash function to obtain a minimum perfect hash value; according to The minimum perfect hash value is searched for a second node in a routing table; and the CAN message is forwarded to the second node. In the embodiment of the present application, the minimum perfect hash value is calculated for the identification information through the minimum perfect hash function. Since the minimum perfect hash values calculated according to different identification information are different, there will be no hash collision. It can also ensure that the CAN messages of all nodes can be forwarded in real time, reducing the delay of message forwarding.
Owner:上海励驰半导体有限公司
Parametric filter using hash functions with improved time and memory
PendingUS20220291925A1Minimize energy functionSpecial data processing applicationsMachine execution arrangementsData streamTheoretical computer science
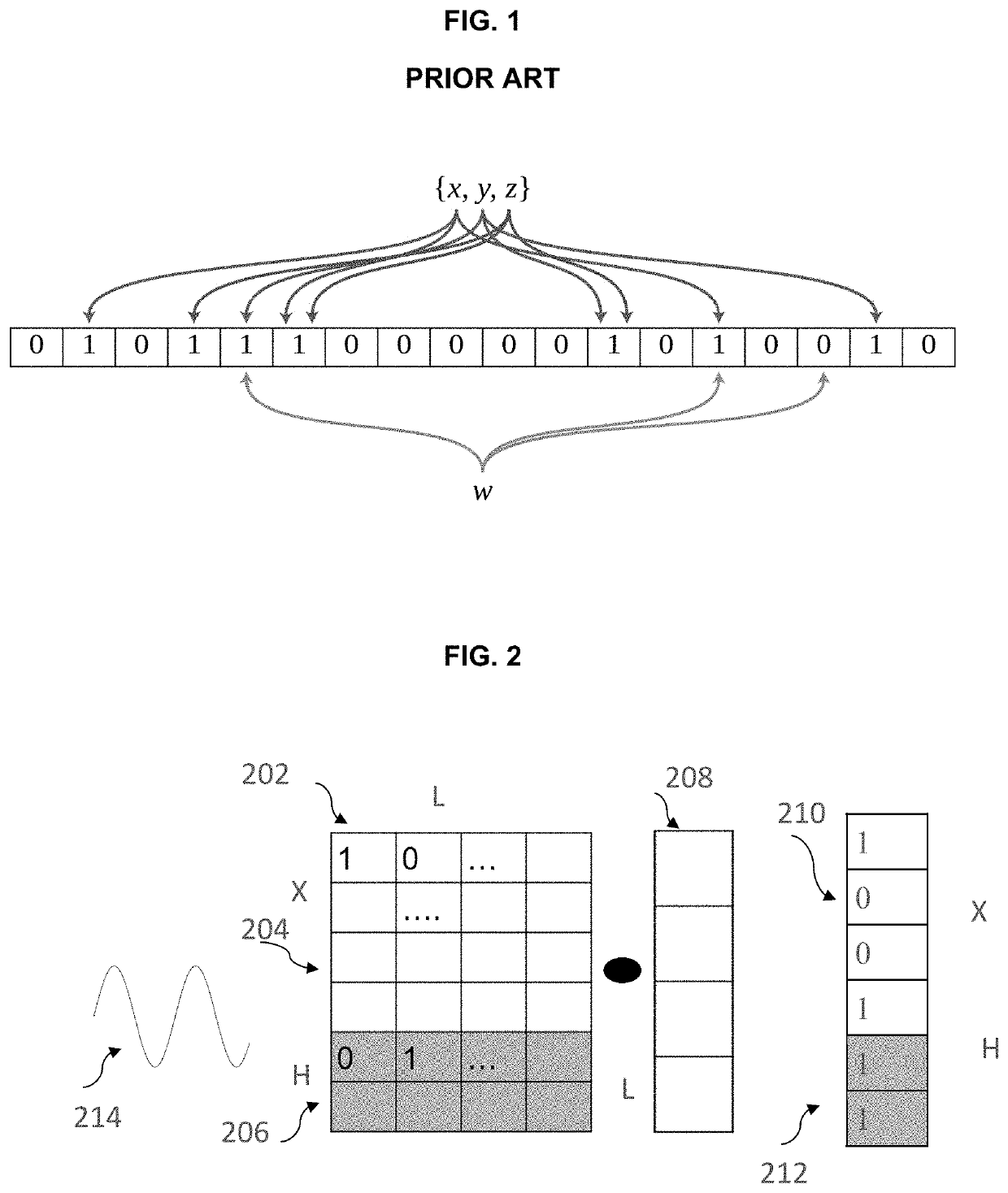
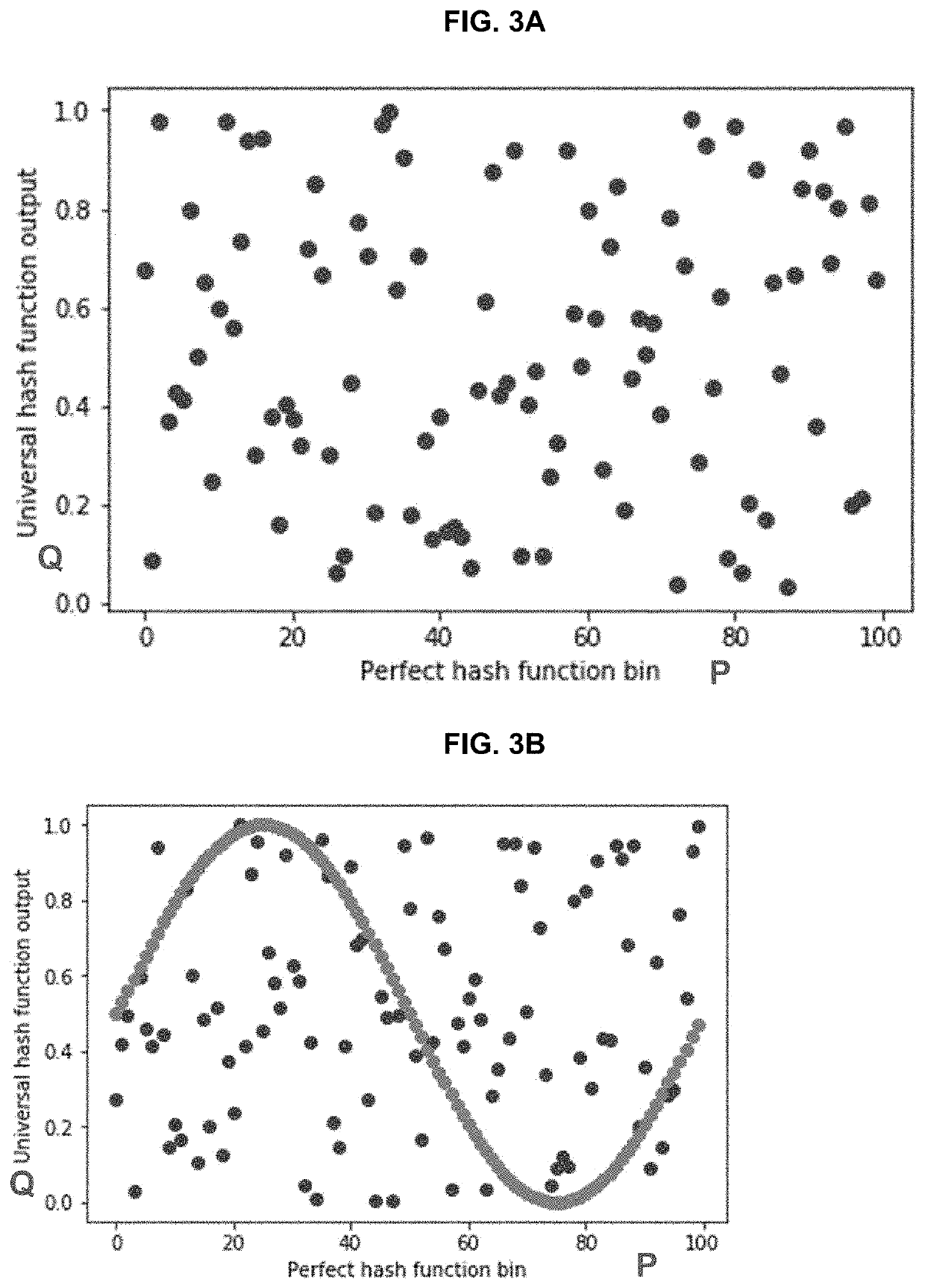
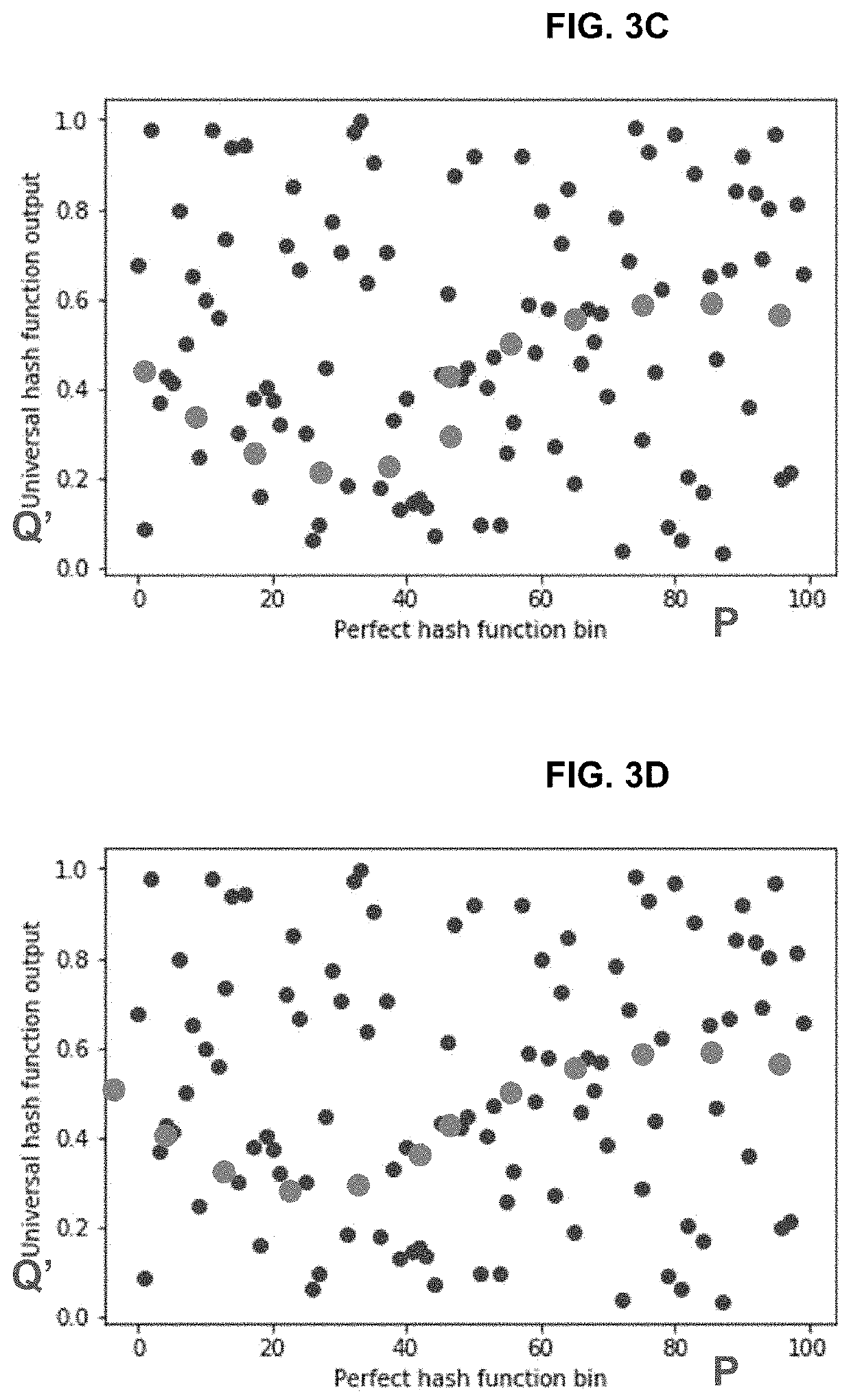
Method for searching an item using a parametric hash filter includes forming an input vector from input data stream; forming a hash matrix having a first portion and a second portion; multiplying the hash matrix with the input vector to generate a second input vector including a hash values of the first input vector; generating a perfect hash vector and a universal hash vector, by applying a smooth periodic function to the second input vector; mapping onto a Markov random field the coordinates of locations of hash values in a search domain for which there is no possibility of collisions in the perfect hash vector to form an energy function; minimizing the energy function to generate a compressed hash table; fitting a band of acceptable locations in the compressed hash table, based on a predetermined false positive rate; and searching for a new item in the band of acceptable locations.
Owner:RAYTHEON BBN TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com